read file error: read notes: is a directory 2023-6-2 21:0:57 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:36 收藏

This post is also available in: 日本語 (Japanese)
Executive Summary
Unit 42 researchers have identified a growing trend of cyberattacks targeting web applications and application programming interfaces (APIs) hosted by cloud service providers. Based on the data from our research, 14.9% of attacks in late 2022 on web applications and APIs targeted cloud-hosted deployments.
Attackers are also operating in the cloud and using it to launch their attacks on applications and APIs, as 5.1% of the attacks originated from cloud service providers' addresses. We will discuss what web and API attacks are and why attackers are exploiting them in the cloud. We will also review possible reasons for attacks originating from the cloud, as well as the potential impact on businesses and individuals.
Palo Alto Networks customers using Prisma Cloud are protected from these threats through the WAAS module, which is designed to protect web applications and APIs in cloud environments.
| Related Unit 42 Topics | Cloud, Malware |
Table of Contents
Understanding Web Applications and APIs
Web Applications and APIs on the Cloud
Attacks on Web Applications and APIs in the Cloud
Origination of Web Application and API Attacks
Conclusion
Understanding Web Applications and APIs
APIs and web applications play a pivotal role in today's digital landscape. Web applications are software programs accessed through web browsers, providing interactive and engaging user experiences. Meanwhile, APIs act as intermediaries that facilitate communication between different software applications.
By enabling seamless interaction between applications, APIs simplify complex processes and promote a more connected digital ecosystem. Generally, both web applications and APIs are served on the HTTP protocol.
The widespread use of web applications and APIs has made them an integral part of the modern online world. Businesses, organizations and developers are increasingly adopting them to create user-friendly interfaces and automate processes, boosting efficiency and productivity.
The growing reliance on these technologies has also led to an increased focus on ensuring their security and reliability. As a result, it is essential to keep up with best practices and stay informed about potential vulnerabilities to protect valuable data and to maintain users' trust.
Web Applications and APIs on the Cloud
There has been a significant surge of organizations moving web applications and APIs to the cloud in recent years. Recognition among businesses and organizations of the numerous benefits offered by cloud solutions is driving this transformation.
Cloud applications are mainly based on microservices architecture, which is why the shift to the cloud is encouraging an evolution in software architecture. This difference is driving these organizations to embrace microservices architecture.
There are also many advantages of employing a microservices architecture, which is an approach to software development where an application is divided into small, independent services that communicate with each other through APIs.
A recent survey of nearly 400 organizations by TechTarget's Enterprise Strategy Group (ESG) Research Team, published in April 2023 and co-sponsored by Palo Alto Networks, revealed that organizations plan to double down on microservices architecture for their applications and move their production workloads into cloud providers.
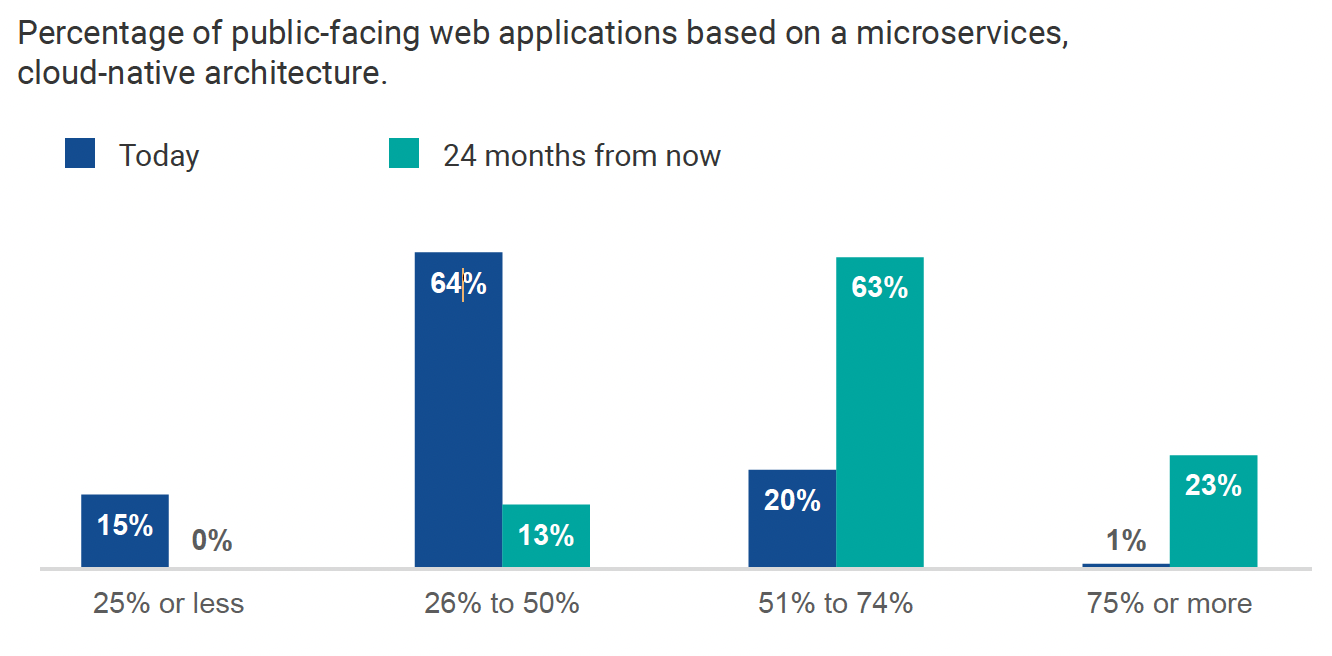
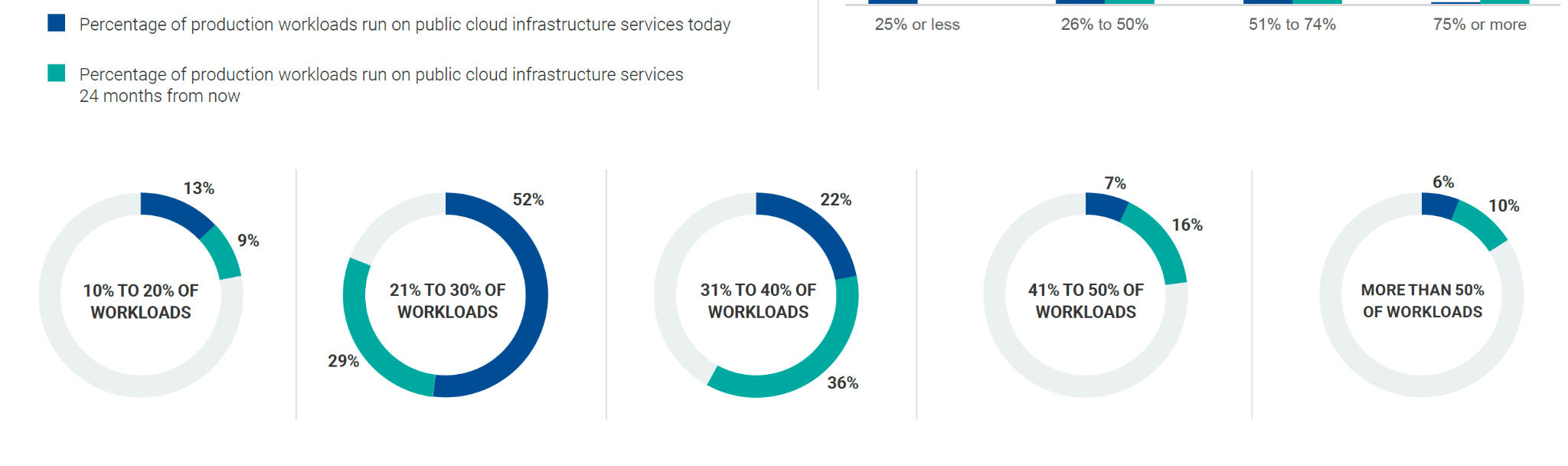
A wide variety of organizations are increasingly deploying their web applications and APIs in the cloud due to its compelling advantages. Cloud-based infrastructure offers scalability, flexibility and cost-effectiveness, allowing businesses to adapt to changing demands quickly and only pay for the resources they use. Moreover, the cloud enables faster development and deployment cycles, promoting innovation and agility.
Attacks on Web Applications and APIs in the Cloud
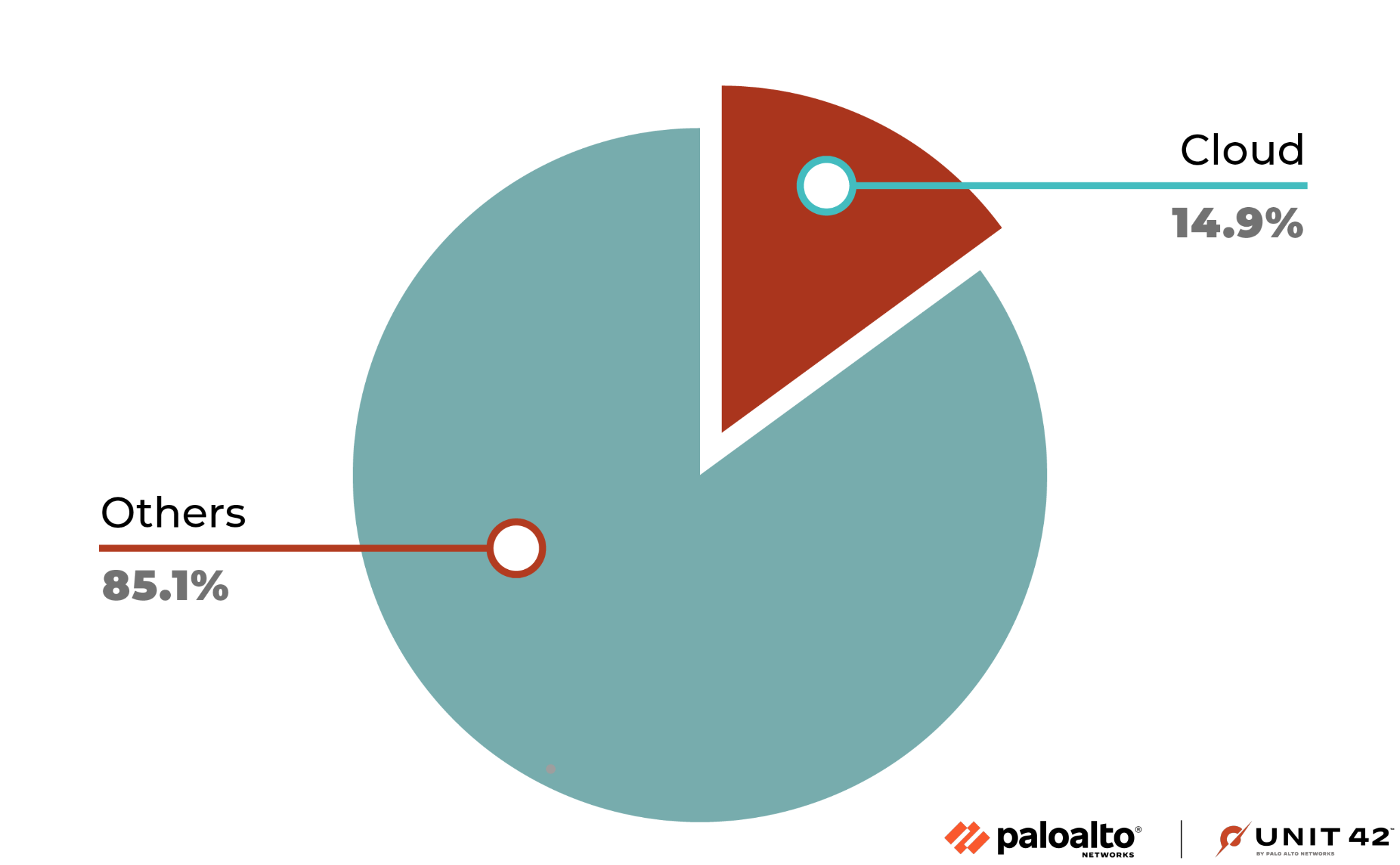
Unit 42 researchers conducted research on roughly 12 billion attacks targeting web applications and APIs to determine if attackers are targeting such instances on the cloud. Their findings revealed that attackers indeed place increased emphasis on targeting cloud-hosted web applications and APIs.
Through the analysis of this data, we discovered that 14.9% of attacks on web applications and APIs were directed at workloads hosted by the top three cloud vendors. This indicates that the cloud is not only a critical component for businesses but also an increasingly attractive target for cybercriminals.
We believe attackers are increasingly targeting web applications and APIs in the cloud for several reasons.
- Growing adoption of cloud services:
- As more businesses and individuals migrate their workloads to the cloud for scalability, cost-effectiveness and convenience, the attack surface for cybercriminals expands, providing more opportunities.
- Complex security landscape:
- Cloud environments often have complex architectures and multitenant setups, leading to increased security risks. Attackers can take advantage of misconfigurations, unsecured data storage or vulnerable APIs to exploit systems.
- Abundant resources:
- Cloud environments offer abundant computing resources, making them attractive targets for resource-intensive attacks such as distributed denial-of-service (DDoS) attacks or cryptojacking.
- Value and Impact:
- Web applications and APIs often handle valuable data or provide critical services. Attackers target these systems in the cloud to gain unauthorized access to sensitive information, disrupt services or leverage compromised resources for further attacks.
Origination of Web Application and API Attacks
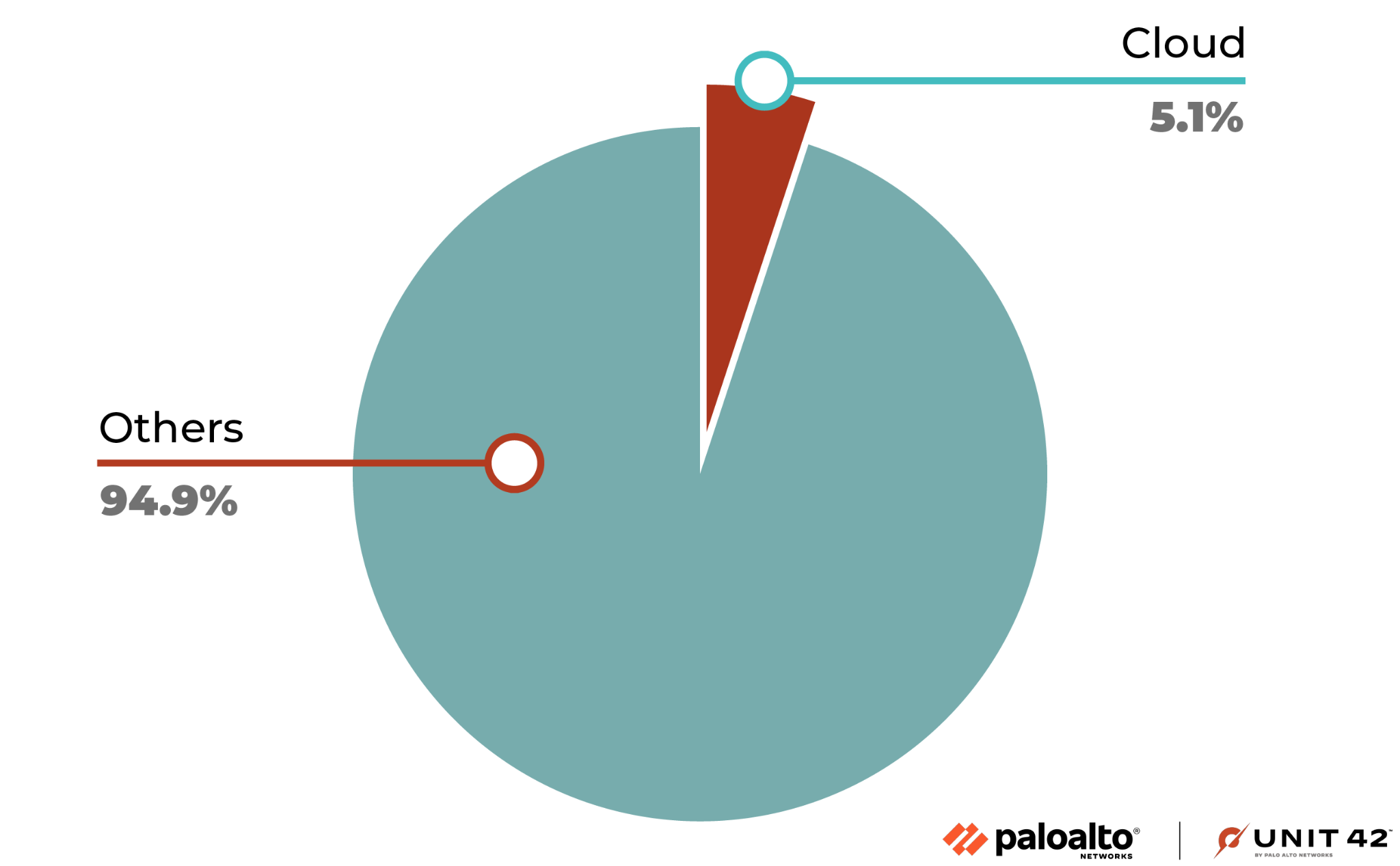
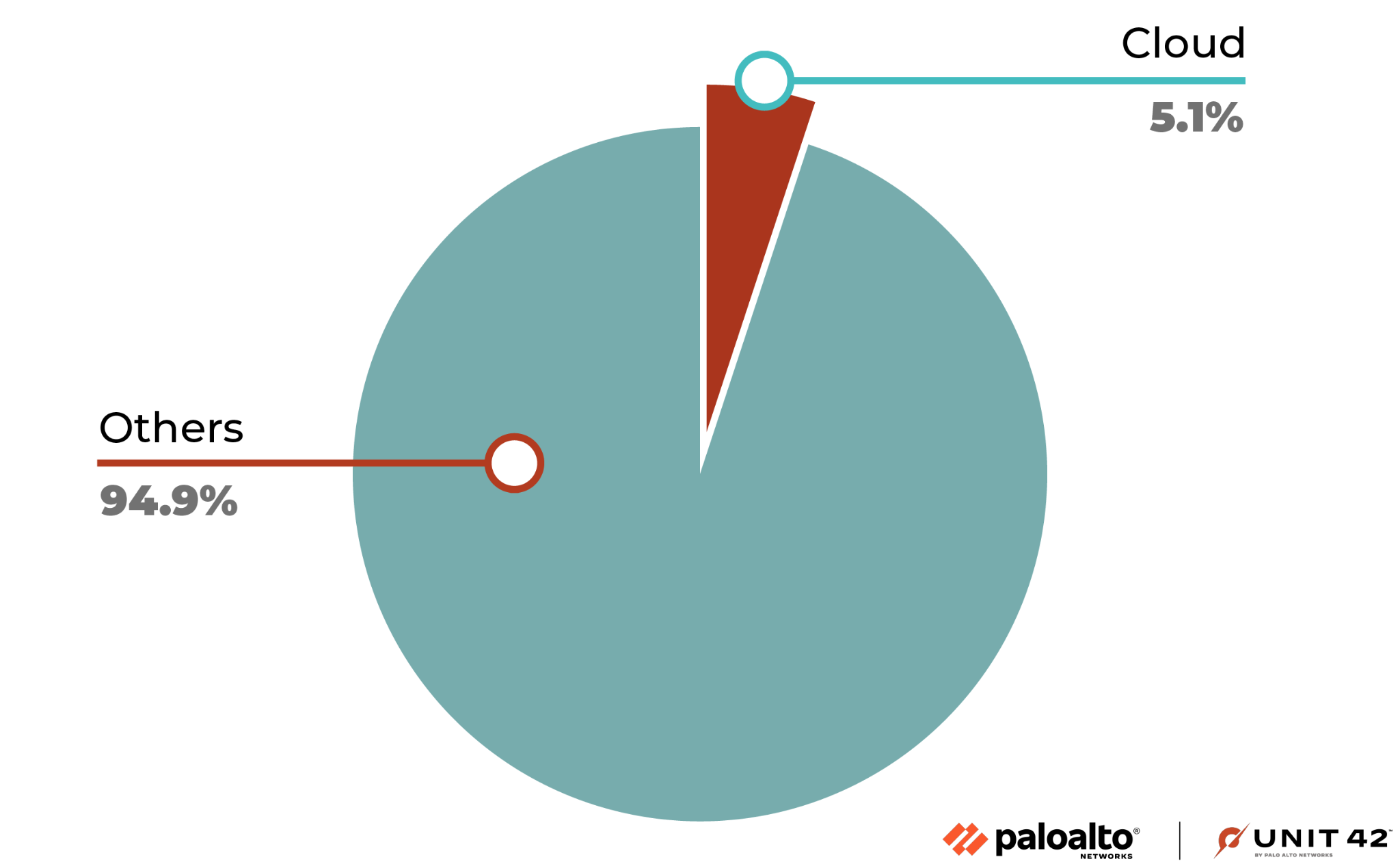
In the course of analyzing attacks on web applications and APIs, Unit 42 researchers placed special emphasis on determining the origins of these attacks. We discovered that 5.1% of the attacks were initiated from deployments hosted by the top three cloud service providers.
One plausible explanation for this high percentage is that attackers compromise legitimate cloud-hosted workloads and then use them as launch pads for further attacks. This tactic enables threat actors to spread their reach to other cloud environments, expanding the scope of their malicious activities.
Another potential reason is that some attackers may pose as legitimate users to gain access to cloud infrastructure. In order to do so, they could use free tiers offered by cloud vendors or use stolen credit card information to pay for cloud services. Once inside the cloud environment, these attackers can launch their attacks directly from within the cloud.
Conclusion
In light of this research, organizations must be vigilant in securing their cloud environments, ensuring proper configurations, and monitoring for potential threats. By understanding the risks and implementing robust security measures, businesses can better protect their web applications and APIs from cloud-based attacks.
As more businesses shift their web applications and APIs to the cloud, attackers might perceive these environments as attractive targets, offering a wealth of valuable data and resources. This trend underscores the importance of implementing robust security measures to safeguard cloud-hosted web applications and APIs.
Palo Alto Networks customers using Prisma Cloud are protected from these threats through the WAAS module, which is designed to protect web applications and APIs in cloud environments.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh