
Revisiting Insider Risk Programs in 2023
As the impact and cost of insider incidents continues to be on the rise, organizati
2023-5-8 20:48:1
Author: www.forcepoint.com(查看原文)
阅读量:17
收藏
As the impact and cost of insider incidents continues to be on the rise, organizations are reshaping how they manage insider risk programs.
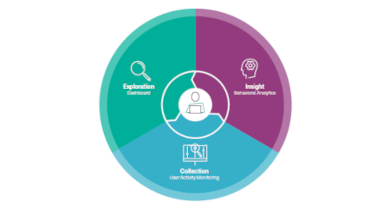
FIT Insider Risk Solutions
Forcepoint Insider Risk Solutions is a User Activity Monitoring
(UAM) and Analytics platform that provides analysts and
investigators with deep visibility into all user endpoint activity for
effective detection programs and resolving anomalous behavior.
Read the Datasheet
Evaluating the effectiveness of an Insider Risk Program
The Intelligence and National Security Alliance (INSA) states that “Establishing appropriate objectives and performance metrics supports business justifications for resources and ensures sustained buy-in and support from senior leadership and other key internal stakeholders.”
When implementing a new insider risk program or looking at existing programs in place, Program Managers and organizations are asking themselves some tough evaluative questions such as:
- Does our existing program identify and score riskiest users, their behaviors, and actions?
- Can our existing program determine if user credentials have been compromised or stolen?
- Do we know if workers are taking proprietary data with them when they leave the organization?
- Does the current program provide indicators for behaviors of workplace violence, self-harm, or sabotage before they occur?
- Are we collecting data on physical methods of data exfiltration, such as printing physical copies, copying content to removable media, taking screenshots, or using the clipboard to copy and paste proprietary information?
Answering these questions involves knowing what types of risky activities are of most concern to your organization. Some examples of insider activities that can pose great risk to your organization’s mission, reputation, and bottom line might include:
- Extremism, workplace violence, self-harm, and sabotage
- Media leaks, misinformation that can harm reputation and public perception
- Corporate espionage, customer data and PII spillage; theft of trade secrets
- Stolen Credentials
- Employees leaving and taking proprietary data with them
- Accidental or intentional systems disruption
- Supply chain disruption
- Fraud
Navigating and Managing Insider Risk
I recently did an educational webinar called Navigating and Managing Insider Risk. It contains useful guidance and information for how organizations can answer the questions above and manage insider risk. Learn how to structure an effective program and where to begin when implementing a new program or improving an existing program.
I also explain why point products that claim to be one-size-fits-all are not effective: Organizations should instead adopt a phased crawl, walk, run approach that focuses on their specific organizational needs. A phased approach that leverages the best practices, proven methodologies, and educational resources from the experts including thought leaders like the Intelligence and National Security Alliance (INSA), Carnegie Mellon, MITRE Labs, Applied Research for Intelligence and Security (ARLIS) and more.
Learn effective ways to manage, navigate and solve Insider Risk. Check out my recent webinar or review the Insider Risk Infographic for more.

Mike Crouse is the Director for Enterprise User and Data Protection at Forcepoint Global Governments and Critical Infrastructure. He works closely with industry thought leaders, executives, and the Forcepoint management team to help guide long-term programmatic and technology...
Read more articles by Mike Crouse
Forcepoint is the leading user and data protection cybersecurity company, entrusted to safeguard organizations while driving digital transformation and growth. Our solutions adapt in real-time to how people interact with data, providing secure access while enabling employees to create value.
文章来源: https://www.forcepoint.com/blog/insights/revisiting-insider-risk-programs-2023
如有侵权请联系:admin#unsafe.sh



