2023-5-3 20:37:4 Author: www.sentinelone.com(查看原文) 阅读量:40 收藏
Recent weeks have seen a number of macOS-specific infostealers appear for sale in crimeware forums, including Pureland, MacStealer and Amos Atomic Stealer. Of these, Atomic Stealer has offered by far the most complete package, promising cybercriminals a full-featured if not particularly sophisticated infostealer. Atomic can grab account passwords, browser data, session cookies, and crypto wallets, and in the version being advertised on Telegram, threat actors can manage their campaigns through a web interface rented out from the developer for $1000 per month.
The threat actor, however, has been busy looking for other ways to target macOS users with a different version of Atomic Stealer. In this post, we take a closer look at how Atomic Stealer works and describe a previously unreported second variant. We also provide a comprehensive list of indicators to aid threat hunters and security teams defending macOS endpoints.

How is Atomic Stealer Distributed?
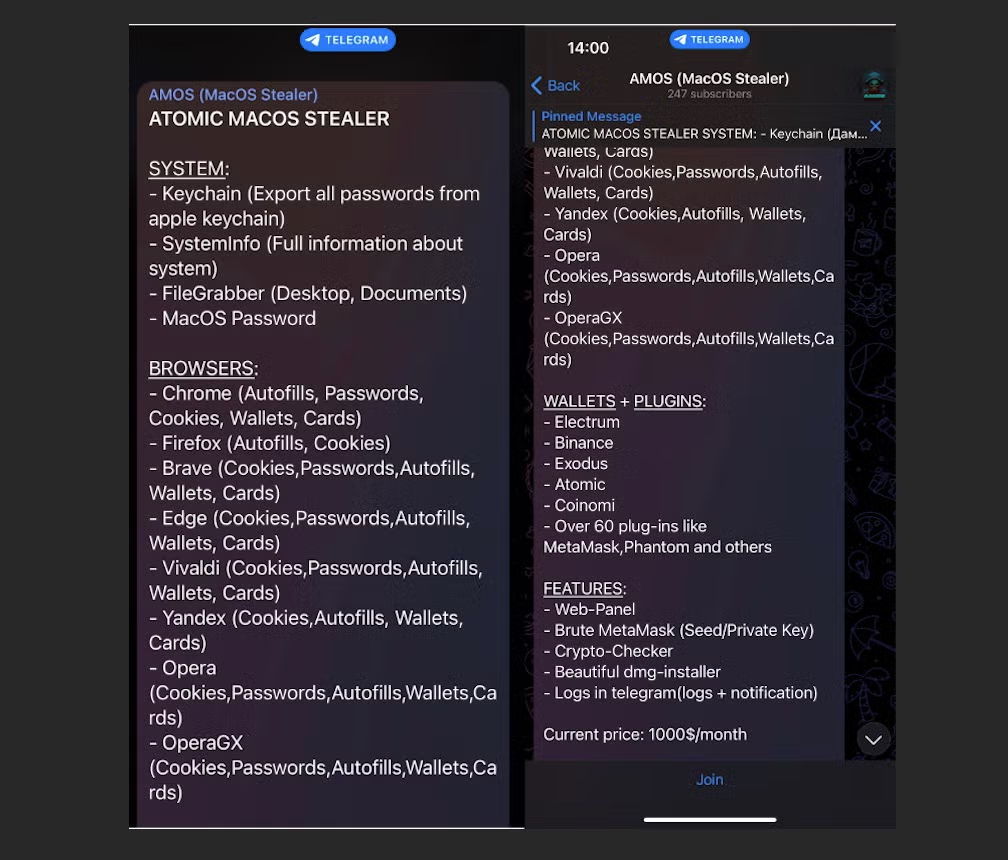
Cybercriminals are currently being offered “Amos Atomic MacOS Stealer” via a dedicated Telegram channel. In the channel, which was opened on April 9th, the author offers to rent access to a web panel and provide a disk-image based installer for $1000/month.
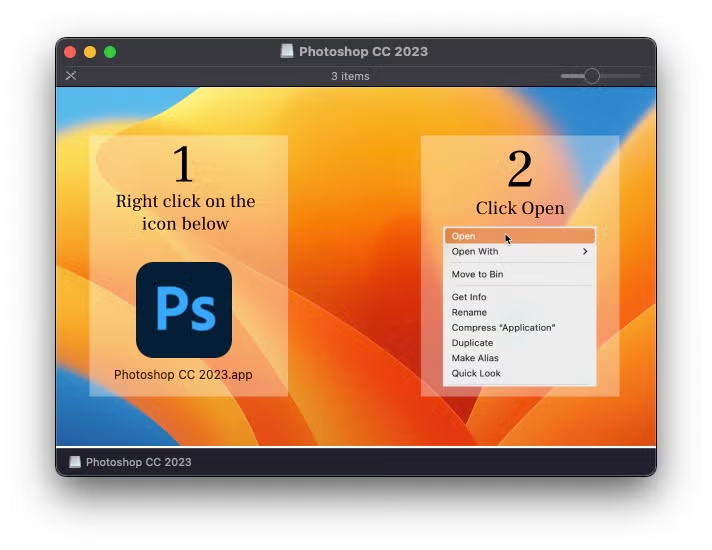
Payload distribution is left up to the crimeware actor renting the package, so methods vary, but so far observed samples have been seen masquerading as installers for legitimate applications like the Tor Browser or pretending to offer users cracked versions of popular software including Photoshop CC, Notion, Microsoft Office and others.
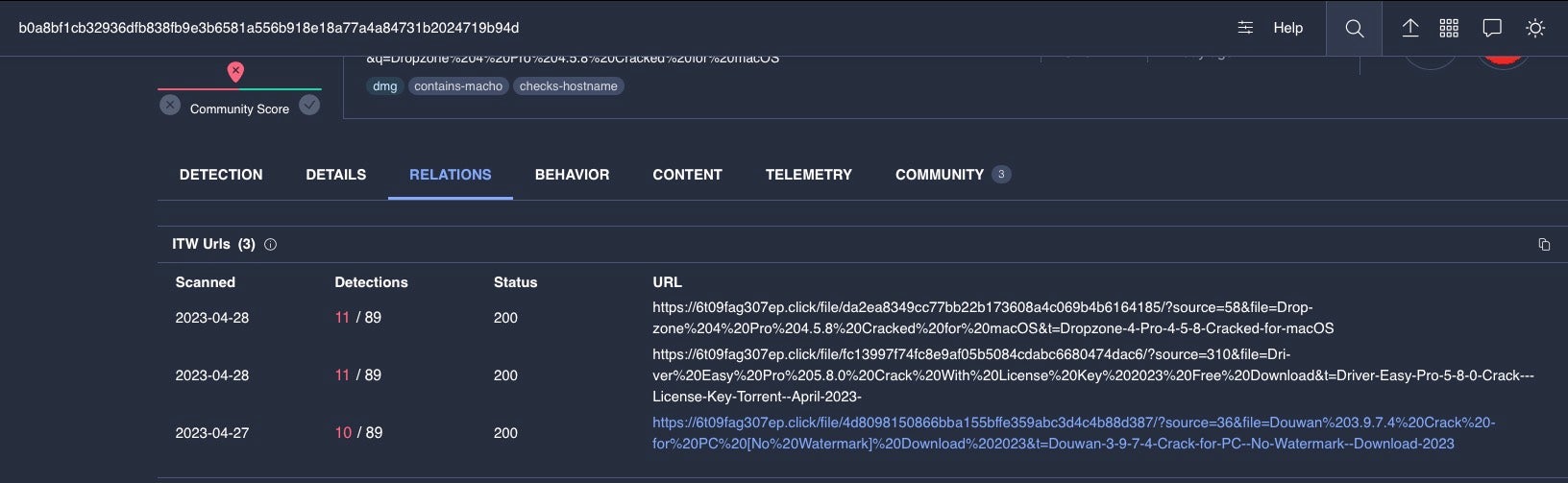
Malvertising via Google Ads has also been noted privately among researchers as a distribution vector for Atomic Stealer.
The Atomic Stealer channel currently has over 300 subscribers, with some posts – possibly planted – appearing to endorse the efficacy of the malware.
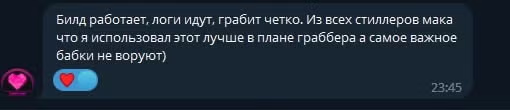
A Google translation of the Russian text reads “The build works, the logs go, it robs clearly. Of all the poppy stealers that I used, this one is better in terms of a grabber, and most importantly, grandmas do not steal)”.
Anatomy of Atomic MacOS Stealer Variant A
These fake applications are made with a fork of Appify, a legitimate script that can be found on Github for making a barebones macOS application. All Atomic infostealers currently contain the same Go-based main executable that weighs in at around 51.5MB as a Universal binary targeting both Intel and arm64 architectures.
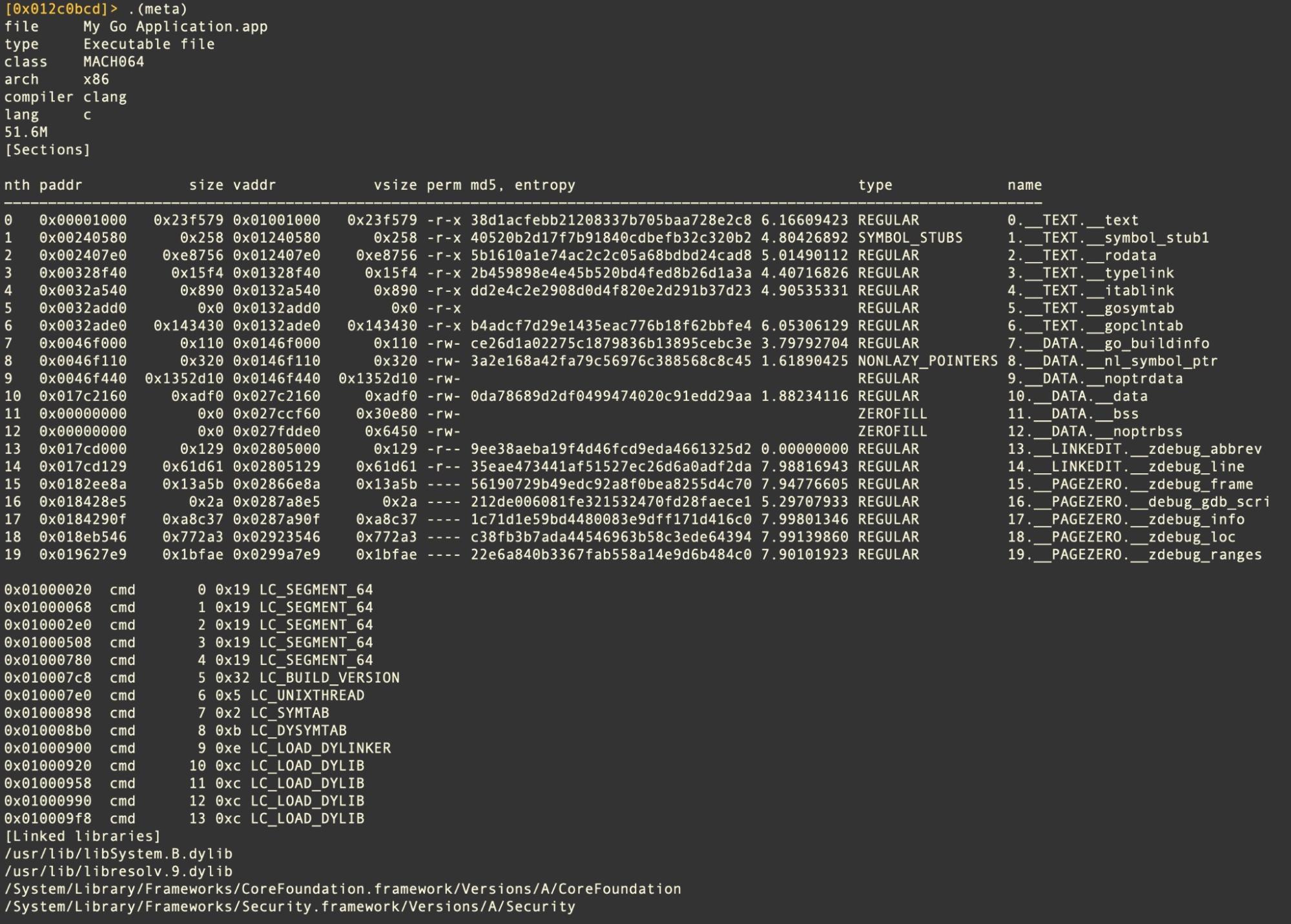
Despite the heft, no attempt has been made to deliver a working copy of the spoofed apps. Aside from the Appify README, the Bundle contains nothing more than the Go infostealing binary, an icon file and a Info.plist.
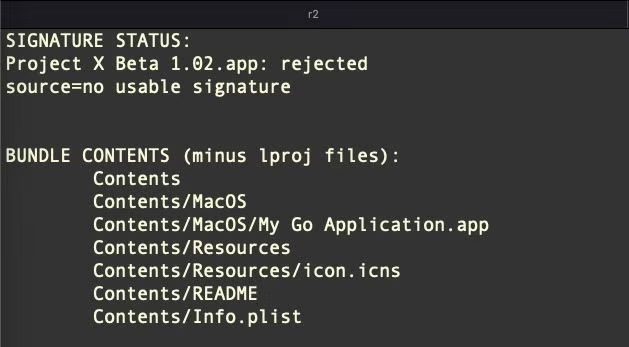
The application bundles currently being distributed are all built with the default Appify bundle identifier, Appify by Machine Box.My Go Application, potentially a deliberate ploy by the author in the hope that detections might be considered false positives.
Execution Behavior of Variant A
Atomic does not attempt to gain persistence, an increasing trend since Apple added login item notifications in macOS Ventura, relying instead on a one-hit smash and grab methodology.
Atomic Stealer uses a crude but effective means of extracting the user’s login password via AppleScript spoofing.
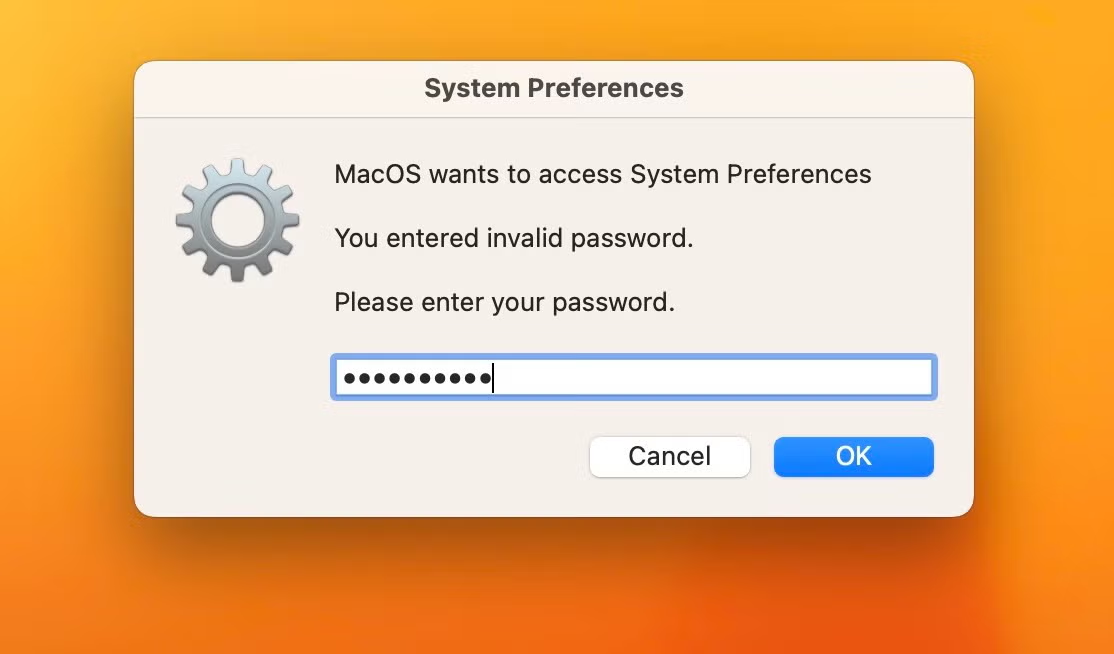
This involves creating a dialog box with osascript and passing the hidden answer parameter to the display dialog command. These dialog boxes contain an ordinary text field, but the parameter displays the user’s typed characters as dots in the text field similar to a genuine authentication dialog. However, the password remains captured in plain text and can be seen in the system logs as such – a good reason why legitimate software developers should never use this insecure method to actually obtain user credentials.
display dialog "MacOS wants to access System Preferences You entered invalid password. Please enter your password." with title "System Preferences" with icon file "System:Library:CoreServices:CoreTypes.bundle:Contents:Resources:ToolbarAdvanced.icns" default answer "" giving up after 30 with hidden answer ¬
The dialog box message contains grammatical and syntactic errors, suggesting the developer’s first language is not English. The dialog box is generated using an infinite loop: Clicking the “Cancel” button simply pops the dialog box again. If the “OK” button is clicked, the malware checks to see that the user entered a valid password via /usr/bin/dscl utility and the -authonly option.
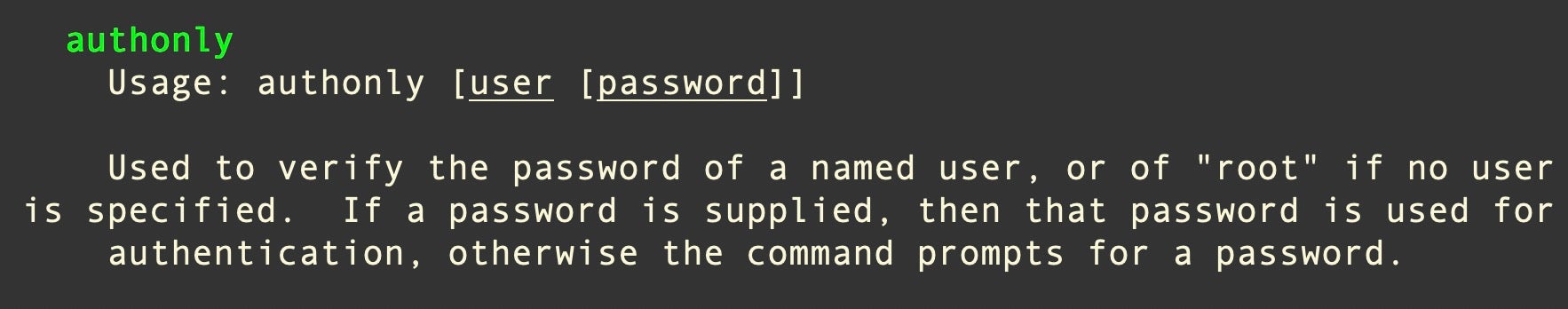
The dialog box repeatedly pops until the correct password is supplied. All of this occurs via the command line utility osascript, so it is easily visible to defenders monitoring command line activity.
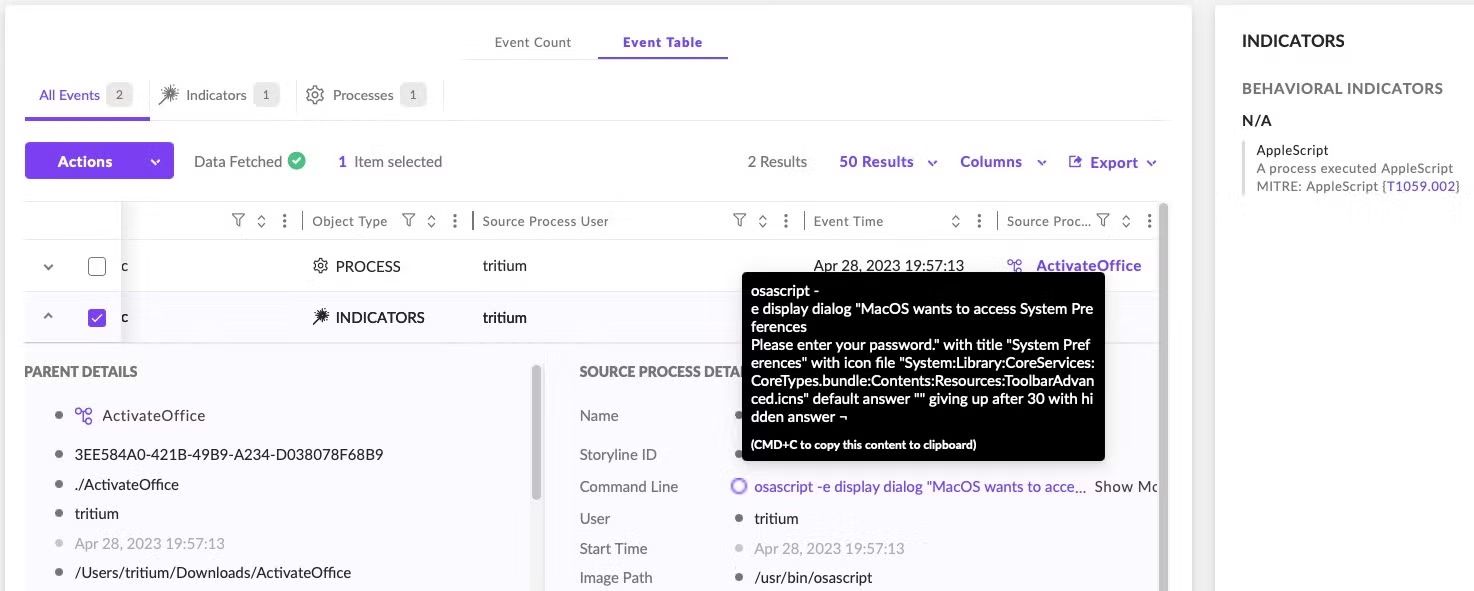
Amos Atomic is hardcoded to throw the user an error message after it has stolen the user’s password and gone about its business of stealing various credentials. Here and elsewhere, the malware author’s lack of familiarity with English and AppleScript provide clues that should raise suspicions: namely, the misspelling of “occurred” and the fact that a genuine error message shouldn’t contain a ‘Cancel’ button.
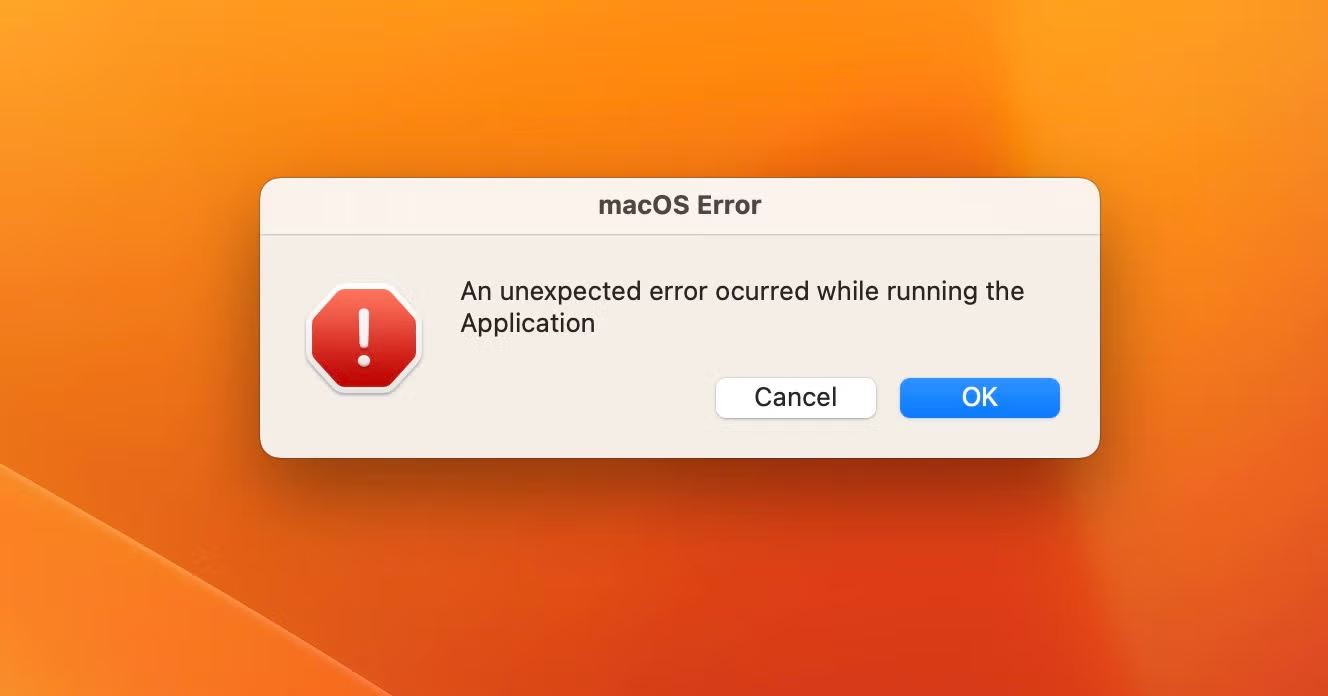
Written in Go, the disassembled source code reveals a comprehensive suite of functions to achieve the infostealers primary aim: financially-motivated cybercrime.
The malware contains logic to steal the user’s keychain and crypto wallet contents, including those for Atomic, Binance, Electrum and Exodus. A process called ‘unix1’ is spawned in memory to obtain the keychain. Atomic stealer also targets both Chrome and Firefox browsers and has an extensive hardcoded list of crypto-related browsers names to attack. A detailed walk through of the functions above has been previously described here.
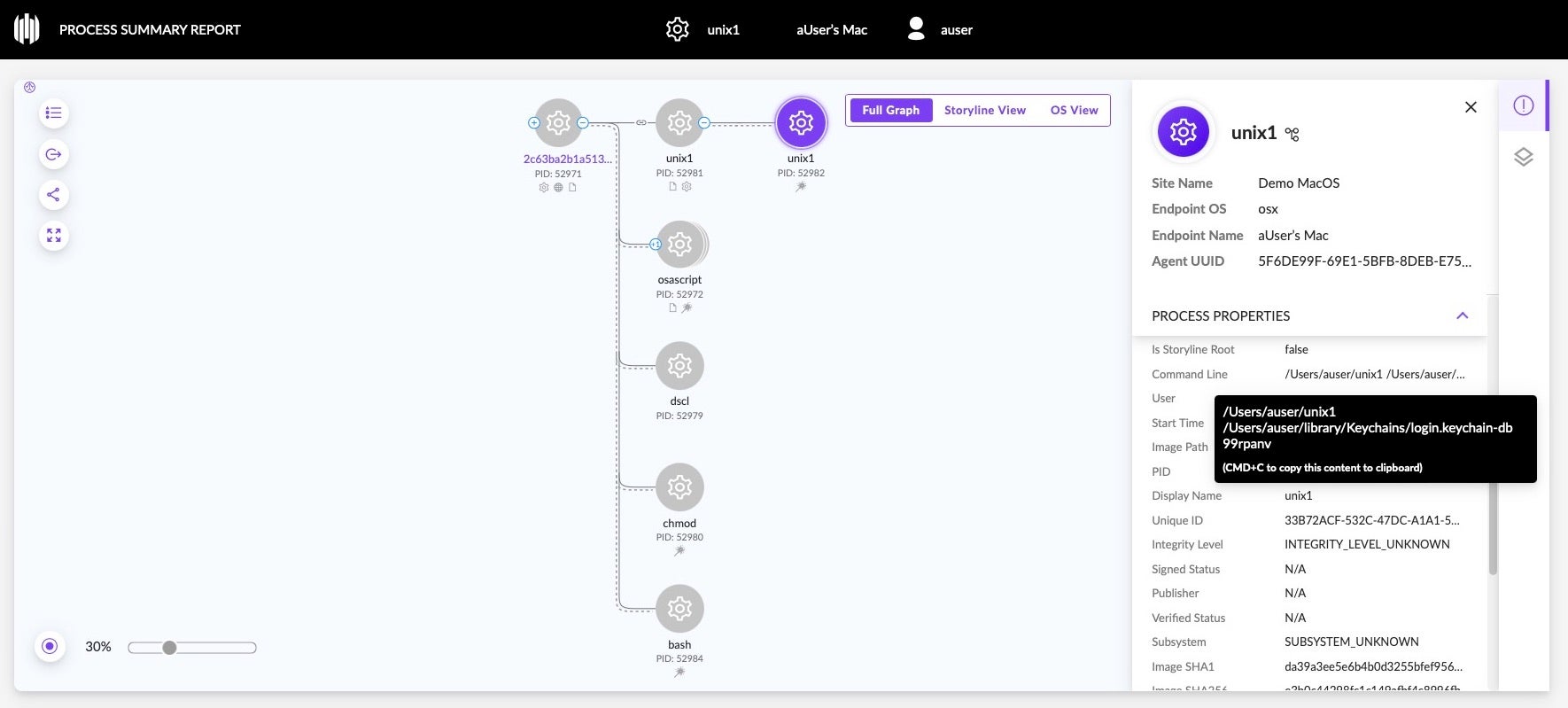
Atomic Stealer Variant B
Pivoting off the IP address 37.220.87.16 seen in some Atomic Stealer samples leads to another variant of the stealer, c70fdf4362eb56032793ab08e6aeb892f1bd4a9b, currently undetected on VirusTotal, masquerading as a Game Installer.
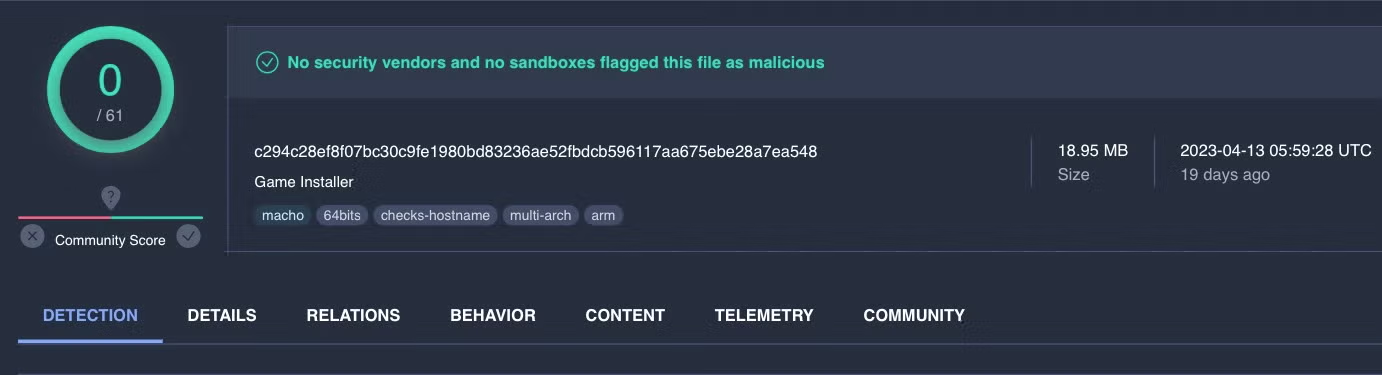
This version is not distributed in an application bundle, but rather as a raw Go binary. The unsigned “Game Installer” Mach-O was uploaded to VirusTotal on April 13th and is contained in a disk image called “ALMV_launcher”. The DMG mounts with the name “Game Installer” and contains a binary of the same name, displaying an icon showing the text “Start Game”.

As the universal binary is unsigned, it will need to be manipulated by the user on both Intel and arm64 architectures in order to run.
Variant B’s list of Go main functions differs from the version being packaged and sold on Telegram and shows a larger number of functions focusing on Firefox and Chromium browsers. Variant B also targets Coinomi wallets.
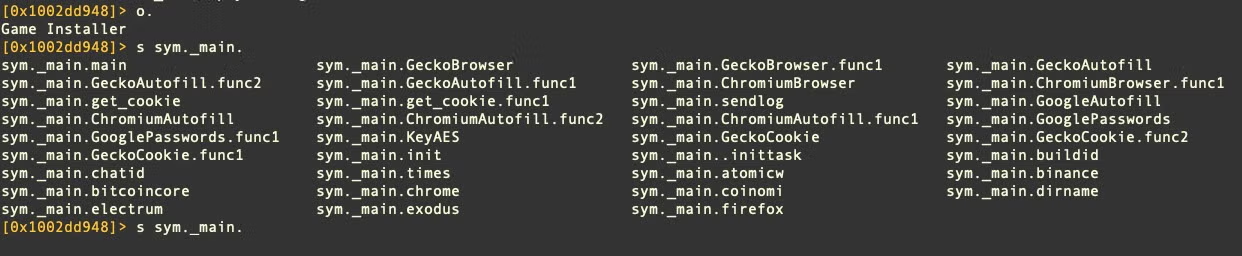
Both variant A and B utilize the /usr/bin/security utility to find Chrome passwords.
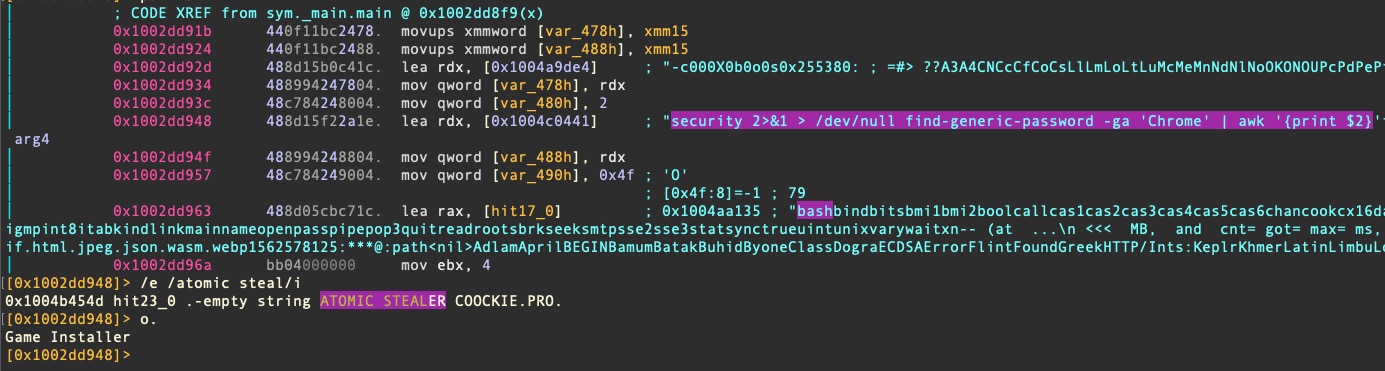
security 2>&1 > /dev/null find-generic-password -ga 'Chrome' | awk '{print $2}
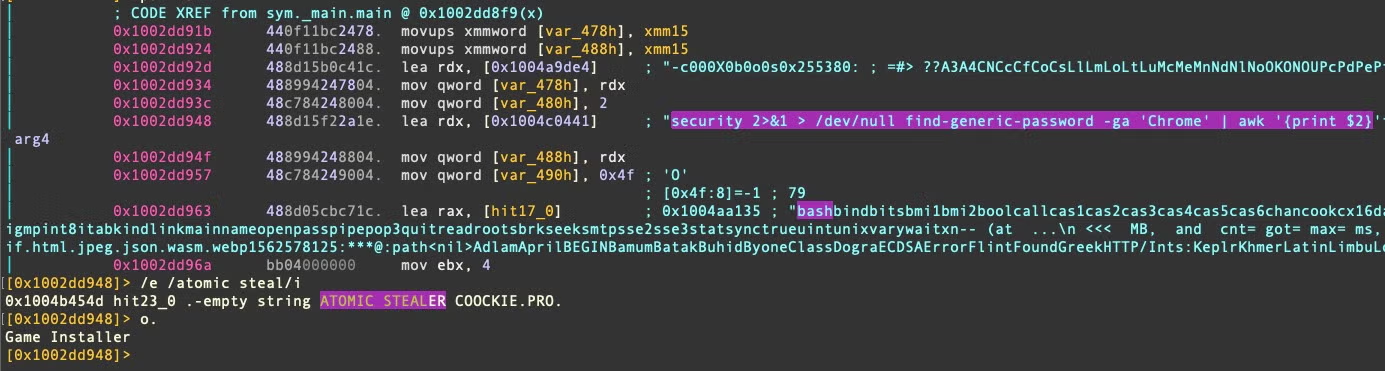
In Variant B, the user name “administrator” appears from the development machine; this differs from variant A, which included the username “iluhaboltov”. The string “ATOMIC STEALER COOCKIE” is also found in variant B but not A.
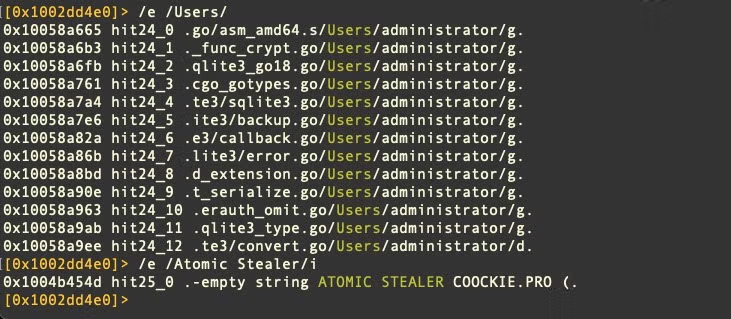
Unlike the package offered in the Atomic Telegram channel, this version of Atomic stealer is more selective in the information it tries to steal and seems to be aimed specifically at games and users of cryptocurrency.
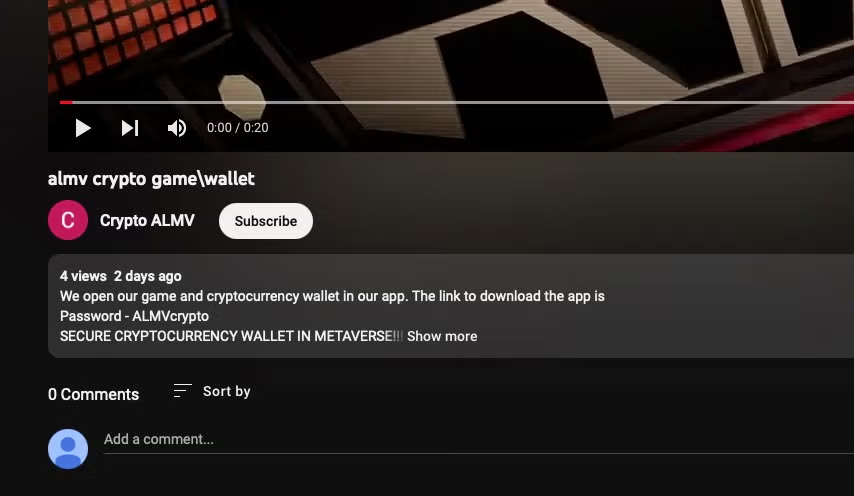
An associated Youtube channel by user @Crypto-ALMV was created on April 29th, apparently advertising a product that offers cryptowallet access within a game. The channel, user, and video appear to be in the early stages of development and may indicate a campaign that is yet to be launched.
How to Protect Against Atomic Stealer
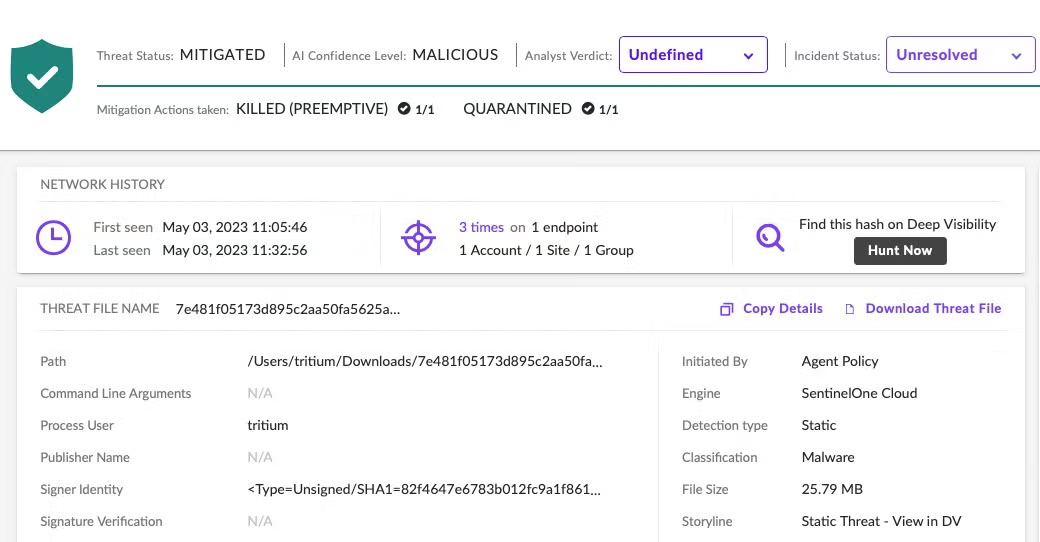
SentinelOne customers are protected against all known versions of Atomic Stealer. When the agent is set to ‘Protect’ mode, Atomic Stealer is prevented from executing.
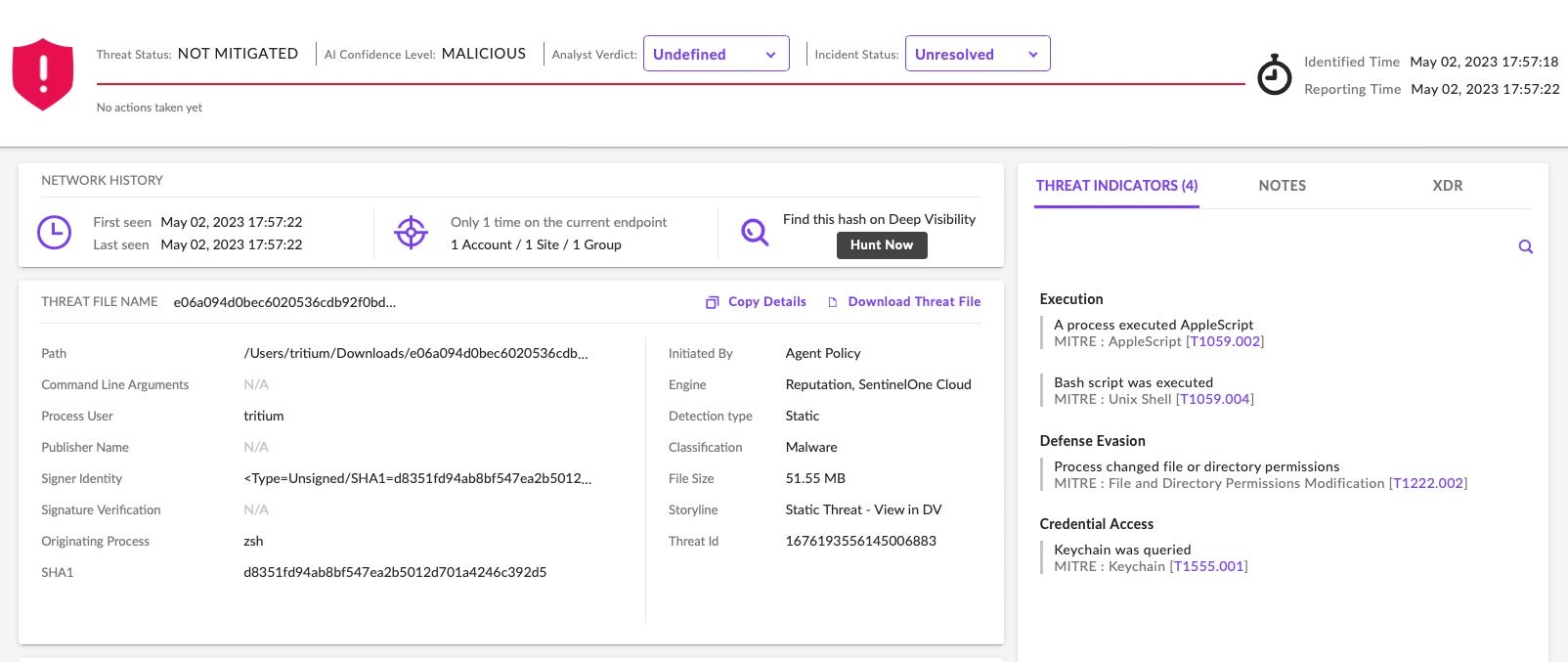
In Detect Only mode, the malware’s execution causes an alert and behavioral and threat indicators are available in the console.
Threat hunters and security teams not protected by SentinelOne are encouraged to review the list of Indicators of Compromise provided at the end of this post.
Conclusion
Infostealers targeted at Mac users have become increasingly viable for threat actors now that Macs have reached widespread use in organizations, both for work and personal use. As many Mac devices lack good external security tools that can provide both visibility and protection, there is plenty of opportunity for threat actors to develop and market tools to aid cybercriminals.
Atomic Stealer’s advertised price suggests there is money to be made by “selling shovels” as cybercrime actors rush for the ‘Gold’ of data that can be harvested by tricking users into running untrustworthy software. However, the existence of a second variant that appears to be aimed at infecting users first-hand suggests the threat actor isn’t averse to a bit of gold digging, too.
Indicators of Compromise
Communications
amos-malware[.]ru/sendlogillegal
37[.]220.87[.]16:5000/sendlog
SHA1 Variant A Mach-O
0db22608be1172844c0ebf08d573ea4e7ef37308
24c9f5c90ad325dae02aa52e2b1bac2857ae2faf
2681a24f0ec0b1c153cc12d5d861c0c19c8383ea
36997111b5e7aa81b430a72df9f54bac2a9695ba
385b9cc7d3147f049e7b42e97f242c5060fc9e97
46426409b9e65043b15ce2fcddd61213ff4e5156
48a0a7d4f0ae4b79b4f762857af3bbb02e8ab584
4f25d1a1aa18c8d85d555cd7a8f1cf2cf202af8c
58a3bddbc7c45193ecbefa22ad0496b60a29dff2
5d2e995fa5dce271ac5e364d7198842391402728
79007aabf9970e0aff7df52fd1c658b69f950c6f
793195d48cce96bb9b4fc1ee5bac03b371db75f7
82f4647e6783b012fc9a1f86108c644fcf491cf6
849cde22d1d188cc290bb527bbd7252ad07099af
9058ab6e05cb1f9ce77e4f8c18324a6827fb270d
97b19a82a32890d5ddaecac5a294cc3384309ea9
98f98a737a26c9dd1b27c474715976356ea4e18b
aab3a2897950e85a2b957f77d2f100e61e29061c
b42243d72765f142953bb26794b148858bff10a8
ca05f80fe44174d1089077f4b2303c436653226f
d5db5a11b9605d54cf66a153b0112b91c950d88f
d9d46ecfc1100d2b671ad97dc870e879d2634473
de465aad6cde9f0ce30fce0157bc18abf5a60d40
e114f643805394caece2326fb53e5d3a604a1aa9
f28025717f9db8a651f40c8326f477bf9d51a10f
SHA1 Variant B Mach-O
a02730f734032ed0f3b3705926b657aa4b88d720
c70fdf4362eb56032793ab08e6aeb892f1bd4a9b
e951b889aabca7ee5b0ff9d06a057884ed788b70
如有侵权请联系:admin#unsafe.sh