题目地址:malware-traffic-analysis-Unit 42 Wireshark Quiz, February 2023
https://unit42.paloaltonetworks.com/feb-wireshark-quiz/数据包下载地址
https://github.com/pan-unit42/Wireshark-quizzes/blob/main/2023-02-Unit42-Wireshark-quiz.pcap.zip数据包基础信息
The pcap for this month’s Wireshark quiz is from an AD environment,and it contains real-world traffic from a simulated enterprise setting.Details of the local area network (LAN) from the pcap follow.LAN segment range: 10.0.0[.]0/24 (10.0.0[.]0 through 10.0.0[.]255)Domain: work4us[.]orgDomain Controller IP address: 10.0.0[.]6Domain Controller host name: WORK4US-DCLAN segment gateway: 10.0.0[.]1Land segment broadcast address: 10.0.0[.]255
根据题目提示,数据包中内网网段为10.0.0.0/24,域控地址为10.0.0.6,网关为10.0.0.1
任务信息
Write an incident report based on the pcap.Our recommended incident report format contains the following three sections:1、Executive summary2、Victim details3、Indicators of compromise (IoCs)
需要根据数据包写一个事故调查报告,该报告包含三部分,第一部分介绍什么时间、什么主机、发生了什么时间;第二部分介绍详细的受害主机信息,包含主机名、IP地址、MAC地址、登录用户等;第三部分包含受害主机发起的IOC信息。
接下来开始解题
先过滤http相关流量
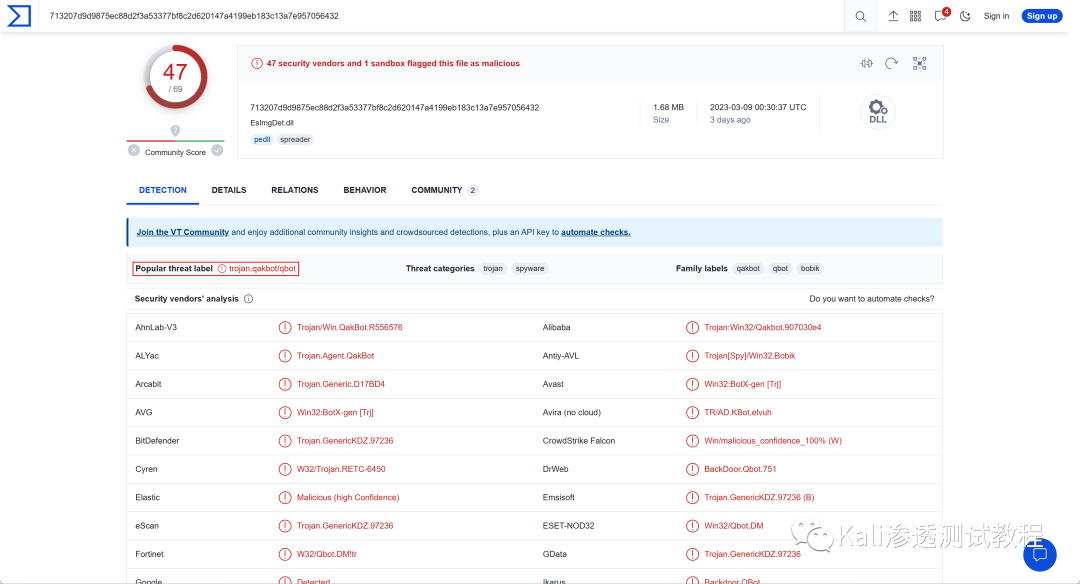
http数据包中http请求下载了一个二进制文件以及一个证书。将二进制文件放入VT中进行检测
检测木马家族为trojan.qakbot/qbot,可以确定受害主机为10.0.0.149。
接下来寻找该主机的详细信息
ip.src == 10.0.0.149 and kerberosip.src == 10.0.0.149 and samr主机10.0.0.149的MAC地址为00:21:5d:9e:42:fb,hostname为DESKTOP-E7FHJS4,用户名为damon.bauer。
接下来寻找数据包跟该木马相关的IoCs
tls.handshake.type eq 1 and !(tls.handshake.extension.type eq 0)根据目的地址梳理得到以下地址
5.75.205.43102.156.32.143208.187.122.74
综上所述:主机10.0.0.149在Feb 4, 2023 01:04:23.448359000 中国标准时间感染了trojan.qakbot/qbot木马。相关的IoCs为
5.75.205.43102.156.32.143208.187.122.74
主机10.0.0.149的MAC地址为00:21:5d:9e:42:fb,hostname为DESKTOP-E7FHJS4,用户名为damon.bauer。
本文数据包以及官网解题报告地址:
https://unit42.paloaltonetworks.com/feb-wireshark-quiz-answers/
文章来源: http://mp.weixin.qq.com/s?__biz=MzI3NDYwMzI4Mg==&mid=2247486304&idx=1&sn=7ba453e452a0ee875484d8b1f0ecaa41&chksm=eb10c71ddc674e0b86ecb8840dfd9e016fd6fb62cb5dd7fc7547e0ab44f6ccf4467623a016f9#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh