read file error: read notes: is a directory 2023-4-18 18:0:42 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:27 收藏

This post is also available in: 日本語 (Japanese)
Executive Summary
The cloud attack surface is as dynamic as the cloud itself. As organizations around the globe increasingly share, store and manage data in the cloud, this expands organizations’ attack surface exponentially. This expansion often happens in ways that are unknown, overlooked or improperly secured. For threat actors, each workload in the cloud presents an opportunity, and without proper management, organizations are exposed to risk in countless ways.
Where previous reports zoomed in on a single threat (e.g., identity access management, supply chain attacks and container security), the “Unit 42 Cloud Threat Report, Volume 7” zooms out to look at a bigger, more expansive problem: Threat actors have become adept at exploiting common, everyday issues in the cloud. These issues include misconfigurations, weak credentials, lack of authentication, unpatched vulnerabilities and malicious open source software (OSS) packages.
The report includes a breakdown of two separate real-world cloud breach incident response cases we observed in 2022. Anonymizing and de-identifying the victims, we illustrate how attackers took advantage of sensitive data leaked on the dark web and the business disruption caused by ransomware.
Below, we’ll present a sampling of the highlights of the research and recommendations in the “Unit 42 Cloud Threat Report, Volume 7: Navigating the Expanding Attack Surface.”
What we learned:
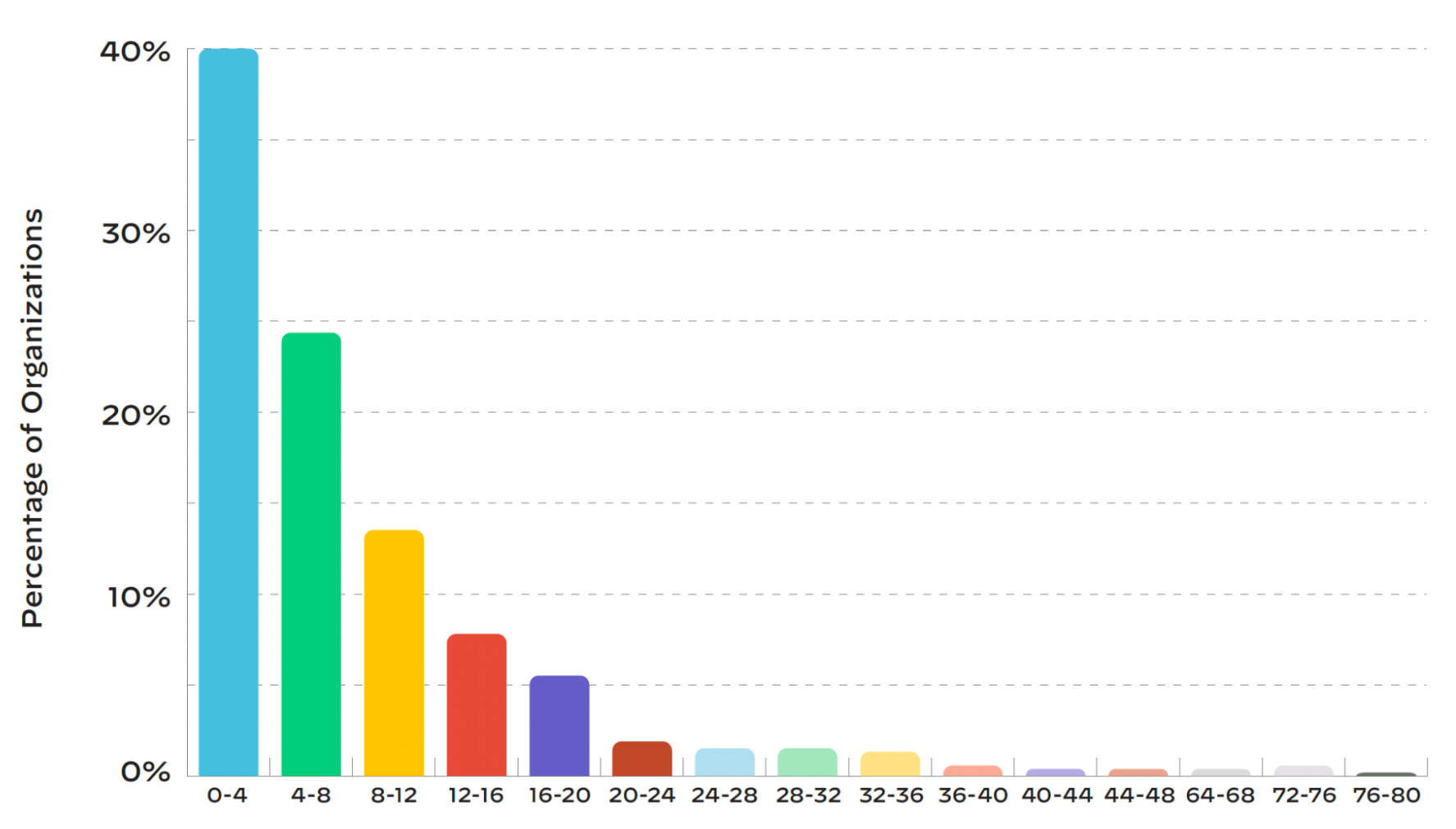
- On average, security teams take 145 hours (approximately six days) to resolve a security alert. 60% of organizations take longer than four days to resolve security issues.
- In most organizations' cloud environments, 80% of the alerts are triggered by just 5% of security rules.
- 63% of the codebases in production have unpatched vulnerabilities rated high or critical (CVSS >= 7.0)
- 76% of organizations don’t enforce MFA for console users, while 58% of organizations don’t enforce MFA for root/admin users.
Common Oversights in the Cloud
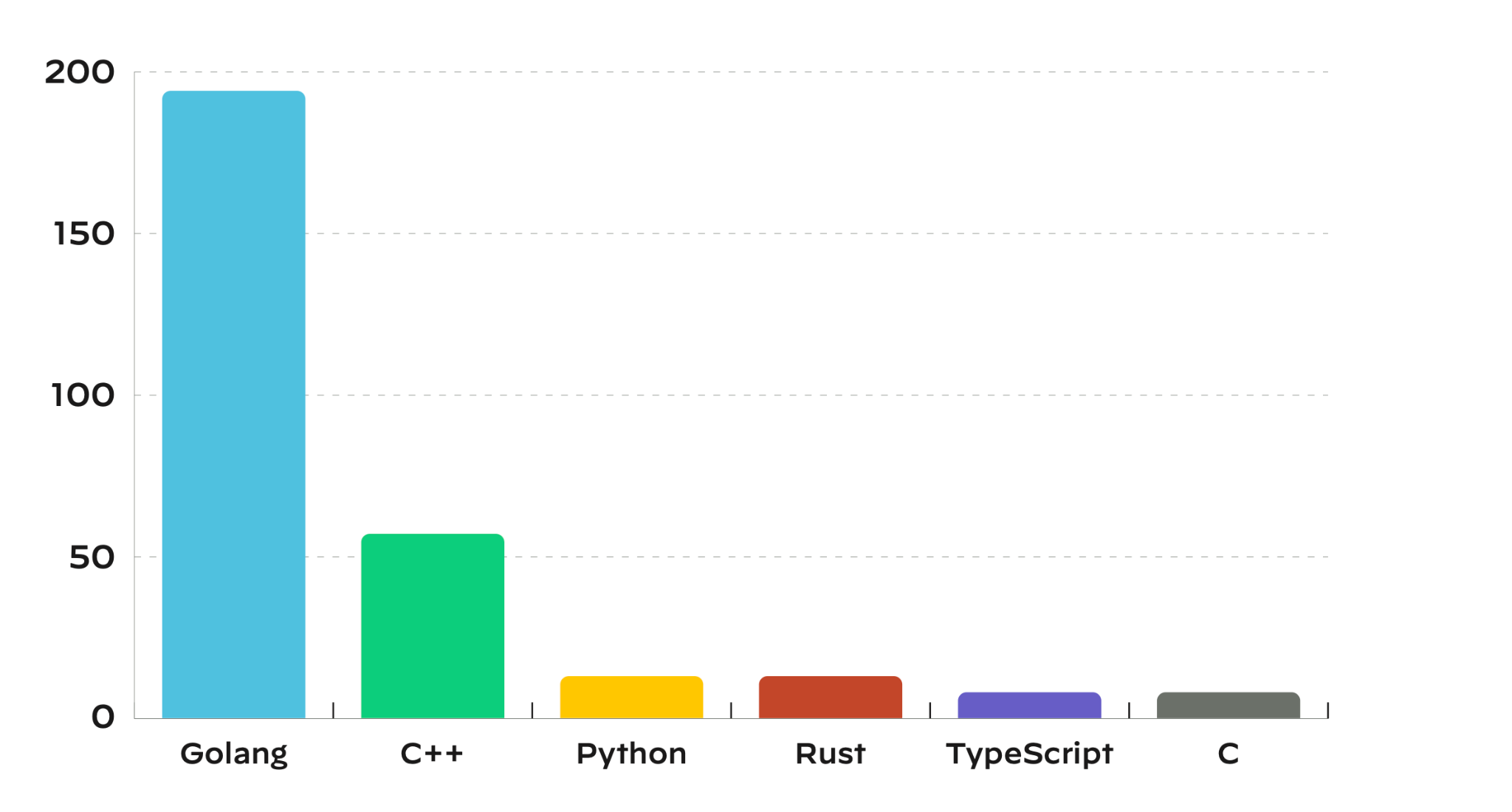
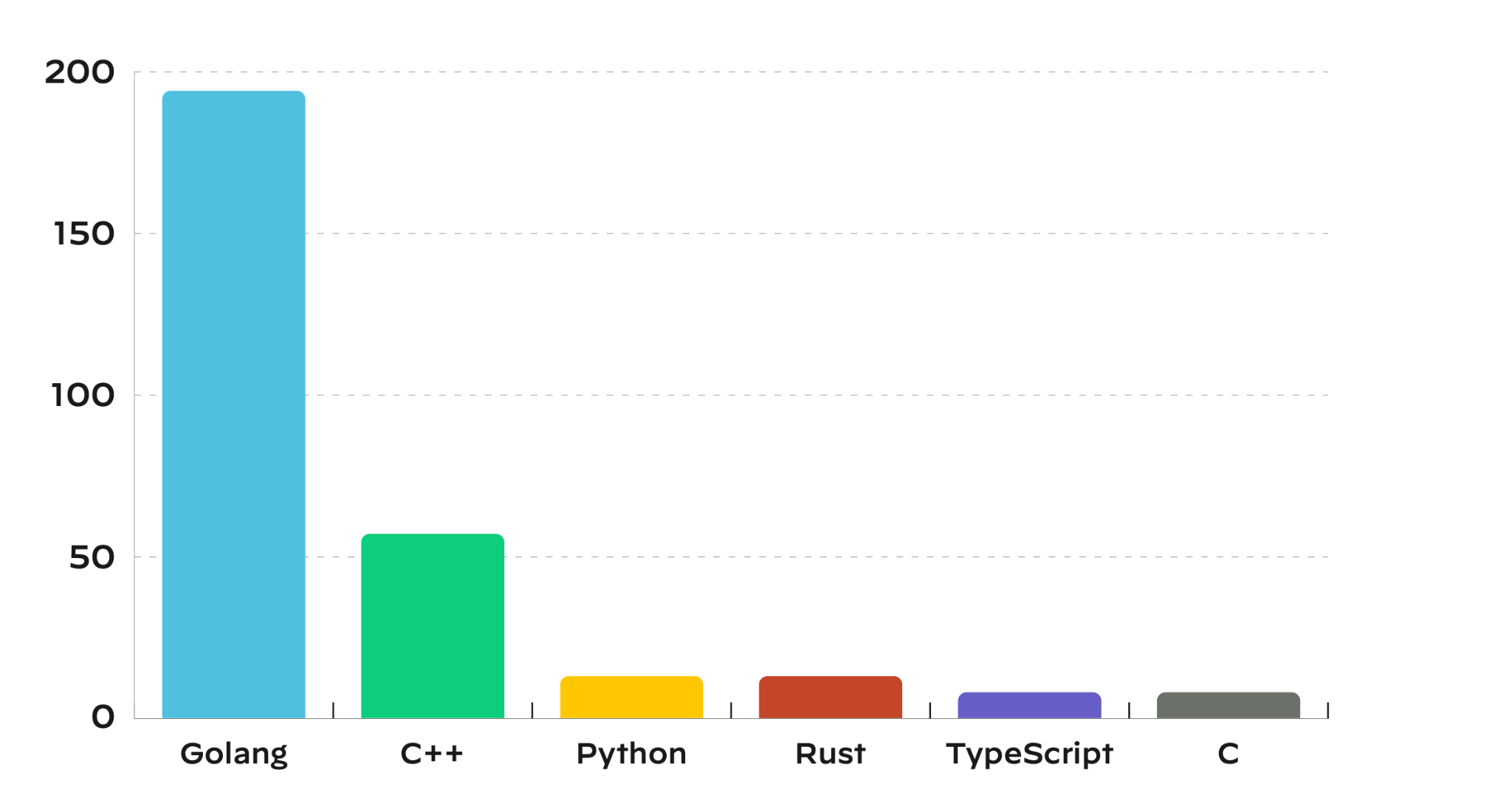
Using large-scale data collected in 2022, the report examines real breaches that impacted medium- and large-size companies, details the issues observed in thousands of multicloud environments, and analyzes the impact of OSS vulnerabilities on the cloud. In particular, we analyzed the workloads in 210,000 cloud accounts across 1,300 different organizations. With many organizations now having multiple cloud deployments, the gaps in security are getting more attention from threat actors.
While user errors, such as insecure configurations, are still the primary concern, Unit 42 researchers also noticed issues stemming from the ready-to-use templates and default configurations provided by cloud service providers (CSPs). These settings and features are convenient, making the adoption of new technologies frictionless, but they don’t position users in the most secure initial state.
Sample Findings:
- 76% of organizations don’t enforce MFA for console users.
- Sensitive data was found in 63% of publicly exposed storage buckets.
Impacts and Risks of Open Source Software (OSS) in the Cloud
Open source software has been one of the driving forces behind the cloud revolution. However, the increased use of OSS in the cloud also increases complexity—increasing the likelihood of depreciated or abandoned software, malicious content and slower patching cycles. This puts the onus on end users to scrutinize the OSS before integrating it into applications. This task is particularly challenging when organizations need to manage scores of projects that are all dependent on potentially thousands of OSS.
Recommendations: Making It Harder for the Threat Actors
Organizations should expect the attack surface of cloud-native applications to continue to grow as threat actors find increasingly creative ways to target the misconfiguration of cloud infrastructure, APIs and the software supply chain itself.
To guard against these threats, our report includes practical guidance for closing the gaps in your cloud security, such as the following:
Tip: There should be an automated backup process for any cloud workload that would interrupt business operations if it were to go down. Backups should be stored in protected locations isolated from the production environment across multiple geographic locations to prevent a single point of failure. All organizations should have business continuity and disaster recovery (BC/DR) plans that incorporate the process of recovering backups.
In addition, we predict the industry will see a shift away from point security solutions toward cloud-native application protection platforms (CNAPPs), which offer a full spectrum of capabilities across the application development lifecycle. Gartner echoes this assertion that there will be a significant uptick in CNAPP adoption, having reported a 70% jump in client inquiries regarding CNAPPs from 2021-2022.
As the report makes clear, the only way to defend against the changing scope and severity of today’s security threats is to always stay one step ahead of the attackers who are perpetrating them.
Download your copy of the “Unit 42 Cloud Threat Report, Volume 7.”
Additional Resources
- Gartner® Market Guide for Cloud-Native Application Protection Platforms - Palo Alto Networks
- Unit 42 Cloud Threat Report, Volume 6 - Palo Alto Networks
- The State of Cloud-Native Security Report 2023 - Prisma Cloud
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh