
2023-4-14 21:0:41 Author: www.sentinelone.com(查看原文) 阅读量:34 收藏
CVE-2023-21554 | Windows Admins Urged to Patch RCE Bug in MSMQ Service
A critical vulnerability included in this month’s Patch Tuesday roundup has caught the eye of cybersecurity researchers for its role in exposing hundreds of thousands of systems to attack. Dubbed “QueueJumper”, CVE-2023-21554 is found in Window’s Message Queuing (MSMQ) middleware service available on all Windows operating systems.
It’s a simple bug, unauthorized – anyone who could reach to 1801/tcp will be able to trigger the bug with a single packet. So patch patch! and check your firewalls to block untrusted connections!
— Haifei Li (@HaifeiLi) April 11, 2023
MSMQ technology is used by applications running at different times to communicate across networks and systems that may be temporarily offline. MSMQ works by effectively routing and securing messages, guaranteeing priority-based message delivery. In the hands of an attacker, CVE-2023-21554 enables unauthenticated remote code execution (RCE) on unpatched Windows servers through specially crafted malicious MSMQ packets.
Though it is an optional Windows service not enabled by default, it is often on in the background when installing enterprise apps and remains on even after uninstalling. Researchers note that more than 360,000 Internet-exposed servers running the MSMQ service are potentially vulnerable to attack, not including those that are not connected via Internet.
Though MSMQ sees low usage and has been end-of-lifed to make way for newer products like Azure Queue, it is still easily enabled via the Control Panel or PowerShell. Given the fact that this type of vulnerability is especially attractive to threat actors, it has been given an “exploitation more likely” tag referring to Microsoft’s exploitability index. Such RCE vulnerabilities are commonly used for initial access and malware deployment so require immediate attention.
Microsoft advises Windows administrators to disable the MSMQ service until the patch can be applied. Admins can also check to see if there is a service name “Message Queuing” running and if TCP port 1801 is listening on the machine.
Credential Theft | Legion Hacking Tool Circulates on Telegram
Researchers this week have reported on a new Python-based hacking tool and credential harvester named “Legion” that is snaking its way from buyer to buyer on Telegram. According to reports, the tool allows threat actors to break into various online services for further exploitation.

Reports indicate that Legion’s primary means of attack compromises misconfigured web servers running content management systems (CMS), PHP, or PHP-based frameworks. Once installed, Legion has been found to enumerate vulnerable SMTP servers, perform RCE attacks, exploit unpatched versions of Apache, brute-force cPanel and WebHost Manager (WHM) accounts, and abuse various AWS services.
The toolset then steals credentials from web services such as email providers, cloud services, server management systems, payment platforms, and databases. Other than extracting credentials, it can also implant webshells, create admin users accounts, and send SMS spam messages across customers of all U.S. telecom carriers.
Legion is also described as a modular malware, bearing resemblance to AndroxGh0st – a similar malware family first discovered in December of 2022. Security experts on the SentinelLabs team recently revealed that AndroxGh0st is part of a comprehensive toolset called AlienFox sold to actors intent on stealing API keys and cloud service secrets.
The development and use of cloud-focused toolkits for spamming and harvesting credentials are rising in popularity with cyber attackers. Multi-purpose credential harvesting tools will continue to be a major risk for any enterprises housing misconfigured or poorly managed web servers.
Transparent Tribe | Nation-State Adversary Targets Indian Education Sector
Suspected Pakistani-based hacking group known as Transparent Tribe has been linked to a series of attacks on the Indian education sector distinguished by its use of weaponized Microsoft Office documents to stage Crimson RAT malware. Also known in the cybersecurity community as APT36, Operation C-Major, PROJECTM, and Mythic Leopard, the group has been active since 2013 but has only recently set its sights on targeting schools since late 2021 before focusing on the Indian military and government sectors.
The Crimson RAT malware is capable of exfiltrating files and system data to servers controlled by the threat actor. Further, it captures screenshots, stops running processes, and executes additional payloads to log keystrokes and steal browser credentials. SentinelLab’s latest report details findings pertaining to the cluster of Office documents used by Transparent Tribe to contain the Crimson RAT malware.
The documents have been seen making use of OLE embedding to stage the malware. Needing users to double-click a malicious element in the document, the documents distributed by Transparent Tribe trick users to perform the action by displaying a ‘View Document’ prompt, as if to unlock the document’s content. Double-clicking then activates the OLE package that stores and deploys the Crimson RAT, which is masqueraded as an update.
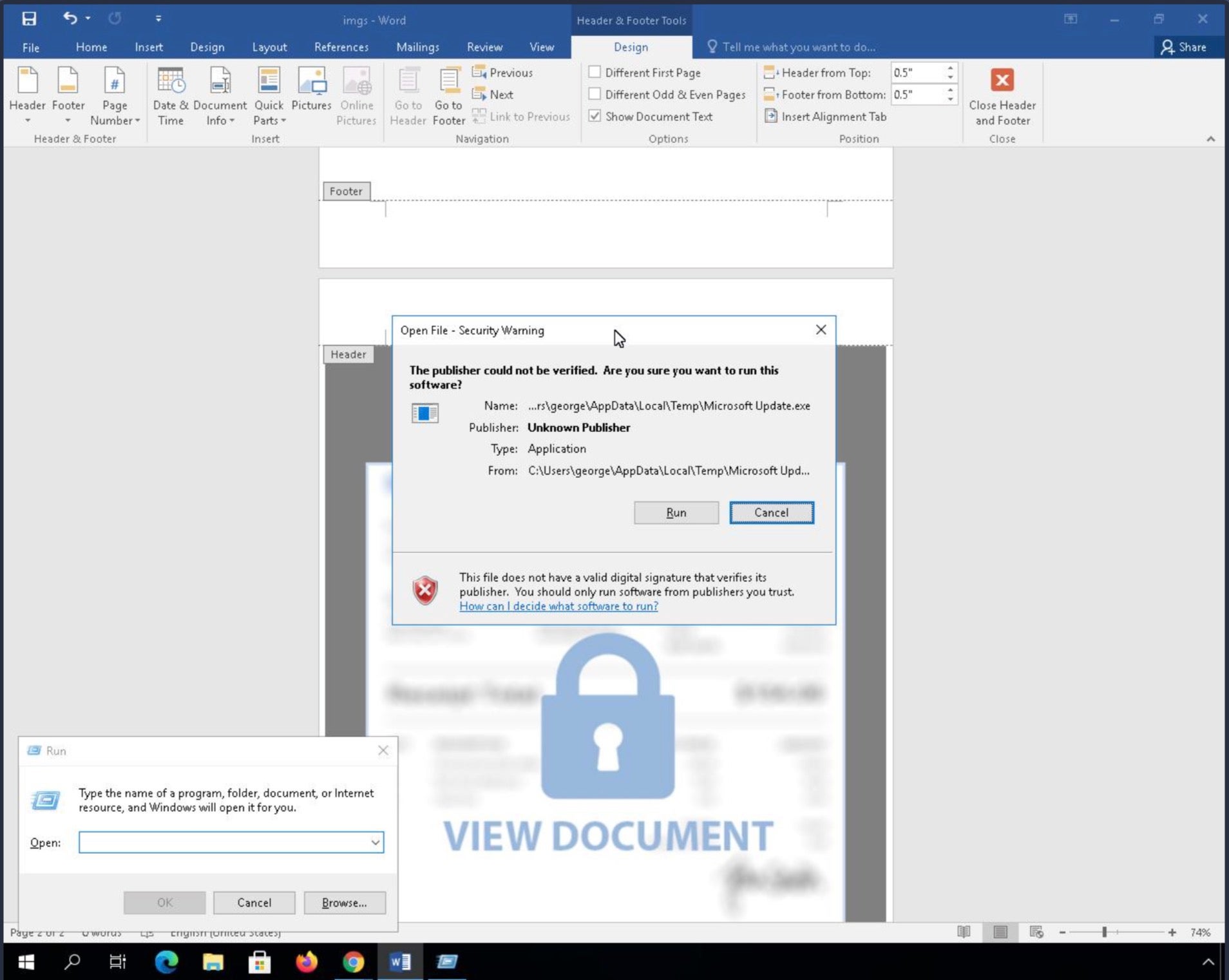
Based on the associated domains and use of Crimson RAT, cyber researchers at SentinelLabs note that the recent series of attacks on the Indian educational vertical are likely part of a previously reported campaign by the same actors. This suggests that Transparent Tribe is a highly motivated and persistent threat actor that operates by regularly updating their targeting strategies, malware arsenal, and operational playbook.
如有侵权请联系:admin#unsafe.sh