
In July 2021 the Cybersecurity and Infrastructure Security Agency (CISA) released its original 2023-4-13 19:28:54 Author: www.forcepoint.com(查看原文) 阅读量:20 收藏
In July 2021 the Cybersecurity and Infrastructure Security Agency (CISA) released its original Zero Trust Maturity Model for agencies in accordance with Executive Order (EO) 14028 “Improving the Nation’s Cybersecurity” § (3)(b)(ii),1 which required that agencies develop a plan to implement a Zero Trust Architecture (ZTA). This week, CISA has officially released an updated Zero Trust Maturity Model 2.0 that further clarifies guidance and milestones required for agencies to achieve an optimal Zero Trust state. CISA has been charged with leading the nation’s effort to understand, manage, and reduce cybersecurity risk, including by supporting Federal Civilian Executive Branch agencies in evolving and operationalizing cybersecurity programs and capabilities, so their definitions and milestones are important for agencies who are progressing toward Zero Trust.
While the latest Zero Trust Maturity Model is specifically tailored for federal agencies, CISA recommends all organizations should review and consider adoption of the approaches outlined in the latest Zero Trust Maturity Model. CISA also suggests that while there are many paths that an organization can take in designing and implementing their transition plan to zero trust architectures this Maturity Model provides further guidance for organizations to achieve increased resiliency and protection against emerging threats and advisories. Outcomes with successful adoption of the model are designed to lead to improved productivity, enhanced end-user experiences, reduced IT costs, flexible access, and bolstered security.
Achieving Optimal Zero Trust
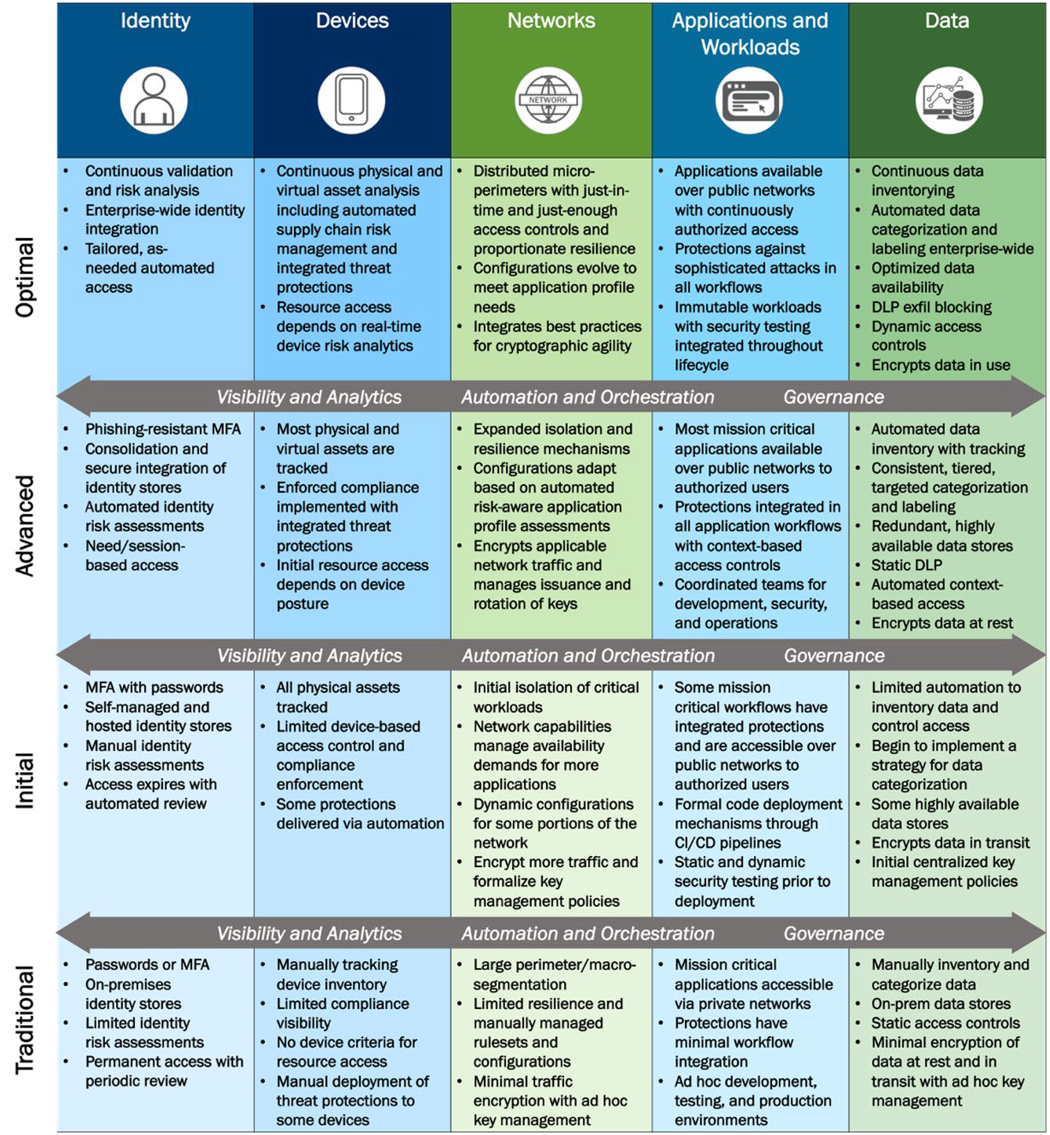
In the 2021 Zero Trust Maturity Model, CISA still points users to the NIST definitions and tenants of Zero Trust as underlying guidance of what Federal entities must build. The whitepaper continues to define 5 pillars agencies must evolve to achieve optimal Zero Trust, including Identity, Devices, Networks, Applications and Workloads, and Data. Each pillar also continues includes general details regarding how Visibility and Analytics, Automation and Orchestration, and Governance capabilities are required to support integration with each pillar and across their ecosystem. In 2021, CISA defined organizational milestones moving from traditional to advanced to later optimal capabilities to achieving Zero Trust.
In the latest 2023 model, CISA defines an optimal Zero Trust state is described as a “fully automated, just-in-time lifecycles and assignments of attributes to assets and resources that self-report with dynamic policies based on automated/observed triggers; dynamic least privilege access (just-enough and within thresholds) for assets and their respective dependencies enterprise-wide; cross-pillar interoperability with continuous monitoring; and centralized visibility with comprehensive situational awareness.” The new maturity model further clarifies what optimal should look like as well as the milestones on a path to this level of Zero Trust maturity. CISA has added to the model initial steps organizations moving toward Zero Trust should take and adds more detail around what the progress stages represent.
Defining new benchmarks and capabilities for an optimized Zero Trust state
New functions required to achieve zero trust are identified and defined in the new version of the Zero Trust Maturity Model under each pillar. Under the identity pillar a new function of access management is define where in an optimal Zero Trust state an agency will use automation to authorize just-in-time and just-enough access tailored to individual actions and individual resource needs. Under Devices, 3 new functions were identified where Policy Enforcement & Compliance Monitoring, Asset & Supply Chain Risk Management, and Device Threat Protection. When it comes to networks, 2 new function of Network Traffic Management and Network Resilience were added. Under applications and workloads, a Secure Application Development and Deployment Workflow function was defined where optimally an agency must leverage immutable workloads where feasible, only allowing changes to take effect through redeployment, and removes administrator access to deployment environments in favor of automated processes for code deployment. Under devices 2 new functions were defined including Data Categorization and Data Availability.
Importantly, the cross-cutting capabilities for optimal Zero Trust were also further defined in the new model. In an optimal Zero Trust state, an agency must achieve a visibility and analytics function that maintains comprehensive visibility enterprise-wide via centralized dynamic monitoring and advanced analysis of logs and events. Automation and orchestration would optimally achieved when orchestration and response activities dynamically respond to enterprise-wide changing requirements and environmental changes. Then optimal governance would mean an agency has implemented and fully automated enterprise-wide policies that enable tailored local controls with continuous enforcement and dynamic updates.
The challenges ahead for agencies adopting Zero Trust
Aside from budget, breaking down silos and delivering the cross-cutting capabilities to achieve Zero Trust is likely the biggest challenge to agencies as they work toward achieving optimal Zero Trust milestones. CISA points out in the newest guidance that one of the keys to effective Zero Trust will be the collaboration of stakeholders across IT from senior leadership to IT staff. CISA states for “agencies to transition stove-piped and siloed IT services and staff to coordinated and collaborative components of a Zero Trust strategy with agency-wide buy in for a common architecture and governance policies.” This also includes collaborating on current and future plans to adopt cloud technologies.
CISA acknowledges in the latest maturity model that organizations adopting Zero Trust have many different architectures and starting points they are coming from to achieve Zero Trust. The paper suggests that “the path to zero trust is an incremental process that may take years to implement” and have designed the model to allow for and defines a gradual evolution to Zero Trust, distributing costs over time rather than entirely upfront. The model also acknowledges that agencies should make decisions based on factors which include risk, mission, federal requirements, and operating constraints. There is not a single vendor product or solution agencies can buy off the shelf that will achieve Zero Trust. Not having a single answer or approach for Zero Trust for agencies adopting Zero Trust ensures that agencies can leverage existing technology and have flexibility in their approach toward Zero Trust, but it also means that every agency must consume this guidance and map out what technologies and capabilities they must achieve and develop their own plans toward achieving Zero Trust. As more clarity and detail of milestones agencies must achieve to reach an optimal Zero Trust state continue to come out, the milestones on the road to Zero Trust for agencies who are trying to transform becomes longer.
Federal agencies have additional complexity that commercial entities do not face when dealing with the need to share data across classified an unclassified environments as securely as possible. There has been confusion among some agencies regarding how Cross Domain solutions will exists in a future where Federal Zero Trust requires management, edge protection, data protection, and risk profiles across all domains, networks, and environments. The importance of how cross domain solutions must uniquely enable Zero Trust is to date not addressed in Federal models, however the NSA has clarified recently in the National Security Agency Cybersecurity Information Sheet: Advancing Zero Trust Maturity Throughout the User Pillar document that “Zero Trust mechanisms do not remove requirements for cross-domain solutions, especially when information sensitivity differences create excessive risk or when maturity levels vary widely.” Watch this webinar to learn more about how agencies must plan for multi-level Zero Trust protection.
What are the next steps for agencies?
As agencies digest the latest Zero Trust guidance, the challenge lies in effectively transforming their operations. Here are some crucial steps to consider:
- Create an Accurate IT Inventory: The Federal CIO Council Handbook highlights that many agencies still lack a complete and accurate inventory of IT assets and services, including mission systems, across their enterprise. To achieve Zero Trust, agencies must map their existing technologies to Zero Trust requirements, identify redundancies, and determine which products are incompatible with their long-term strategy. This is a critical step for success.
- Break Down Silos: Eliminating silos and fostering collaboration among leadership is essential for transformation. Addressing this long-standing challenge requires retraining the workforce to be open to change and replacing outdated technologies. Federal leadership must consistently support and encourage this change to achieve Zero Trust goals.
- Develop a Flexible Zero Trust Migration Plan: Agencies need to use the current guidance to create a Zero Trust migration plan tailored to their mission, requirements, and context. This plan should be adaptable as the landscape evolves over the next five years. The latest DOD Zero Trust strategies and roadmaps offer more detailed guidance for agencies seeking a starting point for their migration plans.
- Secure Funding for Zero Trust: Allocating funds for Zero Trust transformation can be challenging, particularly when dealing with a complex stack of existing technologies. To successfully migrate to Zero Trust, agencies must establish short-term and long-term milestones, align budgets for technology transitions, and maintain flexibility throughout the process. Begin by investing in areas that are easier to understand and adopt, then plan for distributing and funding costs over time.
In conclusion, preparing for Zero Trust requires a strategic approach that focuses on accurate IT inventory, breaking down silos, creating a flexible migration plan, and securing funding. By taking these actions, agencies will be better positioned for success in their Zero Trust transformation journey.
Download the latest report from Forcepoint to learn about additional challenges agencies face as they adopt Zero Trust.
Here's an infographic that maps the timeline of the Federal Quest for Zero Trust:

如有侵权请联系:admin#unsafe.sh