
Enterprise security teams are responsible for the overwhelming task of evolving their organization’ 2023-3-14 21:24:15 Author: www.sentinelone.com(查看原文) 阅读量:15 收藏
Enterprise security teams are responsible for the overwhelming task of evolving their organization’s defenses to keep pace with ever-changing threats. As a result, it’s often difficult to measure the effectiveness of their current cybersecurity measures and determine whether or not progress has been made – let alone stay on top of new, emerging risks to their environment.
At SentinelOne, we’re committed to the success of our customers, not just as a technology provider and platform. We want to ensure that we’re also delivering the knowledge, insight, and resources security programs need to succeed.

Today, we’re introducing a new home to our Global Support & Services reporting capabilities, all accessible through the SentinelOne Customer Community. The Community offers our customers a centralized, collaborative environment to receive help and insight into their SentinelOne deployment, understand the performance and efficacy of their MDR service, and understand what steps can be taken to improve the overall health and security posture of their environments. Customers can also network amongst themselves in groups or access a full library of onboarding videos.
In this post, we’ll highlight how security teams, no matter where they are in the world, can use the reports and resources available through the Customer Community to uplevel their cybersecurity programs.
Seamlessly Manage Your Security Estate with the Enterprise Deployment Report
Our reporting capabilities pull in data from across a customer’s security estate to give security leaders and analysts a comprehensive overview of their deployment. By tracking the number of active agents, teams can track the rollout of Sentinel Agents across their endpoint fleet over time.
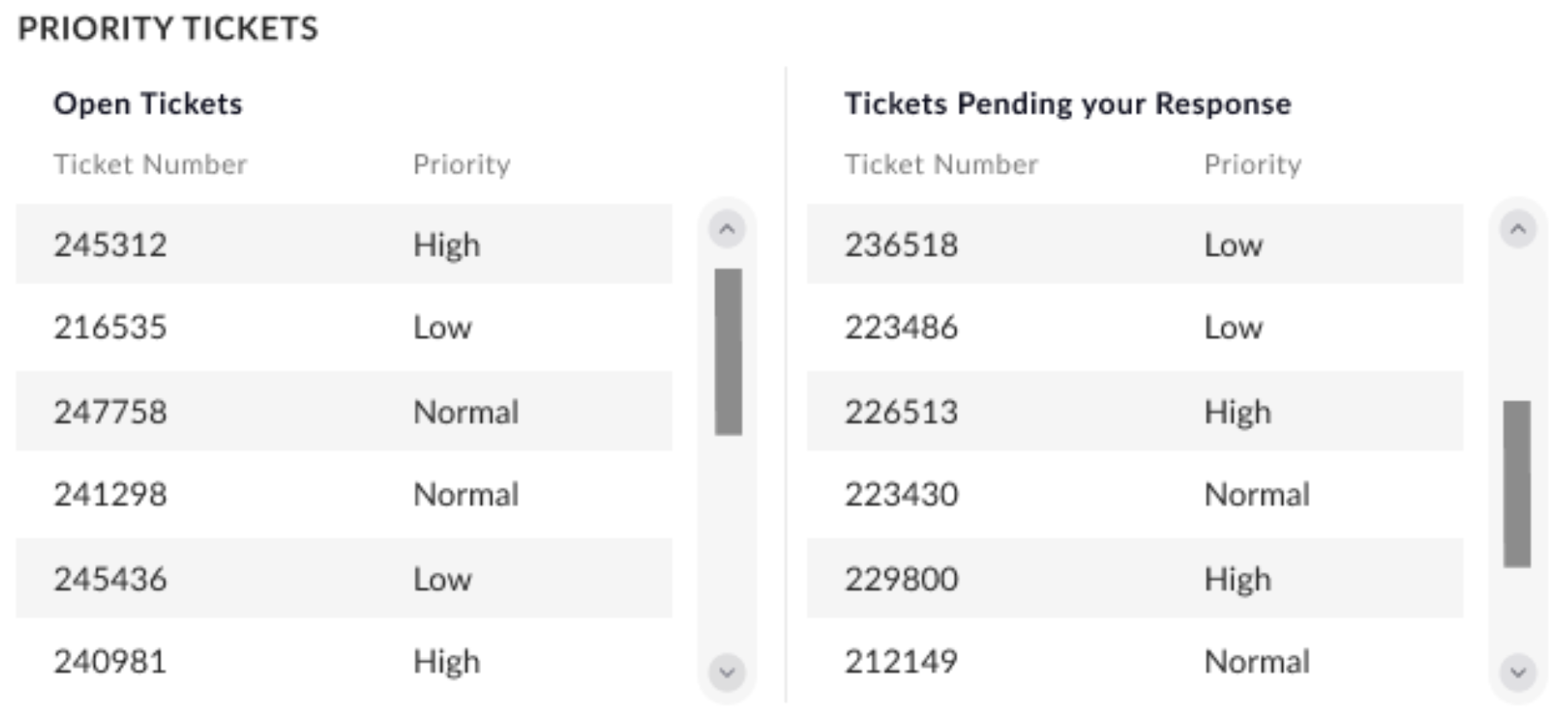
Enterprise Deployment reports also provide a full list of tickets within a security team’s workflow, displaying both open and pending tickets, along with priority levels to track team and analyst performance, so that team leaders can prioritize issues that need to be addressed.
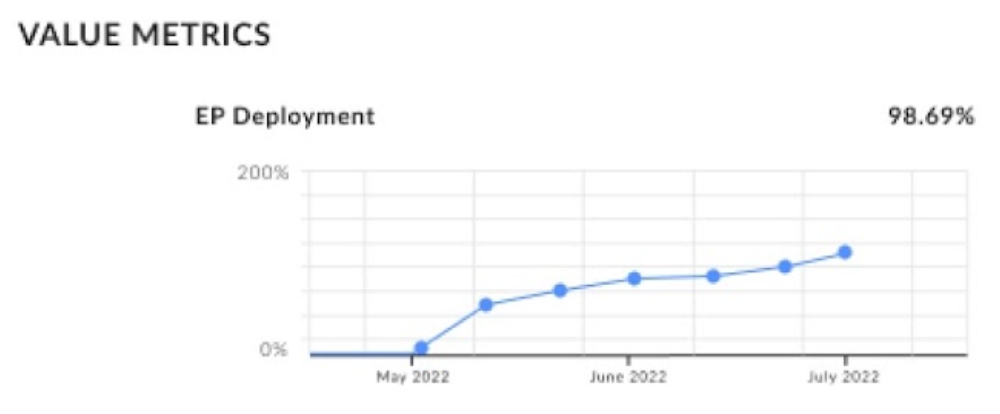
Additional components of the report include the EP deployment graph, which provides security teams with high-level visibility into blindspots in their security estate so they can roll out agents as necessary.
(However, customers that already deploy Singularity Ranger can automatically close any deployment gaps, with no manual intervention necessary.)
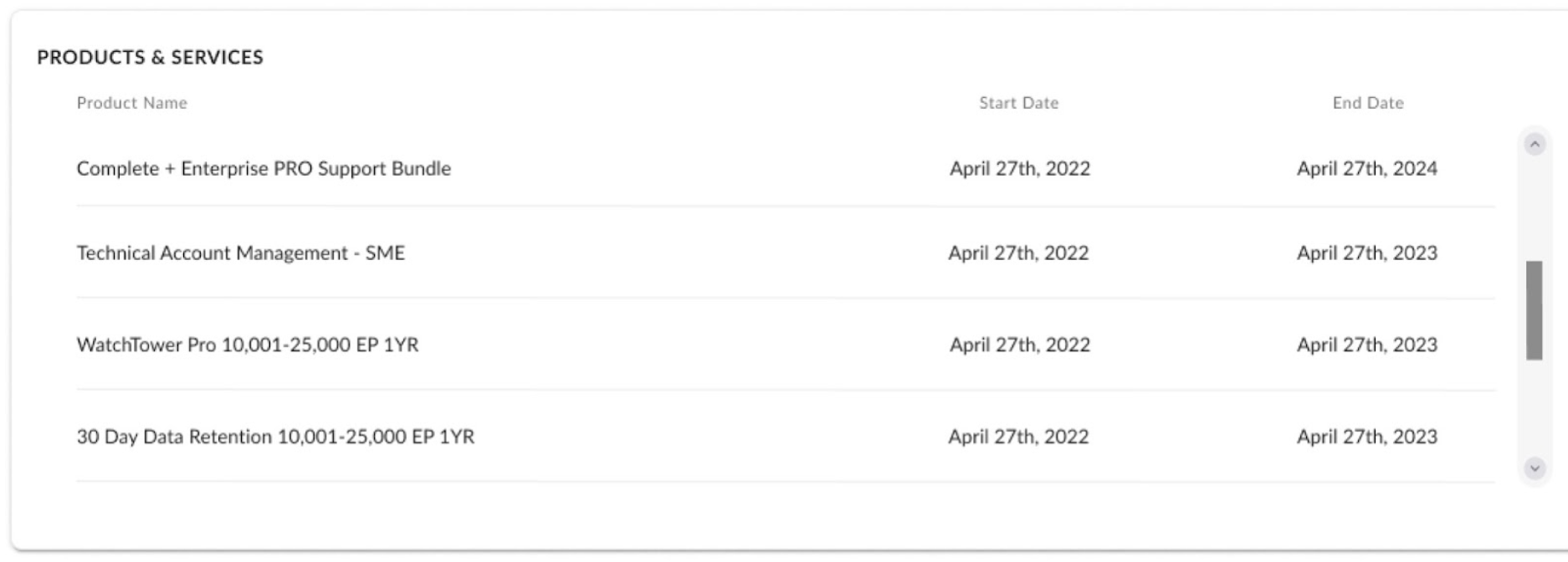
Moreover, security teams can also ensure continuous protection of their enterprise’s various attack surfaces by viewing the start and end dates of the enterprise’s SentinelOne products and subscriptions from one pane of glass.
Understand Effort and Impact with the Business Value Report
With the Business Value Report, enterprise security leaders and CISOs can provide tangible proof of improved security posture to their boards and executives. They can demonstrate their team’s value by showing an overview of the risks they’ve mitigated, which gives them a foundation to expand on by talking about how their analysts have faced more specific known and emergent threats.
This report provides visibility into the number of malicious and suspicious threats the team has detected and resolved. Key stakeholders can also get a look at resolved and unresolved threats, sorted by the incident’s status, to evaluate their security team’s workflows and what blockers may exist for further improvement. This view can be drilled down further to threats at the account level.
The report also offers visibility into a customer’s endpoint fleet by attaching a health overview of their Sentinel Agents. These charts provide valuable insights into agent deployments by sorting them according to their supported operating systems and legacy systems that have reached their end-of-support or end-of-life stage. This organization makes it easier for teams to manage their endpoint devices and stay ahead of any potential security threats. By grouping the devices by OS, site, and attack surface type, such as desktops, laptops, and servers, teams can quickly identify any vulnerable devices and take proactive measures to address them.
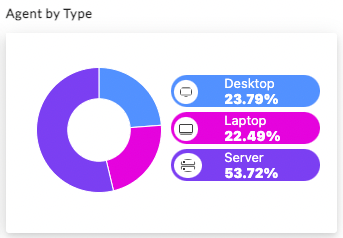
The report provides additional value for our Vigilance customers by giving them a month-by-month look at the number of attacks prevented by our Managed Detection and Response (MDR) service, along with a breakdown of the types of threats encountered by our Vigilance analysts. Vigilance Respond and Vigilance Respond Pro customers can get a more granular view of the work performed by our team and its impact through the Vigilance Executive Report—more on that shortly.
Stay Healthy with Proactive Support & Health Monitoring
With SentinelOne’s Enterprise Pro Support offering, security teams gain unique, unmatched insight into their security suite’s health and performance, so they can quickly detect and resolve performance issues before downstream business impact.
Enterprise Pro Support customers can access daily Proactive Support Reports that provide a snapshot of their environment’s health at both the agent and console levels.
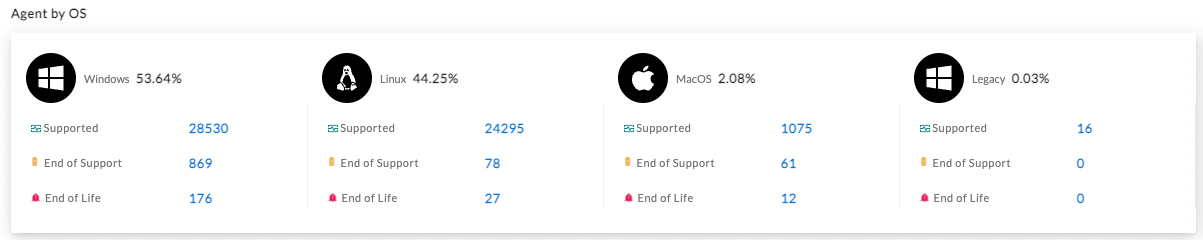
Every report starts with a high-level health overview of Sentinel Agents across a security estate, organized by OS, site, and attack surface type (such as desktop, laptop, and server).
Get insight into agents that are reaching end-of-support or end-of-life, and deploy additional protections immediately. Customers can also identify sites and agents with the highest level of alerts to prioritize their security team’s investigations.
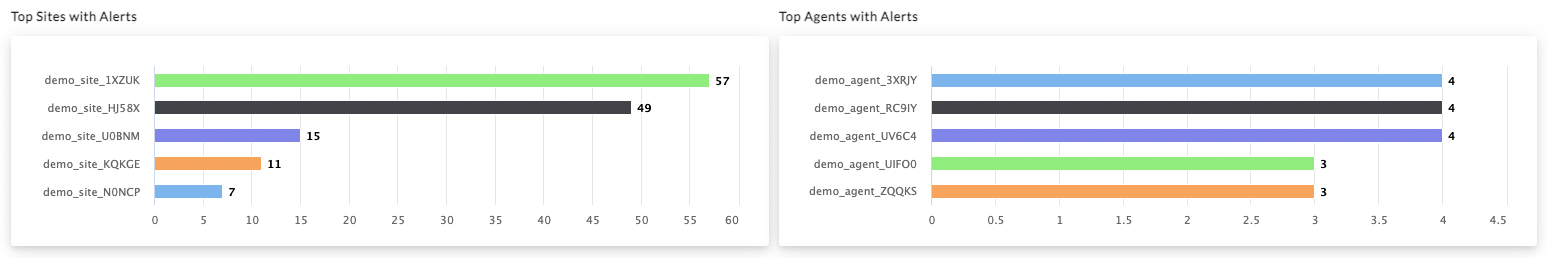
Get a head start on managing any issues in an environment with a comprehensive list of management and agent diagnostics. These reports provide 24×7 visibility into any factors that may impact performance, such as agent performance, CPU and memory impact, anomalies in processes or databases, and upgrade or install progress with actionable steps for remediation. Even better, the Enterprise Pro Support service automatically opens tickets for high-severity issues without requiring a customer to create a ticket manually.
The Singularity Platform offers its administrators and users unparalleled accuracy in isolating and resolving issues, and empowers users to identify and address any potential security risks, ensuring the integrity and protection of their system.
Each report will list impacted devices for each category, and offer policies and best practices that your security program can implement to create additional layers of protection for your environments.
Assess the Impact of MDR with Vigilance Executive Reports
Teams using Vigilance Respond and Vigilance Respond Pro Managed Detection and Response (MDR) can now access their Vigilance executive reports through the Community. These reports offer a month-to-month look at the volume and complexity of threats an environment faces, including the type of threats encountered, Mean Time to Respond (MTTR), and the efficacy of alert and ticket resolution.
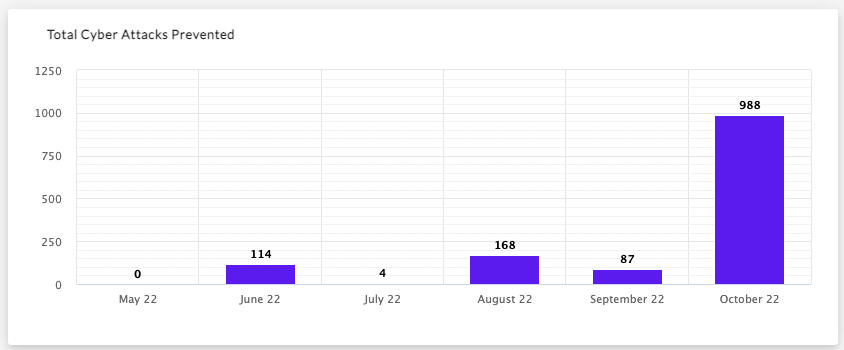
Customers use this overview of their activity in conversations with leadership. For example, this data can be visualized to show how a security program has consistently lowered your company’s MTTR to potential incidents, and break down the number and type of cyber attacks prevented each month.
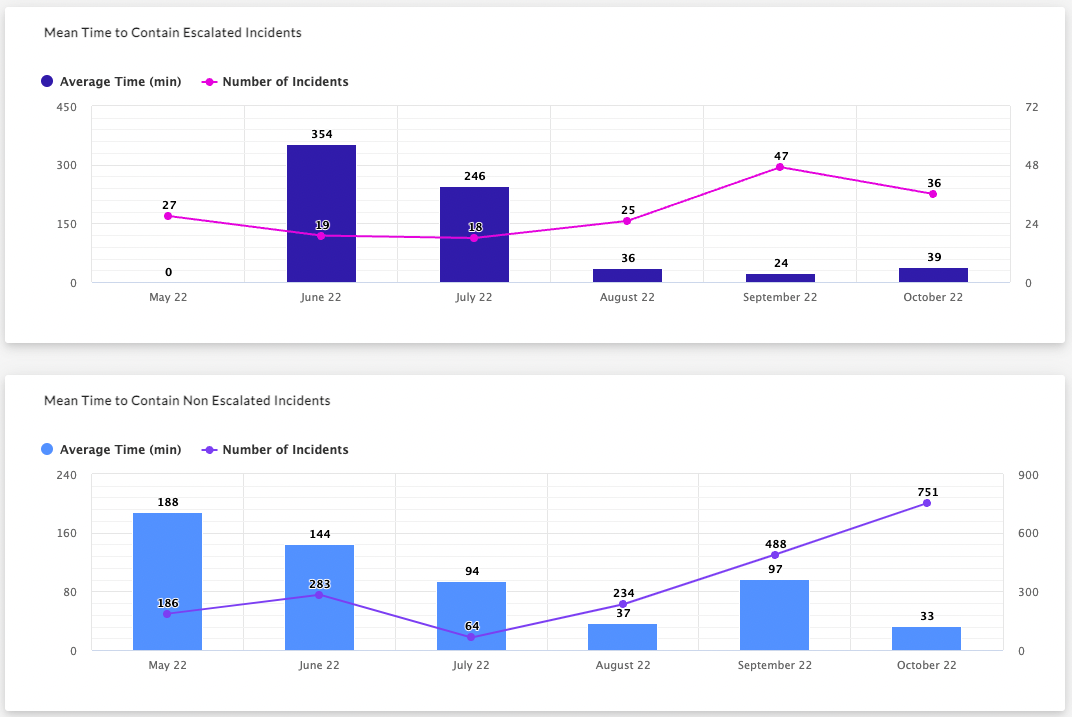
These reports can also help key stakeholders outside of the security discipline to understand how their security team prioritizes and quickly resolves high-severity issues, and show a clear decrease in risks to their company’s sensitive data.
Proactively Prepare for Incidents with Response Readiness Reports
SentinelOne empowers Vigilance Respond Pro customers with quarterly Response Readiness Reviews, which ensure that organizations are prepared to investigate and respond to suspicious or malicious activities and close gaps in their cybersecurity coverage.
In addition to noting the service & retainer hours a customer has left in their Vigilance subscription and expiration date, Response Readiness reviews also allow them to schedule consultations and include suggestions for how they can make the most of the time they have remaining in their subscription, through offerings such as workshops, policy reviews, and tabletop exercises.
Like other Vigilance reports, these reviews also allow them to identify endpoints and servers with operating systems nearing EOL and versions of the Sentinel Agent approaching EOS to mitigate security risks. Teams can also follow given recommendations and notes from Vigilance MDR & DFIR analysts to better align their organization’s security posture with best practices.
Looking Ahead
The reports available in the Community can help teams understand the kind of threats their environments face and proactively tackle high-priority issues. They can also help generate additional buy-in from CISOs and executives by demonstrating the impact of SentinelOne technology and services on keeping their business running smoothly.
And there’s more! As we continue to partner with our customers, the SentinelOne Customer Community will be introducing further new ways to gain and share knowledge, optimize security programs and take informed action. Stay tuned for further exciting announcements ahead by signing up for SentinelOne’s weekly email digest using the form on your right.
If you would like to learn how SentinelOne can help protect your business, contact us or request a free demo.
如有侵权请联系:admin#unsafe.sh