Software components make our lives easier. Thanks to them, companies and individuals can perform thousands of unimaginable actions in the analog world, from using a solution to market a company’s products to an application for a person to control their accounts. Unfortunately, software components have become critical assets of companies and one of the elements most exposed to malicious actions. This is evidenced by the rise of supply chain attacks and their impact on companies of the caliber of Microsoft or IBM.
At the end of 2020, a supply chain attack came to light that had global repercussions: Solorigate. This cyberattack affected the technology company SolarWinds. This name may say nothing to a layperson in the digital world. But SolarWinds supplies enterprise software to companies and public administrations worldwide. So, in addition to Microsoft, as mentioned earlier, we can add Intel, Orange, the agency that controls the U.S. nuclear arsenal (NNSA), NASA and the European Parliament.
The attackers introduced malware on the server used by the company to create software updates for Orion, one of its platforms. Thus, every time a company using Orion updated its software, it allowed the Trojan to sneak into its system. As a result, the attackers could steal information from more than 18,000 companies worldwide, particularly from some of the world’s most important companies and public administrations.
Hence, this security incident is the perfect example of how serious and far-reaching successful supply chain attacks can be, putting the data of organizations and their customers at risk.
1. What are supply chain attacks?
First, we must answer the most obvious question: What are software supply chain attacks?
1.1. Attacking library vulnerabilities
When we see and use a solution, we know that it is the result of the work and talent of its developers.
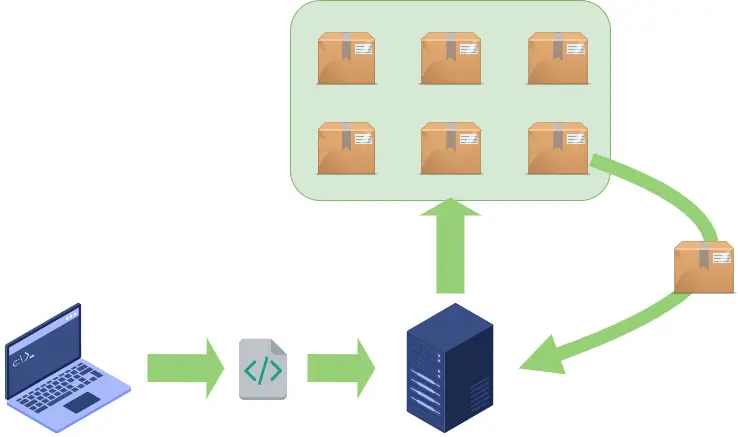
However, nowadays, virtually every software is written from scratch. That is to say, professionals do not have to chop up the code that underpins software but resort to already-developed open-source components found in libraries and repositories. Thus, if a cybercriminal attacks one of these components, it can impact all the software used.
INFO1 – Within the supply chain of a proprietary development, the need to include a library or software package is covered. The system downloads it from its corresponding software repository if it is not installed. Any system, such as Windows, Android, or GNU/Linux… has its repositories for libraries and software. Once the package and the required version are located, it is installed on the system, and the self-development executes the functions included in the package.
1.1.1. Log4Shell, a paradigmatic example
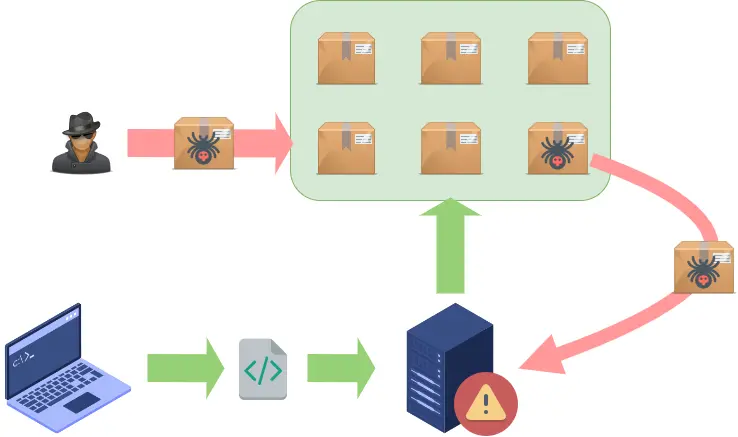
This is precisely what happened with one of the last decade’s most relevant supply chain attacks: Log4Shell. Vulnerabilities detected in the Log4j component, widely used in Java applications for such an everyday task as log message management, allowed cyber attackers to compromise the security of applications that used this component completely.
Its use is so common that even NASA’s Ingenuity helicopter uses Log4j. But so do applications such as IBM Qradar SIEM or NetApp.
INFO2 – In this example, the supply chain is altered in the software repository itself. The attacker gets permission to alter the package and insert malicious code, which will be installed on each system that requires it to run the developed software. When the malicious code is executed on the system, it will be compromised by the attacker.
1.2. Attacking software to impact the companies that use it
Likewise, supply chain attacks can also consist of breaching a software product, as in the case of SolarWinds, as a first step to infiltrate the companies that use it.
In this way, a company can find itself attacked by one of its software suppliers. Think, for example, of third-party identity providers.
The Solorigate and Log4Shell cases allow us to observe an inescapable reality: one of the consequences of digitization is the increase in a company’s technological supply chain. And, just as the supply chain is an asset, it also carries risks. For example, a company can only secure its systems and networks if one of its suppliers is secure.
2. Who is involved in supply chain attacks?
The above context provides a glimpse of the immense breadth of supply chains, the possibilities of attack, and the companies and institutions that can be the target of this kind of aggression.
Companies that develop their software can suffer a supply chain attack by exploiting a vulnerability in the code. And in turn, if this software is successfully attacked and the solution is marketed to third parties, the companies that use it can also be attacked.
In fact, the supply chain works almost like a spider’s web, interconnecting companies that a priori have no reason to be related.
For example, if we use a bank’s app to manage our savings and investments, we tend to think that the bank developed the app. However, an independent development company provides some of the tools used to support it.
Besides, the leap to the Cloud and the massive commercialization of software as a Service (SaaS) has made the spider’s web more opaque. Developers, companies, public institutions and citizens must take supply chain cyber defense very seriously. Otherwise, the economic, legal and social consequences can be devastating.
3. Targeted and untargeted attacks: barnacle picking and trolling
When we talk about cyberattacks, we must consider the objectives of the criminals who design, plan and execute them. Or, to put it another way: who they are aimed at.
Depending on this, we can speak of targeted and non-targeted attacks. For example, if a malicious actor uses phishing to obtain the banking data of as many people as possible, it is clear that his goal is trolling. Therefore, all victims who fall into his net are valid.
On the other hand, if he uses other social engineering techniques to carry out what is known as CEO fraud, we are dealing with a targeted attack. Not just any fruit of the sea will do; the cybercriminal wants to capture a specific barnacle.
If we jump to the field of supply chain attacks, we can find both targeted attacks and attacks that, a priori, are not targeted. But we can also detect that the boundary between one and the other becomes liquid in this spider’s web, that is, the digital supply chain.
A group of cybercriminals can find an open-source component with vulnerabilities, launch a piece of malware, and then infiltrate all the software that uses this element in its code. Would this be a non-targeted attack? What if they take advantage of the security breach to attack several specific companies? Would it become a targeted attack?
Supply chain attacks are a true reflection of the increasing complexity of the supply chain.
Does this mean developers, software contracting companies and users are caught in the web at the mercy of spiders? Not at all. Securing the entire software lifecycle and third-party auditing solutions are value-added cybersecurity services to combat supply chain attacks.
4. Integrate into the software lifecycle to secure it.
Every software component we use has a lifecycle. From the time the idea is conceived until the software is fully operational, it needs to be maintained and updated to protect it against attacks and to optimize it.
Therefore, the best way to protect software is to have a continuous vulnerability scanning and detection service throughout all phases of the software lifecycle.
Often, companies hire an audit to analyze the security level of the software once it has been developed and launched on the market. This is useful for detecting vulnerabilities, assessing risks and proposing measures to remedy weaknesses. But it comes too late.
Moreover, since the software is updated periodically, it is also relevant to evaluate each update before generating its new release. Finally, as Solorigate has shown us, a solution update can be the perfect gateway to attack companies that integrate it into their systems.
Hence, the best option is to integrate a cybersecurity service into the software lifecycle. This kind of service can analyze the software from the development itself, checking the libraries used for vulnerabilities and weaknesses in the source code.
Tarlogic Security professionals are designing this service to help companies protect their software throughout its entire lifecycle. Combining cutting-edge technological tools with the deep knowledge in cybersecurity accumulated by Tarlogic professionals over the years.
Here are the key elements of this service to integrate into the software lifecycle and secure it.
4.1. Automate the search for vulnerabilities
When, integrating into the software lifecycle, it can be extremely useful to have a solution that can be integrated into code repositories and continuous software integration (CI/CD) processes. This tool aims to find vulnerabilities that affect the software in its development stage before the new version of the application is released and can be exploited by cybercriminals.
This way, the application’s dependencies concerning libraries can be analyzed during the software’s life cycle.
In addition, it is possible to automatically search for vulnerabilities in the various versions of a component or software, display them on a control panel and help to ensure that they do not become present in the final product to be launched on the market.
To sum up, the service aims to analyze an application’s dependencies and prevent updates from being released that could generate a security breach in the software and in the companies and users that use it.
4.2. SBOM, a mapping of software elements
As its name suggests, the Software Bill of Materials (SBOM) is an inventory of the elements with which software components have been developed.
This inventory includes the libraries used, versions and vulnerabilities.
As we pointed out earlier, the software supply chain is becoming more and more opaque. Having an SBOM provides transparency about the third-party components used to develop software.
This is of great interest for the developing company to analyze all components for vulnerabilities and for the companies acquiring the solution, which can evaluate its security.
In this sense, SBOMs have become a highly valuable resource for maintaining exhaustive and precise control of the software supply chain, helping to protect it and mitigate vulnerabilities throughout its life cycle.
Therefore, a solution that integrates into the entire software lifecycle and automates the search for vulnerabilities must also have an automated SBOM. To test all the code of both the software and the third-party elements used.
4.3. SCA and SAST. Analyze libraries and source code
SBOM helps us to know precisely which third-party elements are used in the software. But how do we analyze the solution for vulnerabilities?
Two types of analysis come into play here:
- Software Composition Analysis (SCA)
- Software Application Security Testing (SAST)
SAST is a type of analysis that is particularly useful during software development, i.e., before the software is released, since these security tests analyze the software source code to detect new vulnerabilities. Hence we can create an embryonic and of great added value for secure development.
SCA is used to identify the open-source components used in software and detect vulnerabilities that could affect its security. Just as SAST is embryonic, SCA is implemented to analyze known vulnerabilities in already developed third-party software integrated into our code.
The SCA gives only false positives since it works with existing vulnerabilities. This means that it is easier to implement since the security alerts generated are mostly accurate.
Which of the two types of testing is better for securing software? In an optimal scenario, the best solution would be to implement both tools. Since the SCA allows control of the software libraries and repositories, the SAST controls the source code. In such a way, their combined use strengthens the security of software throughout its life cycle.
4.4. Comprehensive advisory service
A cybersecurity service integrated throughout the life cycle of software to automate the detection of vulnerabilities in its source code and control the libraries and repositories used by the application also requires comprehensive advice.
In this regard, the Tarlogic team plans to use the tools best suited to each case and, in addition, to provide continuous advice. For instance, solutions that automate the search for vulnerabilities can generate false positives.
For example, 200 vulnerabilities may be detected in a large piece of code, but only 50 are real weaknesses that need to be addressed. If you have the experience and expertise of experienced professionals in this field, you will not mismanage your resources by trying to fix non-existent or irrelevant problems.
When it comes to securing the software supply chain and preventing supply chain attacks, more is needed to have the ability to detect weaknesses but also to address them. For example, by implementing new versions of an open-source element. Or by releasing a patch to fix a source code-related problem.
In this regard, it is also vitally important to have the advice of cybersecurity professionals who can establish a series of recommendations to mitigate problems.
5. Auditing software vendors
So far, we have discussed strengthening software security throughout its life cycle and preventing supply chain attacks. But this type of attack goes beyond this issue. More is needed to focus on analyzing and securing self-developed software. We must also consider the security risks associated with our third-party software.
Companies do not only use applications developed by themselves but also hire tools from suppliers and even make use of the integration of third-party components focused on specific tasks.
Take Bizum, for example, which provides its payment services software to banks, which, in turn, integrates this tool into their mobile applications.
What is the consequence of all this?
Companies using the software must recognize the security control of their suppliers.
This is why supplier security audits are a booming, value-added cybersecurity service since they are a very useful tool for controlling the supply chain and preventing the economic, legal and reputational consequences of supply chain attacks.
Thus, many companies contract cybersecurity companies such as Tarlogic to audit their third-party solutions. This requires authorization from the developer of the software to be audited.
6. Controlling the supply chain in the era of Cloud and SaaS
The digital transformation of companies has brought an avalanche of benefits, both commercially, opening up new business avenues, and in terms of management and internal processes. However, it also entails risks.
The more digitized a company is, the higher its cyber exposure to criminals.
If the famous superhero Spider-Man was told that «with great power comes great responsibility», we would argue that all the benefits of digitization also entail taking cybersecurity seriously. To this end, it is not enough to invest in protecting one’s assets and systems; it is also essential to monitor suppliers’ security.
6.1. The leap to the Cloud makes the supply chain complex
Even more so at the current stage, when companies have not only digitized their structures but have already gone even further: they have leaped the Cloud.
The Cloud is gaining ground day by day. The proliferation of software as a Service (SaaS) or Platform as a Service (PaaS) is proof of this.
The advantages of these technologies are well known. However, they make a company’s technology supply chain more complex.
Therefore, companies must take measures to protect themselves against supply chain attacks.
The consolidation of the Cloud makes clear an inescapable trend in cybersecurity: supply chain attacks will be on the rise. Both in quantity and in the level of sophistication. If one software integrates another software, that integrates another software, that integrates another software, that integrates another software… Attacking a weakness in the tail of the supply chain can cause a very serious security incident in the head.
In short, supply chain attacks have become a threat to thousands of companies, sometimes without them even being aware of the risk. This is why all companies should take the dangers seriously and hire services to secure their in-house developed software and audit the third-party solutions they use.