2023-2-9 19:53:39 Author: www.sentinelone.com(查看原文) 阅读量:37 收藏
Advertising is an integral part of the modern digital economy, providing businesses with the opportunity to reach a large and diverse audience. However, malicious actors are taking advantage of the ubiquity of online advertising to spread malware, phishing scams, and other forms of malicious content. In recent weeks, Google Ads, one of the largest online advertising platforms, has become a popular target for these types of attacks.
In this analysis, we examine recent malicious Google Ads targeting Amazon Web Services (AWS) logins through fraudulent credential phishing websites.

Overview
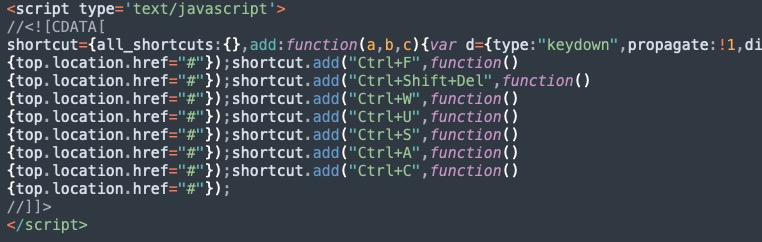
From a high level, the workflow of the malvertising campaign followed a unique pattern, providing yet another example of the evolving malvertising campaigns ongoing through Google search results. In the case of AWS credentials targeting discussed here, we perform a normal Google search for “AWS”, which returns the malicious ad among the results.
The ad itself goes to a hop domain, which is an actor-controlled blogger website. This first hop then redirects to the actual credentials phishing page hosted on a second domain. After the victim submits their credentials, a final redirect sends the victim to the legitimate AWS login page. The redirect represents an effort to evade detection by cautious users, but more importantly to evade automated detection of the phishing websites and malicious ad monitors. The various hops and content included in the webpages of each domain add to the complexity of automated detection in such attacks.
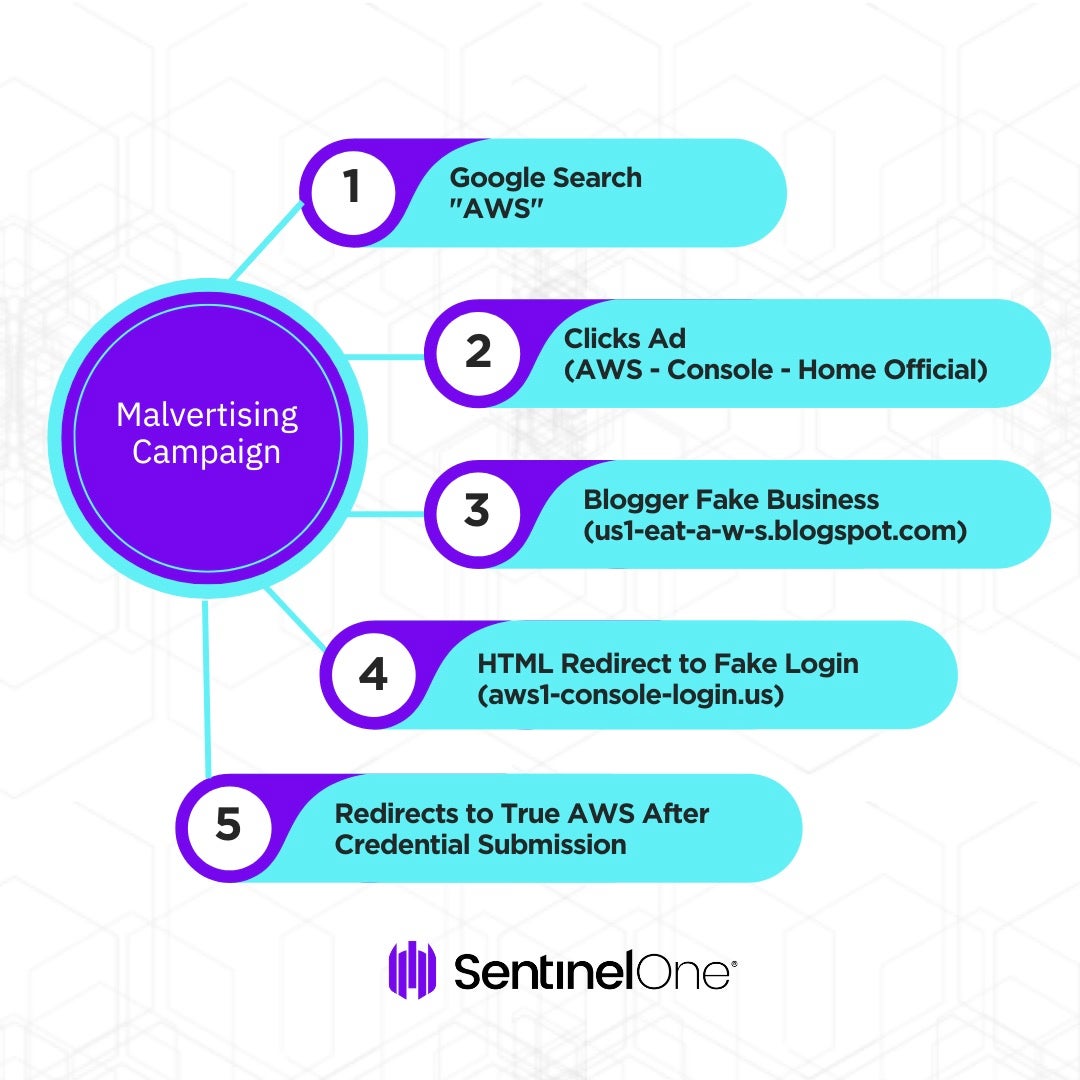
Malicious Ads
The malicious advertisements we observed occurred on January 30th and 31st 2023. These ads were most easily identified by searching “aws” in Google. Initially, the phishing domain was the ad itself; however, the attacker later shifted to a proxy ad through a blogspot.com website. As the image below shows, the attacker made use of us1-eat-a-w-s.blogspot[.]com as the destination for malicious ads. This is likely an effort to evade automated detection by Google of suspicious ad destination content.
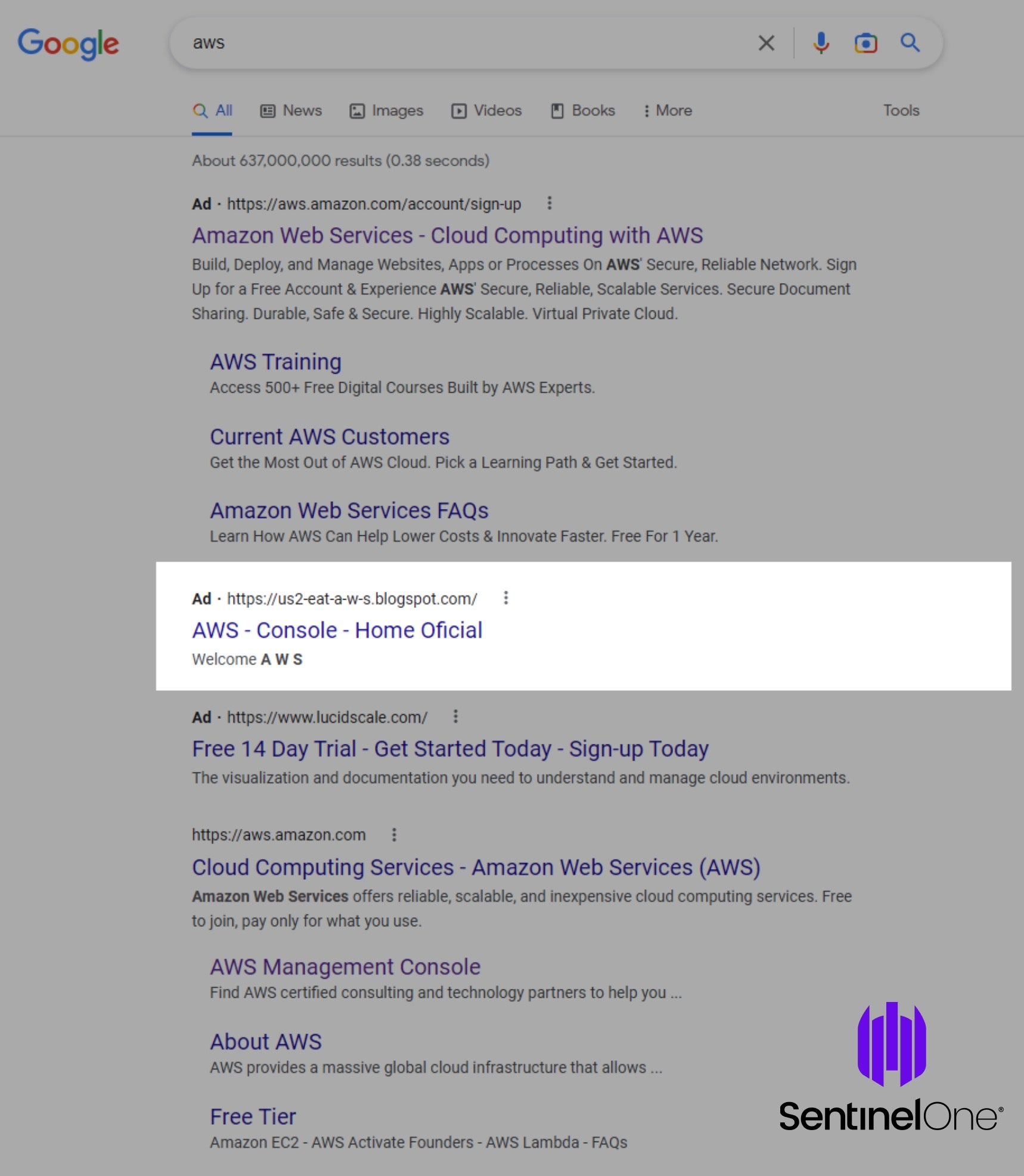
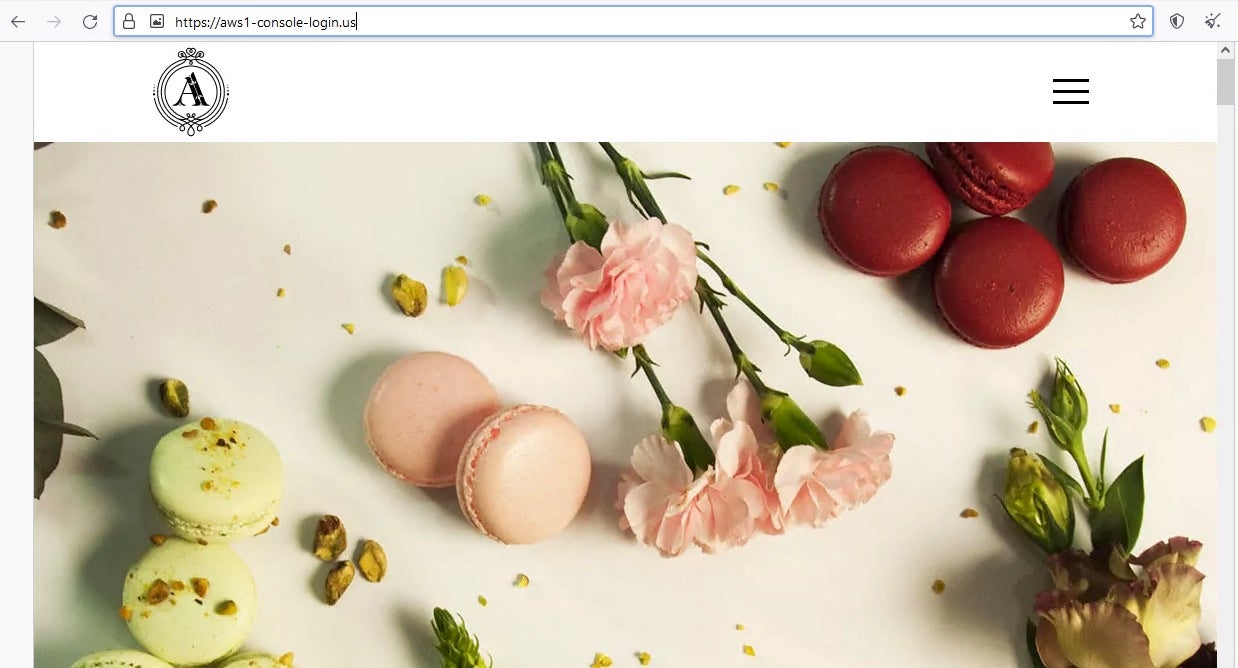
The content of the us1-eat-a-w-s.blogspot[.]com website is a copy of a legitimate vegan food blog. However, the page loads a second domain, aws1-console-login[.]us/login, through an HTML window.location.replace action. Note, the blogger page was shut down less than a day after its creation.
Following the automated redirect to the aws1-console-login[.]us/login destination, the target is finally presented with a spoofed AWS login prompt. The login process appears legitimate to unsuspecting targets.
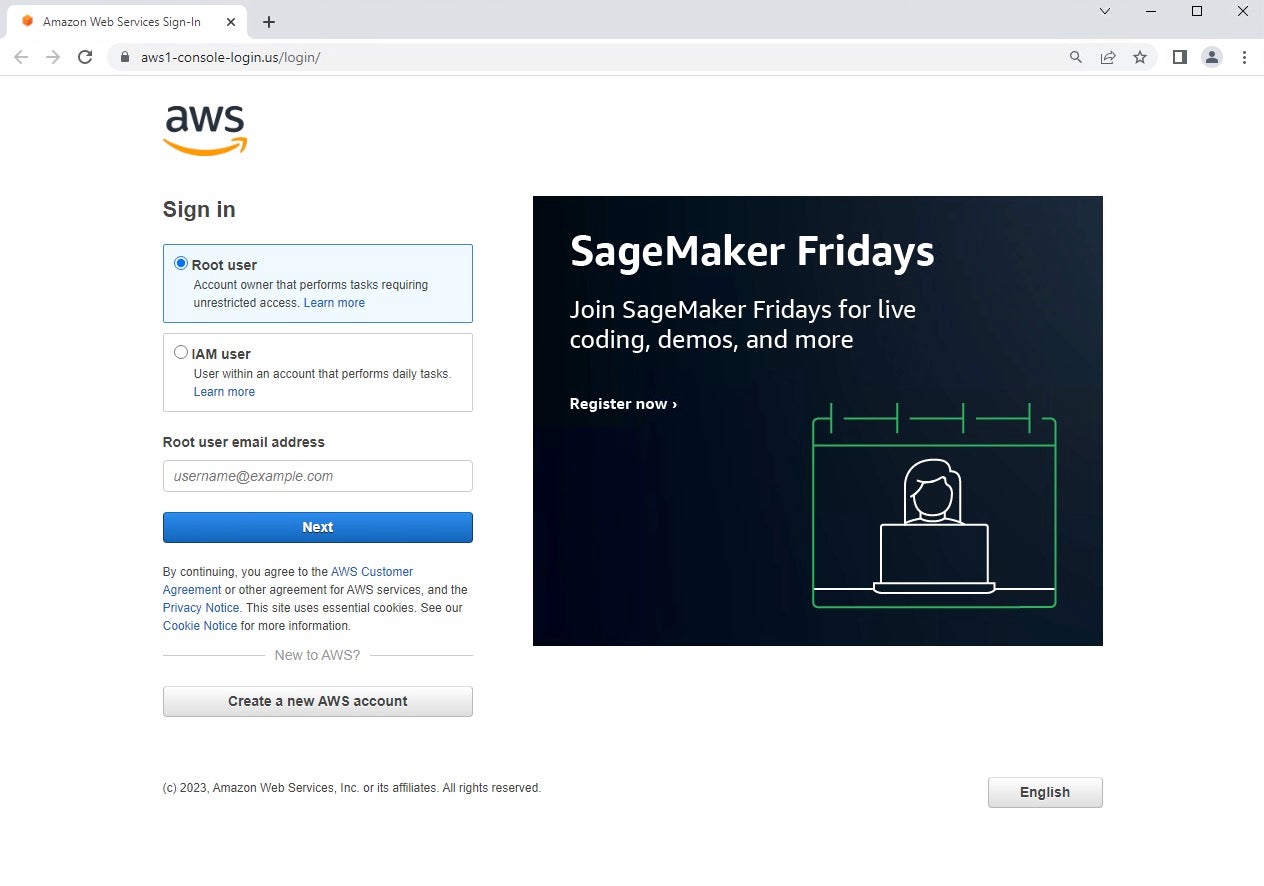
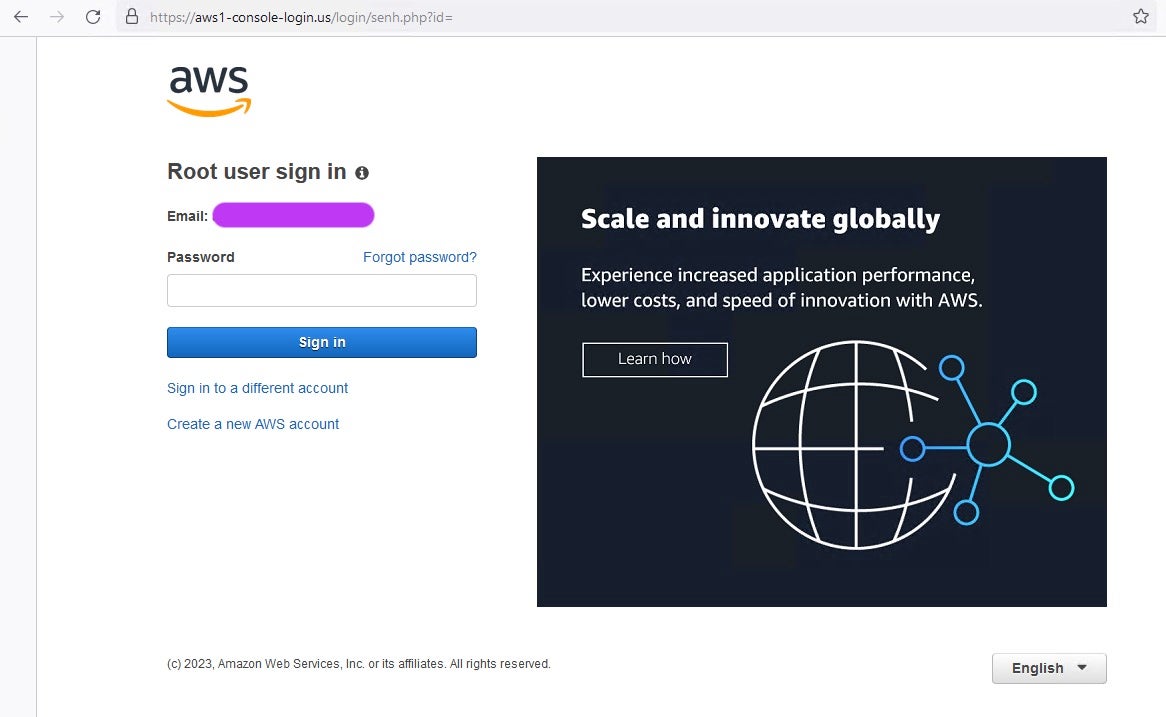
After the user enters their credentials, the final zconfig01.php page is loaded. This contains a single line of code to direct victims to the legitimate AWS login page.
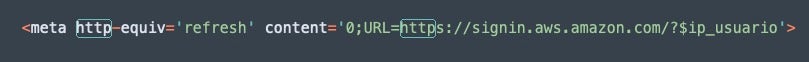
Recently, Permiso’s P0 Labs conducted a review of an AWS phishing site related to the same attacker. Based on our analysis, we attributed it to the same attacker continuing their campaign on new ads with a few technical adjustments.
Phishing Page Characteristics
Several characteristics unique to the phishing pages are noteworthy, including the layout, design, and efforts to hinder analysis as well as the developers’ spoken language.
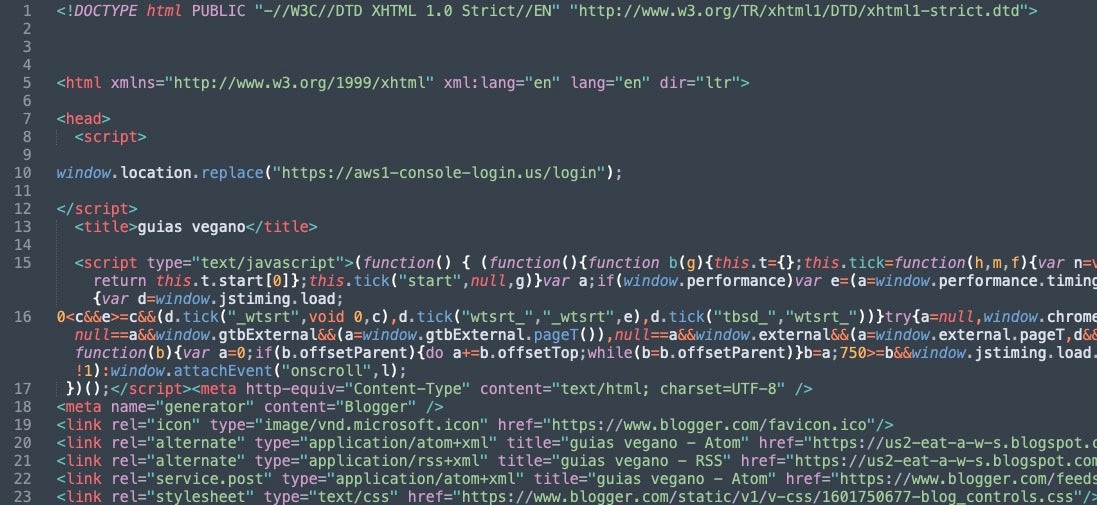
A JavaScript function disables the right-click context menu and middle mouse button click on the web page. The function sets the oncontextmenu event to return false, effectively disabling the right-click context menu. It also sets the onmousedown event to call the clickNS function for non-IE browsers, which checks for middle mouse button clicks and returns false if either is detected. The clickIE function does the same for Internet Explorer. The purpose of this code is likely to prevent users from copying content from the web page using the right-click context menu or middle mouse button.
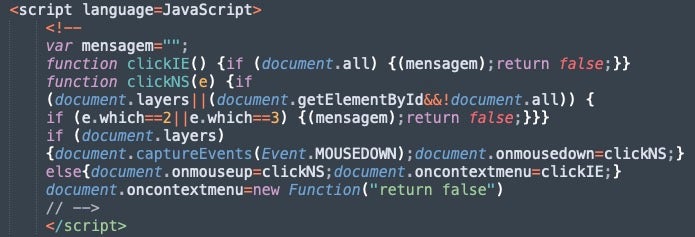
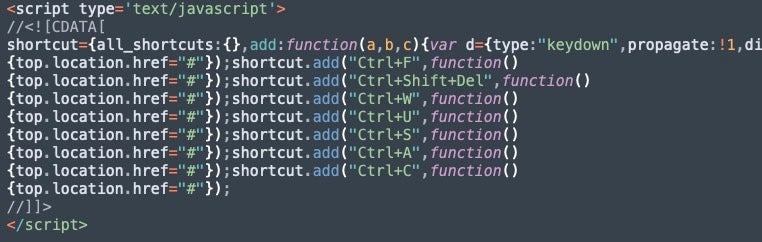
More JavaScript code adds several keyboard shortcuts that, when pressed, will redirect the user to “#”. This does not correspond to a specific page on the website and in effect serves to disable the keyboard shortcuts while the page is active.
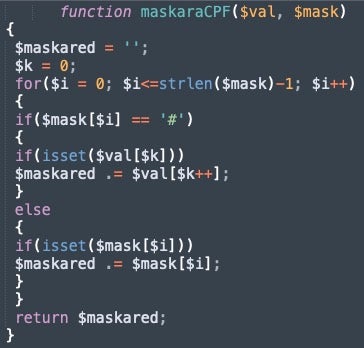
All comments, variable names, and other bits of language are written in Portuguese. Additionally, one unused function included maskaraCPF. It’s possible that this function could be used to format and display personal information, such as a Brazilian CPF number, in a way that makes it appear legitimate to the user.
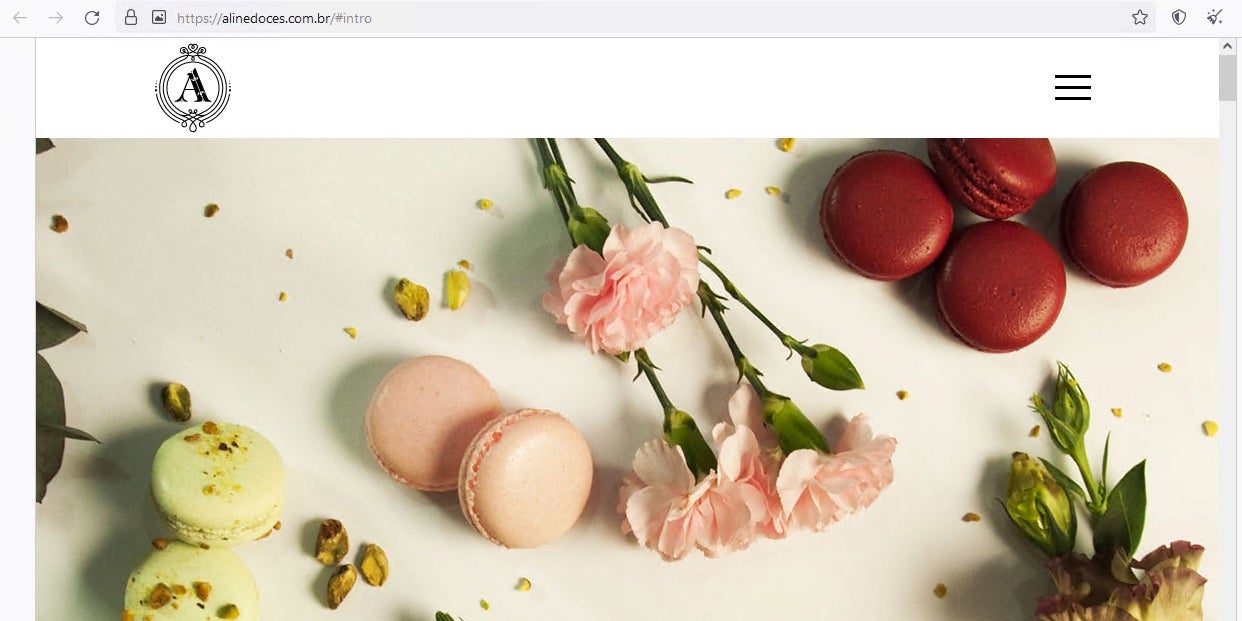
Throughout the various web pages the attacker made for this campaign, such as the blogspot and phishing pages, repeated use was made of source code copied from unrelated and legitimate websites. For example, the root page of the blogger domain mimics a legitimate Brazilian dessert business. The /login file on this site loads the AWS phishing page.
Infrastructure Analysis
The phishing domain aws1-console-login[.]us was registered through Sav, and then protected under CloudFlare on 2023-01-31, the same day it was being used in malicious ads. aws1-us-west[.]info was registered the day prior, and aws1-ec2-console.com on January 21, 2023.
For the aws1-console-login[.]us, the attacker did not protect the WHOIS details, providing yet another interesting link to Brazil.
- City: sao luis
- State/Province: ma
- Postal Code: 65076170
- Country: BR
- Phone: +55.99991638370
- Email: [email protected][.]com
CloudFlare were quick to confirm and responded by shutting down the account for service abuse. Due to this fast action, in some cases ads may be present on Google while the site is actually offline.
Following the removal of the phishing domains from CloudFlare services, we can see the web servers true hosting location through PDNS telemetry, which leads us to additional domains. As it turned out, the actors phishing for credentials with phony AWS Login pages hosted these malicious websites on AWS itself.
For example, aws1-console-login[.]us was hidden behind 172.67.159.93 (Cloudflare). Following its removal from the service, immediate response then resolved to 54.214.158.248 (AWS). This occurred for other associated domains as well, leading us to aws2-console-login[.]xyz.
Conclusion
The proliferation of malicious Google Ads leading to AWS phishing websites represents a serious threat to not just average users, but network and cloud administrators. The ease with which these attacks can be launched, combined with the large and diverse audience that Google Ads can reach, makes them a particularly potent threat.
Indicators of Compromise
| Indicator | Description |
| us1-eat-a-w-s.blogspot[.]com | Malicious Blogger site. Destination of advertisement, redirects to active phishing domain |
| aws1-console-login[.]us | AWS Phishing Domain |
| aws2-console-login[.]xyz | AWS Phishing Domain |
| aws1-ec2-console[.]com | AWS Phishing Domain |
| aws1-us-west[.]info | AWS Phishing Domain |
| 54.214.158.248 | Legitimate Amazon Web Services Hosting Phishing Pages |
| 35.167.172.179 | Legitimate Amazon Web Services Hosting Phishing Pages |
| [email protected][.]com | Phishing domain registrant email |
如有侵权请联系:admin#unsafe.sh