大家好,我是风淮,好久不见。最近开始备考OSCP,为了熟悉全英文场景就先从HTB开始复习基础,今天分享的是Tier0 Free部分的解题,从今天开始基本就会每天更新。
Meow
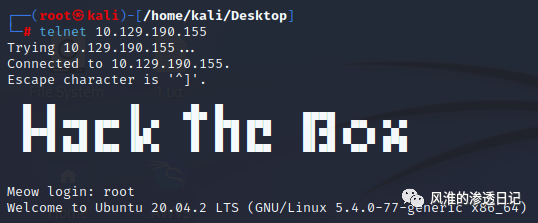
这是入门第一关,讲的是Telnet协议-未授权访问 ()
Q:What does the acronym VM stand for?(缩写字母VM代表什么)A:Virtual Machine (虚拟机器)Q:What tool do we use to interact with the operating system in order to issue commands via the command line, such as the one to start our VPN connection?It's also known as a console or shell.(我们使用什么工具去进行交互)A:terminal (命令行)Q:What service do we use to form our VPN connection into HTB labs(我们使用什么服务连接htb)A:OpenVpn(用的这个vpn做的隧道,详情查看Hack the box安装教程,自行查看官网)Q:What is the abbreviated name for a 'tunnel interface' in the output of your VPN boot-up sequence output?(红体字在系统输出的缩写)A:Tun (隧道)Q:What tool do we use to test our connection to the target with an ICMP echo request?(使用什么工具进行ICMP请求交互)A:ping (ping操作)Q:What is the name of the mot common tool for finding open ports on a target?(发现目标开放端口的使用最多的工具叫什么)A:Namp (神器,不过有点问题,记得看文章末尾问题)Q:What service do we identify on port 23/tcp during our scans?(扫描发现23端口是什么服务)A:Telnet (远程登录服务)Q:What username is able to log into the target over telnet with a blank password?(哪个用户名能够通过telnet以空白密码登录)A:rootQ:flagA:*************
Port:23 (Telnet)
Telnet登录目标,弱口令登录,进入目标
常规Linux操作,获取Flag
2. Fawm
第二关,讲的是FTP的匿名访问,这里就不得不提到常见的FTP未授权访问。
常见的FTP包括三种用户:Anonymous、用户、Administrator,部分地区的公司FTP安全策略还是开放着匿名登录,导致攻击者可以利用anonymous作为访问者通过空密码进行登录。
Q:What does the 3-letter acronym FTP stand for?(缩写FTP的意思)A:File Transfer Protocol (文件传输协议 )Q:Which port does the FTP service listen on usually?(FTP服务常见端口)A:21Q:What acronym is used for the secure version of FTP?(secure version of FTP的缩写)A:sftpQ:What is the command we can use to send an ICMP echo request to test our connection to the target?(使用什么去测试我们与目标的联系)A:pingQ:From your scans, what version is FTP running on the target?(从你扫描中发现FTP的版本?)A:vsftpd 3.0.3Q:What is the command we need to run in order to display the 'ftp' client help menu?(如何打开ftp的帮助面板)A:ftp -hQ:What is username that is used over FTP when you want to log in without having an account?(没有账户如何访问ftp)A:Anonymous (匿名)Q:What is the response code we get for the FTP message 'Login successful'?(登录成功,ftp如何显示)A:230Q:FlagA:*************
Port:21 服务为FTP 版本信息
下面的是当前用户具有读写权限,后面那个被水印挡了,那个是flag
直接匿名登录,成功的状态码为230,下载flag至本地,读取。
3.Dancing
这关讲的是Smb协议
Q:What does the 3-letter acronym SMB stand for? (smb缩写含义)A:Server Message Block (服务器信息块)Q:What port does SMB use to operate at? (SMB常用端口)A:445Q:What is the service name for port 445 that came up in our Nmap scan?(在nmap扫描里,smb叫什么)A:microsoft-dsQ:What is the tool we use to connect to SMB shares from our Linux distribution?(在Linux中,我们用什么工具去连接SMB服务)A:smbclientQ:How many shares are there on Dancing?(在这靶场里一共几个分享)A:4Q:What is the name of the share we are able to access in the end?(最后可以访问的分享名称叫什么)A:WorkSharesQ:FlagA:**********
nmap扫描结果中,smb端口及名称
利用smbclient 查看到4个共享,其中可以利用WorkShares进行无密码访问
2个共享文件夹,分别查看文件夹情况,发现flag,读取
4.Redeemer
作为最后一个Tier 0,考的是Redis数据库
Q:Which TCP port is open on the machine?(哪个端口开放)A:6379 (Redis)Q:What type of database is Redis? Choose from the following options: (i) In-memory Database, (ii) Traditional Database(Redis数据库类型)A:In-Memory (Redis数据库将内存中数据保持在磁盘中)Q:Which command-line utility is used to interact with the Redis server? Enter the program name you would enter into the terminal without any arguments.(利用什么工具可以进行交互)A:redis-cli (kali自带)Q:Once connected to a Redis server, which command is used to obtain the information and statistics about the Redis server?(利用什么命令查看信息)A:InfoQ:How many keys are present inside the database with index 0?(索引为0的数据库中有多少个键?)A:4Q:Which command is used to obtain all the keys in a database?(哪个命令用于获取数据库中的所有键值)A:Keys *Q:flagA:**************
Nmap扫描端口,服务,版本
利用redis-cli进行登录
获取键值,获取flag
Tier0的基础训练到此结束,明天干Tier1,虽然很基础,但可以很好地适应纯英文模式,哈哈哈具体内容确实浅,不过等刷完打Machine的时候就可以了。
作为宝宝巴士,但我还是有个问题想问看见文章的大佬:
Nmap为啥有的时候爆破不出来相关服务呢?就比如上面那台Redis我跑了好多次命令才跑出来这个端口服务,分段绕防火墙的参数我也加了,但还是会遇到什么服务都跑不出来的情况,是不是HTB这个连接不太稳定的原因尼?期待大佬后台私信回复!3Q
如有侵权请联系:admin#unsafe.sh