POSTED BY: sophron / 01.02.2018
The recent key reinstallation attacks (KRACK) against the WPA2 protocol revealed how an adversary can easily eavesdrop, and in some cases tamper, a Wi-Fi connection secured by the WPA2 protocol. At the same time, Wi-Fi automatic association attacks achieve a similar result (man-in-the-middle position) not by attacking the WPA2 protocol directly but by enforcing Wi-Fi clients to join a rogue Access Point.
The most popular Wi-Fi automatic association attack is KARMA. In this attack, a rogue access point is introduced that masquerades as a public network searched for by nearby Wi-Fi clients. The victim client that implements automatic wireless network discovery will automatically join the rogue network. The KARMA attack exploits two different features of an Operating System's Network Manager: i) the active scanning for networks the stations have associated with in the past and ii) the Auto-Connect flag that enables the stations to automatically join previously connected networks.
However, nowadays, most modern network managers have taken countermeasures against the KARMA attack by switching to passive scanning; instead of arbitrarily sending probe request frames, network managers now wait to receive a beacon frame with a familiar ESSID before associating with a wireless network. While this countermeasure has hampered the effectiveness of the KARMA attack, the second feature exploited by KARMA, the Auto-Connect flag, was left intact in almost every modern Operating System.
The Auto-Connect feature is a threat on its own. An attacker that can guess the ESSID of an open network in the victim device's Preferred Network List, will be able to broadcast the corresponding beacon frame and have that device automatically associate with an attacker-controlled access point. In a more sophisticated version of the attack, the adversary may use a "dictionary" of common ESSIDs, that the victim has likely connected to in the past.
Figure 1: Known Beacons Attack
We call this type of automatic association attack the "Known Beacons" attack and have added this attack method to the Wifiphisher tool.
Wifiphisher's dictionary of common ESSIDs, has been prepared based on manual gathering of information from popular networks, wardriving and input from the Wifiphisher community. The dictionary includes:
- Default ESSIDs such as: "AndroidAP", "linksys", "iPhone", etc.
- ESSIDs that are commonly used by network administrators, such as: "wireless", "guest", "cafe", "public", "conference", etc.
- ESSIDs of global Wi-Fi networks, such as: "xfinitywifi", "attwifi", "eduroam", "BTFON", etc.
- ESSIDs of hotspots that exist in hotels, airports and other places of public interest, such as: "hhonors_public", "walmartwifi", etc.
The "Known Beacons" attack can be conducted using version 1.4 of Wifiphisher with the "--knownbeacons" or "-kB" option as shown below:
root@kali:~# wifiphisher -kB
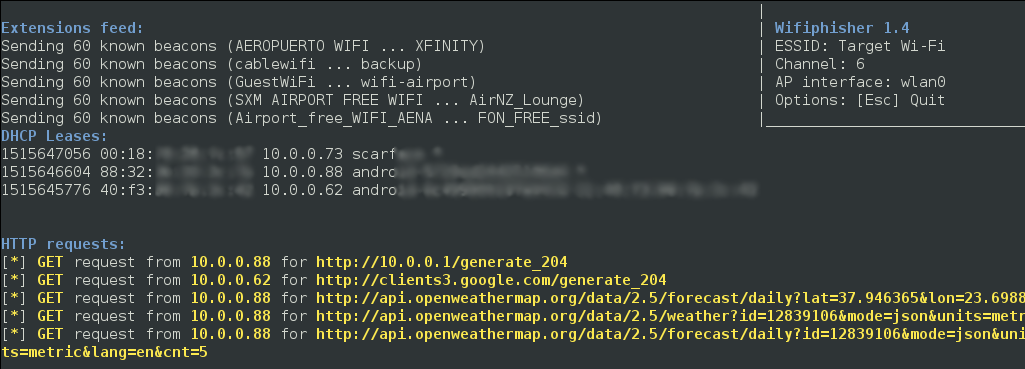
The following screenshot illustrates the Known Beacons attack in action.
Figure 2: Known Beacons Attack in Action
From our research, it appears that most modern Operating Systems, except for Windows 10, have (by default) the Auto-Connect flag enabled when identifying known open networks. Hence, users of these systems that have joined an open network in the past, with a common ESSID, might not be vulnerable to the KARMA attack but may be susceptible to the "Known Beacons" attack.
To protect themselves from this attack, users are strongly advised to make sure no ESSIDs of open networks are listed in their network manager's Preferred Network List.
The "known beacons" attack was first presented as a lightning talk at the 34th iteration of the annual Chaos Communication Congress (34C3). Material from this presentation can be found below:
- Tags: 34c3 , android , iOS , linux , macos , conference , research , wireless penetration testing , man in the middle , wifiphisher , wifi , known beacons
如有侵权请联系:admin#unsafe.sh