
Researchers at ASEC recently reported on a NetSupport RAT campaign that utilizes Pokemon as the soc 2023-1-16 22:28:35 Author: www.sentinelone.com(查看原文) 阅读量:38 收藏
Researchers at ASEC recently reported on a NetSupport RAT campaign that utilizes Pokemon as the social engineering lure. Threat actors staged a malicious website, hosting a Pokemon-based NFT game, offering both a fun and financially rewarding experience. In reality, those drawn into the site are coerced into downloading the trojanized NetSupport RAT client, allowing attackers full access to their device.
NetSupport RAT has been observed in numerous attacks on enterprise environments over the years, and Pokemon is just the latest in a long line of creative lures used to distribute and drop NetSupport RAT. It is frequently used by cybercriminals as a ‘quick solution’ in lieu of implementing something more bespoke.
In this post, we provide an overview of NetSupport RAT and discuss the technical details of a recent campaign.

Background
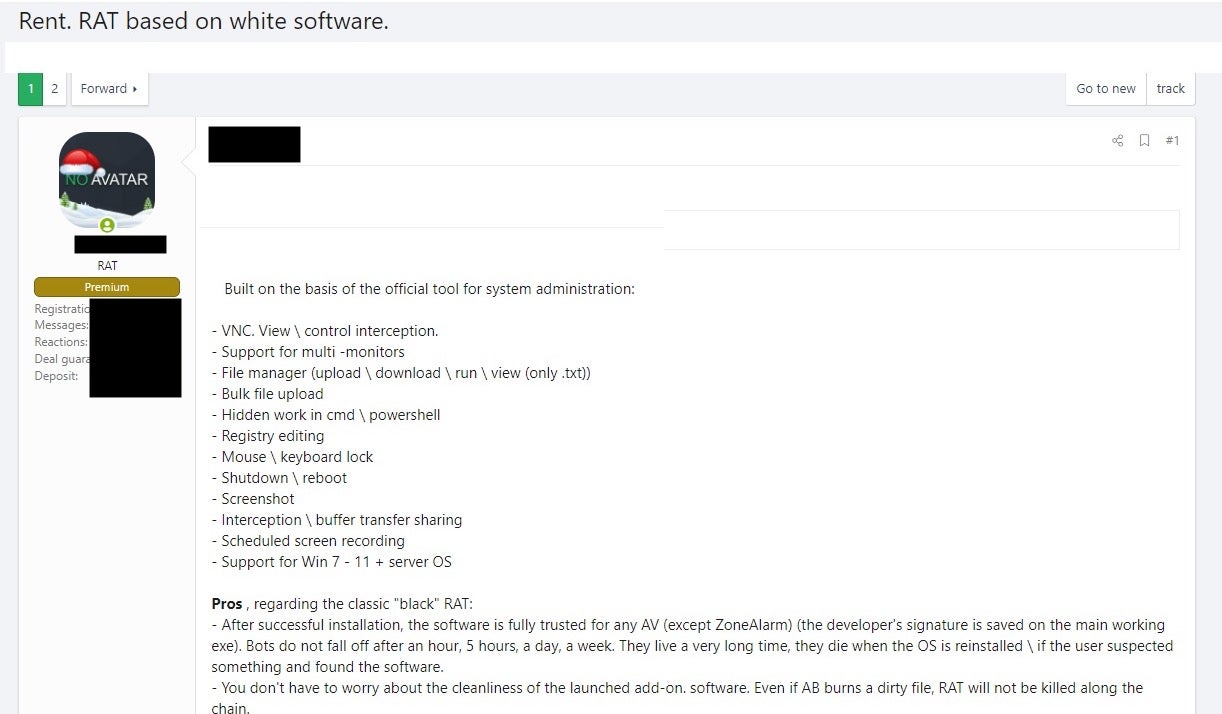
NetSupport RAT is based on NetSupport Manager, a legitimate tool which is frequently used by bad actors for malicious purposes in ways similar to TeamViewer. NetSupport Manager, used maliciously or otherwise, provides full and complete control over the target device. Once the client has been installed, attackers can access, acquire, and manipulate any data on the device (exfiltrate data, execute additional payloads). In addition, the software allows at least the following:
- Real-time screen monitoring, optimized for monitoring multiple devices
- Taking control or redirect user screens
- Capturing screenshots, audio, video
Malicious versions are constantly being sold or rented out via underground crime marketplaces.
As NetSupport Manager is a legitimate tool that has a long history of development, it is highly attractive to attackers as it can be relied on to work ‘out of the box’. Additionally, it is thoroughly documented and actively supported: benefits that are less likely with custom-built malware that provides similar functionality such as Andromeda, Nanocore, CirenegRAT, Dark Comet and others.
Malicious use of NetSupport Manager (aka NetSupport RAT) has been observed since at least late 2017. The use of “legitimate” or COTS (Commercial off the Shelf) tools is highly beneficial to attackers when attempting to achieve the greatest degree of stealth. Custom-written malware can often be detected by some layer of protection, such as EPP and EDR tools, so it is often advantageous to utilize a legitimate tool, even if it takes some creativity to deliver the remote software client.
ASEC reported that the NetSupport RAT droppers were delivered via phishing emails that entice targets to install a “Pokemon card game”. On doing so, the victim unknowingly installs the NetSupport RAT, a doctored version of the NetSupport Manager client (client32.exe) that gives the attacker immediate and direct control of the infected device. While this specific attack was centered around the Pokemon theme, other phishing lures are known to be used.
Some recent NetSupport RAT campaigns utilize .ISO files as droppers. This allows the attackers to evade certain types of detection. This technique has been used by ransomware actors as well such as by both Maze and Ragnar Locker.
When opened, the ISO files will contain either the NetSupport RAT installer (with configs/support files) or a .LNK file redirecting the victim to said installer.
Technical Details
A typical example of this kind of .ISO file is the sample CLF_security.iso (288603f501926756c236e368a1fdc7d128f4f9a1).
This particular .ISO contains an embedded .EXE file (CLFSECUR.EXE) which is then utilized to drop and execute the installer for NetSupport RAT.
Sample 4233ff7941da62b86fc2c2d92be0572c9ab534c8 has been observed in multiple ISO files masquerading as legitimate software, including:
- CodeTwo Exchange Manager
- PCFresh 2022 SDK Tools
- Google Chrome
- Google Crash Handler
- Steelray Project Setup
- BrowserRenew.iso
- CLFsecurity.ISO
- Cloudflare_security_setup.iso
The RAT installation is disguised to look similar to a Google Chrome installation.

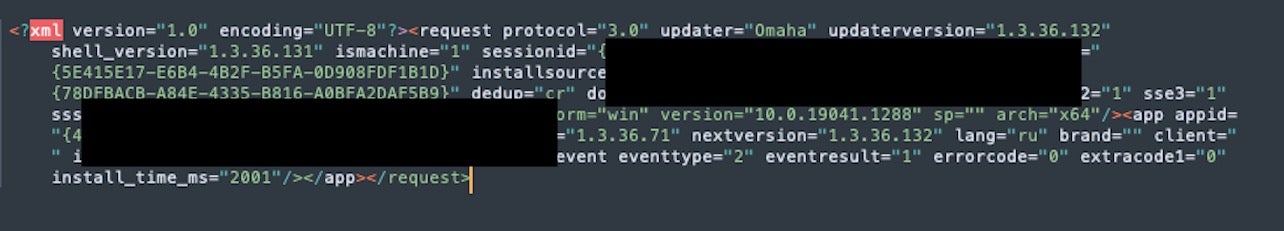
The sample is obfuscated via the Babadeda crypter. When executed, a base64 encoded string is used to specify various parameters including sessionID and other critical values to the NetSupport connection.
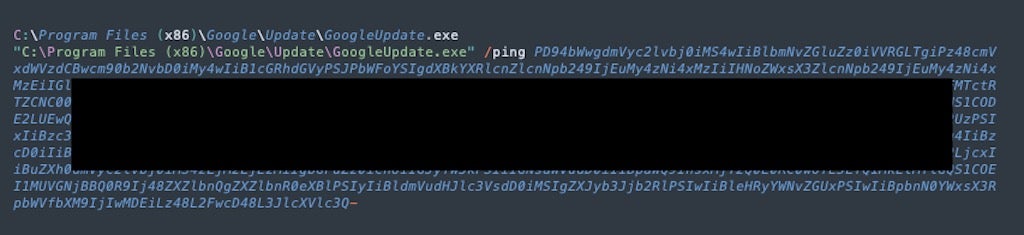
The command decodes to look similar to the following:
Persistence for the RAT is achieved via registry entry, and a shortcut to the installed RAT executable is written to the Startup folder. For example:
~\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\NetSupport.url
In this case, the shortcut links to \AppData\Roaming\Steelray Project Viewer. In addition, the sample generates a scheduled task with multiple triggers.
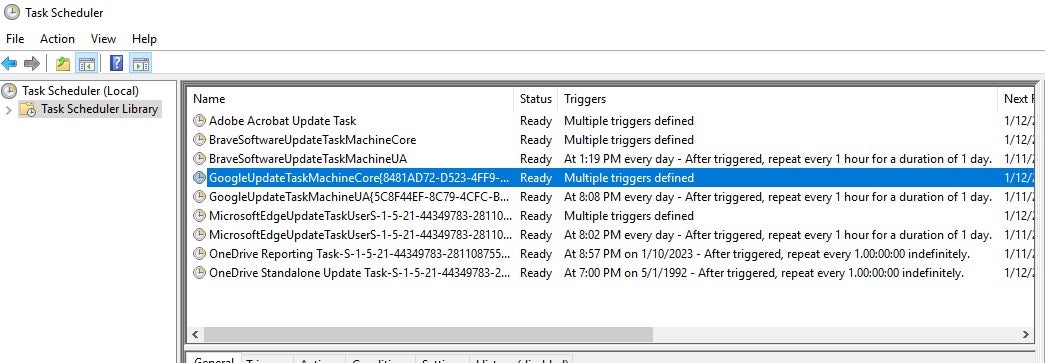
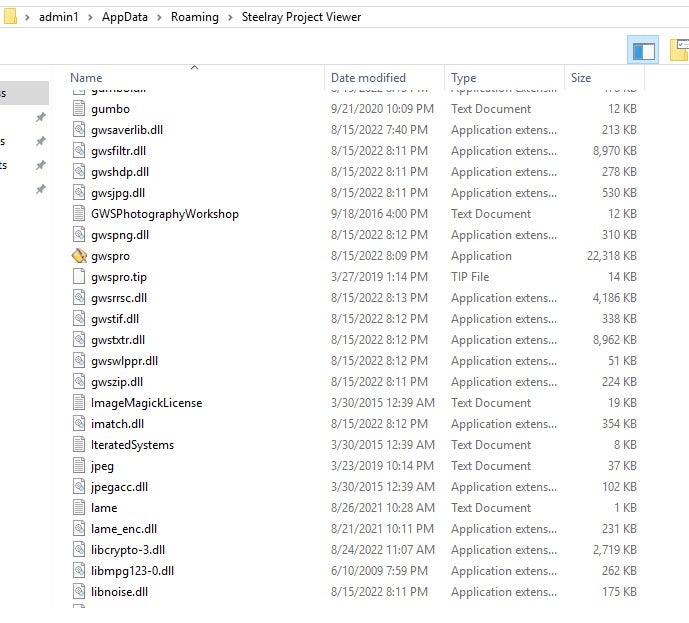
The RAT performs a number of discovery operations to understand its host environment. Network adapter details are pulled via GetAdaptersAddresses. Additional data is gleaned via WMI queries such as:
SELECT * FROM Win32_ComputerSystem SELECT * FROM Win32_SystemEnclosure
The malware deploys some anti-analysis measures such as attempting to detect the presence of a debugger via IsDebuggerPresent, and all running processes are enumerated and logged via EnumProcesses (32-bit processes). Launch behavior, including delays in execution or outgoing connection, can be controlled by the attacker. For example, Sleep statements may be used to delay execution by hours in order to trick sandboxes used in malware analysis or simply to disguise the association between the infection and the social engineering event from the user.
Network requirements vary across different NetSupport Manager configurations and sessions. In the analyzed sample, the client opens a port on TCP 50275 to receive network connections.
NetSupport RAT has the ability to drop and execute additional components. In this particular campaign, system/log data and executable code is dropped into %temp%.
Data files and executables are also written to ~\Program Files (x86) \Google\Temp. These files are all self-deleted after launch or full installation of the attacker configuration. A large number of legitimate Google Chrome support files are also written to this location. These are used by the malware in order to facilitate the fake Google Chrome installation.
Conclusion
NetSupport Manager is a long-standing tool which, like TeamViewer, has unfortunately attracted ample use by cybercriminals. NetSupport RAT, once installed, is very robust and powerful, and threat actors are able to masquerade the dropper or installer in any way they see fit. In addition, threat actors using this tool are very quick to update their lures and find ways to entice their victims into installing the malicious remote control software.
SentinelOne Singularity™ provides protection against malicious behaviors associated with NetSupport RAT.
Indicators of Compromise
SHA1 Samples
593966f38d6b062bec8534ec070a194ac3a3c3d8
3a511941b09fdfed1b53bd89e55be7a3211b19c2
16cf01d8e0753e4b6fac781266d033996af6731d
f1c454645ab0adec41765f29861a5b5dd9bda313
0ef99e15452154c240f80c874384d04c46b154a0
ec7e8093b8d35a0e6fbf7b1869d685f0be0e8108
dfc9b696267ae466c6ffa44e63e314df79264afd
4c5771b7fb683b160cb1f7396d39dd706aa7021d
ee3c0579cbcdb5f50ff8cd750a59d89d7757d7a4
288603f501926756c236e368a1fdc7d128f4f9a1
06906aee0ddba30e560e4b60e140e0c098519bb2
7c090065de1090fa92ff01f06739fbca04e6936d
61679dbe1d13d9c25000142fd51b9f4e952a7098
2d6b1900e093c9c8bcce642792e3fadc90b3b0ac
171692daf0a136154edde6e22c791d238ae8c1d0
4233ff7941da62b86fc2c2d92be0572c9ab534c8
DNS/Domains
she32rn1[.]com
MITRE ATT&CK
T1219 – Remote Access Software
T1053.005 – Scheduled Task/Job: Scheduled Task
T1047 – Windows Management Instrumentation
T1564.001 – Hide Artifacts: Hidden Files and Directories
T1547.001 – Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder
T1564.003 – Hide Artifacts: Hidden Window
T1036 – Masquerading
T1112 – Modify Registry
T1406.002 – Obfuscated Files or Information: Software Packing
T1049 – System Network Connections Discovery
T1083 – File and Directory Discovery
T1057 – Process Discovery
T1012 – Query Registry
T1571 – Non-Standard Port
如有侵权请联系:admin#unsafe.sh