RuoYi漏洞点
RuoYI指纹 => app="若依-管理系统"RuoYI版本 => ry-ui.js?v=4.2.0 | ry-ui.css?v=4.2.0Shiro RCE漏洞分析Pom.xml:20com/ru
2022-12-18 15:8:37
Author: 仙友道(查看原文)
阅读量:58
收藏
RuoYI版本 => ry-ui.js?v=4.2.0 | ry-ui.css?v=4.2.0Shiro RCE
漏洞分析
com/ruoyi/framework/config/ShiroConfig.java:325File Download
漏洞分析
ResourceDownload
V4.1.0 <= RuoYI <= V4.5.0com.ruoyi.common.utils.file.FileUtils#writeBytescom.ruoyi.web.controller.common.CommonController#resourceDownloadFileDownload
com/ruoyi/common/utils/file/FileUtils.java:38com/ruoyi/web/controller/common/CommonController.java:57 任意文件下载File Delete
漏洞分析
com/ruoyi/common/utils/file/FileUtils.java:85com/ruoyi/web/controller/common/CommonController.java:60 任意文件删除Sql Injection
漏洞分析
SysRoleMapper
src/main/resources/mapper/system/SysRoleMapper.xml#58=> com.ruoyi.system.mapper.SysRoleMapper#selectRoleList=> com.ruoyi.system.service.impl.SysRoleServiceImpl#selectRoleList=> com.ruoyi.web.controller.system.SysRoleController#list=> com.ruoyi.system.domain.SysRole#dataScopeSysDeptMapper
src/main/resources/mapper/system/SysDeptMapper.xml#51=> com.ruoyi.system.mapper.SysDeptMapper#selectDeptList=> com.ruoyi.system.service.impl.SysDeptServiceImpl#selectDeptList=> com.ruoyi.web.controller.system.SysDeptController#listSysUserMapper
src/main/resources/mapper/system/SysUserMapper.xml#81=> com.ruoyi.system.mapper.SysUserMapper#selectUserList=> com.ruoyi.system.service.impl.SysUserServiceImpl#selectUserList=> com.ruoyi.web.controller.system.SysUserController#listFastjson RCE
漏洞分析
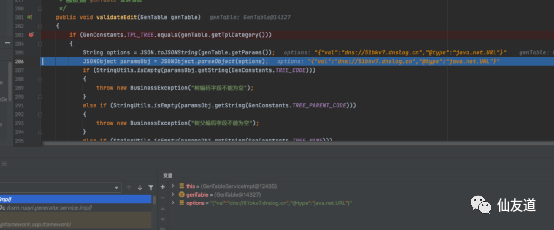
com.ruoyi.generator.service.impl.GenTableServiceImpl#validateEditRCE
V3.3.0 <= RuoYi <= v4.6.2漏洞分析
com.ruoyi.quartz.util.JobInvokeUtil#invokeMethod(com.ruoyi.quartz.domain.SysJob)com.ruoyi.quartz.util.QuartzDisallowConcurrentExecution#doExecute调用invokemethod方法,此处为JOB具体任务类com.ruoyi.quartz.controller.SysJobController#run3、调用目标字符串的参数为:支持字符串,布尔类型,长整型,浮点型,整型
4、调用目标方法除了为Public,无参,还需要具有执行代码/命令的能力
Thymeleaf SSTI
漏洞分析
localRefreshTask
com.ruoyi.web.controller.demo.controller.DemoFormController#localRefreshTaskCacheController
com.ruoyi.web.controller.monitor.CacheController#getCacheNamescom.ruoyi.web.controller.monitor.CacheController#getCacheKeyscom.ruoyi.web.controller.monitor.CacheController#getCacheValueShiro 多个认证绕过、Spring Framework反射型文件下载漏洞、FastJson RCE暂未学习,后续学了回来填坑。Reference
https://doc.ruoyi.vip/ruoyi/document/kslj.html#%E5%8E%86%E5%8F%B2%E6%BC%8F%E6%B4%9E
文章来源: http://mp.weixin.qq.com/s?__biz=Mzg3NjYwNDgzMQ==&mid=2247485706&idx=1&sn=53c26249c714a98026308d8798cff4b1&chksm=cf2ef5faf8597cec705c58f43c7a9d716238128413cb5823e98f02915b2ee92ff528ac7c990d#rd
如有侵权请联系:admin#unsafe.sh
