Introduction
In this blog we will be taking a quick dive into Empire, a popular open-source post-exploitation framework. Empire provides an adversary with the capability to expand his foothold in a victim’s environment by leveraging hundreds of modules, RATs in multiple languages and stealthy C2 mechanisms.
It was initially released back in 2015. The original GitHub repository has since then been archived. However, there are multiple forks that continue to see active development to expand Empire’s capabilities. One such fork is by BC-SECURITY. They also maintain another repository that provides GUI support for Empire.
Empire offers several advanced features such as: –
- Agents in various languages such as PowerShell, python 3, C# and IronPython 3.
- Massive library of support tools.
- Various C2 mechanisms such as OneDrive, Dropbox, php, http/s and Malleable profiles.
- Modular design for adding plugins and tools.
- Customizable Bypasses.
- Integrated obfuscation via Invoke-Obfuscation and ConfuserEx.
- In-memory .NET assembly execution.
- Encrypted communication between client and server.
- Available on Kali, Ubuntu, Debian and docker
and much more …
These features make Empire a sophisticated tool in the adversary’s arsenal.
Adversary Usage
In this section we will aim to identify how relevant Empire is as a threat based on its popularity amongst various advanced threat actors.
A recent uscert alert on a new ransomware gang called Vice Society highlighted their usage of Empire for Lateral Movement. They have been observed to target healthcare and educational organizations.
Wizard Spider has used Empire for Lateral Movement, Credential Dumping and as a C2 for Trickbot modules.
Turla has used Empire’s injection modules. They have also used Empire’s Drobox and OneDrive C2 mechanisms.
Leviathan has used Empire for Persistence, Privilege Escalation, Credential Access, Discovery, and Lateral Movement.
A joint report by cybersecurity authorities of Australia, Canada, New Zealand, the UK, and USA on the five most popular publicly available hacking tools have identified Empire for its lateral movement capabilities.
Other well-known adversaries have also used Empire such as FIN12, DarkHydrus, APT33, APT19, APT41 etc.
Therefore, Empire is a popular choice as an off the shelf fully functional post exploitation framework for actors.
Empire in the Wild
We dumped positive Empire detections over the last three months from Virustotal to identify sample trends as well as active campaigns in the wild. After verification, we had a sample set of 61 unique initial stagers.
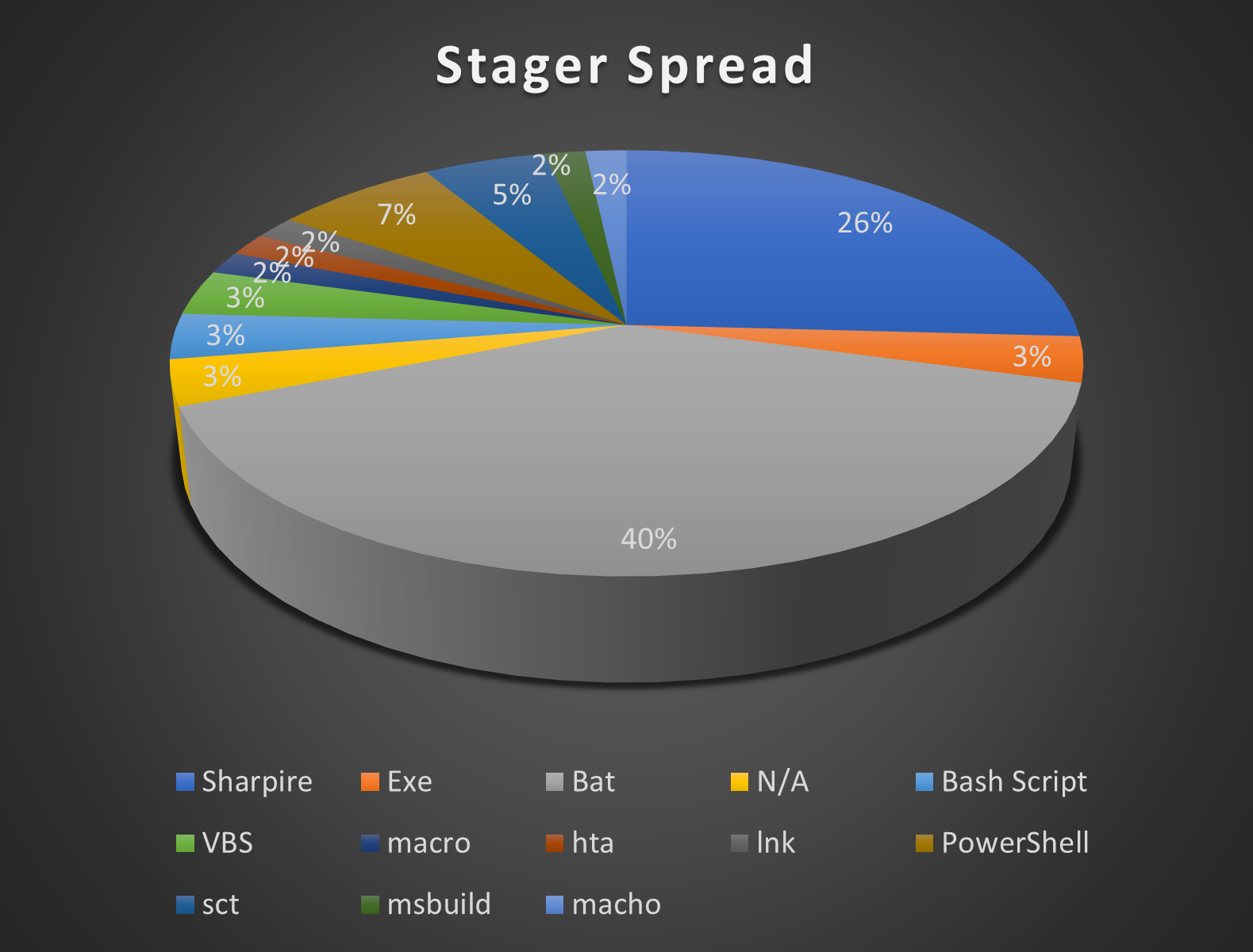
- Most of the samples collected target windows (94.8%) followed by Linux (3.4%) and Mac (1.7%).
- Bat stagers were the most popular, accounting for 39% of the entire sample set. Sharpire stagers followed next with 26%.
- A surprising thing that we observed was that about 98% of the stagers did not bother to change the default parameters beyond the server details.
- The stagers also largely provisioned PowerShell agents (72%). This is followed by dotnet (23%) and python (5%). We did not observe any IronPython agents. This shows that for Empire PowerShell still dominates.
- 57% of dotnet samples were obfuscated by ConfuserEx.
Let us look at some of these samples in more detail.
Campaign #1
We identified a campaign that used custom doc files containing embedded macros. The Macro would execute a PowerShell command to download and execute a script from http://xvfghtyua[.]000webhostapp[.]com/sys.ps1. This script is a PowerShell stager that would provision an Empire agent with jobbfinderrr[.]xyz as the C2 server.
Campaign #2
We identified a http server (193[.]117[.]208[.]148) hosting several popular hack tools while also acting as the C2 server for Empire and Metasploit.
- Variants of Cactustorch shellcode injector configured to inject into rundll32.
- Multiple different stagers for Empire.
- Multiple different meterpreter exes with various levels of obfuscation.
- Lazagne
- Notepad++
- Lnk stubs to download execute CactusTorch.
- Empire stager with 193[.]117[.]208[.]146 as C2.
- Process Explorer backdoored with Metasploit.
A user named r3dbU7z has submitted files related to this to MalwareBazaar on 28-10-2022.
Campaign #3
We identified some files that pretended to install cracked software but would end up executing an Empire stager instead.
One such bundle pretends to be an installer for a cracked version of WinRAR but instead executed an exe stager for Empire with a beacon to an AWS (Amazon Web Services) ip (3[.]142[.]141[.]21). We also saw instances of meterpreter for both windows and android also beaconing to this IP.
Another bundle pretends to install a cracked version of “rusher client,” a paid Minecraft mod specifically designed for anarchy servers. It instead has a bat script that starts a generic PowerShell stager that beacons out to an AWS ip (18[.]222[.]107[.]105).
In the next section we will showcase how Qualys can help protect your organization against threats like Empire.
Qualys Multi-Vector EDR Detections
Qualys Multi-Vector Endpoint Detection and Response (EDR) is a dynamic detection and response service powered by the Qualys Cloud Platform. Qualys Multi-Vector EDR detects malware like Empire by unifying multiple context vectors to spot its insertion into a network endpoint. Qualys Cloud Platform provides asset management, vulnerability detection, policy compliance, patch management, and file integrity monitoring capabilities – all delivered with a single agent and cloud-based delivery for a lower total cost of ownership.
Qualys provides a full suite of detections against all the various Empire modules.
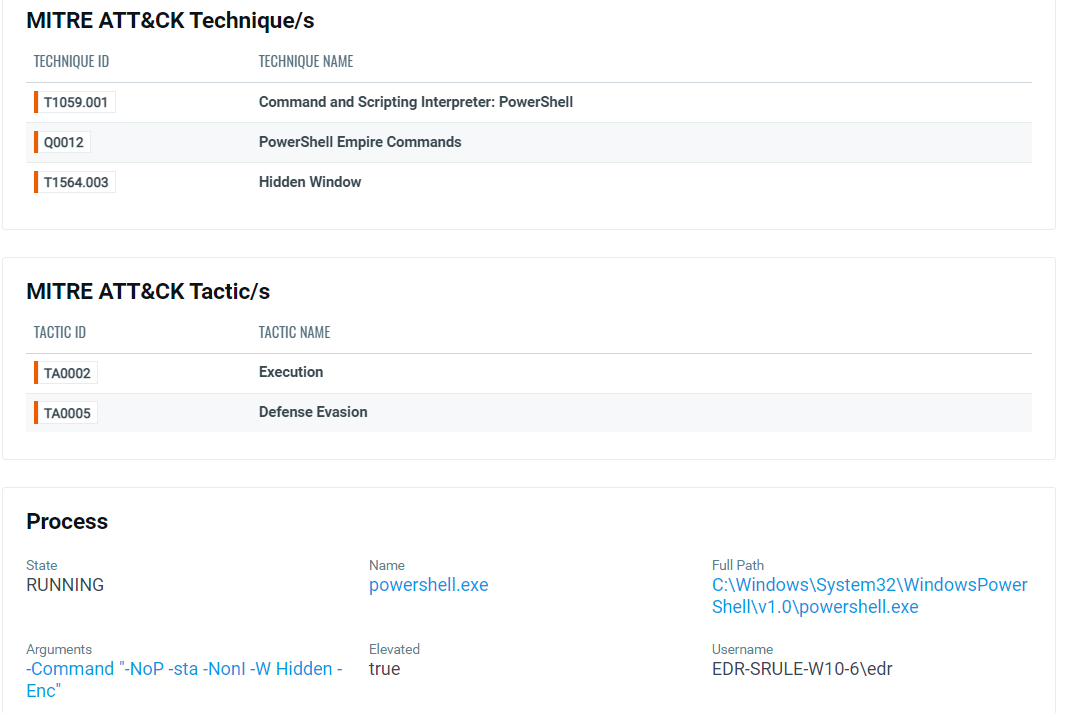
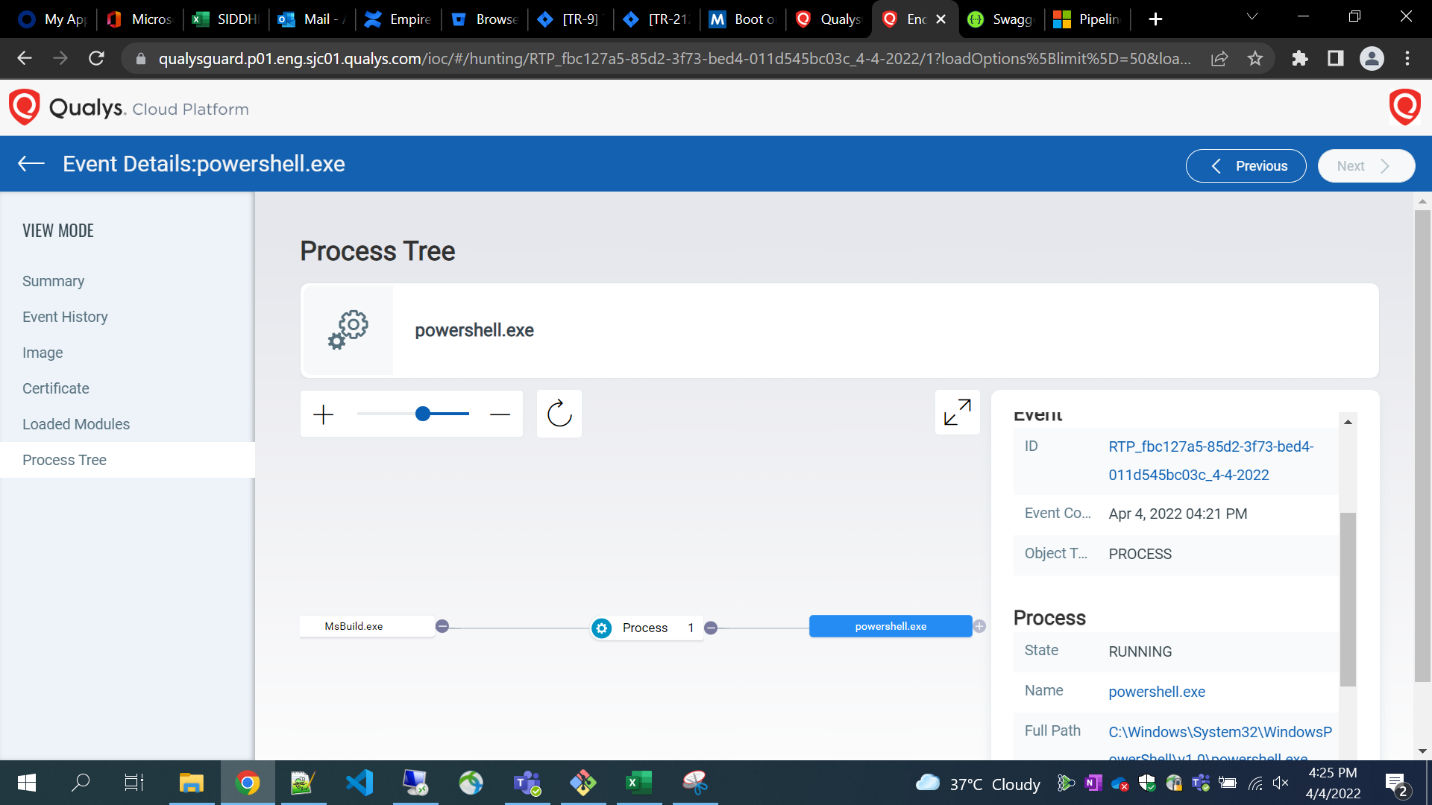
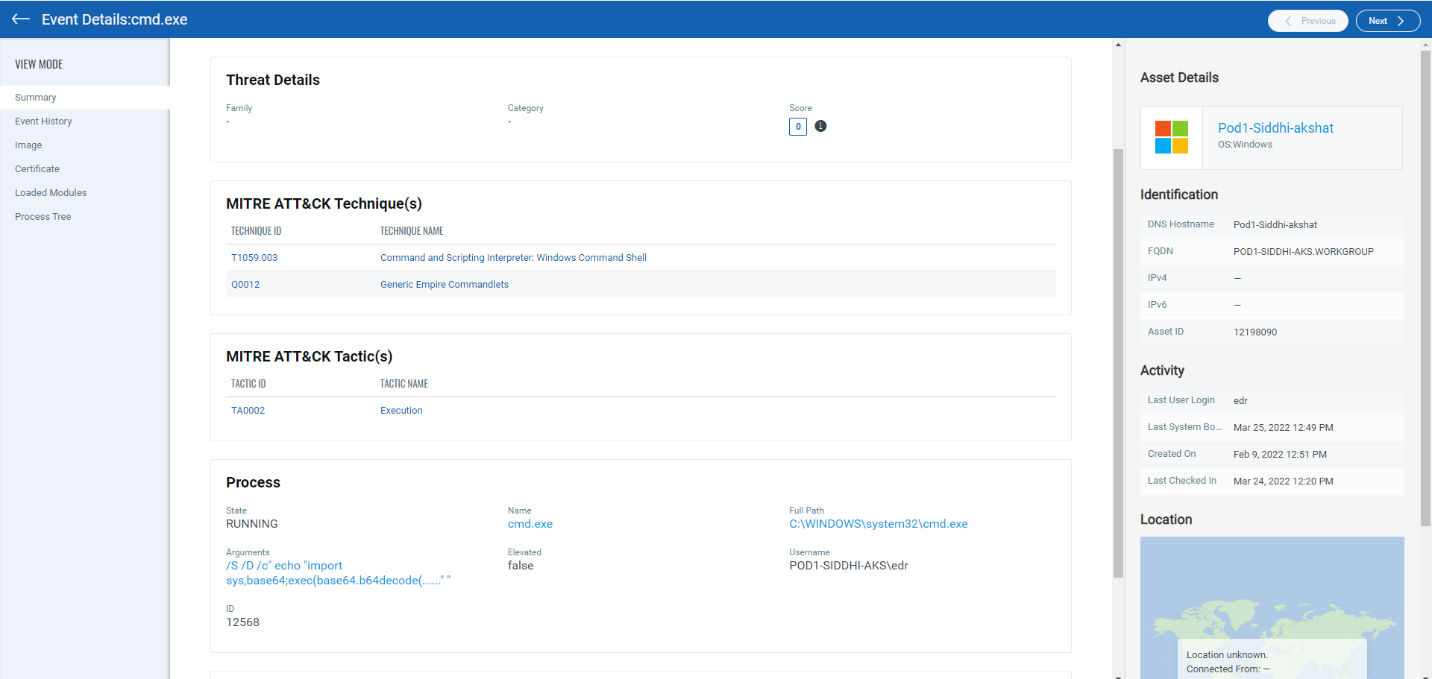
Conclusion
Empire is an impressive post exploitation framework with expansive capabilities. This has led to it becoming a frequent favorite toolkit of several adversaries. In this Blog we went over its features, adversarial usage, and latest trends. Further details about its architecture, components and detection markers can be found in our Threat Thursday webinar for November 2022.
MITRE ATT&CK® Mapping
T1071.001 Application Layer Protocol: Web Protocols
T1071.003 Application Layer Protocol: Mail Protocols
T1102 Web Service
T1059.001 Command and Scripting Interpreter: PowerShell
T1059.006 Command and Scripting Interpreter: Python
T1132.001 Data Encoding: Standard Encoding
T1047 Windows Management Instrumentation
T1127.001 Trusted Developer Utilities Proxy Execution: MSBuild
T1059.005 Command and Scripting Interpreter: Visual Basic
T1218.005 Signed Binary Proxy Execution: Mshta
T1204.002 User Execution: Malicious File