前言:由于之前部署环境损坏实验环境地址由原来192.168.116.200迁移至192.168.116.201
在之前的章节中介绍了如何部署Wazuh indexer以及Garylog,实现了数据的规范化处理,存储安全日志,接下来需要部署EDR采集所有终端上的活动以及行为,提供了对终端上正在发生事件的持续、全面的可见性。EDR通常有两部分组成,部署在终端上的agent以及用于接收终端上报的日志以及威胁分析的manager。
EDR跟传统的杀软存在本质上的区别,杀软用于检测终端上是否存在恶意软件,但现在网络攻击趋于复杂,技战术趋于隐蔽,高级威胁趋于活跃,单纯依靠杀软已经无法满足运营需求,也无法发现隐蔽攻击,EDR相对于杀软可以采集终端行为日志,比如网络连接、命令行执行、用户登录、进程迁移等行为。
开源的EDR种类繁多,此次选择Wazuh server,提供开箱即用功能,例如提供日志分析功能、文件完整性监控、漏洞检测,并且可持续集成,比如允许自定义检测规则、第三方应用调用、RESTful API以及主动响应等功能。
https://documentation.wazuh.com/current/getting-started/components/wazuh-server.html接下来安装Wazuh server
https://documentation.wazuh.com/current/installation-guide/wazuh-server/step-by-step.html第一步:添加Wazuh repository
rpm --import https://packages.wazuh.com/key/GPG-KEY-WAZUHecho -e '[wazuh]\ngpgcheck=1\ngpgkey=https://packages.wazuh.com/key/GPG-KEY-WAZUH\nenabled=1\nname=EL-$releasever - Wazuh\nbaseurl=https://packages.wazuh.com/4.x/yum/\nprotect=1' | tee /etc/yum.repos.d/wazuh.repo
第二步:安装Wazuh server
yum -y install wazuh-manager第三步:配置wazuh manager相关服务
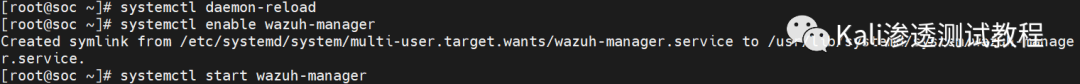
systemctl daemon-reloadsystemctl enable wazuh-managersystemctl start wazuh-manager
第四步:查看服务状态
systemctl status wazuh-manager也可以看到很多wazuh子进程信息
ps auxf | grep wazuh完成Wazuh server安装之后,需要把对应的安全日志转发到Garylog中,以便可以正常进行格式处理以及使用Wazuh indexer进行存储以及搜索使用。
使用浏览器登录Garylog的Web控制台
http://192.168.116.201:9000/gettingstarted点击System->Inputs进入对应页面配置输入源信息,接收Wazuh server的安全日志
在下拉框中选择Raw/Plaintext TCP
点击右边绿色Launch new input按钮,配置详细输入源信息,其中Title命名为Wazuh server,Bind address值默认为0.0.0.0,Port值默认为5555,保持默认即可,如果是生产环境建议开启TLS传输加密,保障数据的传输安全。
点击Save保存配置如下图所示
查看端口监听,可以看到5555监听端口
netstat -npltd完成上述步骤以后,agent会把终端上收集到的日志发送给Wazuh server,Wazuh server收到之后根据规则匹配,满足规则的写进/var/ossec/logs/alerts/alerts.json文件中,接下来需要利用Fluent Bit读取alerts.json这个文件并且将其发送到Garylog中。
接下来使用脚本自动安装Fluent Bit
curl https://raw.githubusercontent.com/fluent/fluent-bit/master/install.sh脚本具体为如下所示
//install.sh#!/usr/bin/env bashset -e# Provided primarily to simplify testing for staging, etc.RELEASE_URL=${FLUENT_BIT_PACKAGES_URL:-https://packages.fluentbit.io}RELEASE_KEY=${FLUENT_BIT_PACKAGES_KEY:-https://packages.fluentbit.io/fluentbit.key}echo "================================"echo " Fluent Bit Installation Script "echo "================================"echo "This script requires superuser access to install packages."echo "You will be prompted for your password by sudo."# Determine package type to install: https://unix.stackexchange.com/a/6348# OS used by all - for Debs it must be Ubuntu or Debian# CODENAME only used for Debsif [ -f /etc/os-release ]; then# Debian uses Dash which does not support source# shellcheck source=/dev/null. /etc/os-releaseOS=$( echo "${ID}" | tr '[:upper:]' '[:lower:]')CODENAME=$( echo "${VERSION_CODENAME}" | tr '[:upper:]' '[:lower:]')elif lsb_release &>/dev/null; thenOS=$(lsb_release -is | tr '[:upper:]' '[:lower:]')CODENAME=$(lsb_release -cs)elseOS=$(uname -s)fi# Clear any previous sudo permissionsudo -k# Now set up repos and install dependent on OS, version, etc.# Will require sudocase ${OS} inamzn|amazonlinux)# We need variable expansion and non-expansion on the URL line to pick up the base URL.# Therefore we combine things with sed to handle it.sudo sh <<SCRIPTrpm --import $RELEASE_KEYcat << EOF > /etc/yum.repos.d/fluent-bit.repo[fluent-bit]name = Fluent Bitbaseurl = $RELEASE_URL/amazonlinux/VERSION_ARCH_SUBSTRgpgcheck=1repo_gpgcheck=1gpgkey=$RELEASE_KEYenabled=1EOFsed -i 's|VERSION_ARCH_SUBSTR|\$releasever/\$basearch/|g' /etc/yum.repos.d/fluent-bit.repocat /etc/yum.repos.d/fluent-bit.repoyum -y install fluent-bitSCRIPT;;centos|centoslinux|rhel|redhatenterpriselinuxserver|fedora|rocky|almalinux)sudo sh <<SCRIPTrpm --import $RELEASE_KEYcat << EOF > /etc/yum.repos.d/fluent-bit.repo[fluent-bit]name = Fluent Bitbaseurl = $RELEASE_URL/centos/VERSION_ARCH_SUBSTRgpgcheck=1repo_gpgcheck=1gpgkey=$RELEASE_KEYenabled=1EOFsed -i 's|VERSION_ARCH_SUBSTR|\$releasever/\$basearch/|g' /etc/yum.repos.d/fluent-bit.repocat /etc/yum.repos.d/fluent-bit.repoyum -y install fluent-bitSCRIPT;;ubuntu|debian)# Remember apt-key add is deprecated# https://wiki.debian.org/DebianRepository/UseThirdParty#OpenPGP_Key_distributionsudo sh <<SCRIPTexport DEBIAN_FRONTEND=noninteractivemkdir -p /usr/share/keyrings/curl $RELEASE_KEY | gpg --dearmor > /usr/share/keyrings/fluentbit-keyring.gpgcat > /etc/apt/sources.list.d/fluent-bit.list <<EOFdeb [signed-by=/usr/share/keyrings/fluentbit-keyring.gpg] $RELEASE_URL/${OS}/${CODENAME} ${CODENAME} mainEOFcat /etc/apt/sources.list.d/fluent-bit.listapt-get -y updateapt-get -y install fluent-bitSCRIPT;;*)echo "${OS} not supported."exit 1;;esacecho ""echo "Installation completed. Happy Logging!"echo ""
编辑Fluent Bit配置文件
vi /etc/fluent-bit/fluent-bit.conf将默认的配置文件修改成下图所示,IP地址根据实际情况替换
[SERVICE]flush 5daemon Offlog_level infoparsers_file parsers.confplugins_file plugins.confhttp_server Offhttp_listen 0.0.0.0http_port 2020storage.metrics onstorage.path /var/log/flb-storage/storage.sync normalstorage.checksum offstorage.backlog.mem_limit 5MLog_File /var/log/td-agent-bit.log[INPUT]name tailpath /var/ossec/logs/alerts/alerts.jsontag wazuhparser jsonBuffer_Max_Size 5MBBuffer_Chunk_Size 400kstorage.type filesystemMem_Buf_Limit 512MB[OUTPUT]Name tcpHost 192.168.116.201Port 5555net.keepalive offMatch wazuhFormat json_linesjson_date_key true
接下来启动Fluent Bit服务并设置开机自启动
systemctl start fluent-bitsystemctl enable fluent-bit
查看日志
tailf /var/log/td-agent-bit.log接下来使用ssh重新登录并同时查看Garylog数据源网络连接
点击蓝色Show received messages按钮,查看接收到的日志
这样就完成了OpenSource EDR安装以及数据转发,欢迎订阅收看开源SOC实现(四)-OpenSource EDR配置以及agent安装
如有侵权请联系:admin#unsafe.sh