The extraction method or methods available for a pa 2022-11-24 20:54:21 Author: blog.elcomsoft.com(查看原文) 阅读量:21 收藏
The extraction method or methods available for a particular iOS device depend on the device’s hardware platform and the installed version of iOS. While logical acquisition is available for all iOS and iPadOS devices, more advanced extraction methods are available for older platforms and versions of iOS. But what if more than one way to extract the data is available for a given device? In this guide, we’ll discuss the applicable acquisition methods as well as the order in which they should be used.
For iOS and iPad OS devices, low-level extraction requires exploiting undocumented vulnerabilities in order to access the file system and some encryption keys required to decrypt the keychain. Such exploits are typically discovered in older hardware platforms and older versions of iOS. In general, devices released less than five years ago and running a recent version of iOS are immune to known public exploits and can be only extracted with logical acquisition. Logical acquisition is universally available on iOS and iPadOS devices regardless of their hardware platform and version of iOS. However, logical acquisition on devices running tvOS and watchOS will be limited as there is no backup services on such devices.
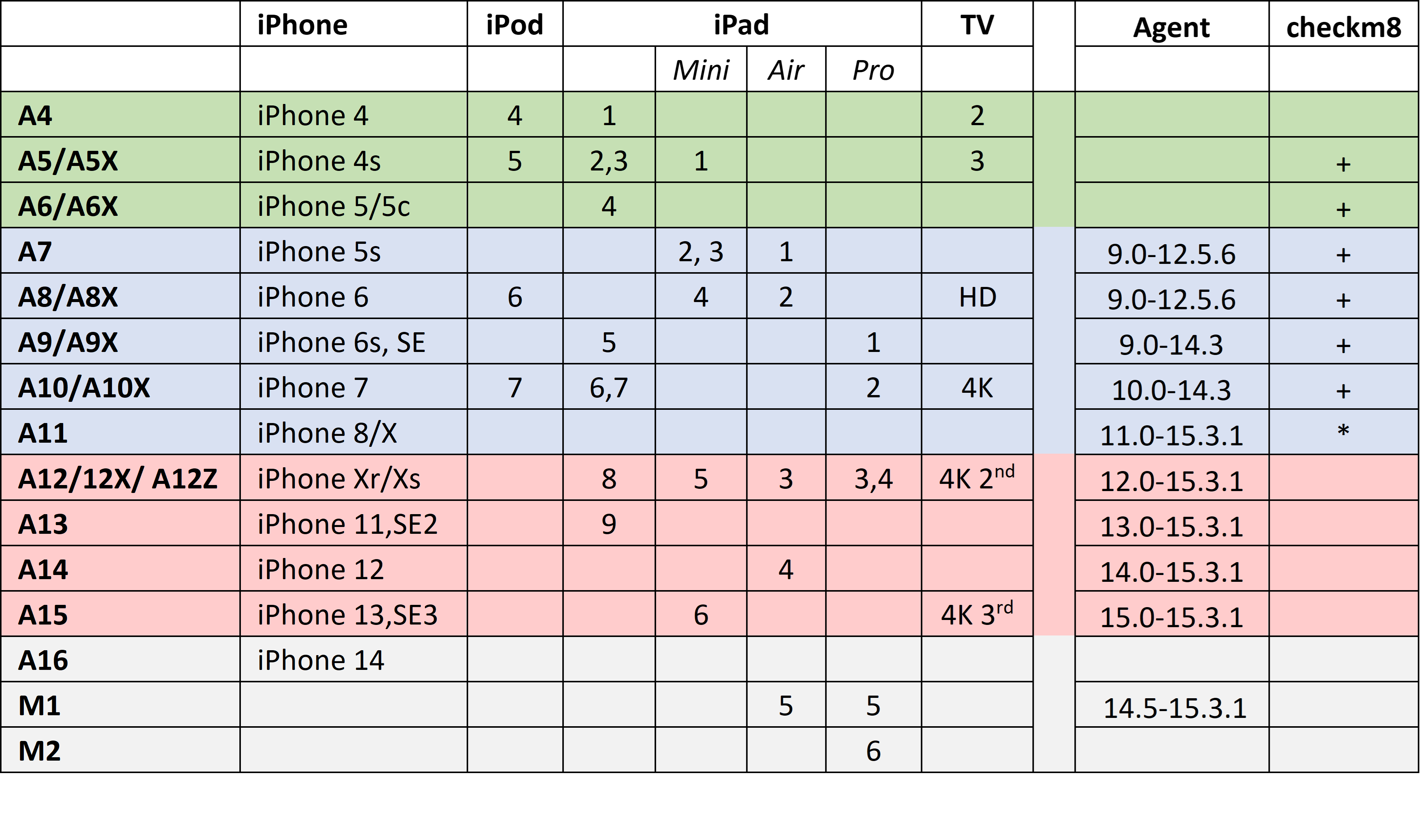
Low-level extraction methods are available on older platforms and versions of iOS. These methods include checkm8 (a booloader-based exploit) and Elcomsoft’s software-based low-level extraction agent. Please refer to the following table to determine which acquisition methods are available to your device:
Notes:
- The iPhone SE 3 (2022) was released with iOS 15.4 on board, which is not supported by the extraction agent.
- For iOS 15.2-15.3.1 the extraction agent can only extract the file system but not the keychain.
- checkm8 extraction of Apple A11 devices running iOS 14 and 15 is only possible once the screen lock passcode is empty.
- No agent-based extraction is available for checkm8-capable Apple TV devices.
- checkm8 support for iOS 16 devices is under development and will be available soon for all supported devices.
- The extraction agent is in active development, with full support for iOS 15.5 and lower (including keychain decryption) coming soon.
Choosing the right extraction method
When more than one extraction method is available, the order matters. We recommend the following workflow.
Note: logical extraction is available for all generations of Apple hardware and all supported versions of iOS.
For older devices compatible with checkm8 (this includes iPhone devices up to and including the iPhone 8, 8 Plus, and iPhone X, as well as the corresponding iPad, Apple Watch, and Apple TV models):
- Only use checkm8 extraction. Attempt other methods if and only if the checkm8 extraction fails.
The checkm8 extraction is the most sophisticated extraction method available for Apple devices that have a vulnerability in their bootloader. Our implementation of checkm8 offers clean, forensically sound extractions with repeatable, verifiable results. If you’ve used checkm8, you have already received the fullest set of data extractable from the device; there is no need to use any other acquisition method.
Using checkm8 extraction: checkm8 Extraction Cheat Sheet: iPhone and iPad Devices
For devices not compatible with checkm8 but running a version of iOS supporting the extraction agent (currently, iOS 9.0 through 15.3.1 for devices supporting these OS versions):
- First, make a local backup with iOS Forensic Toolkit. If the backup is password-protected, make a backup nevertheless. Do not reset the backup password in device settings.
- Use the extraction agent. The backup password will be extracted along with the rest of the data.
For all other devices that support neither checkm8 nor the extraction agent, including the iPhone 14 range:
- First, make a local backup with iOS Forensic Toolkit. If the backup is password-protected, make a backup nevertheless. Do not reset the backup password in device settings. If the backup password is empty, the tool automatically sets a temporary password of “123”.
- Extract all other data that can be obtained through the advanced logical process. This includes media files (photos, videos and metadata), shared application data, some system logs and device information.
- If the backup has an unknown password, attempt a local attack with Elcomsoft Phone Breaker or Elcomsoft Distributed Password Recovery. If unsuccessful, consider resetting the backup password through device settings. Mind the risks and consequences.
Using advanced logical extraction: Advanced Logical Extraction with iOS Forensic Toolkit 8: Cheat Sheet
Conclusion
This publication should help experts better understand their options when extracting Apple devices based on their hardware platform and OS.
REFERENCES:
![]()
Elcomsoft Distributed Password Recovery
Build high-performance clusters for breaking passwords faster. Elcomsoft Distributed Password Recovery offers zero-overhead scalability and supports GPU acceleration for faster recovery. Serving forensic experts and government agencies, data recovery services and corporations, Elcomsoft Distributed Password Recovery is here to break the most complex passwords and strong encryption keys within realistic timeframes.
Elcomsoft Distributed Password Recovery official web page & downloads »
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
![]()
Elcomsoft Mobile Forensic Bundle
The complete mobile forensic kit enables law enforcement, corporate and government customers to perform physical, logical and over-the-air acquisition of smartphones and tablets, break mobile backup passwords and decrypt encrypted backups, view and analyze information stored in mobile devices. Bundle consists of all currently available mobile forensic tools offering the best value on the market.
Elcomsoft Mobile Forensic Bundle official web page & downloads »
![]()
Elcomsoft Phone Breaker
Gain full access to information stored in FileVault 2 containers, iOS, Apple iCloud, Windows Phone and BlackBerry 10 devices! Download device backups from Apple iCloud, Microsoft OneDrive and BlackBerry 10 servers. Use Apple ID and password or extract binary authentication tokens from computers, hard drives and forensic disk images to download iCloud data without a password. Decrypt iOS backups with GPU-accelerated password recovery.
如有侵权请联系:admin#unsafe.sh