Sandfly 4.0 has been released and includes our powerful new SSH key and credential auditing feature: SSH Hunter. This new feature allows you to track SSH key usage across your Linux fleet automatically.
In addition to this, we also have many other upgrades:
eBPF rootkit detection and related activity.
Restricted scheduling windows.
Evasion resistant user-defined binary names.
New UI look and refinements.
Many improvements and expanded threat coverage.
SSH Hunter
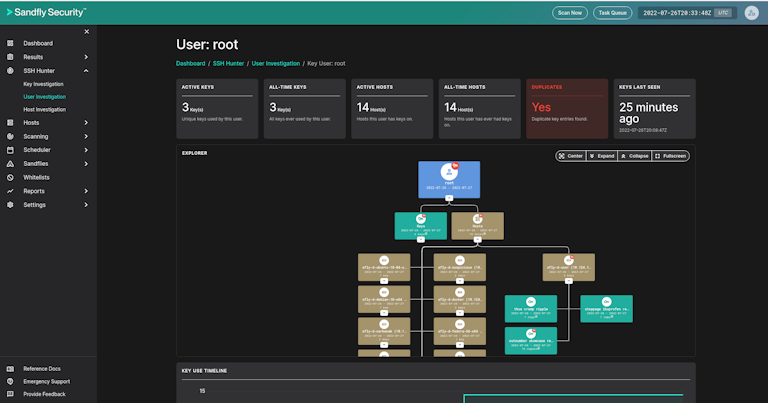
SSH Hunter is a powerful tool to track SSH key usage across your Linux systems. SSH Hunter leverages Sandfly's agentless architecture to give you the ability to:
Track keys across all your Linux systems.
See which users can access your Linux systems.
Discover when keys were first and last seen, key types, and key locations.
Visualize how SSH keys, users, and host access are distributed.
Find anomalies such as duplicate keys or users with new keys unexpectedly added.
Rapidly respond to incidents involving compromised SSH credentials.
Search for new keys, old keys, banned keys, and much more.
With Sandfly's SSH Hunter, you now have the ability to quickly track and identify issues with SSH keys. Sandfly let's you find SSH credential problems before they become a major incident.
Sandfly's SSH hunter feature is enabled by default to begin profiling users' public keys if we find any on the host. All keys are then inventoried and made available for tracking and searching after your hosts are scanned and kept up to date automatically every time we check your systems.
If you want to read more about this new feature please see this overview:
In-depth documentation on how to use the new feature is available here:
Sandfly now has modules to detect emerging threats using eBPF capabilities. In this release we've added in signatures to find common types of eBPF rootkits. We've also added the ability for customers to scan for processes running with eBPF features for incident response and reconnaissance use.
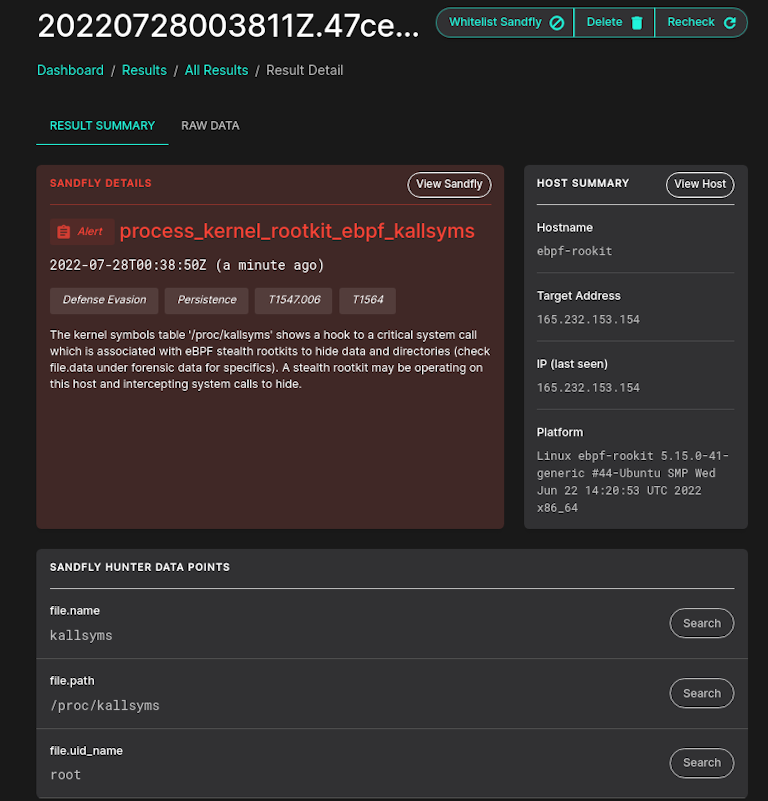
Restricted Scheduling Window
If you run a very sensitive production network and want to ensure that any impacts are limited to only certain hours of the day, Sandfly now does that. Simply add your schedule like normal, and at the bottom of the form enable the restricted scan window with the times you want.
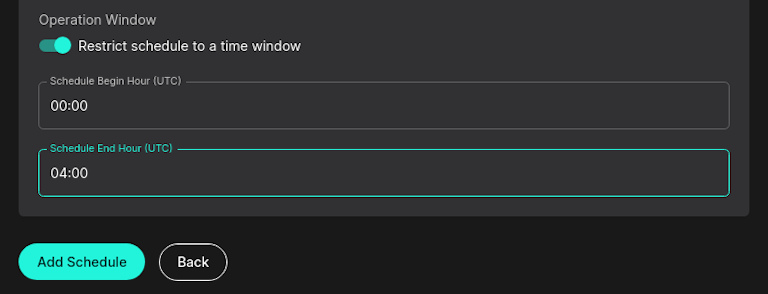
Evasion Resistant Binary Names
You can now configure Sandfly to modify what binary name it runs under on remote systems. The default name is sandfly and this can disclose to attackers that a scan is running on the remote system. Now you can supply a list of names you want us to run under on remote hosts.
With this feature we will randomly select one of the names supplied when we execute on remote systems. This ability gives the product further evasion resistance against being bypassed during normal scans. It also provides additional protection for incident response teams wishing to keep a low profile during their investigations.
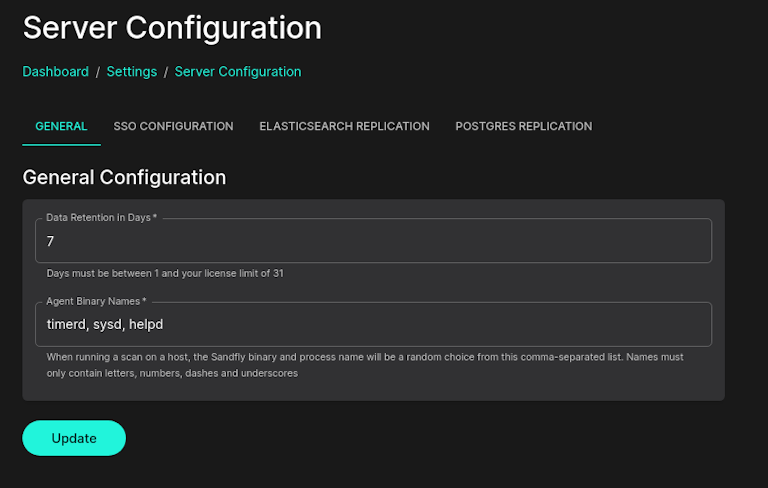
To make use of this new feature, go under server configuration and enter in a comma separated list of names.
UI Refreshed
The Sandfly UI has been completely refreshed. It features refinements across the board in terms of usability and color. Data views have been updated along with more intuitive interface updates to results, hosts and more. Filters for results and hosts have been improved along with new configuration options and more.
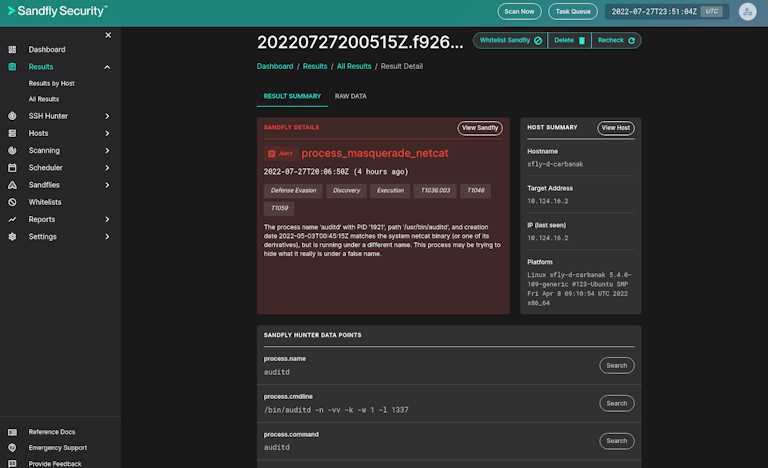
Expanded Sandfly Coverage
Sandfly checks have been expanded and refined to broaden coverage and add new detection methods for attack variations. For instance, we have expanded our ability to detect obfuscated IP addresses or process hiding methods. We now have over 1,100 modules for attack detection, incident response, reconnaissance and more.
Free Updates
All users are eligible for updates to 4.0. The update is in-place and requires no changes on your part to run it today. Upgrade instructions are below:
The SSH Hunter feature is for licensed customers only. If you'd like to try out the SSH Hunter in your environment, please contact us and we can send you a full license for evaluation.
Thank you for using Sandfly.
