There appears to be a general misunderstanding among internet users about the difference between malware and viruses. The two terms are often used interchangeably — and to an extent, this is perfectly fine.
But in today’s article, we’ll be clarifying the difference between viruses and malware while helping to identify the most common types of malware. We’ll also offer some pointers on how to check if you have malware or virus on your mobile device, website, or computer.
Are malware and viruses the same thing?
We spend a lot of time discussing website malware specifically, but today we are going to examine how computer viruses and website malware work. We’ll also explore how they vary by type.
To start with, malware is a combination of the words “malicious” and “software”. It refers to a malicious software present on exploited systems.
There is computer malware (or viruses) and website malware. Website malware is malicious code that infiltrates a website’s file system, server, or database. While computer malware is specifically designed to interfere with an end-user’s computer. Both computer malware and website malware seek to disrupt your productivity for malicious personal gain, however, they both do so in different ways.
Computer malware generally attacks a personal system, like a home computer. Website malware generally attacks a public facing system, like an ecommerce website.
Since websites are visited by hundreds or thousands of visitors, website malware is frequently used as a staging ground to infect endpoint devices. For example, one of the most common types of website malware that we see is the NDSW / NDSX JavaScript malware. This infection aims to trick users into installing fake browser updates.
What is the difference between malware and viruses?
A virus is often used as a synonym for “malware”, but it technically refers to one specific type of malware. A virus self-replicates by inserting its code into other programs, and can infect anything from a computer to mobile device, depending on its objective.
Malware, on the other hand, is a general term used to describe any malicious software. This term can be used regardless of how it’s distributed or what actions it performs.
Next, let’s go over some examples of malware.
What are some examples of malware?
While there is some overlap in the way that the different types of malware operate, each type has its specific identifiers.
Here is a breakdown of some of the most common types of malware and viruses:
1. Virus
A virus is a malicious computer application which is installed on an endpoint device, often by tricking the user into thinking that it is a legitimate application. Viruses can have many purposes, which we will get to in the next sections, but often have the end goal of either spying on or stealing money or data from the victim’s computer or online bank account.
Unlike some other types of malware, viruses do not automatically spread to other devices on the same network and are typically isolated to the device on which it was installed.
2. Worm
A worm is a self-replicating malicious application. Its goal is to spread onto as many computer systems as possible through internet-connected systems and applications. The most notorious worm was the Blaster Worm of the early 2000’s.
Unlike a virus though, it is autonomous—not requiring external activation. A worm has the ability to travel on its own through networks and find new locations to infect. However, a virus needs to rely on a host application for movement. It travels by exploiting vulnerabilities within a given system and passes through the open door.
3. Trojan
A trojan is a malicious software application which grants an attacker remote access into an infected system. Their purpose is often to either steal banking information, social media account access, or spy on their victims.
Trojan horses usually pass as benign or innocent looking software. Their objective is to steal information and/or provide further access into the system.
They can also be programmed to take over systems’ resources, such as core files and network bandwidth. Be wary of .EXE or .BAT files with no personalized icon or labels that seem confusing (or irrelevant to the advertised application). A telltale sign of a trojan application is if it triggers a warning from the operating system that it has no official trusted signature – for verification purposes.
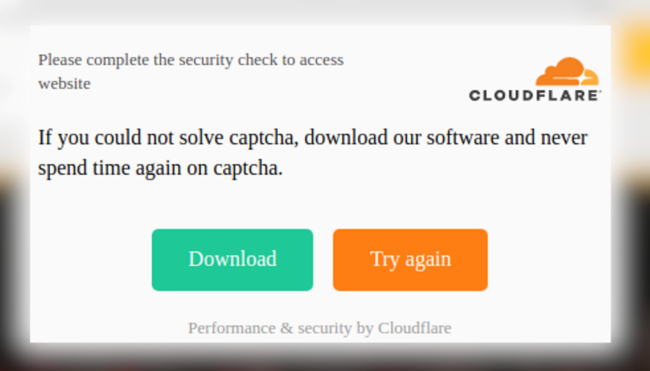
Within a web environment, a good example of a trojan is a user clicking on a seemingly legitimate CAPTCHA and ending up downloading some piece of software.
4. Scareware
Many users have seen scareware. Unfortunately, there is enough awareness about it that it’s not as big of a threat as it used to be.
For those who don’t know, this malware generates an obnoxious (and sometimes flashing) alert that pops up on the screen to inform the user that their system is infected, urging them to purchase the advertised anti-malware product to remove it.
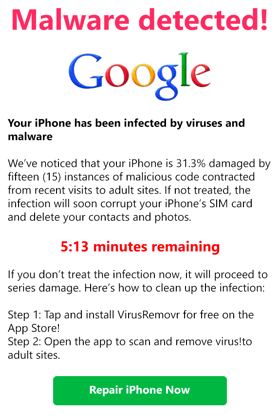
While they aren’t necessarily lying that the system is infected, it is their underhanded strategy that puts the threat there in the first place: to scare an individual into the sale or installation of a piece of software which can itself be malicious. This strategy can also be emulated through a website, where the system is not really infected – the page just displays the same type of alert to make a person think that it is.
A lot of these shady programs (such as “registry cleaners” or some shady “pc optimisation software” programs) are categorized by antivirus companies as “Potentially Unwanted Programs” or PUPs. While not explicitly malicious, they are unnecessary applications which bilk the end user out of money and sometimes rope them into recurring credit card fees.
5. Spyware
Spyware is a type of malware that hides in the background of a system and records personal information – such as visited sites, financial information, or keystrokes. This information is reported back to the malware’s creator for personal use or used to interact with the infected user on a more personal level (more information on this in the next section). The interesting thing about spyware is that it can be used in both an illegal and legal setting.
One way that spyware can be used in a legal way is called workspace spyware. In this case, the company tracks what the employee does when using the computer. This can be for internal security reasons, to ensure that the employees are not spending their time doing what they shouldn’t, or used by metrics-heavy corporate employers to monitor words-per-minute typing speeds and other information
Spyware can definitely hide within an application and operate without consent of the system owner. If a person is not careful to read the terms of service for an application or skips through too many steps of an installation process, they can inadvertently agree to the installation of spyware without realizing it.
6. Adware and Pop-up Ads
Adware is a type of malware that usually works in conjunction with spyware. It can track a person’s browsing or purchasing habits through the spyware and then constantly display advertisements that reflect those habits in a frequent and irritating manner. It is not just limited to pushing sales though, as adware can prompt (sometimes even force) a person to click on an unwanted link or visibly and audibly promote pornographic material – simply as a means for embarrassment, depending on the agenda of the malware creator.
Pop-up ads and adware can infect a website in the same manner. One well-known example is the display of advertisements for a particular product within the header of the site, such as a Viagra knockoff. Both adware and malicious pop-ups are commonly found on infected websites.
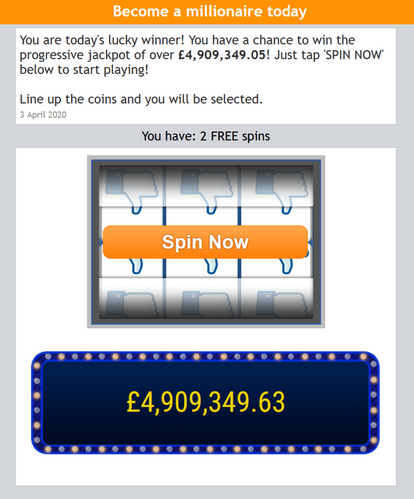
7. Ransomware
Ransomware is one of the most notorious types of malware. It takes advantage of a vulnerability found within a system, or the user downloading a trojan file to encrypt the files, so that those files cannot be understood by the system. The cybercriminal then leaves a message for the owner of the system to demand payment – usually through some kind of untraceable cryptocurrency.
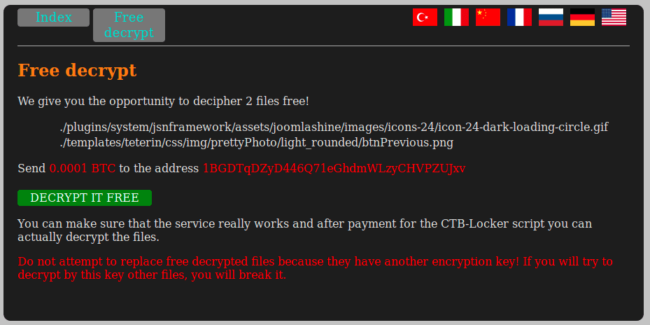
Why? In order to retrieve the decryption keys built in the encryption itself. Once this is in place, not even a malware removal service can undo the damage without that privacy key, as it is the only thing that can undo the encryption.
The victim must unfortunately choose to pay the ransom (with no guarantee that the cybercriminal will even uphold their end of the bargain) or restore a backup that they hopefully created before the infection. A loss of any recent updates to their site or system is unavoidable.
Ransomware can also act as a worm where it encrypts a system and demands payment but also immediately tries to spread itself through nearby connected systems.
And occasionally, ransomware can affect websites themselves — but it is not very common.
In the wake of some high-profile ransomware attacks on United States institutions, ransomware was recently declared by the American government to be a threat comparable in scope to terrorism.
8. Phishing
Phishing malware comes in all shapes and forms. Attacks occur when a bad actor pretends to be a reputable brand or known person in order to obtain login credentials, personal information, bank account information, and other sensitive information.
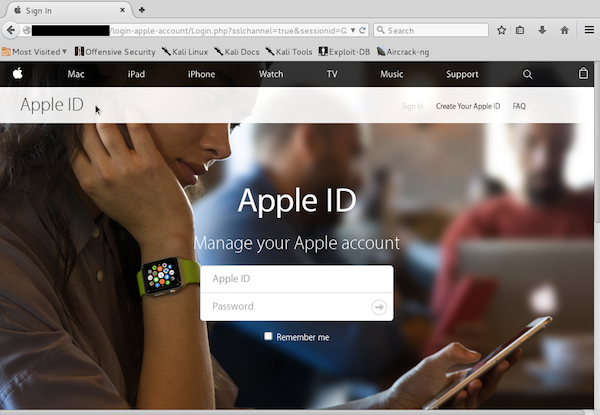
This malware is frequently found on compromised website environments It is frequently paired with mailer scripts which send out bogus emails with the intent to trick users into entering their login credentials on the fake sign-in pages.
Phishing attacks are widespread. With the holidays so close, this malware becomes even more common.
9. SEO Spam
SEO spam infections often result in unwanted keywords and spam, malicious redirects, and polluted search results, as seen below.
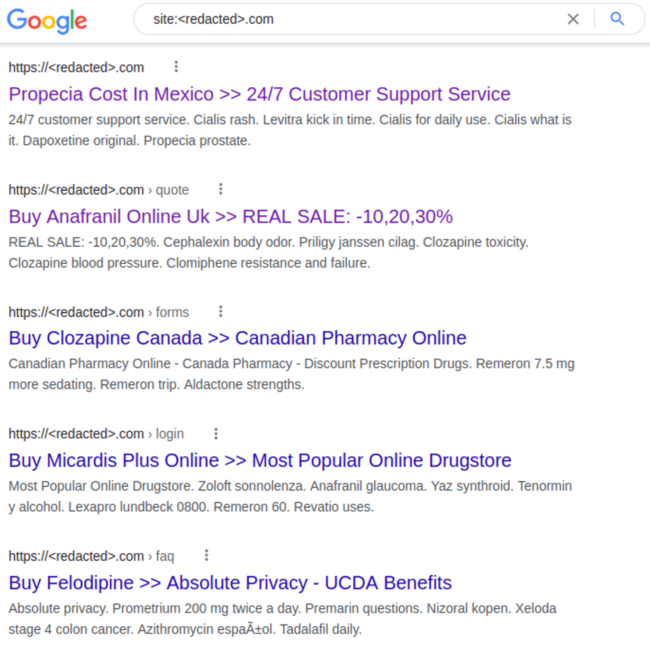
Attacks are known to inject malicious links, create multitudes of spam comments, or even produce thousands of posts and pages on the hacked website.
This malware can be especially challenging for webmasters, since they can lead to blocklisting by Google and other search engines. Infections can lead to a loss of website rankings, traffic, reputation, and revenue.
In Q3, a total of 119,865 websites were detected with SEO spam infections during remote scans.
If you’re interested in learning more, check out our guide which details all the different types of website malware in detail.
How to check if you have malware or virus
Let’s go over a few general steps on how to check if you have a malware or virus infection on your mobile device, computer, or website.
- Scan your computer.
- Scan your mobile phone.
- Remotely scan your website for infection.
- Scan your web server for malware.
Step 1: Scan your computer.
If your computer is infected, you’ll want to perform a thorough scan of your computer file system. This helps you check for any malware or viruses that may be present.
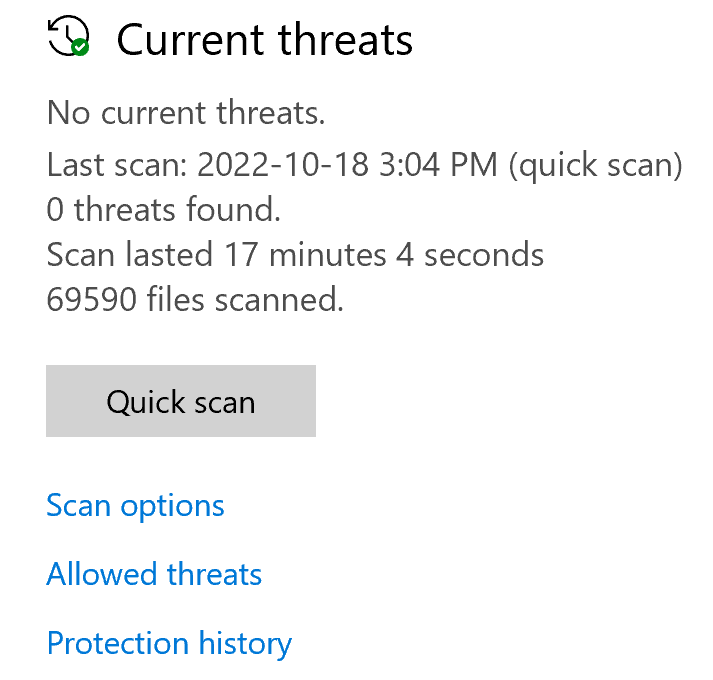
You can scan with an antivirus application designed for your specific operating system. Go with a trusted name in the security space, such as Malwarebytes, Bitdefender, or Norton. These software applications will help you to identify whether your computer is infected with a malware or virus.
If you’re a Windows 10 user, Microsoft offers Windows Defender to help detect and remove or quarantine malware on your computer.
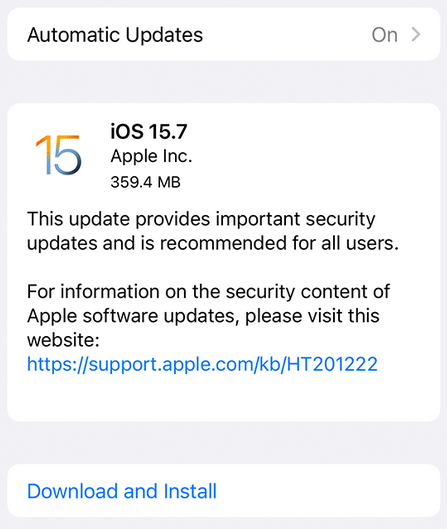
Step 2: Scan your mobile phone – or update it.
Android is an open ecosystem, making the OS more vulnerable to malware than iOS. To mitigate risk, you’ll want to perform regular scans for malware or viruses on your device. Fortunately, many of those trusted security vendors also maintain Android applications for security software.
Security restrictions for iOS mean that Antivirus software on iOS isn’t available, however. Updates are released regularly for both iOS and Android that patch important security issues, so make sure you stay on top of regular updates to mitigate risk.
Always make sure that the apps that you are installing are from the official stores. You’ll also want to review the permissions or data that installing the app grants to the software author.
Step 3: Remotely scan your website for infection.
A remote scan of your website is one of the fastest ways you can detect malware on your website.
Remote scans help pinpoint infections that may be found in your website’s source code and outward facing website files. For example, a remote scan can help locate malicious JavaScript injections, SEO spam, defacements, and unwanted ads.
Remote scanners have limited access to your website, however. They are not able to scan at the database or server level. For that, you’ll need to scan a bit deeper.
Step 4: Scan your web server for malware.
A server side scanner is one of the most important tools in a webmasters toolkit. Scan your web server regularly for any indicators of compromise.
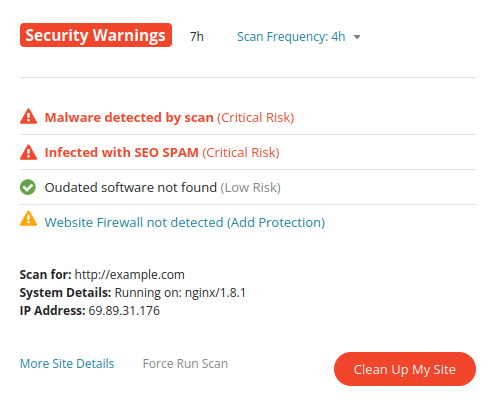
Not all website malware displays outwardly. Scanning server-side can help locate malicious PHP scripts, website backdoors, phishing pages, and credit card skimming malware that isn’t easily detected on the front of a website.
Sucuri offers web server scanning and detection that makes it easy for you to find and respond to malware found on your website.
What’s the difference between antivirus and anti-malware?
A good anti-malware program can protect a computer against malicious file infections. If you are looking for computer antivirus software, then here are some top-rated companies to consider.
Malware attacks target more than computers. Cybercriminals have adapted these methods so that they are compatible with web applications as well.
Nowadays, cybercriminals target websites for their own personal profit at the expense of the site owner. But what options are available to protect a person’s priceless web presence? Well, this is where Sucuri comes in! We remove website malware.
How to protect against malware and viruses
Proper personal security hygiene is always strongly advised, such as hard-to-guess passwords and limited server access where it is not necessary.
And if you’re looking for extra website protection, Sucuri’s Web Application Firewall (WAF) protects a website from all of these attacks. Our virtual patching technology protects sites from the latest known software vulnerabilities in the event that you can’t patch your website in time. For more information on how Sucuri’s WAF works to protect a site, you can visit our website firewall page.
With good security, you can help keep attackers at bay – regardless of the attack method they try to use. Sucuri is here to help whether a person decides to consider one of our available security plans or not. We aim to educate anyone interested at the very least.
Knowledge is the first step in defense against these attacks. And as any child of the 80s would recall, “Knowing is half the battle!”
