
2022-10-6 21:37:7 Author: infosecwriteups.com(查看原文) 阅读量:15 收藏
Welcome to this new article. This article is a story about misconfigurations found on a domain. Since it is a private program let’s call it redacted.com So do you wanna know how??
The scope of the application was huge, but starting off with the normal subdomain scan and all of those fancy recon I decided to start testing the main application. The web application was a simple E-commerce website with a lot of deals to grab on! ;)
I usually try to check all sorts of business logic vulnerabilities on such websites, but this time my eyes captured the authentication mechanism.
So the first thing was to create an account! But what came to my notice was the OAuth mechanism. Perfect it was time to check for various OAuth vulnerabilities!!

So I used the beautiful methodology from Pentest Book and my 2nd dummy account and started checking for OAuth vulnerabilities, but was not able to find any!
But Hey!! The basic vulnerability check was forgotten. I instantly tried to create an OAuth account using my 1st dummy account and Boom, I was able to create 2 accounts using the same email ID.



To summarize the entire procedure the following steps were performed:
- Visit the website and click on Sign Up.
- Create an account using an unregistered victim email (say [email protected])
- Create another account using the OAuth mechanism and using the same OAuth account.
Impact:
The account created using email and password should get invalidated but it does not which means the attacker can still log in using the credentials he used while creating the account using email leading to pre-account takeover.
Perfect! I got one, let's hunt for more! This time my eyes caught the forget password functionality.
The password reset mechanism was as follows:
- The user enters his email.
- A 6-digit OTP is generated and sent to the email of the user
- The user sets a new password.
Great, let's try for Authentication Bypass and check if we are able to change the victim’s password. So I entered my email and requested an OTP, entered the wrong OTP, and captured the response and tried for response manipulation but no luck.
But my eye caught that the application was using ajax to perform password reset .
AJAX allows web pages to be updated asynchronously by exchanging small amounts of data with the server behind the scenes.
So here’s what I did :
- Go to Sign in page and click on forgot password
- Enter attackers email (i.e my email say [email protected] )
- Now enter the correct OTP received on [email protected] and Capture the Response and save it .
- You will be redirected to set new password page but DONT SET THE PASSWORD instead Again go to Sign in page and click on forgot password
- Enter victims email i.e. [email protected] ( in our case it was [email protected] )

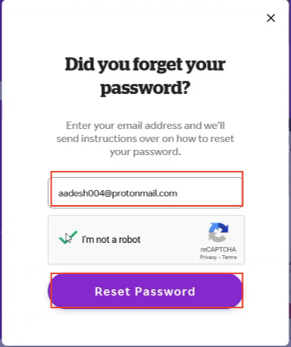
6. Enter random OTP i.e. 000000 and Intercept the request using burp and Do intercept > Response to this request

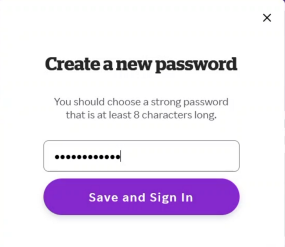
7. IN THE RESPONSE MANIPULATE THE RESPONSE TO :{“successTextKey”:”success”,”errors”:null}


8. Forward the request and You will be redirected to Set new password . This time Set the password and boom ACCOUNT TAKEOVER .

We hope that you enjoyed this article! Do let us know your stories about misconfigurations!
Happy Hunting!
如有侵权请联系:admin#unsafe.sh