
Hi, My name is Hashar Mujahid and in this blog, we will talk about some techniques to bypass the csrf protection.

You can read my previous blog here if you want to learn about what csrf is.
If the application only relies on client-side values like cookies then the application will be vulnerable to csrf attack. An attacker can easily trick the user to click the malicious payload and initiate actions that the user didn't intend to happen.
To prevent the Csrf attacks the csrf tokens are used. Now you might have a question
WHAT ARE CSRF TOKENS?
Well to simply put an answer the csrf tokens are randomly generated values that the web application assigns to each user session this value will be renewed after every post action that the user performed.
HOW DOES CSRF TOKEN WORK?
When the user performs any action on the application the request contains the user session (cookies) right? In this case, the request also contains a randomly generated value assigned by the application in the csrf parameter which will be then validated on the server side. If the csrf value is not valid then the server will stop the request from processing.
HOW TO BYPASS CSRF PROTECTION?
As we all know if any protocol is implemented correctly then we have less chance of bypassing it. It is the same case in CSRF bypass. If there are some implementation errors then we could be able to bypass this protection.
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
1: Check if the CSRF value is being validated on the backend.
To test if the CSRF is being validated on the backend, try to temper with the CSRF value in the CSRF parameter and send the request if the value is being checked and validated the request should not be processed if not you will have a valid CSRF bypass.
Now when we change or temper with the value we can see the server responds with an invalid csrf token.

If the vulnerability is present the application should have redirected you to your profile without any errors.
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
2: CSRF where token validation depends on the token being present.
Some applications skip the csrf validation if we remove the csrf parameter from the request. In simple words, if the application flags the tempered or invalid tokens we can try removing the csrf parameter altogether to see if our request is still processed.

Let's remove the csrf parameter.

We can see our request is successful.
We can use this vulnerability to perform unintended actions on the user’s behalf like changing the user's email by generating a csrf payload. If you want to know how to generate a csrf payload without a burp professional read my previous blog.
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
3: Validation of CSRF token depends on the request method.
Some times application only validates the csrf on post requests but it can be a grave mistake because attacker can also perform similar actions on the user’s behalf with the GET request method.
We can change the request type to get from burp and test for this vulnerability.

We can see when we tempered the token in the request and send it the server responded with the error.
Now Let’s change the request method and send this request.

We can see now our tempered token is not validated and our request succeeded.
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
4: CSRF token is not tied to the user session
It’s also important for an application to validate that if the csrf token belongs to the same session that sends the request.
Sometimes attackers can register an account and in payload send their valid csrf token to make the attack successful.
To overcome this issue server should validate if the token belongs to the same session or not.
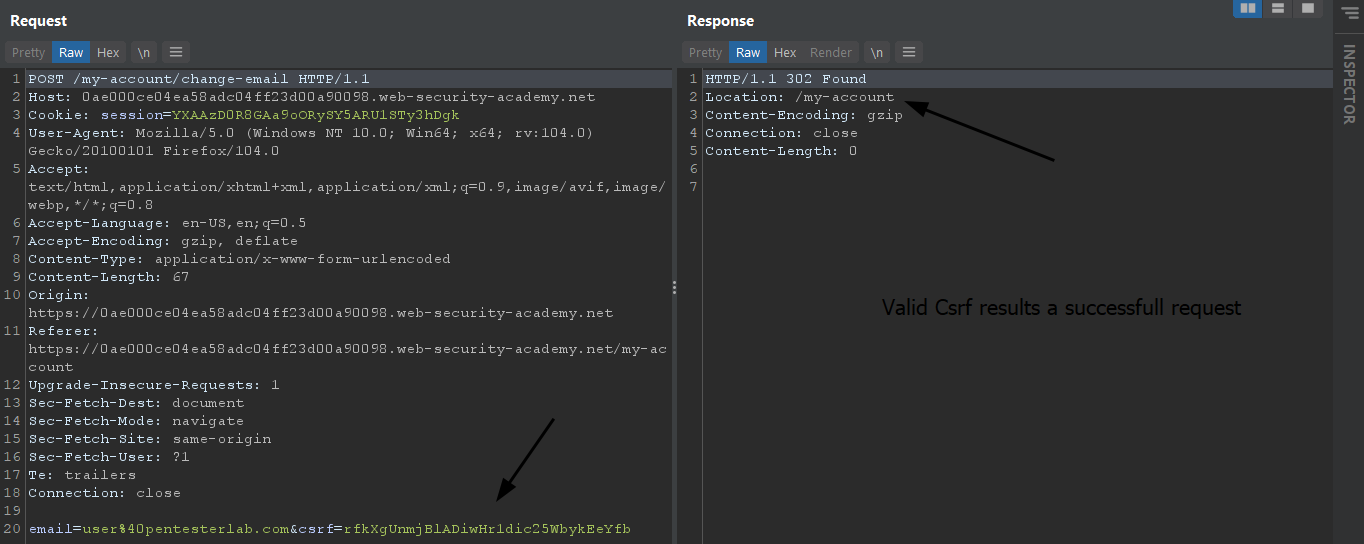
To test for this vulnerability create 2 account’s on the web application and when performing the action change the token on one account with another and send the request if the request is completed that means the csrf value is not tied to the user’s session.
Solve this lab to practice what we have learned.
That’s enough for today, I will post some more advanced techniques to bypass the CSRF protection in the future.
Till then HAPPY HACKING! ❤
From Infosec Writeups: A lot is coming up in the Infosec every day that it’s hard to keep up with. Join our weekly newsletter to get all the latest Infosec trends in the form of 5 articles, 4 Threads, 3 videos, 2 Github Repos and tools, and 1 job alert for FREE!
如有侵权请联系:admin#unsafe.sh