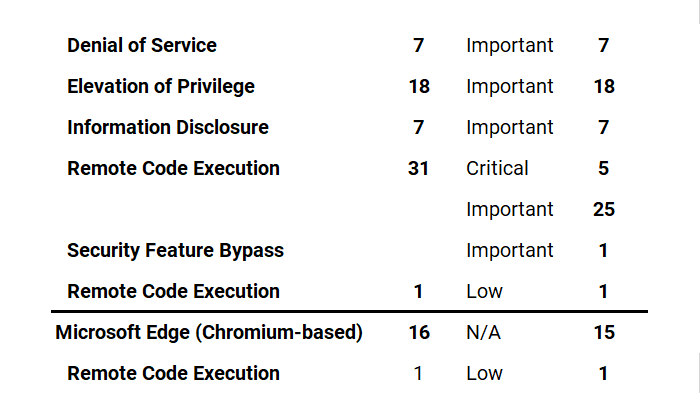
Microsoft has fixed 63 vulnerabilities (aka flaws) in the September 2022 update, including five (5) vulnerabilities classified as Critical as they allow Remote Code Execution (RCE). This month’s Patch Tuesday fixes two (2) zero-day vulnerabilities, with one (1) actively exploited* in attacks (CVE-2022-37969*, CVE-2022-23960). Earlier this month, on September 1 and 2, 2022, Microsoft also released a total of 16 Microsoft Edge (Chromium-Based) updates, one (1) addressing a Remote Code Execution (RCE) (CVE-2022-38012) ranked Low.
Microsoft has fixed several flaws in its software, including Denial of Service, Elevation of Privilege, Information Disclosure, Microsoft Edge (Chromium-based), Remote Code Execution, and Security Feature Bypass.
The September 2022 Microsoft vulnerabilities are classified as follows:

CVE-2022-34718 | Windows TCP/IP Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8/10.
An unauthenticated attacker could send a specially crafted IPv6 packet to a Windows node where IPSec is enabled, which could enable a remote code execution exploitation on that machine.
Exploitability Assessment: Exploitation More Likely
CVE-2022-34721, CVE-2022-34722 | Windows Internet Key Exchange (IKE) Protocol Extensions Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8/10.
An unauthenticated attacker could send a specially crafted IP packet to a target machine that is running Windows and has IPSec enabled, which could enable a remote code execution exploitation. NOTE: This vulnerability only impacts IKEv1. IKEv2 is not impacted. However, all Windows Servers are affected because they accept both V1 and V2 packets.
Exploitability Assessment: Exploitation Less Likely
A vulnerability is classified as a zero-day if it is publicly disclosed or actively exploited with no official fix available.
CVE-2022-37969 | Windows Common Log File System Driver Elevation of Privilege (EoP) Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8/10.
An attacker must already have access and the ability to run code on the target system. This technique does not allow for remote code execution in cases where the attacker does not already have that ability on the target system.
An attacker who successfully exploited this vulnerability could gain SYSTEM privileges.
Exploitability Assessment: Exploitation More Likely
CVE-2022-23960 | Windows Common Log File System Driver Elevation of Privilege (EoP) Vulnerability
This vulnerability has a CVSSv3.1 score of 5.6/10.
CVE-2022-23960 is regarding a vulnerability known as Spectre-BHB. MITRE created this CVE on behalf of Arm Limited.
Please see Spectre-BHB on arm Developer for more information.
Exploitability Assessment: Exploitation Less Likely
This month’s advisory covers multiple Microsoft product families, including Azure, Browser, Developer Tools, Extended Security Updates (ESU), Microsoft Dynamics, Microsoft Office, System Center, and Windows.
A total of 92 unique Microsoft products/versions are affected, including but not limited to .NET, Azure Arc, Microsoft Dynamics, Microsoft Edge (Chromium-based), Microsoft Office, Microsoft Office SharePoint, SPNEGO Extended Negotiation, Visual Studio Code, Windows Common Log File System Driver, Windows Credential Roaming Service, Windows Defender, Windows Distributed File System (DFS), Windows DPAPI (Data Protection Application Programming Interface), Windows Enterprise App Management, Windows Event Tracing, Windows Group Policy, Windows IKE Extension, Windows Kerberos, Windows Kernel, Windows LDAP – Lightweight Directory Access Protocol, Windows ODBC Driver, Windows OLE, Windows Print Spooler Components, Windows Remote Access Connection Manager, Windows TCP/IP, and Windows Transport Security Layer (TLS).
Downloads include Cumulative Update, Monthly Rollup, Security Hotpatch Update, Security Only, and Security Updates.
CVE-2022-38009 | Microsoft SharePoint Server Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
In a network-based attack, an authenticated attacker with Manage List permissions could execute code remotely on the SharePoint Server.
The attacker must be authenticated to the target site, with the permission to use Manage Lists within SharePoint.
Exploitability Assessment: Exploitation Less Likely
CVE-2022-26929 | .NET Framework Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8/10.
The word Remote in the title refers to the location of the attacker. This type of exploit is sometimes referred to as Arbitrary Code Execution (ACE). The attack itself is carried out locally.
For example, when the score indicates that the Attack Vector is Local and User Interaction is Required, this could describe an exploit in which an attacker, through social engineering, convinces a victim to download and open a specially crafted file from a website which leads to a local attack on their computer.
Exploitability Assessment: Exploitation Less Likely
CVE-2022-38007 | Azure Guest Configuration and Azure Arc-enabled servers Elevation of Privilege (EoP) Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8/10.
An attacker who successfully exploited the vulnerability could replace Microsoft-shipped code with their own code, which would then be run as root in the context of a Guest Configuration daemon. On an Azure VM with the Guest Configuration Linux Extension installed, this would run in the context of the GC Policy Agent daemon. On an Azure Arc-enabled server, it could run in the context of the GC Arc Service or Extension Service daemons.
Exploitability Assessment: Exploitation Less Likely
Microsoft Edge | Last But Not Least
Earlier in September 2022, Microsoft released Microsoft Edge (Chromium-based) vulnerabilities including CVE-2022-38012. The vulnerability assigned to the CVE is in the Chromium Open Source Software (OSS) which is consumed by Microsoft Edge. It is being documented in the Security Update Guide to announce that the latest version of Microsoft Edge (Chromium-based) is no longer vulnerable. For more information, please see Security Update Guide Supports CVEs Assigned by Industry Partners.
CVE-2022-38012 | Microsoft Edge (Chromium-based) Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 7.7/10.
The word Remote in the title refers to the location of the attacker. This type of exploit is sometimes referred to as Arbitrary Code Execution (ACE). The attack itself is carried out locally.
For example, when the score indicates that the Attack Vector is Local and User Interaction is Required, this could describe an exploit in which an attacker, through social engineering, convinces a victim to download and open a specially crafted file from a website which leads to a local attack on their computer.
This vulnerability could lead to a browser sandbox escape.
Successful exploitation of this vulnerability requires an attacker to take additional actions prior to exploitation to prepare the target environment.
NOTE: Per Microsoft’s severity guidelines, the amount of user interaction or preconditions required to allow this sort of exploitation downgraded the severity. The CVSS scoring system doesn’t allow for this type of nuance which explains why this CVE is rated as Low, but the CVSSv3.1 score is 7.7
Qualys Patch Tuesday QIDs are published as Security Alerts typically late in the evening on the day of Patch Tuesday, followed later by the publication of the monthly queries for the Unified Dashboard: 2022 Patch Tuesday (QID Based) Dashboard by Noon on Wednesday.
Qualys Threat Protection High-Rated Advisories for September 1-13, 2022
Patch Tuesday is a process. Please check back periodically as this blog is updated throughout Patch Tuesday week. New information, insights, and resources are added and updated as they become available.

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are part of this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.