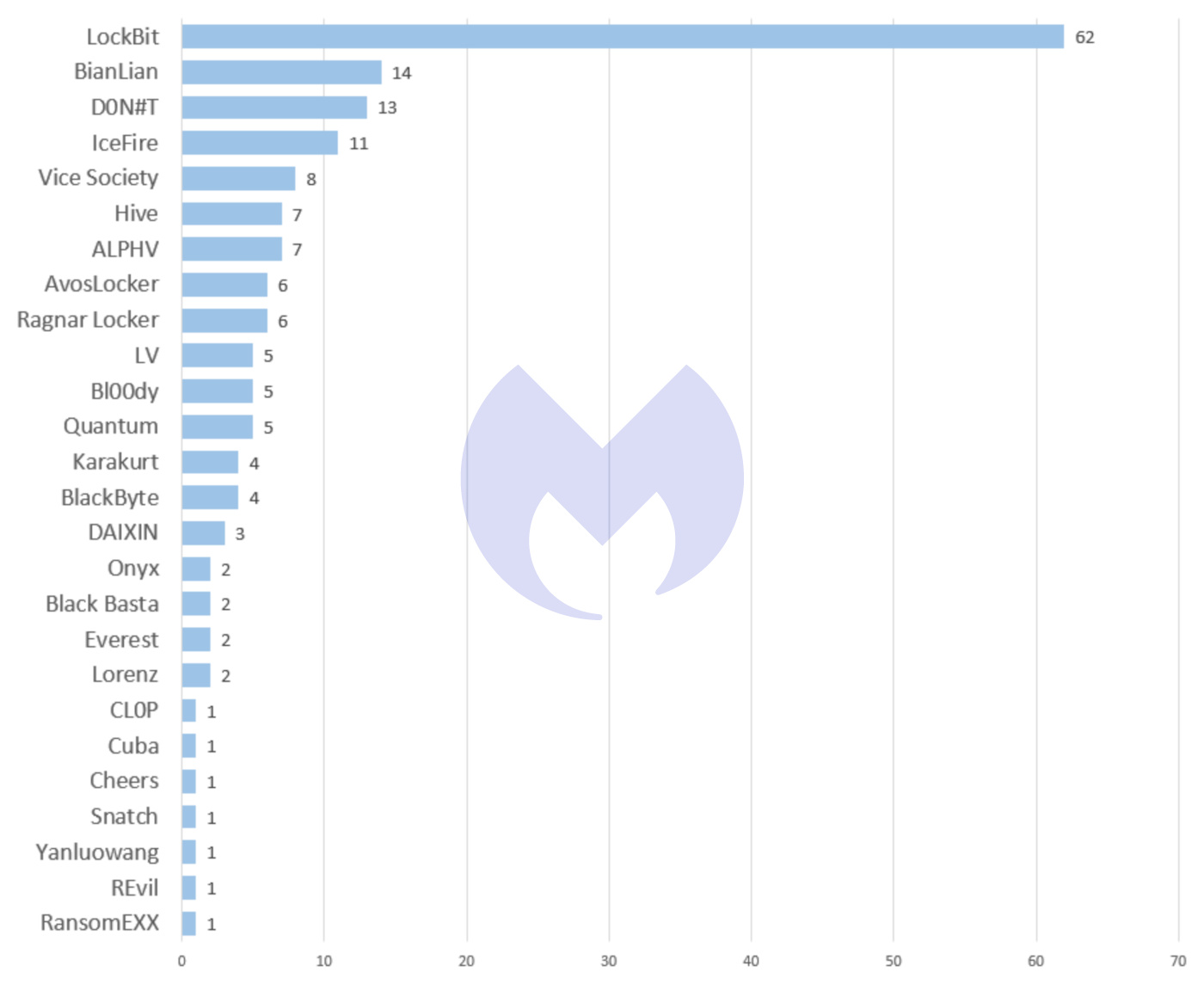
Malwarebytes Threat Intelligence builds a monthly picture of ransomware activity by monitoring the information published by ransomware gangs on their Dark Web leak sites. This information represents victims who were successfully attacked but opted not to pay a ransom.
As expected, LockBit remained the dominant ransomware variant in August, as it has all year. At the other end of the scale REvil's revival in slow motion continued with a single victim listed, RansomEXX posted its first victim for four months, and Snatch posted a single victim after fourty days of inactivity. Intriguingly, the victim listed on the Snatch site was also listed by REvil in April. It's not unusual for victims to be attacked multiple times, so this is not necessarily a sign of cooperation.

As we wrote in June, part of LockBit's success comes from avoiding the kind of fatal missteps made by rivals like Conti, REvil, and DarkSide, all of whom attracted a great deal of public attention from US law enforcement. We cannot help wondering how long that will last though. LockBit has been the most active ransomware threat for all of 2022 and it is impossible to imagine there isn't a team of FBI agents somewhere plotting its demise.
Over the last six months, between March 2022 and August 2022, LockBit has racked up 430 known attacks in 61 different countries, including 128 in the USA. In that period it was responsible for one in three known ransomware attacks—more than the next four most active gangs combined, and 300 more than its nearest rival. Between March and August it averaged about 70 known attacks per month, while the median average for the gangs we monitor has never exeeded seven.

The USA continues to bear the brunt of ransomware attacks, although its preeminence likely reflects the size of its service economy and the large number of potential vicitms rather than a deliberate targeting. Few countries escape attention and the 175 known attacks in August spread across 43 countries as diverse as Luxembourg, Qatar, and Gabon.


The future of ransomware
Two events in August hinted at how ransomware gangs' tactics may evolve beyond "double extortion", the biggest innovation in ransomware tactics in recent years.
Originally, ransomware encrypted files and its operators demanded a ransom in return for a decryption tool. It was all but impossible to decrypt the files without the decryption tool, but victims could avoid paying a ransom by restoring encrypted files from backups.
In late 2019 the group behind Maze ransomware began stealing files from its victims before encrypting them, and then threatened to leak the stolen files on a dark web website. This gave victims an incentive to pay the ransom even if they could restore their system from backups. The tactic was quickly copied and it is now standard for large ransomware groups.
Triple extortion
In August, LockBit stole data from security company Entrust in a double extortion attack. According to LockBit, which spoke to VX-Underground, the victim's unusual response was to prevent LockBit from publishing the stolen data by launching a distributed denial of service (DDoS) attack against the group's leak site.
The attack delayed the leak but does not seem to have prevented it. However it does seem to have inspired LockBit to try the same thing. Having seen how effective DDoS attacks can be, the group took to a hacking forum to explain that it is now planning to use DDoS as a third stick to beat victims with, alongside encryption and extortion.

The utterings of ransomware gangs should always be taken with a pinch of salt, but the idea is worth taking seriously because it isn't new. In fact DDoS extortion is an older tactic than encrypting files and demanding a ransom. It has simply fallen out of favor in recent years.
The end of ransomware?
Data leaking has been such a successful tactic that some groups, like Karakurt, don't bother to encrypt files at all and rely entirely on the threat of leaked data. We believe that we will see more gangs taking this approach in future.
Since ransomware gangs started adopting "big game" tactics about five years ago, the skills required for a successful attack have changed. In a "big game" attack the encrypting malware is a commodity—the expertise that determines an attacker's likely success are their ability to find a target, understand its value, and then break into its network and operate undetected.
This has led to significant specialization, with some criminal groups providing the software, some working as initital access brokers, and others actually performing the attacks. The skills that access brokers and attackers have developed have lucrative uses beyond deploying ransomware, such as surveillance, sabotage, espionage, and data exfiltration.
If encrypting ransomware ceases to generate significant revenue, its operators will simply pivot to other forms of attack. The pressure to do that started with improved backups triggering the switch to "double extortion", and has increased as a result of Russia's war in Ukraine. Since the start of the war, ransomware gangs have found it harder to get paid because of the threat of sanctions, and one of the most high profile gangs has disappeared completely as a direct result.
Ransomware operator Mikhail Matveev was asked in a recent interview with The Record if he thought ransomware will remain the best monetization model for cybercriminals over the next three years. His response: "ransomware will soon die—not in three years, but sooner. Literally, everything has changed over the last six months. Since the beginning of the special operation in Ukraine, almost everyone has refused to pay."
Some members of the security industry have gone further, predicting ransomware's imminent demise.
We believe that while the long term trend may see gangs moving away from encryption, we don't expect a sudden change. The reality is that some groups find it difficult to obtain their demands without the use of encryption, and encryption is still the tactic of choice for 2022's most successful ransomware group, LockBit.
New groups
It seems that some cybercriminals haven't received the memo about the imminent end of ransomware-as-a-service, and a handful of new groups appeared in August, just as they did in July. The new groups are D0nut, IceFire, DAIXIN, and Bl00dy. Unusually, Bl00dy doesn't have a leak site and instead use the Telegram messaging app.