In a statement filed at the London Stock Exchange, InterContinental Hotels Group PLC reports that parts of the company's technology systems have been subject to unauthorized activity. The activity significantly disrupted IHG's booking channels and other applications.
InterContinental Hotels Group
The InterContinental Hotels Group, also known as IHG Hotels & Resorts, operates 17 hotel brands around the world, including established brands like InterContinental, Regent, Six Senses, Crowne Plaza, and Holiday Inn. IHG has over 6,000 open hotels in more than 100 countries, and more than 1,800 in the development pipeline. Approximately 325,000 people work across IHG's hotels and corporate offices globally.
Ransomware?
Obviously, ransomware is not the same as “technology systems have been subject to unauthorized activity,” but in cases like these it is an automatic reflex to assume that it’s a ransomware attack. Especially when, as reported by BleepingComputer, last month the Lockbit ransomware group claimed an attack on Holiday Inn Istanbul Kadıköy, one of the hotels operated by IHG.
IHG didn't disclose whether the attack was the result of ransomware or some other malware. For now, they are in the process of notifying authorities about the intrusion, and working with their technology suppliers. In addition, experts from outside of IHG are being brought in to help with the investigation.
Booking system
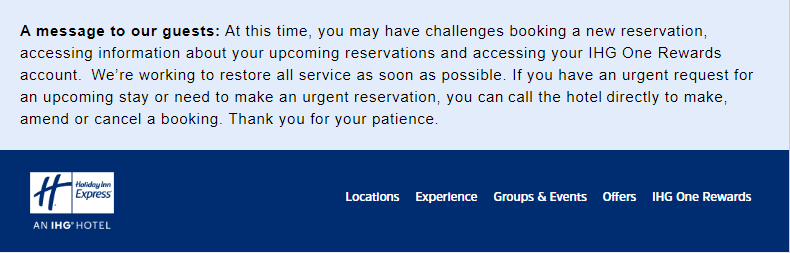
The unavailability of the online booking system must be a major pain for IHG. The website is unresponsive and a message in the booking system says the company is working to resolve the issues as quickly as possible and suggests customers with questions to call the hotel directly.

“At this time, you may have challenges booking a new reservation, accessing information about your upcoming reservations and accessing your IHG One Rewards account. We’re working to restore all service as soon as possible. If you have an urgent request for an upcoming stay or need to make an urgent reservation, you can call the hotel directly to make, amend or cancel a booking. Thank you for your patience.”
The company emphasizes that IHG's hotels are still able to operate and to take reservations directly.
Mitigation
A complete set of defenses against ransomware should cover 3 stages:
- Prevention and detection
The least painful time to thwart a ransomware attack is before it can do any harm. Use anti-malware software, and keep all operating systems, software, and firmware up to date. (Timely patching is one of the most efficient and cost-effective steps an organization can take to minimize its exposure to cybersecurity threats.)
Block and/or flag emails that could contain malicious links and attachemnets. And educate and train your staff about how to handle such emails.
- Monitoring and containment
Authentication policies can help to limit the lateral access that ransomware operators often exercise before they actually deploy the ransomware. Segment networks to prevent the spread of ransomware and disrupt lateral movement. Identify, detect, and investigate abnormal activity with a network monitoring tool. Endpoint detection and response (EDR) tools are particularly useful for detecting lateral connections as they have insight into common and uncommon network connections for each host. Disable unused ports.
Disable command-line and scripting activities and permissions. Privilege escalation and lateral movement often depend on software utilities running from the command line. If threat actors are not able to run these tools, they will have difficulty escalating privileges and/or moving laterally.
- Recovery and removal
Put your backups outside of the reach of attackers, and make sure they work by testing that you can restore working systems from them. Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, and secure location (i.e., hard drive, storage device, the cloud). Some security solutions offer built-in ransomware rollback options.
A complete removal is key if you want to prevent the threat actor from coming back. It’s not just about closing the door they got in through, they could also have planted a backdoor they can leverage to come back. Many of the tools they deploy are legitimate, but will still have to be removed or disabled for unauthorized access.
Customer data
At this point it is unclear whether any customer data were compromised, but we will keep you updated.