If you just want to read the rules, you can find them he 2022-8-29 23:9:49 Author: www.thezdi.com(查看原文) 阅读量:67 收藏
If you just want to read the rules, you can find them here.
Our Fall Pwn2Own event has become a bit of a nomad, having gone from Amsterdam to Tokyo to Austin. This year, we’re heading to Toronto to celebrate the 10th anniversary of the contest formerly known as Mobile Pwn2Own. Since 2012, we’ve expanded the contest to include devices beyond phones. This year is no different, with devices typically found on homes and home offices.
Pwn2Own Toronto will be held at our Toronto office on December 6-8, 2022. While this year’s contest isn’t being held in conjunction with a conference, we still want contestants to attend in person. In fact, we want them there so much that we’re going to put our money where our mouth is by reimbursing $3,000 for travel expenses for teams that participate in Toronto. We’re also going to try to have some sort of audience there as well, but we’re not offering cash just to watch. If you are a former Pwn2Own winner and would like more information about this program, you know how to get in touch with us.
If you can’t be in Toronto due to travel restrictions or travel safety concerns, you can opt to compete remotely. You will still need to register before the contest deadline (December 2, 2022) and submit a detailed whitepaper completely explaining your exploit chain and instructions on how to run the entry by December 5, 2022. A member of the ZDI staff in Toronto will run your exploit for you. All attempts will be filmed and available for viewing by the contestant and the vendor. As in the past, we will work with remote contestants to monitor the attempt in real-time via a phone call or video chat. Please note that since you are not in person, changes to exploits/scripts/etc. will not be possible, which could lower your chance of winning should something unexpected occur.
As for the contest itself, we’re pleased to welcome back Synology as a co-sponsor of the competition. We’re also excited to announce a special challenge for this year’s contest we’re calling the “SOHO Smashup” (as in Small Office/Home Office). This is a real-world scenario of how a threat actor would exploit a home office, so we wanted to include it here, too. It works like this; a contest picks a router and begins by exploiting the WAN interface. They must then pivot into the LAN to their choice of second target – one of the other devices in the contest. For example, you could pick the TP-Link router and the HP printer. If you compromise both, you’ll win $100,000 and 10 Master of Pwn points.
Beyond that, the contest remains largely the same as in previous years. We will have a random drawing to determine the schedule of attempts on the first day of the contest, and we will proceed from there. Our intention with allowing remote participation is to provide as many people as possible with the benefits of participating in Pwn2Own while still treating all contestants as equally as possible. As always, if you have questions, please contact us at [email protected]. We will be happy to address your issues or concerns directly.
Now on to the specific target categories. We’ll have seven different categories for this year’s event:
Let’s take a look at each category in more detail, starting with mobile phones.
Back when this version of Pwn2Own started in 2012, it was called Mobile Pwn2Own, and phones are still at the heart of our fall event. As always, these phones will be running the latest version of their respective operating systems with all available updates installed. We’ve increased the rewards on these targets to add further incentives to these handsets.
In this category, contestants must compromise the device by browsing to content in the default browser for the target under test or by communicating with the following short-distance protocols: near field communication (NFC), Wi-Fi, or Bluetooth. The awards for this category are:
The Google and Apple devices in this category also include an add-on bonus. If your exploit payload executes with kernel-level privileges, you earn an additional $50,000 and 5 more Master of Pwn points. That means a full exploit chain for the iPhone or Pixel that includes kernel-level access will earn $250,000.
Routers - Your SOHO Entry Point
You connect to the world through your local wireless router, and the world has the opportunity to reach back to you. In the past, successful demonstrations included some flair by having the LED lights flash in different patterns. In addition to the home office routers, we have some devices typically used by SMBs as well. An attempt in this category must be launched against the target’s exposed network services from the contestant’s device within the contest network.
Home Automation Hubs
As people add smart devices to their homes, they tend to add a hub to centralize control of all of those devices. From lights, to locks, to thermostats, cameras, and more, all can be accessed through a home automation hub. Of course, that means a threat actor could potentially access them as well. Three of the most popular smart hubs are included in this year’s event.
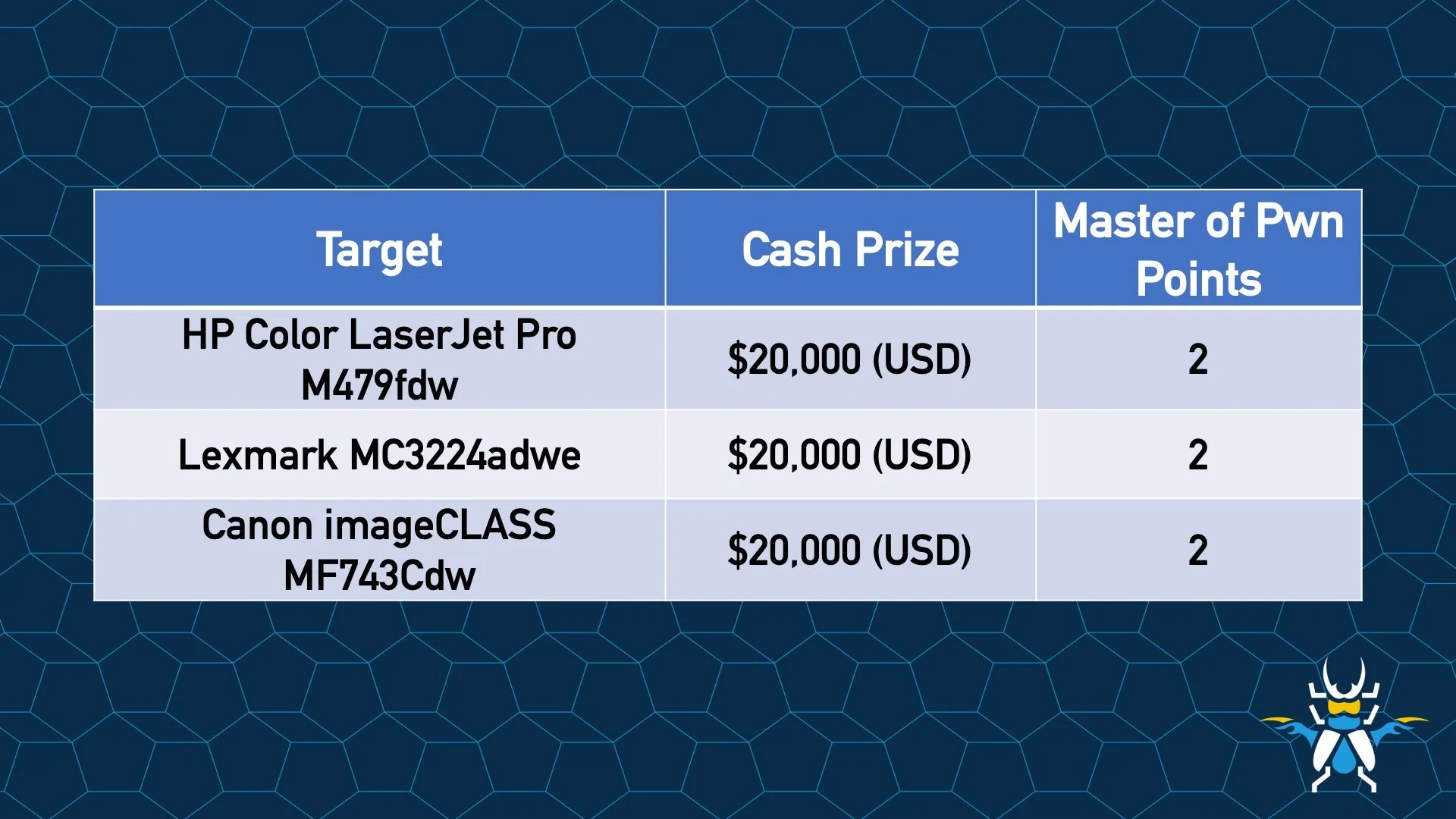
The Return of Printers
Exploits involving printing capabilities have made quite a bit of news over the last couple of years, with ransomware gangs incorporating PrintNightmare bugs in their exploit kits. In last year’s contest, one printer was turned into a jukebox playing classic rock. It will be interesting to see what exploits the contestants come up with this year.
Smart Speakers
Smart speakers continue to play a large part in our daily interactions with music, news, and more. They also offer an attack surface for threat actors to target. For this event, Pwn2Own Toronto has three targets available in this category.
Network Attached Storage (NAS) Devices
NAS devices make their return to Pwn2Own, and both Synology and Western Digital have returned as targets with their latest offerings. Last year’s event exposed some industry-wide Netatalk bugs. Time will tell if this year’s event has a similar impact. An attempt in this category must be launched against the target’s exposed network services from the contestant’s laptop within the contest network.
The SOHO Smashup
With more and more people working from home, many enterprises have found their network perimeter move to the home office as well. Threat actors who exploit home routers and consumer devices can use these as a launch point for lateral movements into enterprise resources. We wanted to demonstrate this during the contest, so we’re introducing the SOHO Smashup category to show how this could happen. Contestants will need to first compromise the WAN port on a selected router. Once they accomplish that, they will need to pivot to one of the other devices and compromise it as well. The contestant is free to select any combination of router and home automation hub, smart speaker, printer, or network attached storage device during the registration process. If they get both devices within 30 minutes, they earn $100,000 and 10 Master of Pwn points. We’re hopeful several contestants will use this category to choose their own (mis)adventure.
Master of Pwn
No Pwn2Own contest would be complete without crowning a Master of Pwn, which signifies the overall winner of the competition. Earning the title results in a slick trophy, a different sort of wearable, and brings with it an additional 65,000 ZDI reward points (instant Platinum status in 2023).
For those not familiar with how it works, points are accumulated for each successful attempt. While only the first demonstration in a category wins the full cash award, each successful entry claims the full number of Master of Pwn points. Since the order of attempts is determined by a random draw, those who receive later slots can still claim the Master of Pwn title – even if they earn a lower cash payout. As with previous contests, there are penalties for withdrawing from an attempt once you register for it. If the contestant decides to remove an Add-on Bonus during their attempt, the Master of Pwn points for that Add-on Bonus will be deducted from the final point total for that attempt. For example, someone registers for the Apple iPhone 13 with the Kernel Bonus Add-on. During the attempt, the contestant drops the Kernel Bonus Add-on but completes the attempt. The final point total will be 15 Master of Pwn points.
The Complete Details
The full set of rules for Pwn2Own Toronto 2022 can be found here. They may be changed at any time without notice. We highly encourage potential entrants to read the rules thoroughly and completely should they choose to participate. We also encourage contestants to read this blog covering what to expect when participating in Pwn2Own.
Registration is required to ensure we have sufficient resources on hand at the event. Please contact ZDI at [email protected] to begin the registration process. (Email only, please; queries via Twitter, blog post, or other means will not be acknowledged or answered.) If we receive more than one registration for any category, we’ll hold a random drawing to determine the contest order. Registration closes at 5:00 p.m. Eastern Daylight Time on December 2, 2022.
The Results
We’ll be blogging and tweeting results in real-time throughout the competition. Be sure to keep an eye on the blog for the latest information. Follow us on Twitter at @thezdi and @trendmicro, and keep an eye on the #P2OToronto hashtag for continuing coverage.
We look forward to seeing everyone in Toronto and online, and we look forward to seeing what new exploits and attack techniques they bring with them.
With special thanks to our Pwn2Own Toronto 2022 sponsor, Synology, for providing their assistance and technology.

©2022 Trend Micro Incorporated. All rights reserved. PWN2OWN, ZERO DAY INITIATIVE, ZDI, and Trend Micro are trademarks or registered trademarks of Trend Micro Incorporated. All other trademarks and trade names are the property of their respective owners. The “Synology” logo are trademarks of Synology, Inc., registered in the Republic of China (Taiwan) and other regions.
如有侵权请联系:admin#unsafe.sh