Hey guys, hope you all are doing well. I am Bharat Singh a Security Researcher and bug hunter from India. In this writeup I am going to tell you about my recent finding on a VDP which eventually got duplicated :( . Due to the company’s policy I can’t reveal the name of the program.
The target I was hunting on was actually a coding platform with a hell lot of functionalities. Whenever I select a program to test, I usually go through all the functions and try to understand the target manually. So, after a whole day understanding the target I started searching for bugs but got no luck and started feeling burnouts. There were no low hanging fruits and the site was quiet secure, next day with the fresh mind I started hustling again then my eyes went to the profile picture upload option. Since it was quiet secure and I got no low hanging bugs I was not expecting to find a file upload vulnerability there but I give it a try. Firstly I uploaded a txt file and I was SHOCKED!!! it was accepting the .txt files then I moved to another step and tryed to upload a .svg file again it was allowing svg files also which is not common.
What is an SVG file?
Scalable Vector Graphics (SVG) is a web-friendly vector file format.The SVG file format is a popular tool for displaying two-dimensional graphics, charts, and illustrations on websites.
So, I started thinking of how can I exploit this vulnerability and make the more impactful, the first thing that came to my mind was stored XSS, then I made a file with .svg extension with the following payload:
<?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd"><svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<polygon id="triangle" points="0,0 0,50 50,0" fill="#009900" stroke="#004400"/>
<script type="text/javascript">
alert("XSS by BHARAT");
</script>
</svg>
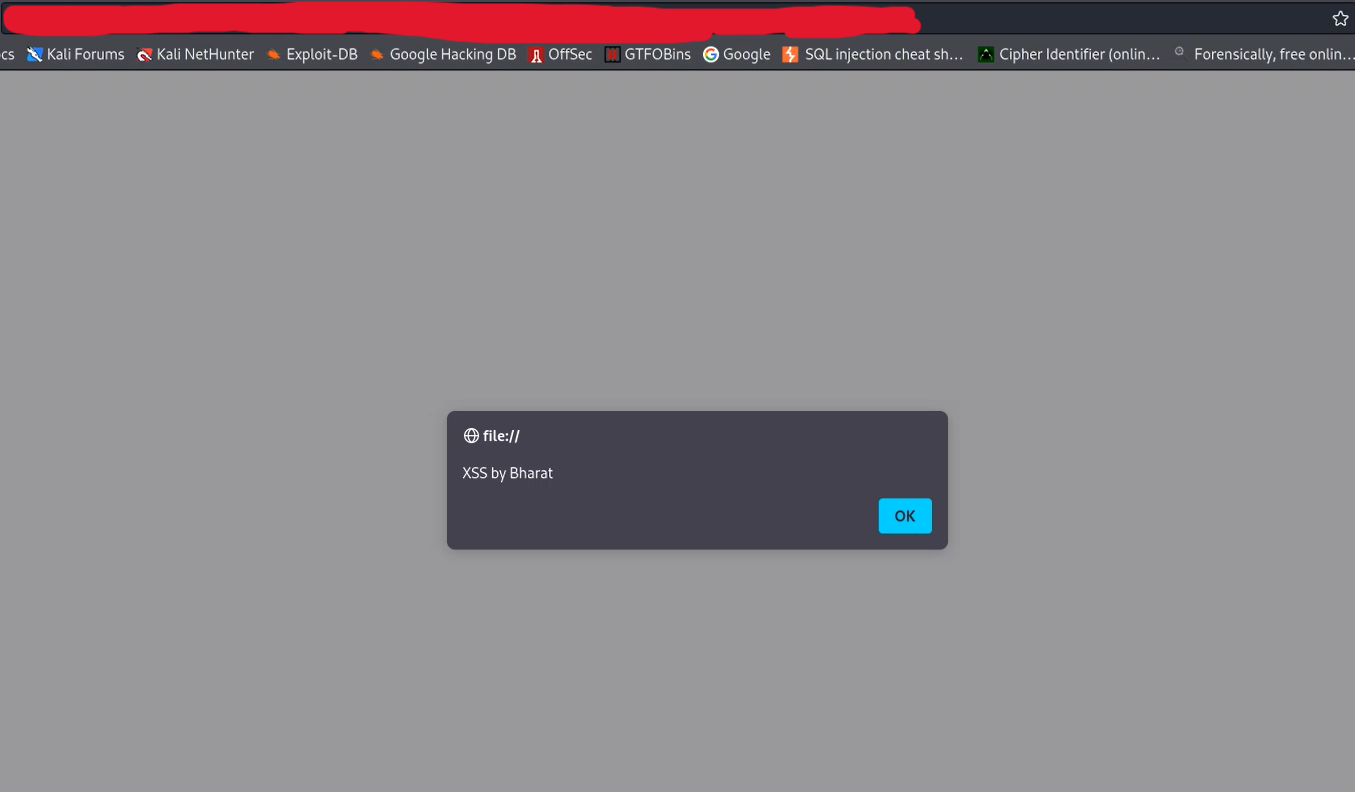
After uploading the file in the profile photo section, I opened the image in new tab and BOOM!!! that alert box.

I was like …
I got a little excited and tried to take it to the next level the RCE (Remote Code Execution), hours went by but I got no luck. I immediately reported the bug to their security team and waited for their response. After two days I got their mail saying…

I was frustated and sad at the same time by felt OK as the time went by, atleast I got a valid bug :).
Timeline:
16 July 2022 — Bug Reported
18 July 2022 — Marked Duplicated
19 July 2022 — Got rewarded with nothing but HOPE and NEVER GIVE UP attitude.
Feel free to connect with me and ask me anything regarding bug bounty and other stuff
Linkedin-https://www.linkedin.com/in/bharat-s1ngh/
Twitter- https://twitter.com/zingzangoo
From Infosec Writeups: A lot is coming up in the Infosec every day that it’s hard to keep up with. Join our weekly newsletter to get all the latest Infosec trends in the form of 5 articles, 4 Threads, 3 videos, 2 Github Repos and tools, and 1 job alert for FREE!
如有侵权请联系:admin#unsafe.sh