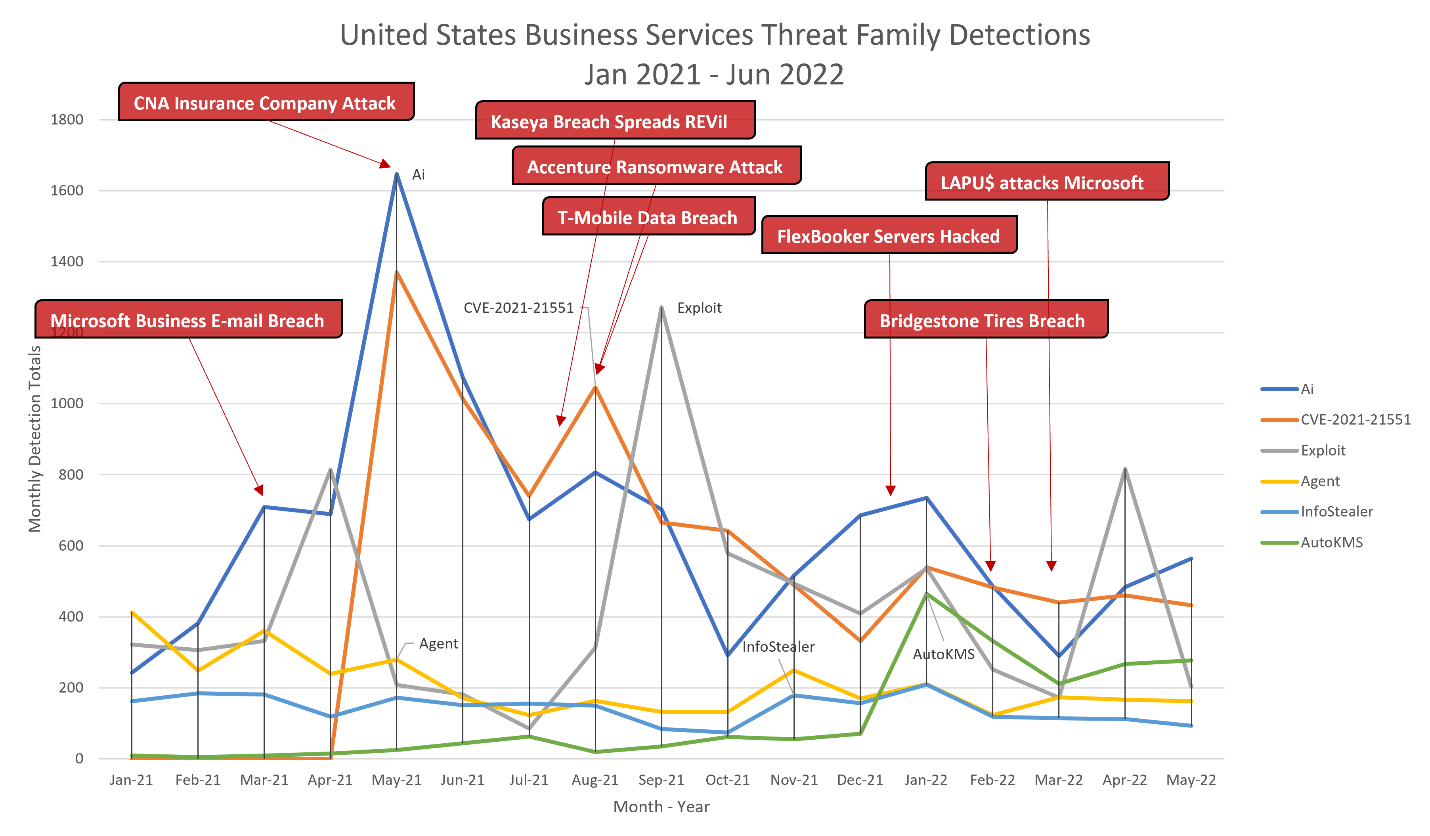
The presence of so many hacking tools in the detections for the Business Services industry tells a story about these organizations being targeted for not only infection, but to establish backdoors and likely gain access to customers of the organizations through the victim’s network.
Just like everyone else, the Business Services industry dealt with heavy detections of exploit attempts using the CVE-2021-21551 Dell driver vulnerability. The trend line followed by these exploit blocks also follow the trend of our heuristic engine detecting never-before seen malware, likely a result of successful exploit attempts during the same period. At the same time we observed this spike, the insurance company CNA Financial was breached in a ransomware attack.
A subsequent spike of this threat in August 2021 coincides with three major attacks, likely achieved because of the success of CVE-2021-21551.These were the Kaseya Breach which spread REvil to hundreds of networks, the ransomware attack on insurance firm Accenture, which demanded $50 million in payment, and the T-Mobile data breach which exposed the information of 50 million people.

Tools meant to compromise or hack an endpoint were discovered in numerous places throughout the year. This includes PortScanner slowly gaining traction through 2021, then spiking during January and February of 2022. Around this same period, the tire-marker Bridgestone was attacked by the LockBit ransomware gang. Our telemetry reveals these attacks focused on organizations in Georgia and Arizona.
Next, OpenPort is a hacking tool that had most of its traction in May and August of 2021 against companies in California and New Jersey, matching up with spikes in detections of the Dell driver exploit.
In addition, the RemoteAdmin tool was detected primarily in Tucson, Arizona and saw a spike in November 2021, which never let up through the rest of the period, meaning that there are likely existing infections of this threat that have yet to be caught.
Wrapping up hacking tools, Business Services in Massachusetts fought off multiple attempts to launch malicious PowerShell scripts on their systems. This was observed throughout the entire period but spiked in December of 2021, coinciding with the hack against the business scheduling provider FlexBooker.
Folks in California and Ohio have been dealing with increasing detections of the notorious Emotet trojan. A massive increase was observed in October 2021 and has continued until the end of the period.
Recommendations to the Business Services industry
Our recommendation is to ensure security staff can push updates and force regular scans on all endpoints, ideally remotely. Regular scanning goes beyond just checking for malware though. We recommend utilizing a traffic monitoring tool to identify any malicious or suspicious traffic coming both in and out of the network. Also, take the time to do regular audits of open ports on all endpoints, looking for possible backdoors.
Considering the desire to utilize these tools from inside of the network, ensure that individual user rights don’t extend to the point of being able to scan the entire network, open ports, or establish remote connections without the permission of IT. This effort will reduce the success these actors have and make their lives a lot harder.