Google updated the Stable channel for Chrome to 104.0.5112.101 for Mac and Linux and 104.0.5112.102/101 for Windows which will roll out over the coming days/weeks. Extended stable channel has been updated to 104.0.5112.101 for Mac and 104.0.5112.102 for Windows , which will roll out over the coming days/weeks.
This update includes 11 security fixes. One of the vulnerabilities is labeled as “Critical” and one of the vulnerabilities that is labeled as “High” exists in the wild.
Vulnerabilities
Publicly disclosed computer security flaws are listed in the Common Vulnerabilities and Exposures (CVE) database. Its goal is to make it easier to share data across separate vulnerability capabilities (tools, databases, and services). We discuss some of the CVE’s included in this update below.
CVE-2022-2852: a critical use after free vulnerability in FedCM. Use after free (UAF) vulnerabilities occur because of the incorrect use of dynamic memory during a program’s operation. If after freeing a memory location, a program does not clear the pointer to that memory, an attacker can use the error to manipulate the program. The Federated Credential Management API (FedCM) allows the browser to understand the context in which the relying party (for example a website) and the identity provider (a third party authentication service) exchange information.
CVE-2022-2856: Insufficient validation of untrusted input in Intents. Chrome intents are the deep linking replacement for URI schemes on the Android device within the Chrome browser. Google’s Threat Analysis Group submitted the vulnerability and technical details will not be released until everyone has had ample opportunity to update.
Google is aware that an exploit for CVE-2022-2856 exists in the wild. A remote attacker can trick the victim to open a specially crafted web page and execute arbitrary code on the target system.
CVE-2022-2854: a UAF vulnerability in SwiftShader. SwiftShader is a an open source library that provides a software 3D renderer. The attacker would have to trick the victim to visit a specially crafted website.
CVE-2022-2853: a heap buffer overflow in Downloads. A buffer overflow is a type of software vulnerability that exists when an area of memory within a software application reaches its address boundary and writes into an adjacent memory region. In software exploit code, two common areas that are targeted for overflows are the stack and the heap. The heap is the portion of memory where dynamically allocated memory resides.
How to protect yourself
The easiest way to update Chrome is to allow it to update automatically, which basically uses the same method as outlined below but does not require your attention. But you can end up lagging behind if you never close the browser or if something goes wrong—such as an extension stopping you from updating the browser.
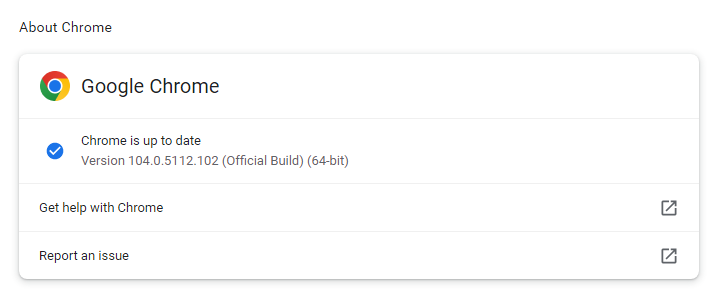
So, it doesn’t hurt to check now and then. And now would be a good time, given the severity of the vulnerabilities in this batch. My preferred method is to have Chrome open the page chrome://settings/help which you can also find by clicking Settings > About Chrome.
If there is an update available, Chrome will notify you and start downloading it. Then all you have to do is relaunch the browser in order for the update to complete.

After the update the version should be 104.0.5112.101 or later.
Stay safe, everyone!