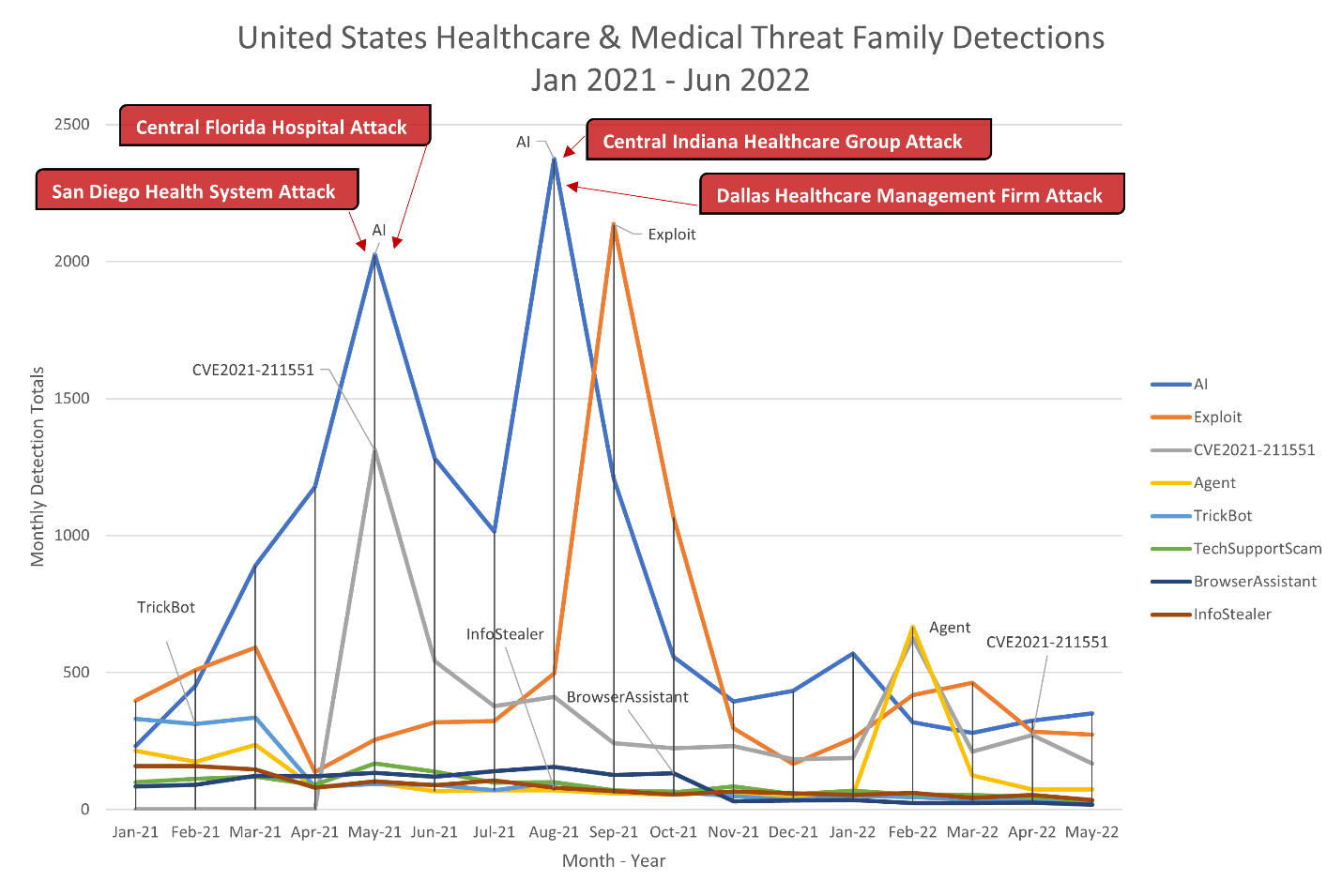
May 2021 was a tough month for the Healthcare and Medical sector–the most notable threat trend at the time was the heavy use of a new popular exploit against Dell systems, leading to immense effort by attackers to utilize the exploit before it became less effective due to patching.
During this period, hospitals in central Florida were hit with malicious attacks that disrupted their operations and forced them to conduct business via pen and paper. In addition, a hospital system in Southern California was forced to modify how it did business due to a cyberattack. The San Diego-based health system quickly moved its information technology program offline, to reduce the damage done by the attack. However it also put a roadblock in the way of legitimate employees and customers trying access their medical information online.

Figure 1. United States Healthcare and Medical Threat Family Detections by Month
After the spike in May, CVE 2021-21551 detections dropped to about a quarter of the original numbers, and remained there throughout the year, except for another spike in February 2022. It seems the primary target for these attacks were healthcare and medical organizations in Pensacola, FL, but detections for New York, Wisconsin and New Jersey weren't far behind.
Heavy detections of TrickBot were observed, especially against organizations in York, Pennsylvania during the first three months of 2021. But detections of this threat all over the United States quickly dropped beginning in April 2021 and steadily declined throughout the time period. TrickBot isn't a stranger to healthcare organizations and has historically targeted them for the sake of launching ransomware or causing operational disruption.
This threat is even a concern to the US Government, which released an alert, through the CISA portal, back in October of 2020, about the danger of the TrickBot organization specifically targeting Healthcare organizations.

Figure 2. United States Healthcare & Medical Family Threat Detections Pie Chart
In August and September, we observed significant spikes of AI behavioral-based detections, which lines up with a series of newsworthy healthcare breaches during the same period.
For example, a healthcare group in central Indiana was the victim of an attack that lead to a ransomware infection and the loss of information from patients and employees, then released on the dark web. The attack itself occurred in early August and forced organizations to turn away ambulances for several days, an action which led to the death of a person in Germany.
Another attack in early August, this time against a healthcare management firm in Dallas, Texas, resulted in the theft of valuable information, including patient information, health insurance and financial data.
Securing healthcare and medical organizations
Our recommendations for securing healthcare and medical organizations start with acknowledging that securing these organizations from every possible threat is not possible. Therefore, when considering how to defend against a ransomware attack, be sure to account for getting operations back online after an attack. This includes having plans for operating the business without the use of computers, establishing secure backups of sensitive data off-site and off-line, while still following HIPPA protocol.
Beyond that, this industry has dealt with lots of heavy attacks originating from both attempts to exploit vulnerabilities, as well as spear phishing. Quickly patching vulnerabilities is a high priority, however given that quick patching isn’t always an option, times like these require risk reduction, such as removing non-patchable endpoints from direct Internet access, creating additional layers of authentication to access high value systems, and a thorough review of user accounts and permissions, to tighten up who has access to what.
Finally, many of these organizations utilize mobile stations for inputting or reviewing data. These systems should not be able to do things like using USB drives. They should have screen protectors to prevent unintended information disclosure, and these systems should be completely wiped with a new image on a regular basis, to ensure removal of any hidden rootkit-level threats.