2022-8-10 21:58:39 Author: www.nowsecure.com(查看原文) 阅读量:28 收藏
Only 22% of developers have a clear understanding of which security policies they are expected to comply with, according to the “Bridging the Developer and Security Divide” study conducted by Forrester Consulting on behalf of VMware. For many businesses, adopting mobile security standards such as OWASP Mobile Application Security Verification Standards (MASVS) can play an important role in unifying security and development teams and speeding releases.
Standards-based mobile application security testing establishes consensus between security, developers and other stakeholders on the risks that must be addressed as part of the release process of a mobile application. By embracing mobile AppSec testing standards, organizations can reduce the time it takes to build and release secure mobile apps.
Organizations should adopt practices in which the development team commits to security by design — that is, building mobile apps with security baked in – and all teams commit to testing to that standard. Specifying secure coding requirements up front improves consistency and code quality, resulting in fewer security issues. In addition, clarifying expectations builds trust between mobile app developers and security analysts.
Why Security Standards Matter
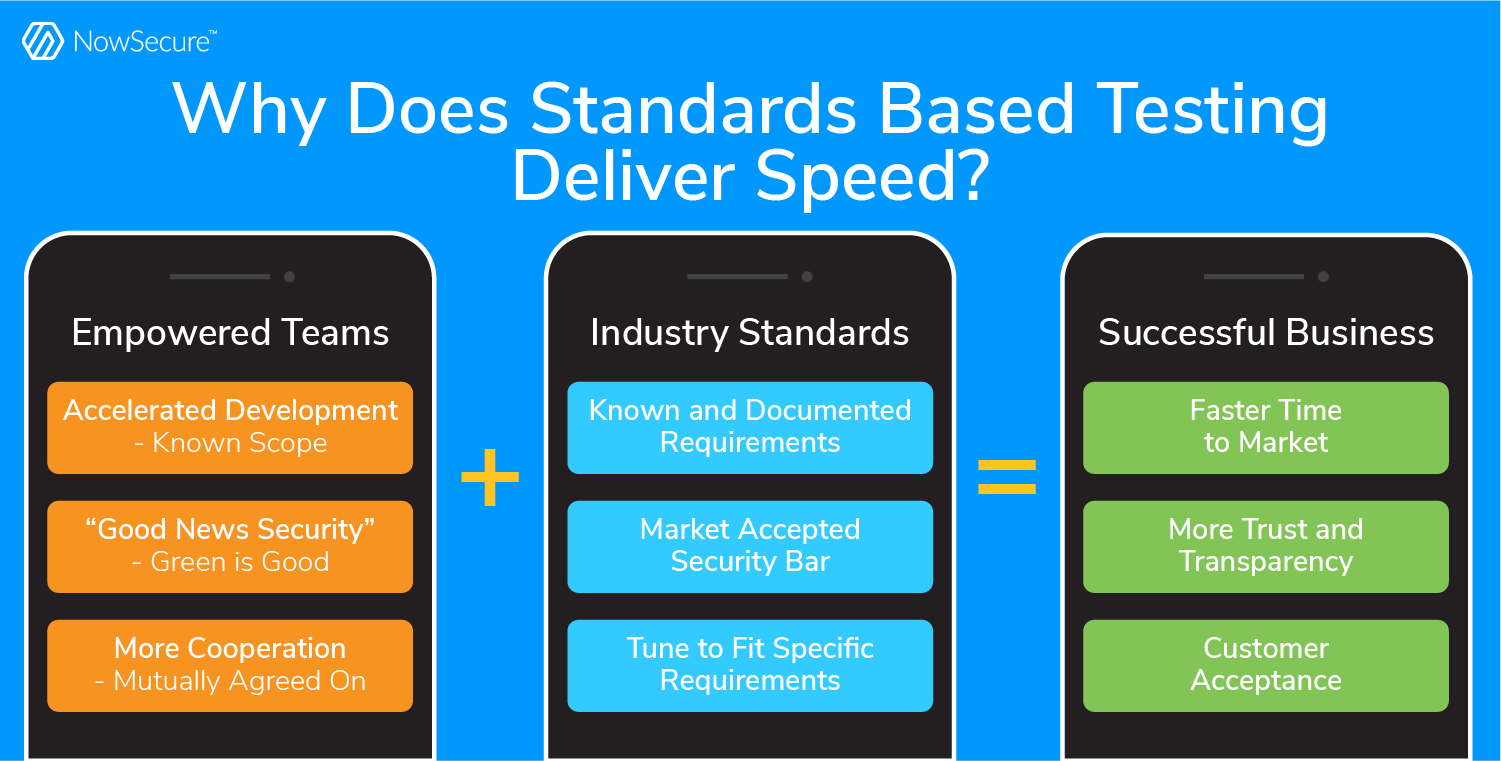
Defined mobile application security standards make it significantly easier for security and development teams to agree in advance about what does and does not need to be addressed before a mobile app is released to production. A common form of reference will improve communication and prioritization between the two groups and aid the process of training development teams on the minimum standards required for a particular risk category. Developers want to build secure applications and they want to know the rules of the security road. Standards-based testing enables the security team to give developers the rules and then support the release process vs being viewed as a blocker.
Forging consensus about mobile app security standards pays off by creating efficiency throughout every stage of the SDLC. For example, product managers can write specific mobile app security stories and requirements, developers can code in line with enterprise security standards and security analysts can automatically test and conduct manual mobile pen testing faster against an agreed-upon standard that sets the minimum bar for release to production.
Once rules are defined, the mobile AppSec and DevSecOps teams can apply automated mobile application security testing within the development pipeline to speed testing and remediation. Development can own the prioritization and remediation process with direct involvement from security, while in turn security can monitor the dashboards to see that an app passed all standards before release and can provide periodic quality control.
This scenario empowers both groups to work autonomously and manage by exception, focusing solely on issues that fail the security standards test. For example, the NowSecure Platform mobile AppSec testing tool dashboard displays color-coded security scores to convey risk with green items representing good, orange and yellow requiring caution and red alerting to the need for remediation. Achieving green results gives teams validation and assurance that they’re doing the right thing and can take pride in building secure mobile apps.
Standards-based testing benefits mobile AppSec, DevSecOps and development teams by delivering:
- Speed throughout the SDLC
- Efficiency with everyone operating in sync
- Scale across the business
- Accountability to meet requirements
- Alignment across teams
- Predictability of what to do and how
- Consistency for the same thing every time
- Security based on risk
“Industry standards provide mutually agreed-upon benchmarks that are vendor agnostic and that change as industry and attack vectors change,” says NowSecure CEO Alan Snyder. “Industry standards eliminate concerns about security companies overpromising and under delivering because the requirements are clearly defined and understood.” In addition, standards enable industry participants such as regulators, consumers and cyber insurance providers to accept standards-based testing as proof of controls.
OWASP Awareness
The industry has embraced OWASP as the global standard for mobile security. Launched in 2013, the OWASP mobile project has driven standards-based security requirements and testing strategies for nearly a decade. Used by mobile app developers, architects, security teams and security researchers, the OWASP mobile project combines three critical resources to provide the best risk reduction approach for mobile app teams:
- The OWASP Mobile Application Security Verification Standard (MASVS) establishes a baseline of security requirements for mobile apps
- The OWASP Mobile Security Testing Guide (MSTG) outlines how to test the MASVS requirements
- The OWASP Mobile App Security Checklist tracks security assessment tasks
“The OWASP MASVS and MSTG are the foundation of a mobile AppSec program,” says Carlos Holguera, OWASP project lead and NowSecure security researcher. “The MASVS guides developers and security analysts on architecture, threat modeling and proper techniques to secure mobile data.”
The OWASP MASVS domains include:
- V1: Architecture, Design and Threat Modeling Requirements
- V2: Data Storage and Privacy Requirements
- V3: Cryptography Requirements
- V4: Authentication and Session Management Requirements
- V5: Network Communication Requirements
- V6: Environmental Interaction Requirements
- V7: Code Quality and Build Setting Requirements
- V8: Resiliency Against Reverse Engineering Requirements
OWASP MASVS aids threat modeling by categorizing apps into four different levels of security verification based on risk profile. Ranging from basic security to the most stringent level, the risk profiles help security and development teams prioritize testing and remediation:
- L1: Standard Security
- L2: Defense-in-Depth
- L1 + R: Standard Security + High Reverse Engineering Resiliency
- L2 + R: Defense-in-Depth + High Reverse Engineering Resiliency
For example, a WebMD app functionality doesn’t present much risk if compromised so can be classified as L1. An Internet of Things weight monitoring app contains sensitive personal information categorizing it as requiring L2. A medical formulary app contains intellectual property making it L1 + R, while a healthcare drug delivery app requires the highest level of L2 + R security.
Secure Mobile App Development: 6 Ways to Power Efficiency
NowSecure Supports OWASP
NowSecure partners with the mobile security community to support open-source tools such as Frida and Radare and help create standards and compliance programs such as the App Defense Alliance (ADA) Mobile Application Security Assessment (MASA) and ioXt. The OWASP MASVS community recognizes NowSecure as a “god mode” sponsor for MASVS and an OWASP Mobile Security Testing Guide (MSTG) Advocate based on its experts’ contributions, effectively setting a blueprint for other potential contributors to help drive the project forward.
Several NowSecure solutions and services help organizations achieve secure coding and testing standards and policies based on OWASP MASVS and tune them to their specific internal or industry requirements. NowSecure Platform security assessment findings map to MASVS and the company recently debuted OWASP MASVS compliance pen testing. Get a NowSecure Platform demo today or reach out to learn more about our pen testing services.
By embracing mobile AppSec testing standards such as OWASP MASVS, mobile app development organizations can achieve predictability and stability and in turn reduce the time it takes to build and release secure mobile apps.
如有侵权请联系:admin#unsafe.sh