Microsoft has fixed 121 vulnerabilities (aka flaws) in the August 2022 update, including 17 vulnerabilities classified as Critical as they allow Elevation of Privilege (EoP) and Remote Code Execution (RCE). This month’s Patch Tuesday fixes two (2) zero-day vulnerabilities, with one (1) actively exploited in attacks (CVE-2022-34713, CVE-2022-30134). Earlier this month, August 5, 2022, Microsoft also released 20 Microsoft Edge (Chromium-Based) updates addressing Elevation of Privilege (EoP), Remote Code Execution (RCE), and Security Feature Bypass with severities of Low, Moderate, and Important respectively.
Microsoft has fixed several flaws in its software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Microsoft Edge (Chromium-based), Remote Code Execution (RCE), Security Feature Bypass, and Spoofing.
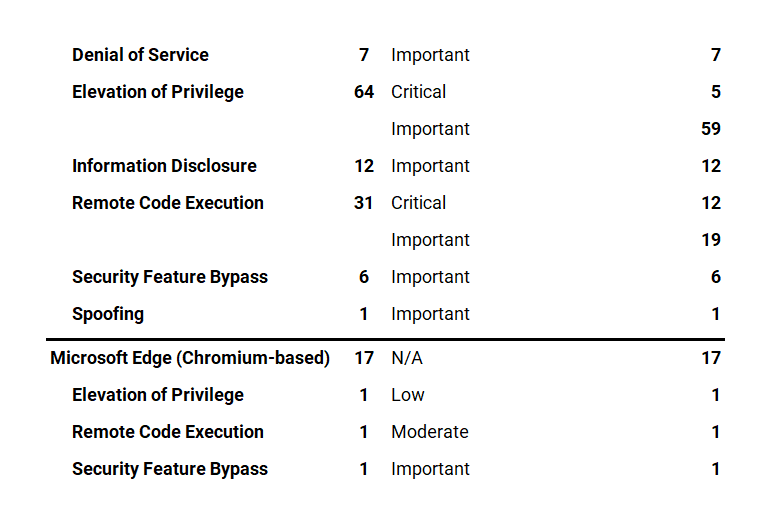
The August 2022 Microsoft vulnerabilities are classified as follows:

A vulnerability is classified as a zero-day if it is publicly disclosed or actively exploited with no official fix available.
CVE-2022-34713 | Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8/10.
In May, Microsoft released a blog giving guidance for a vulnerability in MSDT and released updates to address it shortly thereafter. Public discussion of a vulnerability can encourage further scrutiny on the component, both by Microsoft security personnel as well as our research partners. This CVE is a variant of the vulnerability publicly known as Dogwalk.
Exploitability Assessment: Exploitation Detected
CVE-2022-30134 | Microsoft Exchange Information Disclosure Vulnerability
This vulnerability has a CVSSv3.1 score of 7.6/10.
This vulnerability requires that a user with an affected version of Exchange Server access a malicious server. An attacker would have to host a specially crafted server share or website. An attacker would have no way to force users to visit this specially crafted server share or website, but would have to convince them to visit the server share or website, typically by way of an enticement in an email or chat message. For more information, see Exchange Server Support for Windows Extended Protection and/or The Exchange Blog.
Exploitability Assessment: Exploitation Unlikely
Security Feature Bypass Vulnerabilities Addressed
These are standalone security updates. These packages must be installed in addition to the normal security updates to be protected from this vulnerability.
These security updates have a Servicing Stack Update prerequisite for specific KB numbers. The packages have a built-in pre-requisite logic to ensure the ordering.
Microsoft customers should ensure they have installed the latest Servicing Stack Update before installing these standalone security updates. See ADV990001 | Latest Servicing Stack Updates for more information.
An attacker who successfully exploited either of these three (3) vulnerabilities could bypass Secure Boot.
CERT/CC: CVE-2022-34301 Eurosoft Boot Loader Bypass
CERT/CC: CVE-2022-34302 New Horizon Data Systems Inc Boot Loader Bypass
CERT/CC: CVE-2022-34303 Crypto Pro Boot Loader Bypass
At the time of publication, a CVSSv3.1 score has not been assigned.
Exploitability Assessment: Exploitation More Likely
Microsoft Critical and Important Vulnerability Highlights
CVE-2022-35794, CVE-2022-35794 | Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 8.1/10.
Successful exploitation of this vulnerability requires an attacker to win a race condition.
An unauthenticated attacker could send a specially crafted connection request to a RAS server, which could lead to remote code execution (RCE) on the RAS server machine.
Exploitability Assessment: Exploitation Less Likely
CVE-2022-30133, CVE-2022-35744 | Windows Point-to-Point Protocol (PPP) Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8/10.
This vulnerability can only be exploited by communicating via Port 1723. As a temporary workaround prior to installing the updates that address this vulnerability, you can block traffic through that port thus rendering the vulnerability unexploitable. Warning: Disabling Port 1723 could affect communications over your network.
Exploitability Assessment: Exploitation Less Likely
CVE-2022-34691 | Active Directory Domain Services Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
This vulnerability can only be exploited by communicating via Port 1723. As a temporary workaround An authenticated user could manipulate attributes on computer accounts they own or manage, and acquire a certificate from Active Directory Certificate Services that would allow elevation of privilege to System.
Please see Certificate-based authentication changes on Windows domain controllers for more information and ways to protect your domain.
Exploitability Assessment: Exploitation Less Likely
CVE-2022-33646 | Azure Batch Node Agent Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 7.0/10.
Successful exploitation of this vulnerability requires an attacker to prepare the target environment to improve exploit reliability.
Exploitability Assessment: Exploitation More Likely
Qualys Patch Tuesday QIDs are published as Security Alerts typically late in the evening on the day of Patch Tuesday, followed later by the publication of the monthly queries for the Unified Dashboard: 2022 Patch Tuesday (QID Based) Dashboard by Noon on Wednesday.
Please check back again today and tomorrow for additional information and resources.